If someone violates a protective order, there are — the remedy would be the police would be involved. You'll get arrested. So, basically, a protective order is usually good for two years, and it has all the specific things you cannot do. For instance, you can't go by that person's — within 200 feet of them or their residence or their employer. So it has some very specific things. A restraining order is different. It's a standard thing that's given that's a mutual thing where it just says be n...

Great video by Southwest Yard & Garden. tutorial on how to identify garden pests on your plants & shrubs. Went into detail on the Salvia plants - always be careful spittle bugs, they produce spittle commonly on Salvia plants. Whiteflies and aphids are known to take residence in Ash trees. Aphids commonly take on the look of mildew. Ways to manage moths for apples, you can use insecticide spray but be conservative. Took a look at signs of Cochineal Scale on a Prickly Pear. Went over ways to ta...

In this tutorial, we learn how to get a Canadian Permanent Resident card. The residence card will identify you and your name as a resident of Canada. If you do not have a card when entering Canada, you have to obtain a new PR card within 30 days and have a new Canadian address. If you need to replace or renew your PR card, you must file an application as soon as you lose it. This information will need personal information and residency information. The fee is 50 Canadian dollars. If you need ...

In this six minute tutorial the host and keyboard player for the band "Brazilian Girls," Didi Gutman, shows viewers how to play the keyboard in the song titled "Reason." Throughout the video, Didi Gutman shows various methods and techniques that are used for the style of keyboard that he plays. Filmed in Gutman's place of residence in Brooklyn, New York, Gutman also talks briefly about how the band got started and how he first got involved with playing the keyboard. The video also shows him r...

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

On Friday, at IFA 2018 in Berlin, Samsung invited attendees into the residence of Family Guy's Griffin family to learn all about its "smart home" products via augmented reality.

Augmented reality allows for all kinds of experiences to happen just about anywhere, and that creates some incredible potential for entertainment. While games like Pokémon GO take you out into the world, one crowd-funded game wants to keep you inside—to scare the crap out of you in your own home.

Watch how the F5 Networks BIG-IP Edge Client solution gets you connected automatically when you boot/start up your computer along with seeing the browser based version of the F5 BIG-IP Edge Gateway. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Learn how to use the BIG-IP Edge Client and its Smart Connect, Location Awareness, Customization, Deployment features. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

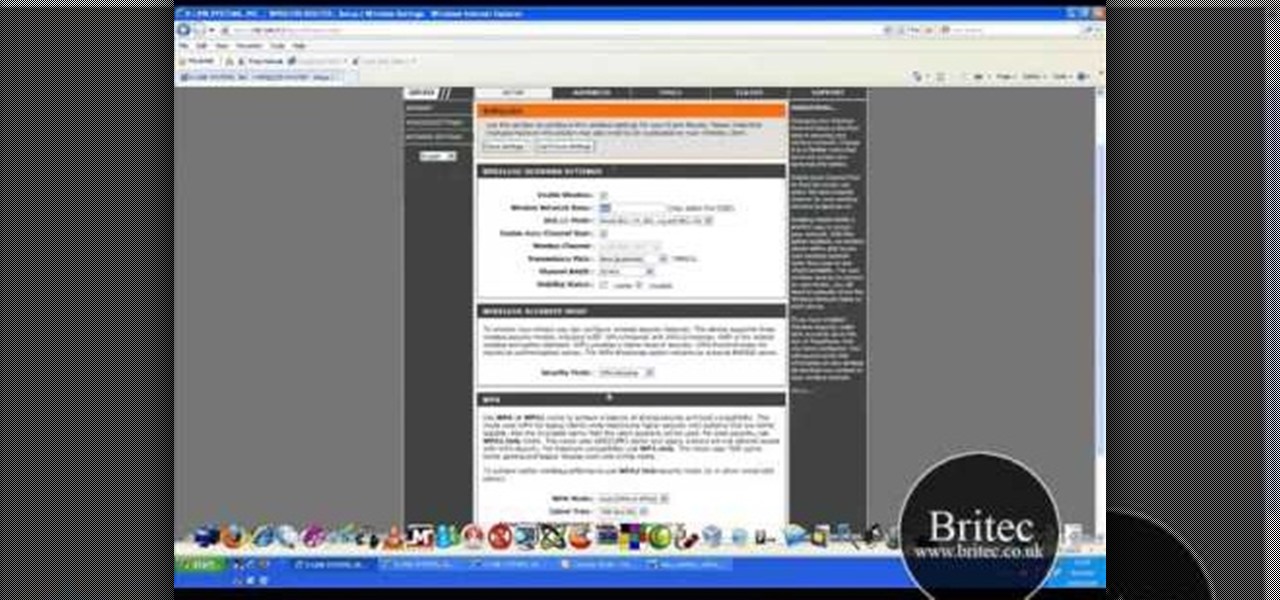
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

The purpose of this video is to show how to become a permanent resident in Canada. Some programs are federal and some are for Quebec. The first program is the skilled worker program. The applicant is accessed under a point system and is awarded points for education level, knowledge of English or French, work experience, age, confirmed job offer, and adaptability and you must have sufficient proof of funds. The next program is Family Class Sponsorship. A citizen or permanent resident can spons...

If you’re selling your home, you’ll need to know its square footage. Why pay a professional when you can measure it yourself?

Burglary is common, but is also quite preventable with these tactics. You Will Need

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

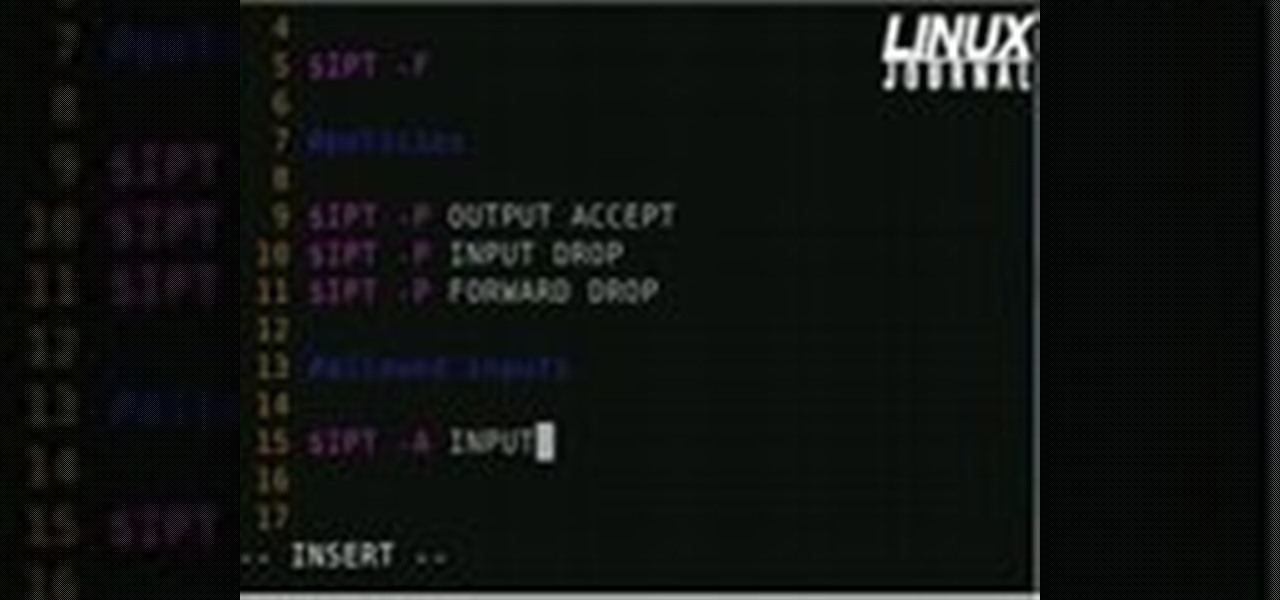
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

This clip discusses how authorization roles work and their role in the security of the latest release of the F5 Networks Management Pack suite. It also touches on the creation and use of user roles within Operations Manager console and how to apply the authorization tasks to those roles. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with F5 Networks Management Pack suite, you're sure to benefit fro...

In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to use the PCI compliance reporting functionality within BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

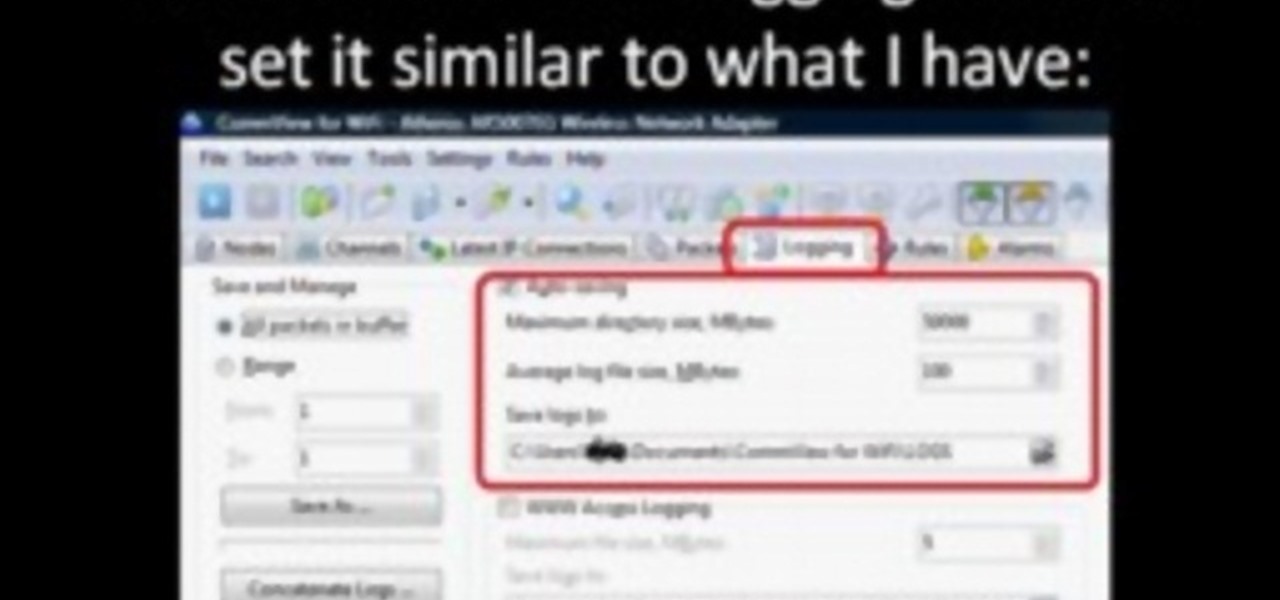
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

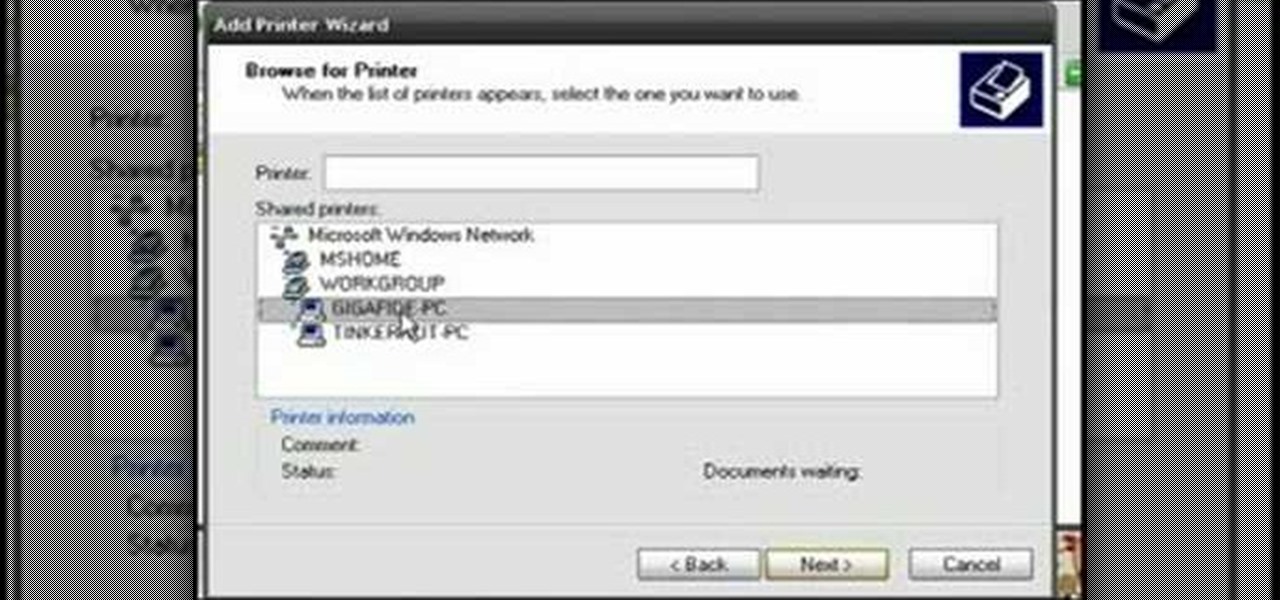
Odds are you have more computers on your network than printers. This video lays out the steps for sharing a printer over a network. This tutorial assumes that the printer is installed on another computer and not connected directly to the network. Take a look!

No wireless router? There is a way to network your computers by using your existing power-line. This CNET video will show you how to set up a power-line network - it's not as sexy as a wireless network, but it's easy and reliable!

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

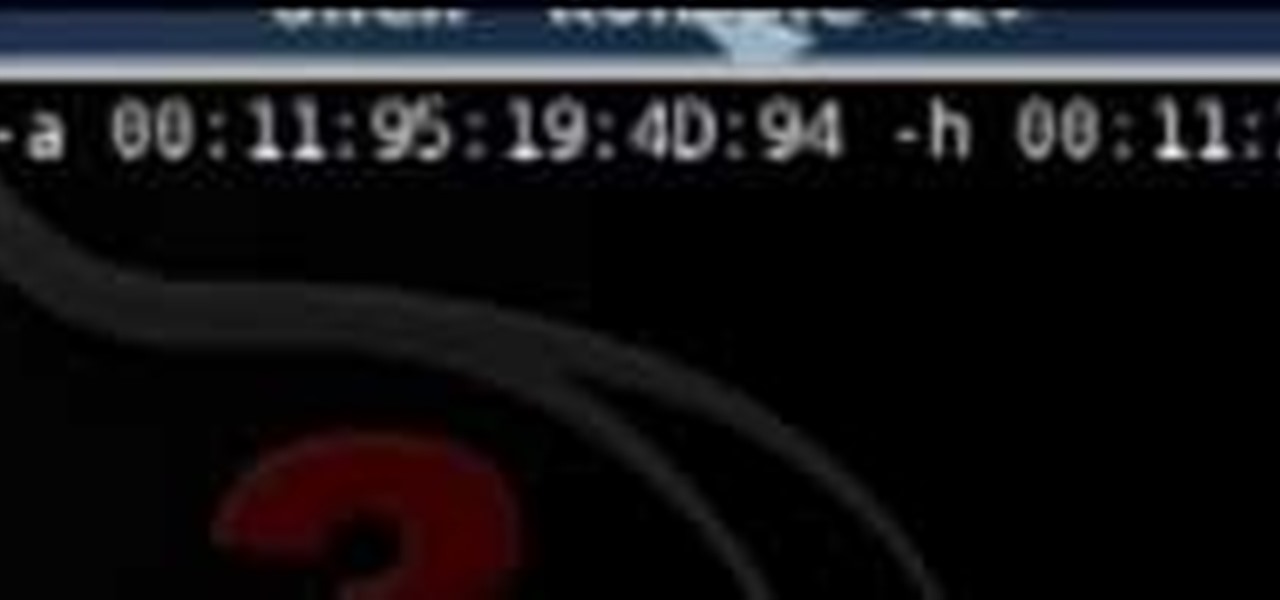
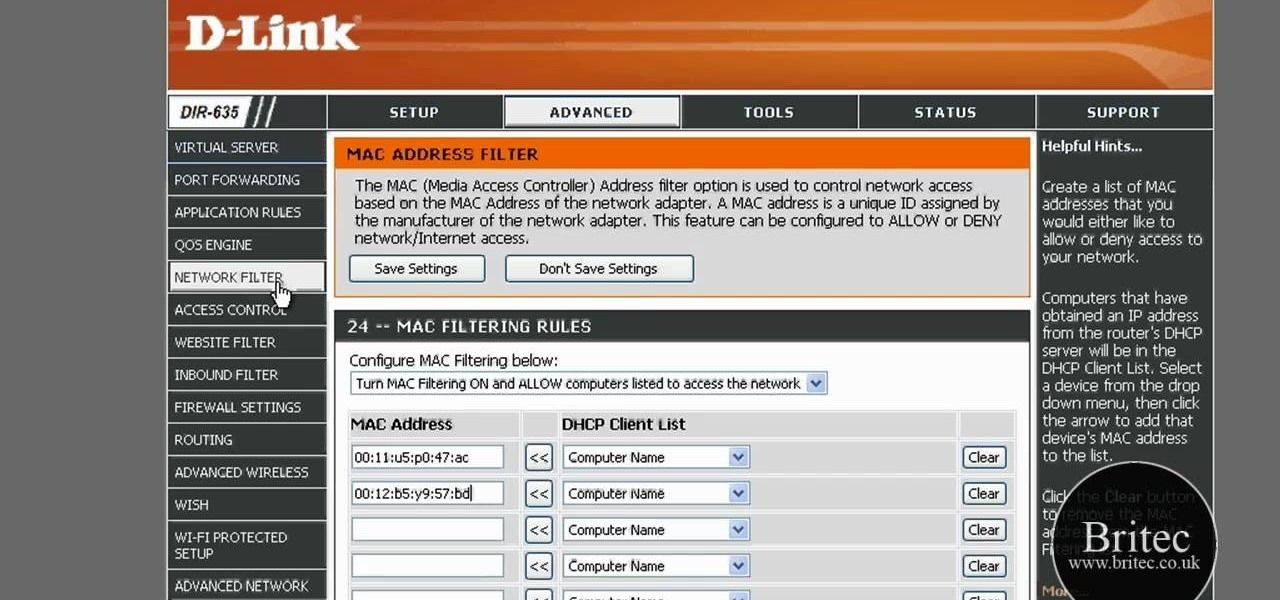
The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.

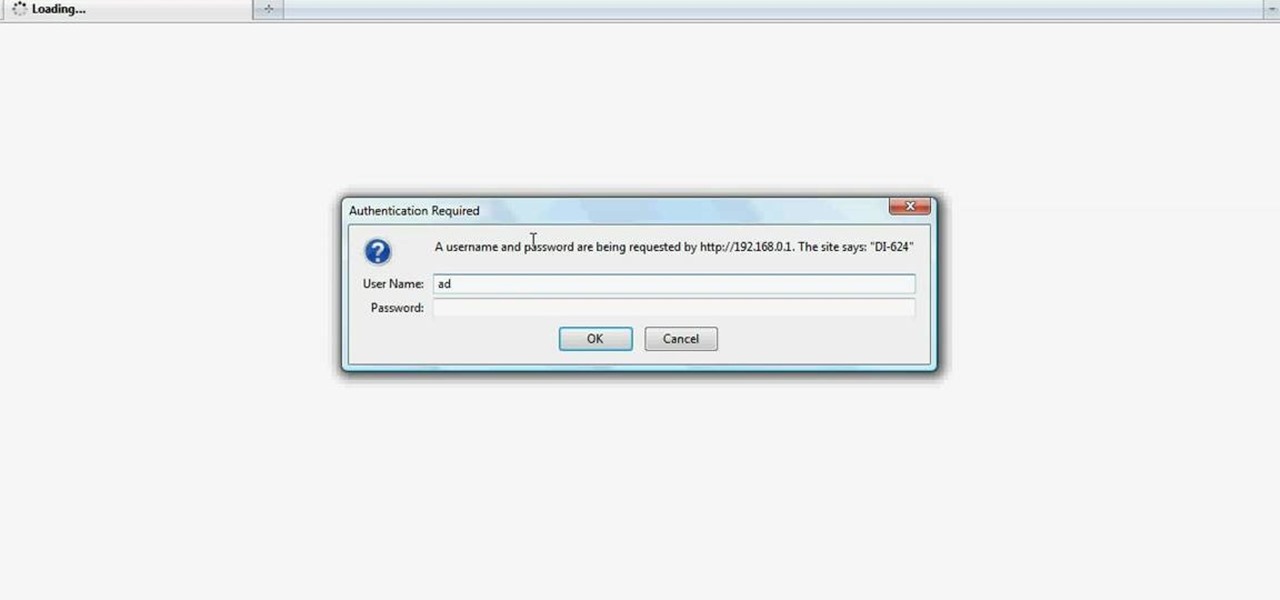
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

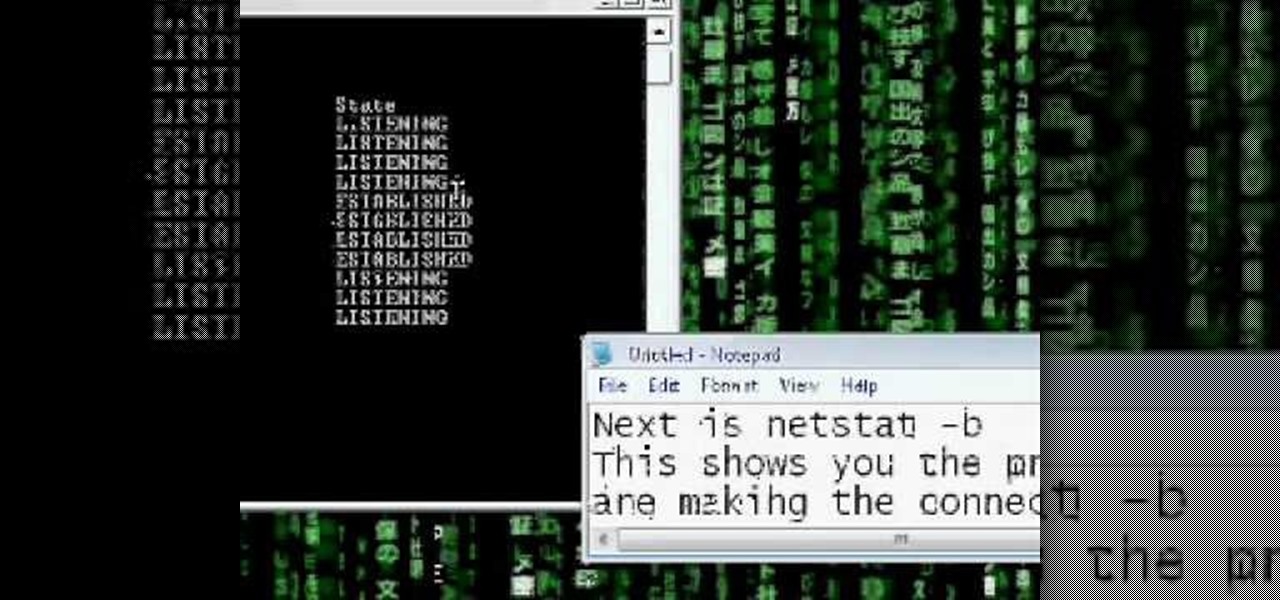
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.