
News: Industry Anxiously Awaits Trump DOT's Revisions to Driverless Guidelines
Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.


Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.
Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!
The laws and regulations in place in the US for driverless vehicles are a mess, but Republican congressional members say they can fix it.

Crochet hexagons are a great way to amp up your crocheting skills since they advance on your knowledge of how to crochet triangles by mandating that you crochet six triangles at once, all stitched together.
This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite focuses on how you can see the history of your defects, features, tasks, and incidents, as well as project wiki pages. For more information, as well as to get started using the history and audit trails features in Axosoft OnTime 2008, take a look.

Despite Ruling, Jack Lew Refuses to Call Health Care Mandate a Tax - ABC News.

More and more jurisdictions are mandating drivers use hands-free sets when they make or receive cell phone calls. This tutorial shows you how you can use a Bluetooth or hands-free headset to make and receive calls, or how to use the hands free functionality in some cars.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

From Salon.com "AB 32 mandates that California must reduce its greenhouse gas emissions to 1990 levels by the year 2020. But California's crazy government-by-initiative system means that just because a law has been passed by the California House and Senate and signed by the governor doesn't make it secure. On the ballot this November, voters will get their own chance to weigh in on AB 32 by deciding whether or not to pass Proposition 23, the misleadingly named "California Jobs Initiative."

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.

Making sure your home is working as energy efficient as possible is the first step in saving money on energy costs. Getting a Home Energy Audit will show you areas of you home that may need a little fixing or tweaking. Best of all, you can save hundreds to thousands of dollars a year with a Home Energy Audit!
See how to audit a live website for broken hyperlinks in a matter of minutes. With Xenu's Link Sleuth tool, it's easy. So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just over two minutes' time. For the specifics, and to get started checking your own website for broken links, just watch this handy how-to.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.
In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more
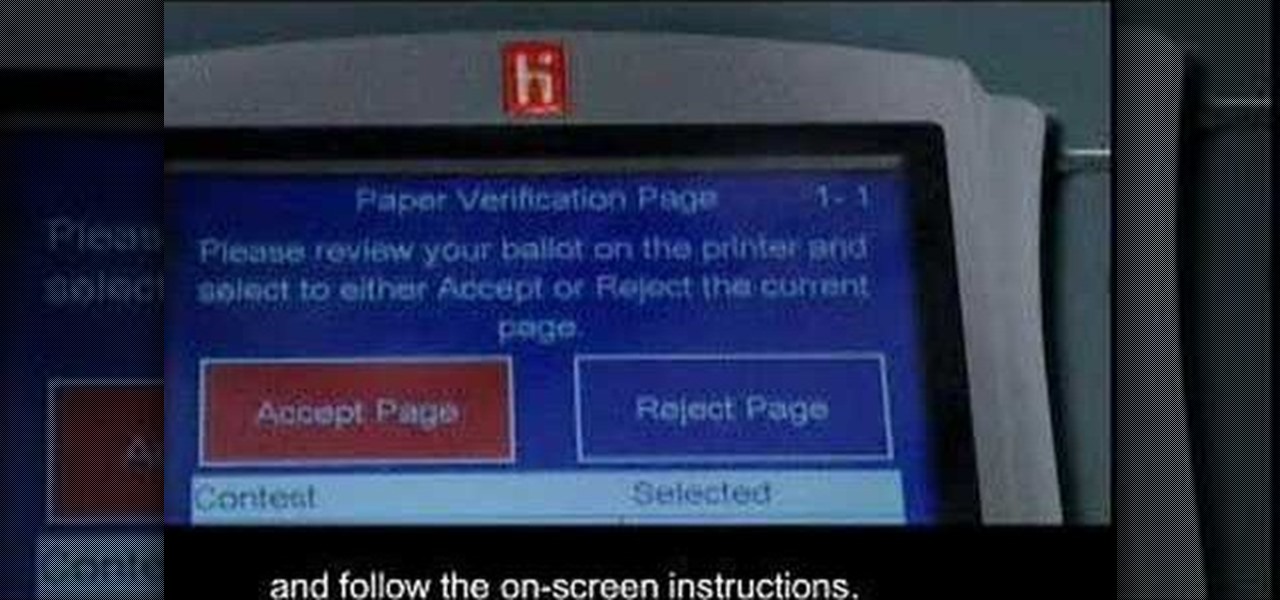
This is an instructional video on how to vote using the popular eSlate electronic voting machine with VVPAT (voter verifiable paper audit trail). eSlate is an electronic voting device made and distributed by Hart InterCivic.

Sunkissed, glowy skin, bright eyes, and flushed cheeks never go out of style, and during the summer they're practically makeup mandates. Exuberant skin looks youthful and will turn heads and make jaws drop in awe as you careen down the street.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Ron Paul’s bill to audit the Federal Reserve has passed overwhelmingly in the House. It cleared a suspension of House ruled requiring a two-thirds vote. The final vote was 327 to 98 and all but one Republican and 89 Democrats voted yes. The bill had more than 274 cosponsors and faced strong opposition by Democrats and the Federal Reserve » Ron Paul’s Audit the Fed Bill Overwhelmingly Passes in the House.
I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.
THC-Hydra is a remote dictionary attack tool from The Hacker?s Choice group. It?s a well made tool that supports a lot of protocols and options. The following protocols are supported: TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, RSH, RLOGIN, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, LDAP2, Cisco AAA. Audit remote password using THC-Hydra.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

I'm sure a lot of people have been following the news and depending on your position on the issue, you might have been happy or dissappointed about the fact that Obamacare has been OK'd by Congress. Let's see what this really means to us.

In this tutorial, we learn how to optimize a PDF document in Adobe Acrobat 9 Pro. This will adjust the size of the PDF to better adjust your need and work flow. Fire, go to file and then go to properties, then you will be able to see what size the file is. If you would like to change this, go to the PDF Optimizer, which has an "audit space usage" button. From here, you can change the compatibility level and also change the compression and the color bitmap resolution. After you are done editin...

Are your electricity and water bills comparable with that of Raging Waters? Then it's probably the right time to consider how to save on your energy and water bill by taking small steps like assessing where you're at in your home, having an energy audit, and eliminate leaky faucets.
This video is about burning a DVD using Nero. On menu bar choose create/edit. Select audit, edit and capture video in dialog box. Nero vision 5 appears. Go to DVD dialog box. Choose where you will import video from. Drag video into open screen. For best quality keep video size to 1 GB. You can add titles, edit or create chapters. Click next. Choose a category which are choices of how the video will appear. You can customize text and audio in this screen. Click next and view the final product....

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

The AFL-CIO's Transportation Trades Division, which represents 32 unions in the US, has successfully lobbied for the removal of 10,000-lb. and heavier commercial trucks from provisions in bills expected to pass that could allow for millions of driverless vehicles on public roads and streets, Bloomberg News reported.

Call Your State's Nurse Aide Registries for School Inquiries

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.
Crafting is someting you can do in Star Trek Online after you complete the Scientific Mandate mission at level 4. Once you do, you'll gain the ability to craft items. This tutorial shows you what to do once you acquire this ability.

In Judaism, men customarily cover their heads with a skullcap as a sign of humility before God, though it is not mandated by law. In Hebrew, it is called a kippah; in Yiddish, a yarmulke. In Europe, the custom dates to the end of the 16th century. Learn how to wear a kippah (yarmulke) with this Howcast guide.

Engineer Anthony Levandowski has officially been kicked off Uber's driverless program by a judge as the company's legal war with Waymo continues.

Okay, so this doesn't exactly teach you how to audit as a Scientologist... but I think it is the closest to an explanation we are going to get. So, listen up & try to learn.

News in a nutshell: Iran Boosting enrichment efforts

Earlier this month, AT&T quietly introduced a new "Mobility Administrative Fee" which levies a $0.61 monthly charge to all postpaid contracts. While it's a seemingly small amount on an individual basis adding up to $7.32 per year, with its huge customer base, AT&T stands to make around half a billion from the tight-lipped move. AT&T has stated that the fee will "help cover certain expenses, such as interconnection and cell site rents and maintenance" that's consistent with other phone carrier...
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.