What's better than stealing that roll of chocolate chip cookie dough from your fridge and eating it straight from the tube? Mixing it with peanut butter and baking it into a delicious cupcake, of course.

Nuggeting is a popular craze hitting schools everywhere. It involves stealing a backpack, removing the contents, turning it inside out, and replacing the contents. The victim will soon find that their backpack has been turned in to a "nugget." This is a great prank for the school classroom. Use this as inspiration for one of your April Fools Day pranks!

Now that Kratos had made it past the Palace of Hades, he must confront none other than Hades himself. This is the ultimate boss fight in the Realm of Hades, so be prepared. Try stealing the Claws of Hades to help. Watch the walkthrough for the Hades Boss Fight in God of War III on PS3.

Are you sick of your dogs bad behavior? Such as chewing your furniture, bothering you while eating dinner, barking incessantly, and even stealing your slippers! Dee Hoult shows us how to properly use the 'Kong' toy to prevent all this undesirable behavior. It's simple, you just fill the toy with your dogs regular dog food, soak it with water, and put it in the freezer for 1 hour! Then you give your "Kong Pupsicle" to your dog, who will play with it for 30-45 minutes, getting the food out of t...

Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

Scam School presents four silly beer gags in this how-to video.

Is Taylor Swift your fashion idol? Emulate her style by stealing her hair do with tips from this hair tutorial! Learn how to get her curls at home without dropping tons of cash at a salon.

Watch this video to learn how to make a cheap grind rail without welding. This does involve stealing a stop sign which is illegal.

Keep your trailer safe just like you would your car or truck! This video shows you how to use a trailer coupler lock. You can place this lock on your trailer when it is not in use and it prevents people from hooking up and stealing your trailer.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Instagram Direct is fast becoming the end-all-be-all messaging app, and it just added some incredibly convenient features that should make it a bit more practical. These new additions have a clear purpose: To help Instagram Direct grow its base and take on more feature-rich messengers like Snapchat or WhatsApp.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

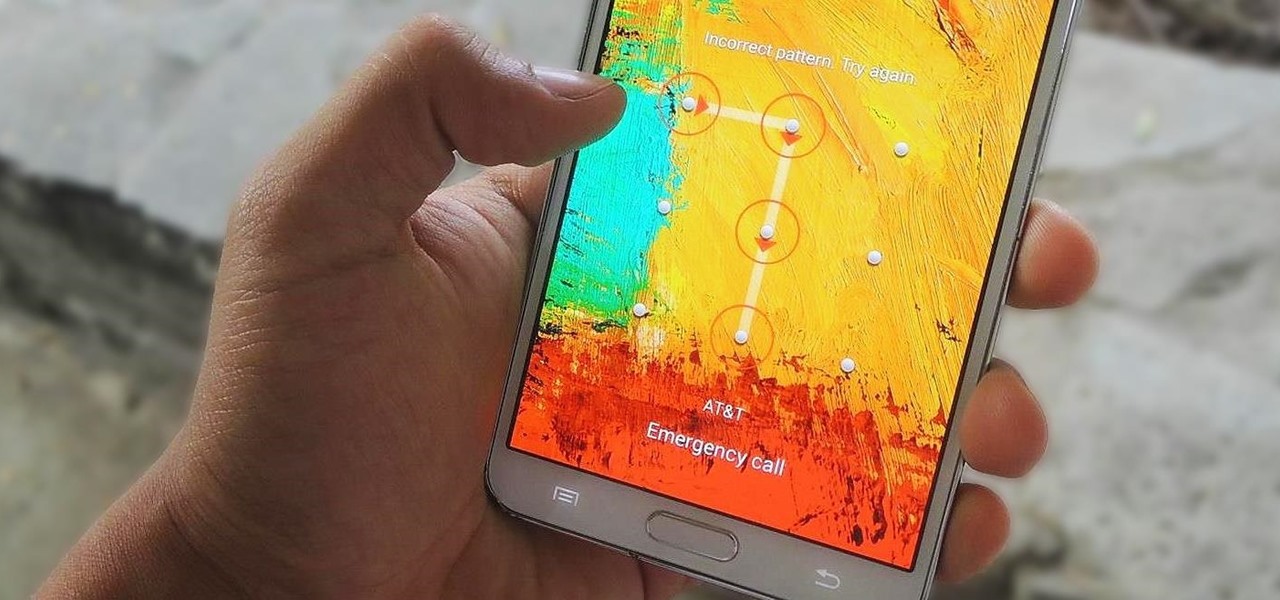
Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

With the bombardment of technical issues that have plagued GTA Online since its inauguration, it hasn't been easy to enjoy stealing cars and killing hookers with all your friends.

I know I can't be the only person whose socks go missing in a shroud of mystery, but I'm determined to catch the sock-thieving gnomes in the act. While I have my suspicions, I can't quite prove it. Sure, I could drink a load of Red Bulls and never sleep, guarding my socks—but that's just crazy right? Luckily, I've found a way to set up my phone to catch the culprits.

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

After stealing the show at the HoloLens 2 launch and starring in Qualcomm's unveiling the Snapdragon XR2, holographic video conferencing app Spatial has landed a leading role in Magic Leap's second act with the enterprise segment.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Instagram is no stranger to stealing features from Snapchat. Stories, originally a Snapchat invention, feels more at home with Instagram today. Now, Instagram is attempting to repeat this feat with nametags, a way to quickly add new friends akin to Snapchat's Snapcodes.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Facebook just ratcheted up its ongoing augmented reality war against the competition by stealing away Google's director of product for AR, Nikhil Chandhok. In his new role, the executive will serve as Facebook's director of product on the company's Camera/AR team.

Waymo and Lyft have remained highly secretive about their driverless car programs, but may be forced to reveal a lot about their plans after a judge in a US federal court granted Uber's request to review documents about Waymo and Lyft's partnership.

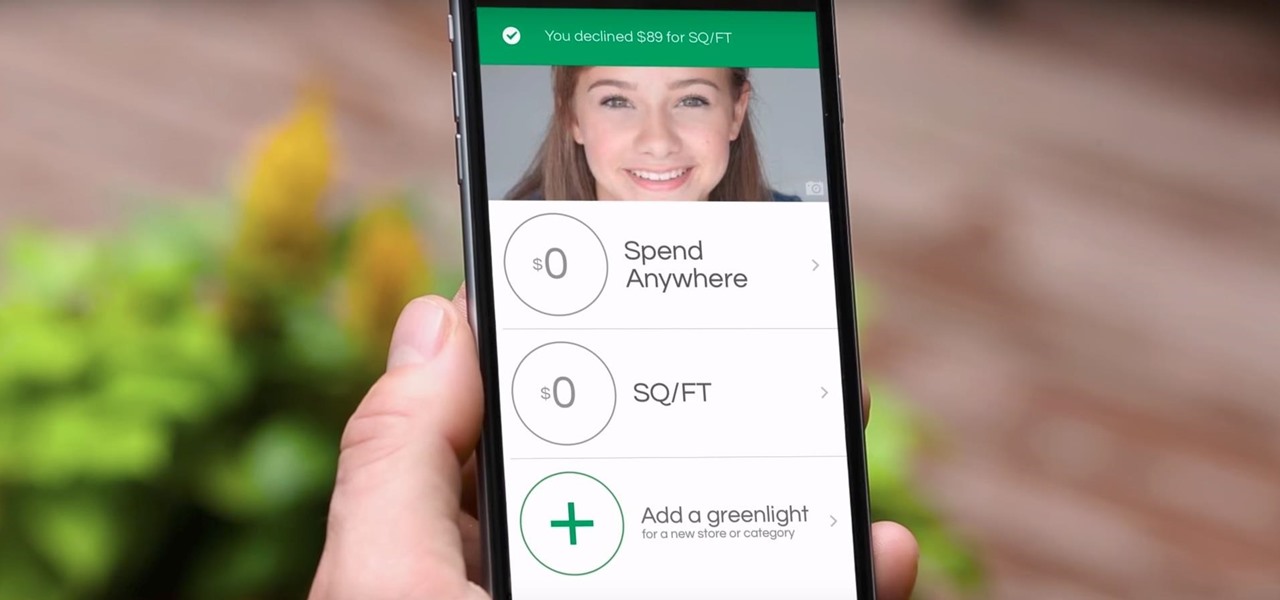
Parents rejoice, Apple Pay is making it much simpler for your kid to use Greenlight, the MasterCard for kids app.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

You were the chosen one, Snapchat! The new download numbers for the social media app show just how hard it will be to bring them back to the light after the rise of the Instagram empire.