Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...
» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

If you suspect that there may be something wrong with the fuel pump on your Saturn car, you should make sure you have proper voltage in the connector in your trunk. If you do, the next step is to check the ground.

Suspicious of the pumpkin pie filling you can find in the store? Just feeling ambitious and want to try to make your own filling? Here's how you can bake a traditional pumpkin pie using real pumpkins. Make sure you get the right kind of pumpkins!

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Want music now? Not keen on downloading software or suspicious files to get it? This is a handy media trick from Tinkernut on how to torrent audio files without downloads. Stream music torrents without having to download any torrent software using Bitlet.org .

Skin Cancer Expert Dr. Coyle Connolly, D.O., does a full body check up on patient to detect if there are any new or existing moles or suspicious lesions that could be precancerous or cancerous.

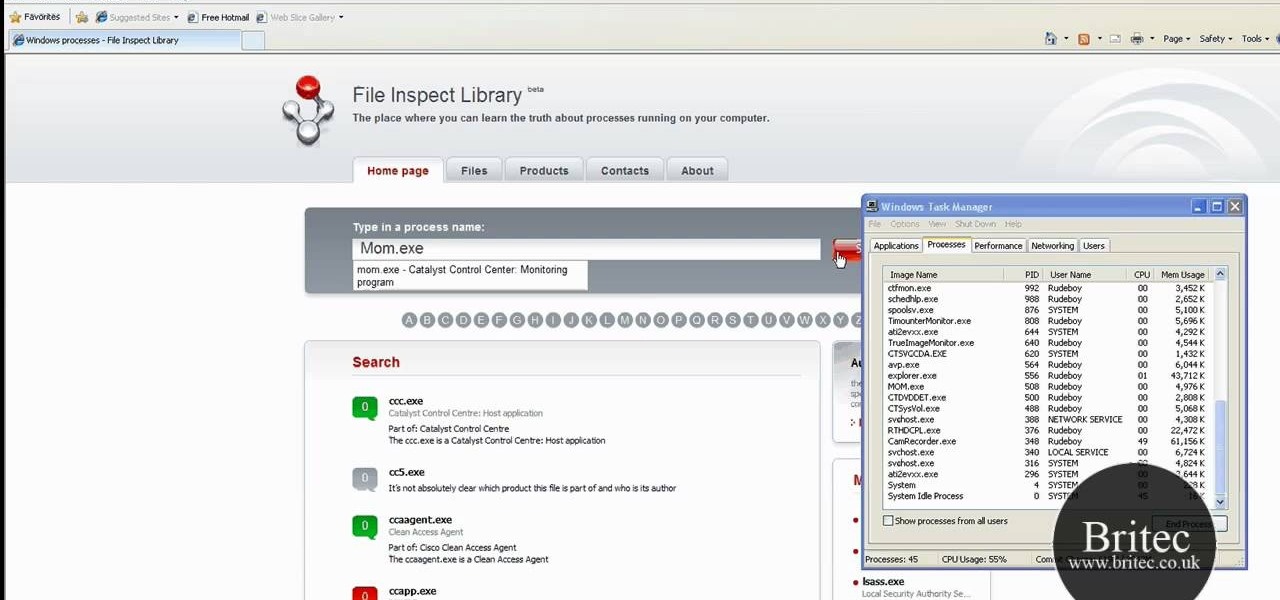
Need help figuring out what a suspicious process is up to on your Microsoft Windows PC? With FileInspect, it's easy to figure out whether a given process is benign or malicious. So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For complete details, including step-by-step instructions, watch this video guide.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

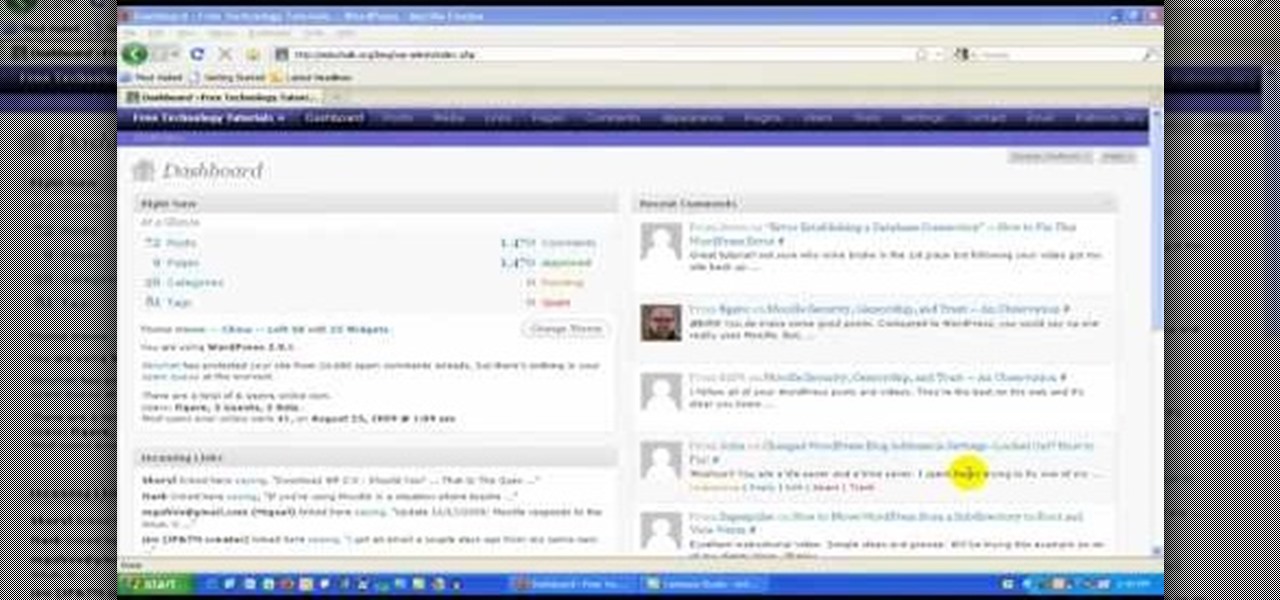
In this video tutorial, viewers learn how to locate and remove spam accounts from a WordPress blog. Begin by logging on your blog and select the User tab. Search through the user list and look for suspicious email accounts. Some keys that reveal spam accounts are: emails that have .ru, poker, Viagra, pharmacy and accounts with more then one dot. Use your common sense to find spam accounts. Select the account you want to delete. Select Delete and click on Apply. This video tutorial will benefi...

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.

The Climbup Insect Interceptor is a new monitor for the use of detecting bed bugs. This is a new monitor. It's a passive monitor. You can place the monitors underneath one of the legs of a sofa or bed or other suspicious piece of furniture. This will not rid your home of bed bugs. This is a way of letting you know where the infestation is or isn't. It is a monitor, but it does not control them. Once the bugs fall into the trap, they can't get out. You will need to properly dispose of them, af...

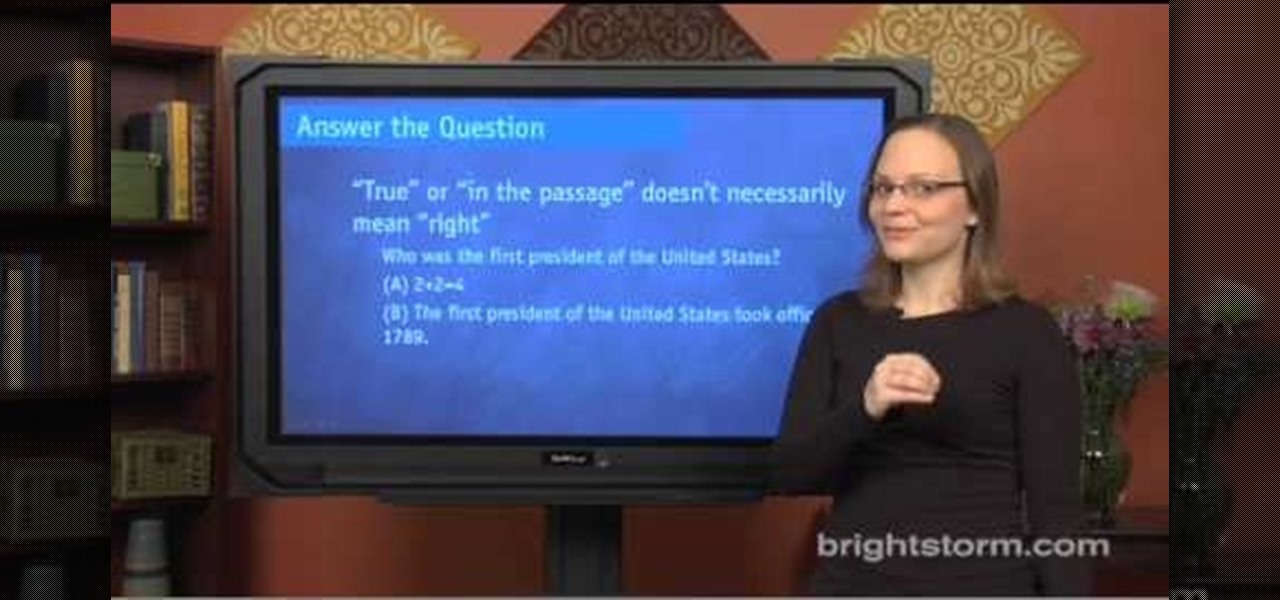
In this Education video tutorial you will learn how to avoid wrong answers on the SAT critical reading area. Five principles to keep in mind are rephrase the question and predict the answer, answer the question being asked, find evidence in the passage, extreme answers are suspicious and finally remember a little wrong is all wrong. To rephrase the question, read 2 lines before and after, ask the question in your own words and find the answer choice that best matches your prediction. Now comi...

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

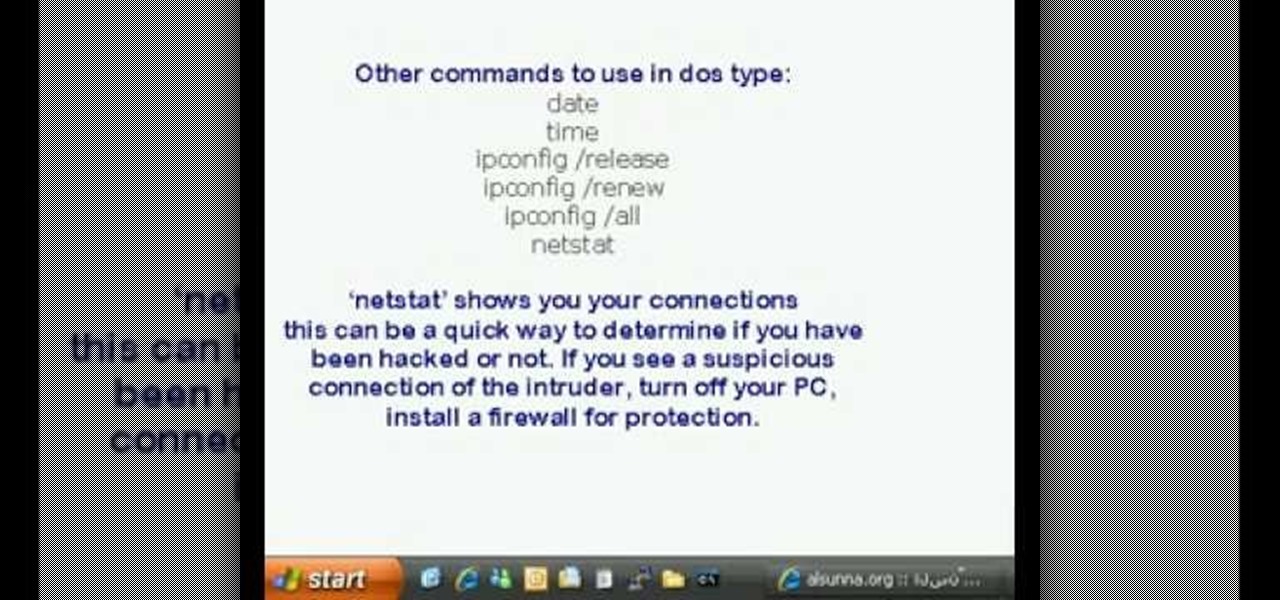
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

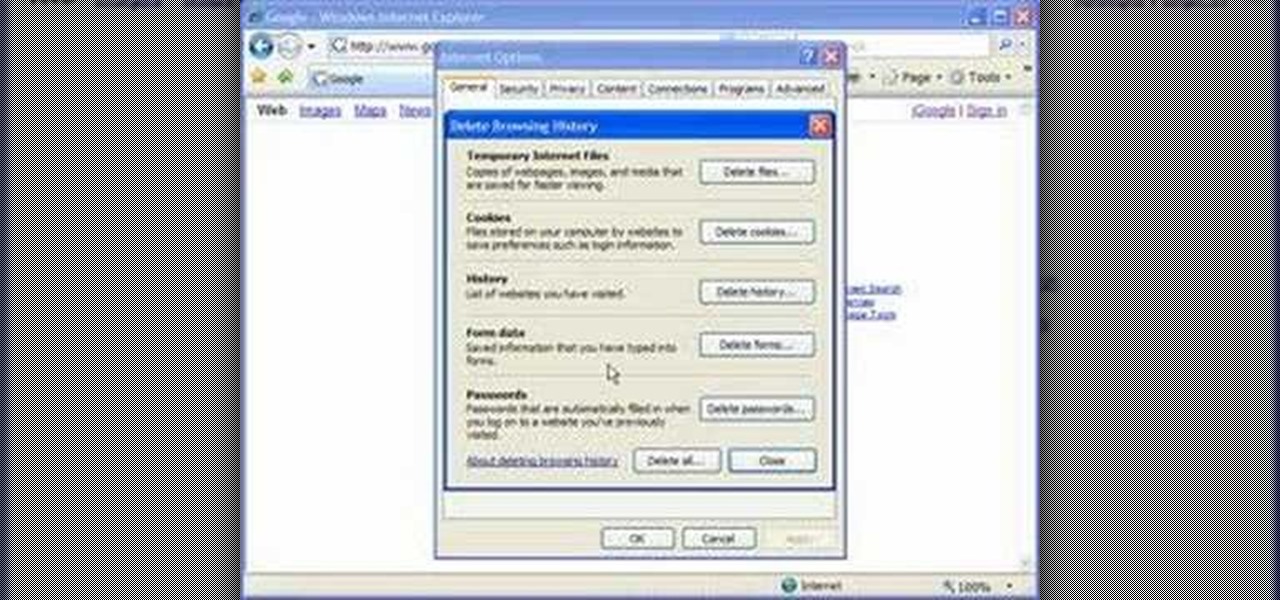
In this Computers and Programming video tutorial you will learn how to delete temporary internet files in Internet Explorer 8. The video is from FreeComputerRepair. Click on Start -> control panel ->network and internet connections -> internet options. Now the internet properties dialog box opens up. Here you go down to browsing history and click ‘Delete’ button. This will open up the Delete Browsing History window. Here you check all the data that you want to delete. If you don’t want to del...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to create an Internet enabled claw game.

This tutorial demonstrates how to use Microsoft Internet Explorer and Mozilla Firefox. Learn more about web browsers in this free instructional video series.

With iTunes, you can listen to the radio over the internet and hear broadcasts from around the world. Make sure your computer is connected through the internet, then click "Radio" in the source list to see the internet radio stations available through iTunes.

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

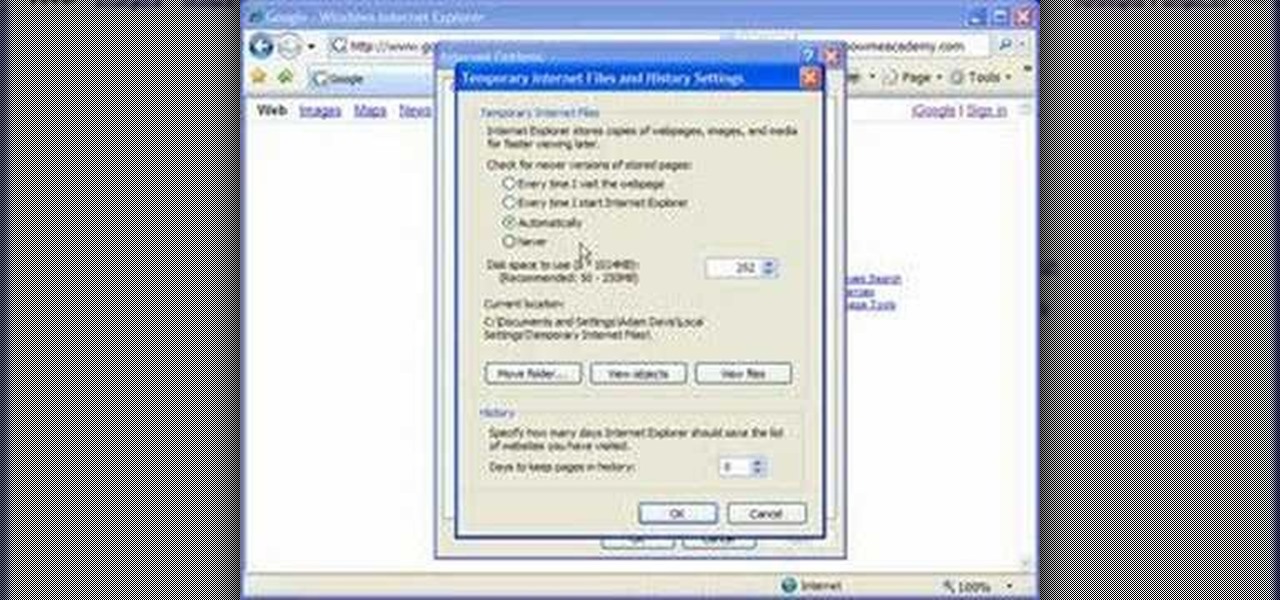
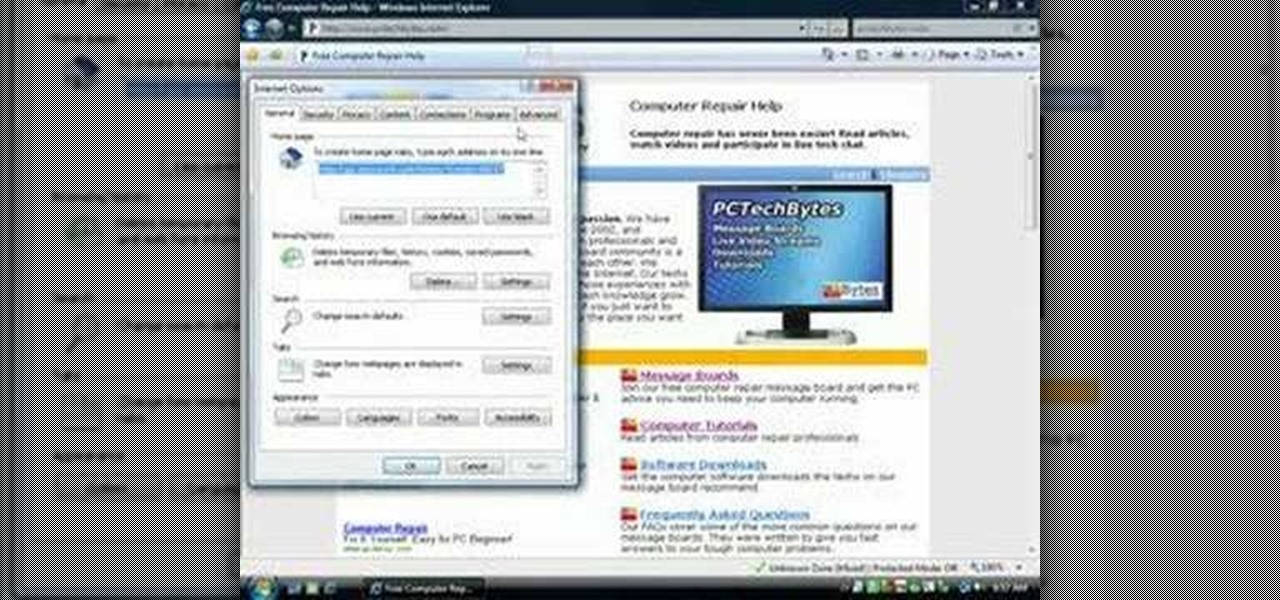
In this video, we learn how to automatically clear browser cache in Internet Explorer. This will help your internet run faster and it will also help protect your computer from your personal information being store. First, open up Internet Explorer, then click on the tools drop down menu and go to internet options. From here, go to temporary internet files and click on the button that says "automatically", then adjust the disk space to use to what you prefer. After you have changed the setting...

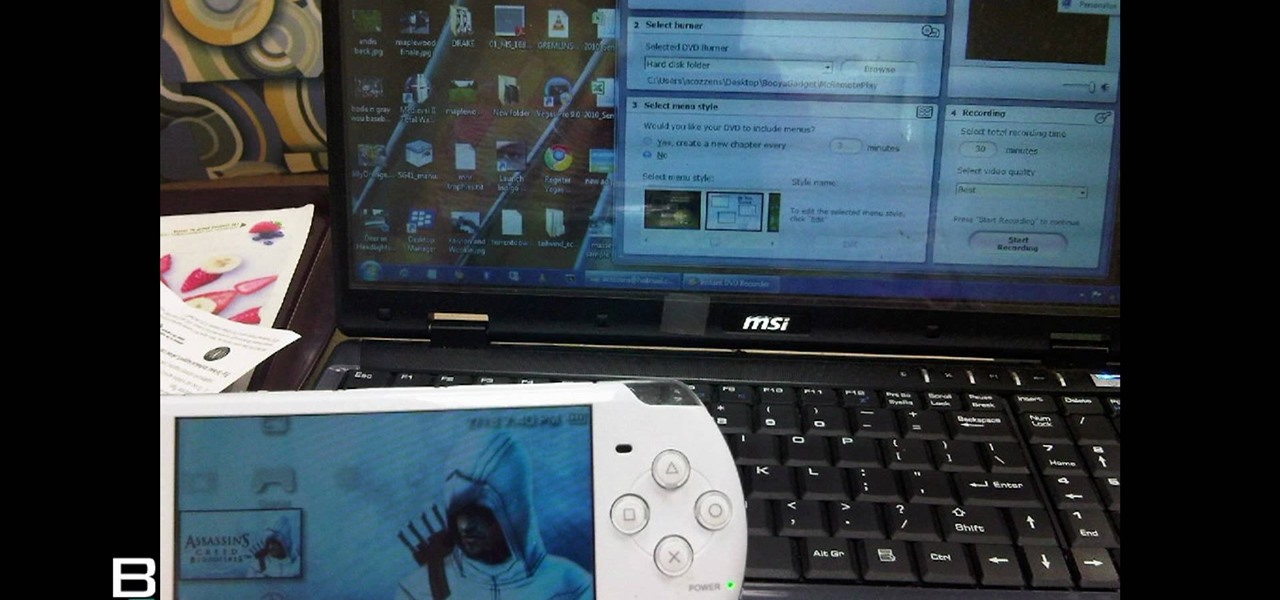
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection with your PSP.

If you've already gotten your hands on Sony's Internet TV Blu-ray Disc Player, powered by Google TV, then you know how powerful this thing is. But if you're thinking of getting one soon, this video series will help you learn what you'll be getting yourself into.

Cookies serve their purpose in Internet Explorer 7. They let the browser know which sites you have visited so you don't have to get security prompts every time you back to them. However, they can also slow down your browser, which can be frustrating. This video will show you how to delete cookies in Internet Explorer and browse faster.

Just because the internet renders you virtually anonymous does not mean social customs should be ignored. Just like in the outside world, there is etiquette that should be obeyed if you want to be treated as a friend rather than an annoyance online. In this how to video, Proper Ollie teaches you how you can have proper internet etiquette in social networking forums.

Have you maybe been eyeballing some things you'd rather other people didn't know about? Clear your Internet history and leave your anxiety behind.

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.

If your computer or web browser is running slowly, a good place to start clearing space is in your Temporary Internet Files. Temporary Internet files, as well as cookies, are collected every time you visit a site online. These files make it easier for your PC to remember your browsing history, and your log in information for various websites. However, sometimes all of these little files can add up into one big clog on your machine. If your computer isn't running up to par, follow along with t...

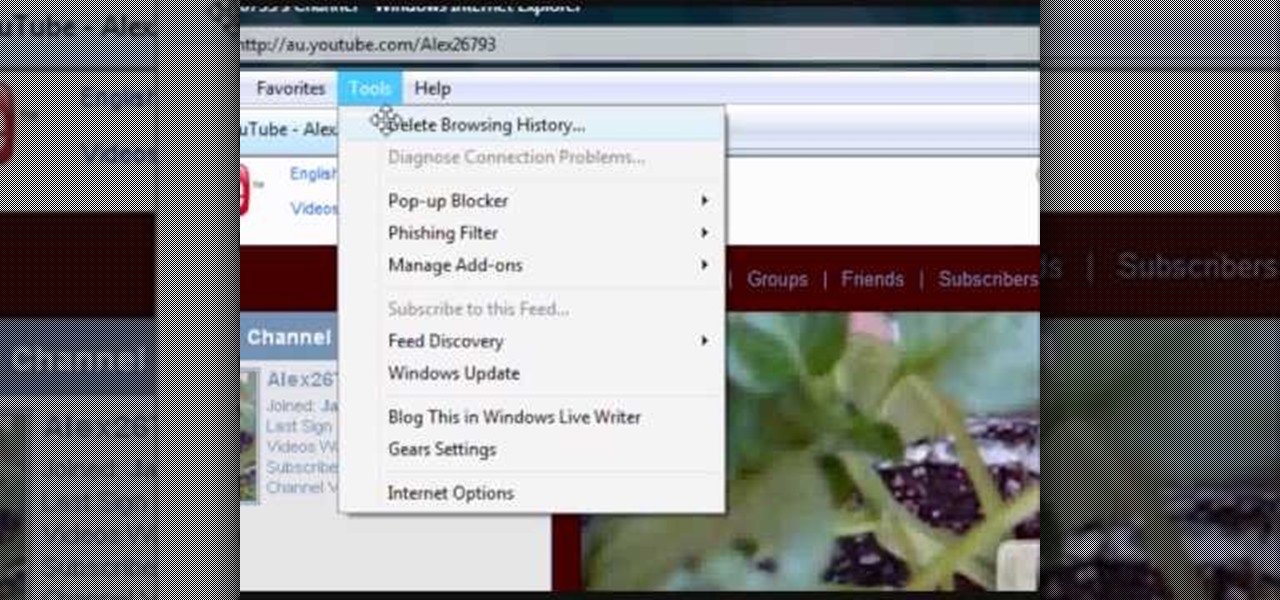
In this video, we learn how to remove our browsing history on Internet Explorer. First, click on "tools", then click on "delete browsing history". If you want to delete all of your browsing history, then click on that option. Most people are content with only deleting temporary internet files as well as browsing history. Getting rid of these will speed up your internet a bit. Another way is to go into "internet options", click under the "general" tab and choose which files you'd like to delet...