Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.
Well another great way to burn up our taxpayer money. From Cold Warriors to targeting trafficking: US military shifts focus in Europe - World News.

Learn how to use camera and light targeting in modo 302. Camera and Light targeting adds a finer level of control to an already robust system. In modo 302, targeting allows the Camera or light to automatically track the selected target item. In camera mode you can even have the target set the focus distance. The modo 302 update is free of charge to all registered modo 301 users. Use camera and light targeting in modo 302.

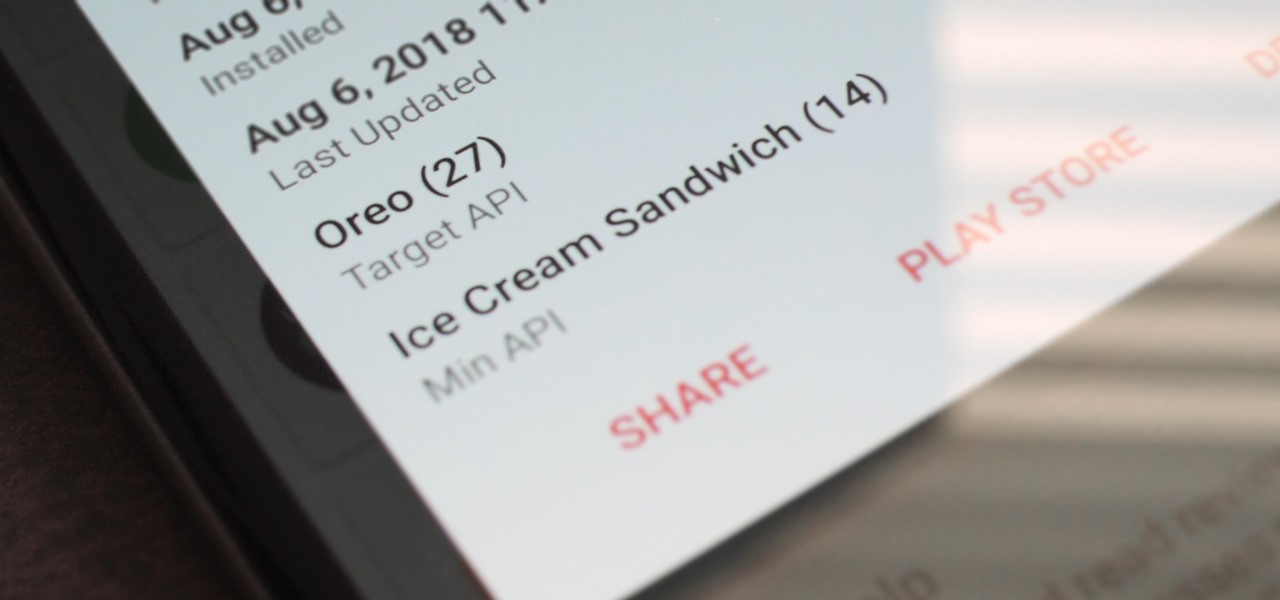
On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

Behavioral ad targeting companies are diving deeper into the realms of your subconscious with a new approach to serving adverts to you online—and they're using your television.

The arms are the part of the body most used by Westerners in fighting. As a result, targeting and disabling an opponents arms is a great way to end a fight quickly without the risk involved in hitting an opponent's head. This three-part video details pressure points all over the arms and various ways of striking them in order to hurt and disable your opponent, ending your engagement with limited damage to both yourself and them.

Get rid of your water-wasting sprinkler system— but not entirely! Keep your landscape and garden maintained by converting those sprinklers into eco- and pocket-friendly drip irrigation. In this how-to video, Paula Mohadjer from the Cascade Water Alliance explains how you can easily convert your sprinklers into a drip irrigation system.

Component 1. Frame And Posture. The benefits of dance shoes never outweigh the benefits of proper spin technique. Your body should be straight lower abs and stomach should be tight. Your arms are in proper position. If you lift your hand it should be in 90 degree angle.

Commemorate the worst president in history by drawing his face to a lifelike representation and then having a dart throwing contest with your homeboys at the bar! This drawing tutorial, which teaches you how to sketch the face of George W. Bush, or W, is an excellent way to hone your targeting and aiming skills.

Practice lineout throws for rugby from the Ford Academy in Australia. Throwing the rugby ball with two hands overhead. It is important to focus on targeting, speed and your teammates. A lineout throw is made when the ball goes out of bounds and you need to reenter it into play.

Going for a Predator outfit for Halloween or as a cameo in your film, you want to try to get as close to the real thing as possible. In this video you will learn how to perfectly align LED lights to create the targeting lights that the predator uses for its canon with a quick tutorial!

Squats are a weight training exercise that involves lowering the body and raising it again, targeting the legs and core. Learn how to do squat exercises in this strength training video. Take action: keep back straight & flexed, keep knees over heels, stick butt out to maintain safe posture, and look forward. Tom Clifford, the instructor in this how-to video, has a degree in physical education, fitness and health from Eastern Michigan University, where he ran track and cross-country. Tom has w...

Isolate shoulder muscles with specific weightlifting exercises. Learn tips and techniques for working out the chest, back, shoulders, and arms in this weightlifting video. Take action: targeting anterior & lateral deltoids, bring dumbbells to side with feet shoulder-width apart. Lance is certified personal trainer through American Fitness Association of America. He graduated from UNC with a biology degree and currently works for a gym. He specializes in weight training, circuit training, endu...

Love the idea of a superhero MMO, but prefer the feel and controls of a first person shooter? You can actually set up your controls and targeting system in the game to make the interface behave more like your favorite FPS!

Targeting Notes and Creating Harmonies Using MIDI -- Jeff Dykhouse shows us how to use MIDI to tell Auto-Tune which notes to tune. In addition, you can use this technique to create harmonies. Antares Auto-Tune is the fastest, easiest, and highest quality tool for pitch correction. Use this in conjunction with DigiDesign's Pro Tools for awesome sounds.

Sadie Nardini shows you how to transform the basic sun salutation yoga exercise into a core-targeting exercise that burns calories.

Learn how to do wide push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Rainbow trout are a unique, elusive catch. When you are hunting this fantastic fish, you will need to have specific skills and certain equipment. In this tutorial, learn how to fish for rainbow fish like a pro, with expert advice.

Kathy Kaehler, author, celebrity trainer, spokesperson and mother, gives us a rundown of the best exercises for fellow women and moms on how to target their belly fat and love handles, and specifically the best ways to tighten these areas. Kathy first does advise us that if you're going to be targeting like this the most important thing first will be cardio and general fitness. Then, she offers us first the side plank, where you place one elbow to the ground, lying on your side, and then elev...

Paul Bolzoni is one of the best exterminators of New York City. Watch as he talks about some of his experiences as he goes around New York helping people with the bedbug epidemic.

In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

Less than two months after launching its augmented reality platform for casual gaming and shared experiences, Snapchat is ready to make Snappables available to advertisers.