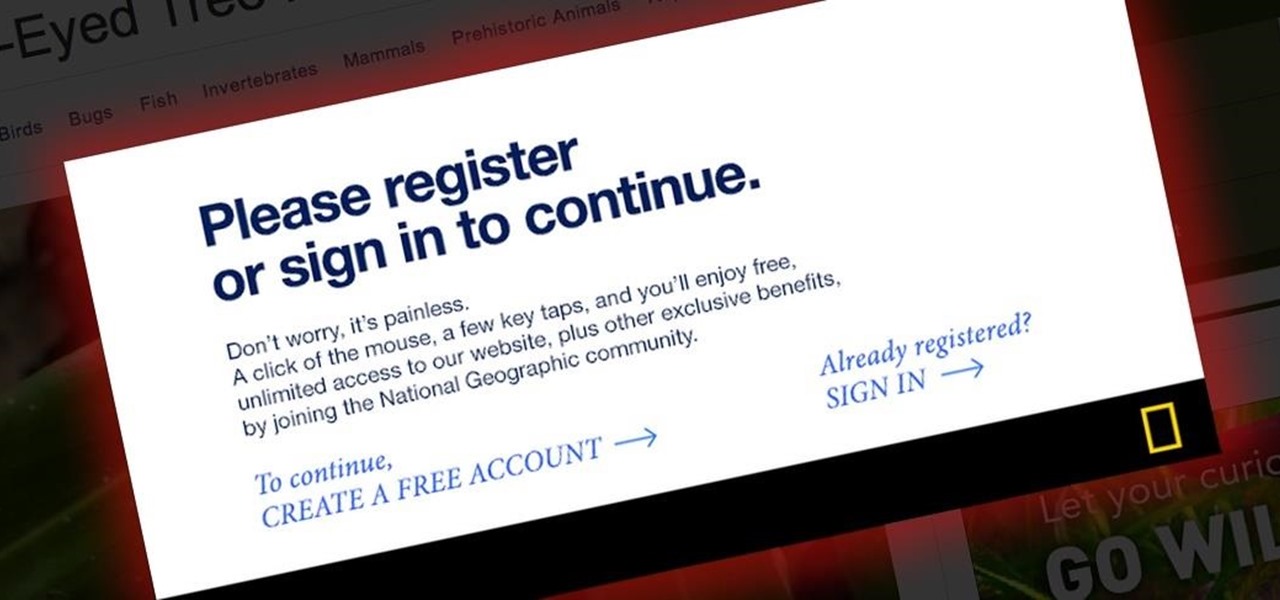
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Windows 8 comes with a bunch of new features, and none may be cooler than the new Picture Password option. If you're tired of the old lock screen and login options, or don't want to remember any more passwords, than you'll like this great new addition to Windows.

We all hate spam. It is a waste of time and very troublesome. So here is a way i found to avoid spam. I am not responsible for anything that happens. M'Kay?

Notaries can make $75-125 an hour for their services. All it takes is one course and a small fee to get a license and you will be on your way to raking in the extra cash. Being a notary is a great boost to your resume and your pocketbook, so why not give it a try?

So this one is going to be a prank on hundreds, maybe thousands of people. What you're going to do is advertise a Jackass autograph signing somewhere. Put up flyers or posts on Facebook or something like that to get people to come. Have a long ass table set up with a bunch of chairs so people think its a seat for each member of Jackass. Make people wait a little telling them the Jackass crew are running a little late. Then after a little while you can announce that Jackass has arrived and the...

Learning American Sign Language is a great way to communicate with the hearing impaired, particularly if you have deaf friends and family. Learn how to sign words from around the home in sign language with tips from a deaf signing expert in this free sign language video series.

Learning American Sign Language is a great way to communicate with deaf people and the hearing impaired. Learn the signs for several foods with tips from a deaf signing expert in this free sign language video series.

A great way for your child to learn sign language. American Sign Language(ASL) is easy with Signing Time.

Teach your toddler how to sign "dog" in American Sign Language (ASL). Learning is fun with Signing Time.

Signing Time teaches toddlers how to sign "water" using ASL. A great introduction to sign language for children.

Learn how to sign "eat" from Signing Time. Teach your toddlers and children how to use sign language.

One of the fun and special traditions enjoyed and shared by the Deaf Community is signing stories using number or alphabet hand shapes. In these stories, various hand shapes do not stand for the numbers and letters themselves, but are used as signs or gestures to convey concepts. They are signed in alphabetical or numerical order, and used in amazing ways to sign or act out a story.

One of the fun and special traditions enjoyed and shared by the deaf community is signing stories using number or alphabet hand shapes. In these stories, various hand shapes do not stand for the numbers and letters themselves, but are used as signs or gestures to convey concepts. They are signed in alphabetical or numerical order, and used in amazing ways to sign or act out a story.

Learn how to sign Ball using American Sign Language. Signing Time teaches toddlers how to sign in a fun and engaging way.

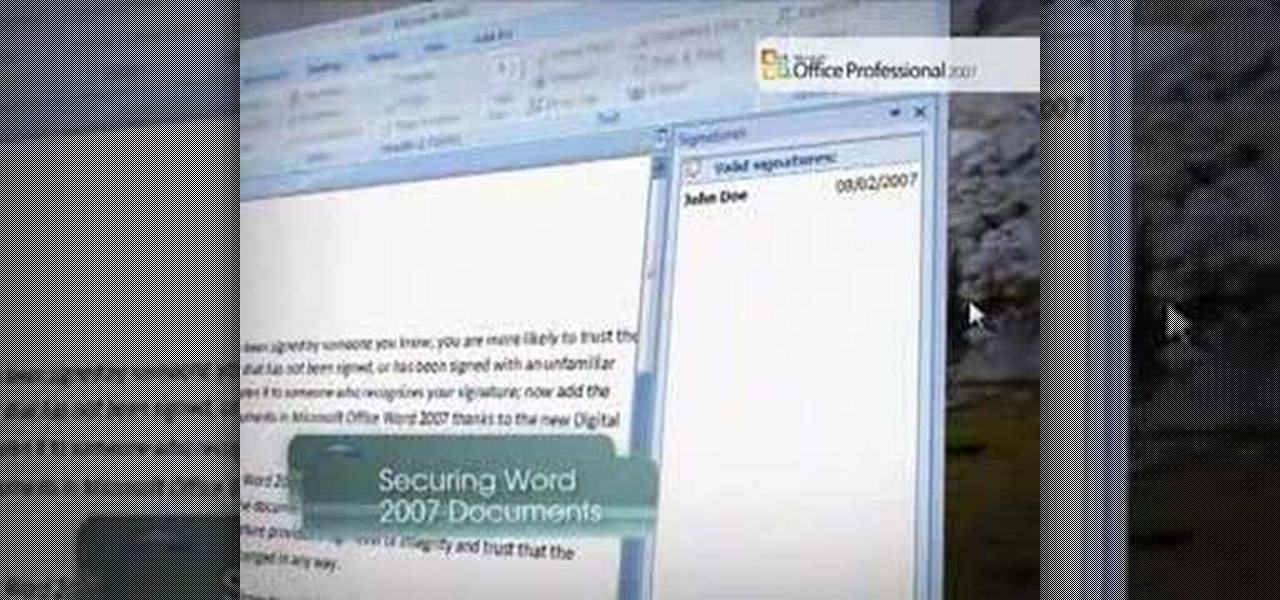
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

Signing into Windows Live from a HTC HD7 is easy! This clip will teach you how. Whether you're the proud owner of an HTC HD7 Windows Phone 7 smartphone or are merely toying with the idea of picking one up in the near future, you're sure to be well served by this official video guide from the folks at T-Mobile.

Mystery shopping is a great way to make money on the side while getting a chance to shop, check out new stores and restaurants, and over all improve the quality of service at these locations. The key is to not let them know that you are there evaluating them. If you think you've got a knack for blending in, then check out this video. In it you will learn the process of signing up and becoming a secret shopper, what to expect, and some tips for how to carry out your jobs.

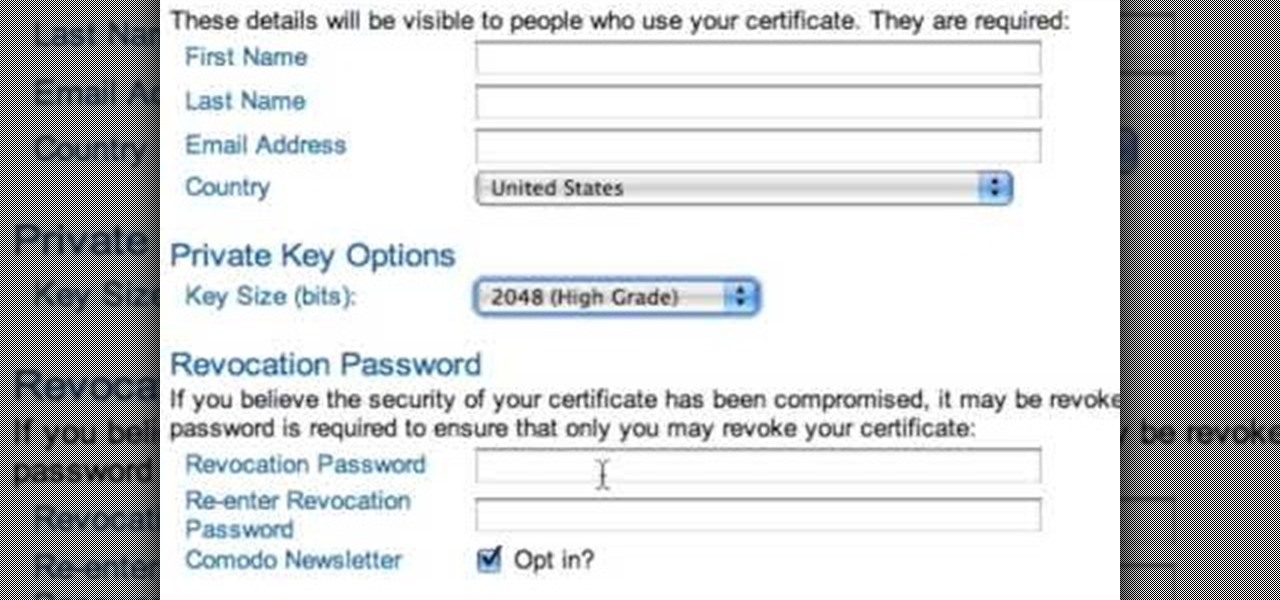
The only people who should read your emails are you and your intended recipients. Protect your privacy with this simple crytography guide, which shows how to obtain a free certificate for signing and encrypting email messages, how to download and install the certificate on Mac OS X 10.5, and how to use the newly installed certificate in Apple Mail.

Want to know how to set PDFs up so that they can be digitally signed? In this Adobe acrobat tutorial you'll see how to set up a PDF to accept a digital signature. You all also see how to create your own digital signature for signing and a strategy to work with your clients so that you know who is signing those documents.

Sign language for infants helps accelerate language development and is also a great way to spend time and bond with your baby. Learn how signing can help you and your child and then learn some easy to do signs that you can practice with your baby at home. Just watch this parenting how-to video.

The long tease that is the release of Minecraft Earth continues, this time with an opportunity to start playing what might be one of the hottest augmented reality games ever, before the general public.

Now that Apple's latest Worldwide Developer's Conference (WWDC) is over, you can sign up for the public beta version of iOS 9 for your iPad or iPhone. For the first time in their history, Apple made a beta version of their mobile OS available to the general public just a few months ago, in the form of iOS 8.3, and they'll continue that trend for the newest build.

While the App Store is filled with news aggregators, Apple News is a solid choice when it comes to keeping up with current events. Apple recently made it easier than ever to stay informed, thanks to a daily newsletter sent straight to your inbox. The problem? It's unclear how to sign up for this newsletter, and it's equally unclear how to unsubscribe.

Update: August 1, 2014 Earlier today, President Obama signed into law the Unlocking Consumer Choice and Wireless Competition Act, making the act of unlocking your unsubsidized cell phone 100% legal.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

Anyone who's worked in web development or graphic design long enough knows that one of the most difficult job elements is finding high-quality stock images that aren't tangled in red tape. Whether you're trying to build a website, ad campaign, or email newsletter, you need to have reliable graphics that are easy to find and use across multiple platforms.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

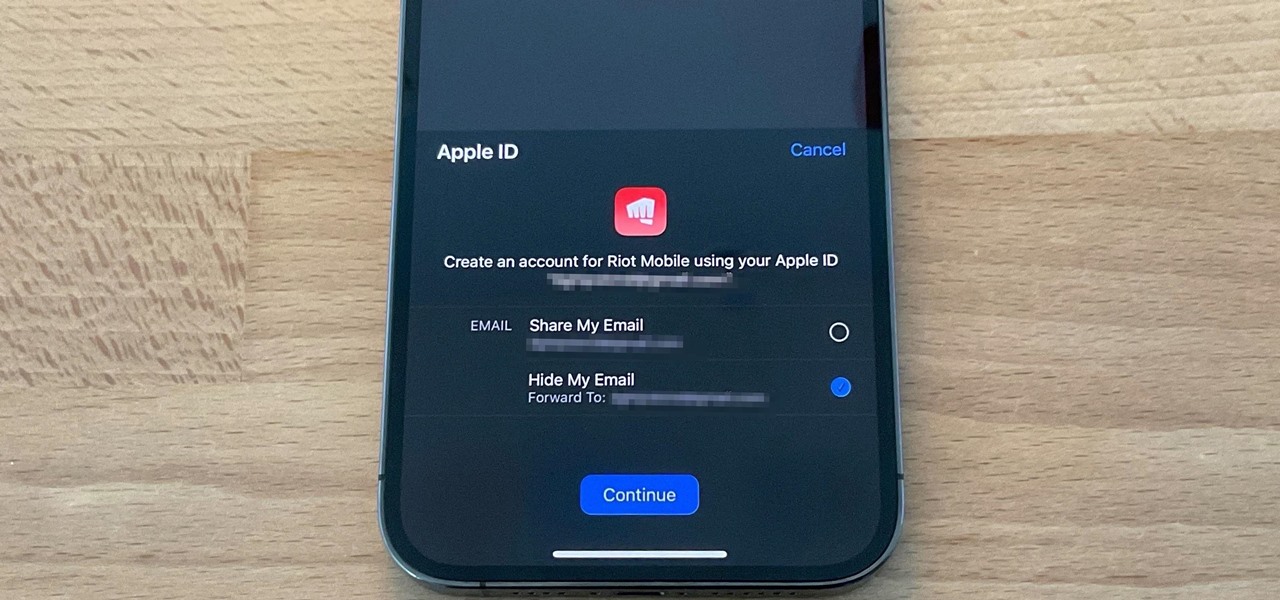
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

Ever wished you could check your cell's voicemail online? You can, for free, with the YouMail web application. In this tutorial, you'll find step-by-step instructions for signing up the the YouMail service. For more, or to get started signing up for you own YouMail account, take a look! Sign up for, and use, YouMail visual voicemail.
In what has become a rare scene in Washington, a group of bipartisan lawmakers joined President Barack Obama today at the White House for his signing of the Stop on Congressional Knowledge Act.
President Barack Obama and Afghan President Hamid Karzai signed an agreement that provides a framework for a lasting U.S. commitment to Afghanistan after the long and unpopular war comes to an end.

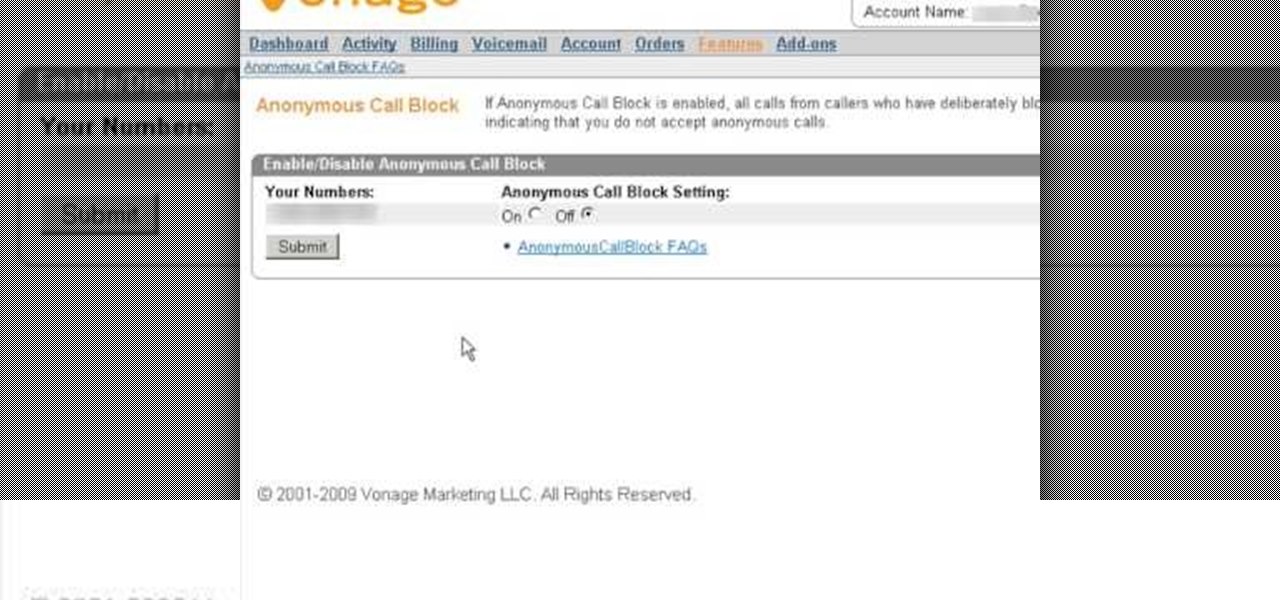
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

Ever wish you could automatically forward your Yahoo! webmail to Gmail without signing up for their premium email service? It's easy. So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to auto-forwarding mail from your Yahoo! Mail account with signing up for Yahoo! Plus, watch this clever guide.

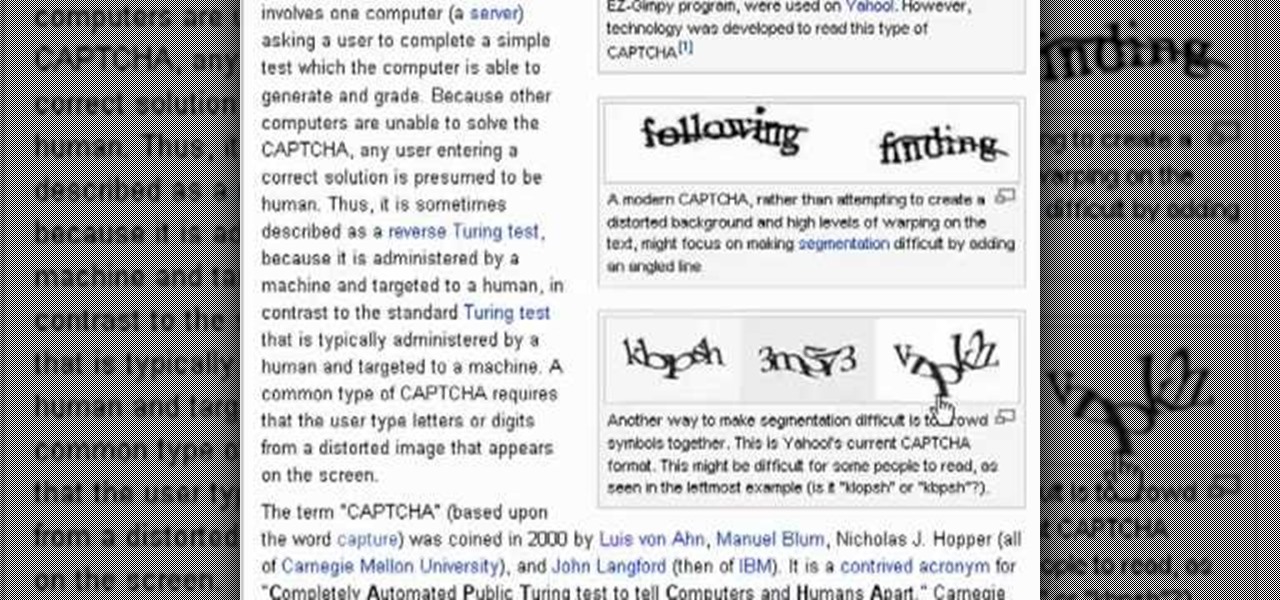
Even if you don't know what CAPTCHA stands for, you've more than likely run into them while browsing the Internet. It is actually a test to differentiate between humans and computers. In this clip from the folks at Butterscotch, you'll learn how to respond to CAPTCHA challenges when, for example, signing up for a website. For more information, including detailed, step-by-step instructions, and to get started asserting your own humanity, watch this home-computing how-to.

Don't sign any termination papers until you're sure you've made the best deal you can. You Will Need

If you've ever heard of the Yes Men, then you know about some of their most famous and awesome pranks. These guys have done so much and have tricked so many people in the past decade. From tricking people to signing petitions about allowing Global Warming to occur to passing out over 80,000 fake New York Times papers, these guys are good.

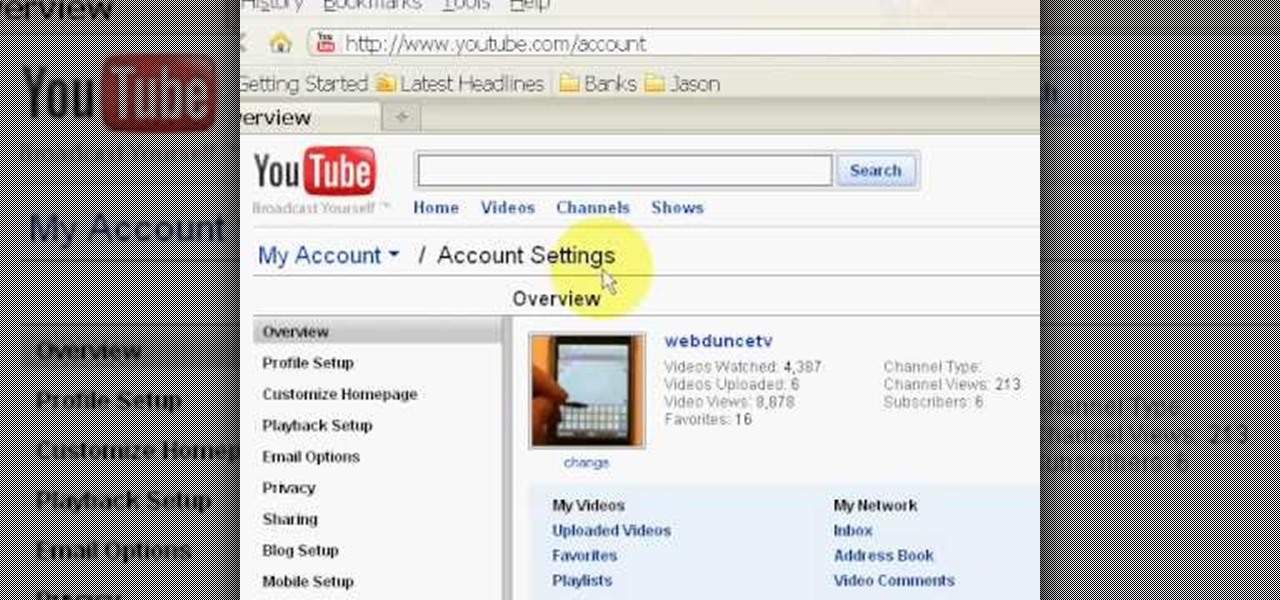
Want to change your YouTube Channel type? YouTube user webduncetv shows you how. After signing into your YouTube account hover your mouse over user name and click on the word "Account" from the drop down list.