Is there something strange in your neighborhood? Don't bother with a phone call, just watch this video and learn how to build your own EM pump. An EM pump improves EVps and attract paranormal entities. If you are going ghost hunting, you need an EM pump.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this introductory video, Alex James will show you how to build a simple Entity Data Model in a short amount of time.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this introductory video Diego Vega will show you how to use the Entity Data Source in an ASP.NET Application.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Take a look at this instructional video and learn about the basics and functions of components in Google SketchUp. The difference between components and groups being that groups have no relation to each other. Any of copy of a group is a completely separate entity. This tutorial covers components versus groups, how to edit components, and the component browser.
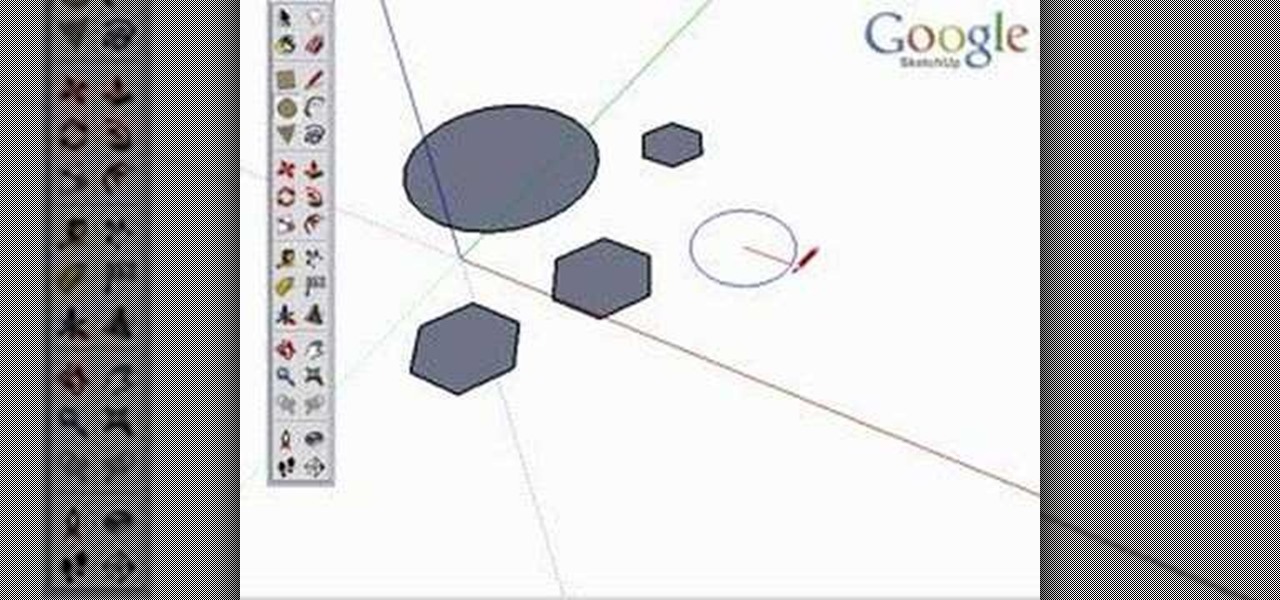
Take a look at this instructional video and learn how to use the circle and polygon tools in Google SketchUp. This tutorial covers drawing a circle or polygon, changing the number of sides of a circle or polygon, and viewing additional information through the entity info dialog box.

This video tutorial will talk about html formatting on YouTube. specifically how to make your comments bold, italicized (italics), underlined, or all of the above. It also explains html entities.

One of the first daunting tasks that confronts most aspiring gamemakers is a simple one: making a character jump and land predictably. If you're gotten to this point and wonder what to do, you're in the right place. This video will teach you how to use Actionscript 3 in Flash CS4 to make your character jump like Mario (or Sonic if you prefer) making your game much closer to being the playable, fun entity that it will soon be.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 677th installment in their series of digital spreadsheet magic tricks, you'll learn how to average the last three scores eneterd for any Player using the functions: AVERAGE, IF, ROW, COUNTIF, MIN, LARGE.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

The legal drama framing the closure of Meta Company continues even after the company's assets have been sold to a new owner.

In the latest update to the ongoing Meta Company patent infringement case, the court has responded to a request from the defendants, and the answer isn't good news.

The personal computer is a strange and powerful entity, capable of bringing great joy. Just as often, you probably want to chuck the damn thing at the wall because it doesn't work right. If you want to pull a prank on a friend that will really upset them, messing with their computer is one of the best ways to do it. This hilarious video will show you how to do three great PC pranks quickly and easily, including changing the contrast on the monitor and pretending to edit websites using Javascr...

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Successful public speaking is a product of numerous considerations. Become a successful public speaker with tips from an award-winning speaker in this free communication video series.

Write a great speech! Get tips for selecting the right words for your public speaking occasion in this free video series from a professional public speaker.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

As far as your audience is concerned, there are few things less magical than a card trick seen a dozen or more times. As such, as a magician, it's important that you build a strong repertory of tricks to maintain your public's interest. And what better place to start than the "flying" card trick outlined in this free video magic lesson.

How many women have heard "You can't do that here!" when trying to nurse in a public place? Parents TV's Anne Ebeling explores the issue of public breastfeeding from etiquette to laws that protect nursing mothers.

Prior to this year, Time primarily relied on image markers in the magazine to trigger its special augmented reality features

Apple released the fourth public beta for iOS 12 to public beta testers on Tuesday, July 31, just one day after the company seeded the fifth developer beta to eligible users. Both releases are surprising, as Apple had appeared to stick to a two-week release schedule for the iOS 12 beta season, and these updates both came one day earlier than expected.

The augmented reality cloud and multi-user experiences are shaping up to be one of the hotter areas of augmented reality, and now Google is the latest entity to back these emerging branches of AR.

Magic Leap is no stranger to hype and speculative advancement—when their name pops up in the news, all focus turns to them. And the company is making news again this week, with the knowledge of an acquisition of a startup founded by former Apple employees, and by hiring animators from an Emmy and Oscar award-winning studio.

It appears a privacy lawsuit that began five years ago is about to come to an end, and you might get some money out of it.

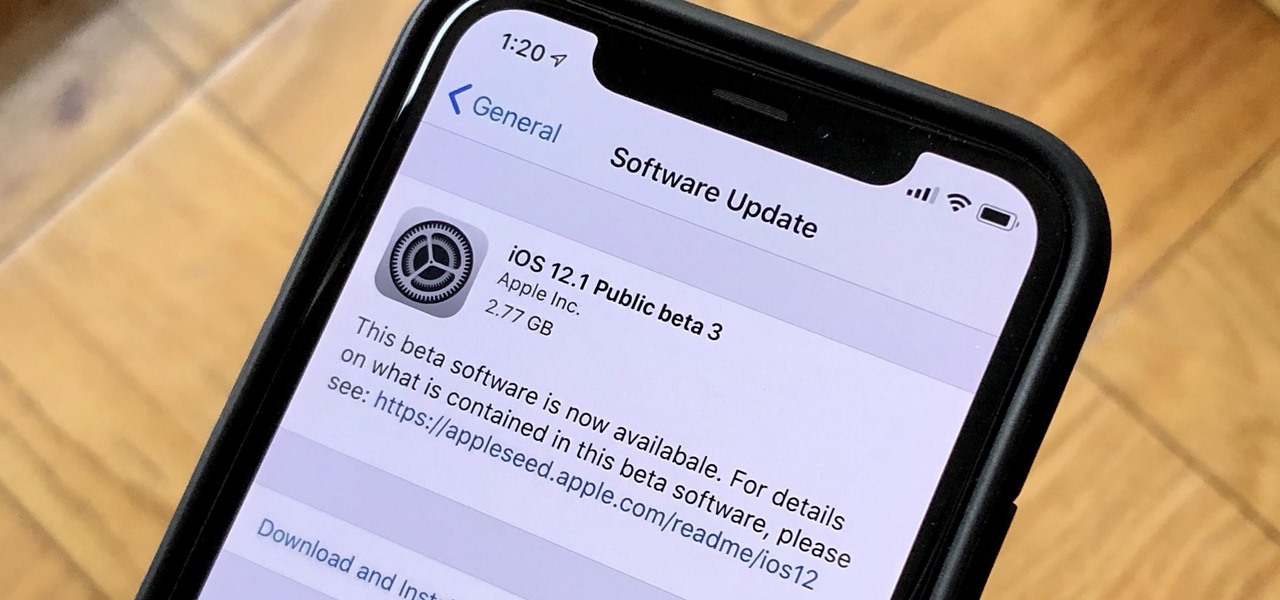
Apple released the third public beta for iOS 12.1 to software testers on Tuesday, Oct. 9, and there's not a whole lot to be excited about. The update came just hours after Apple released iOS 12.1 dev beta 3 to registered app developers, signaling a return to the traditional Tuesday release schedule for iOS betas. At least, for now.

Toddlers can be difficult to manage in a public setting. This mother of three shows how you can get even a very young child to behave and have good manners when you're in a place like a restaurant or other public place.

Apple released the first public beta for iOS 13.5.5 on Monday, June 1. The update comes just hours after Apple seeded developers their first 13.5.5 beta, as well as the public release of iOS 13.5.1, which introduced a patch for the Unc0ver jailbreak exploit. It was a big day for iOS software.

The great iOS beta hiatus is over. After 28 days of waiting, Apple finally seeded the second developer beta for iOS 13.3.1 Tuesday, Jan. 14. Lucky for us public beta testers, we didn't need to wait long to get our version of the beta, as Apple just released 13.3.1 public beta 2.

Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.

When you sign up to be a public tester for Apple's iOS, you get early access to features most users won't see for months. But you aren't the first — developers get priority when it comes to beta releases, made clear when they received 13.2 beta 3 while public testers were still on beta 2. Well, we public testers finally caught up, after Apple released iOS 13.2 public beta 3 Wednesday, Oct. 16.

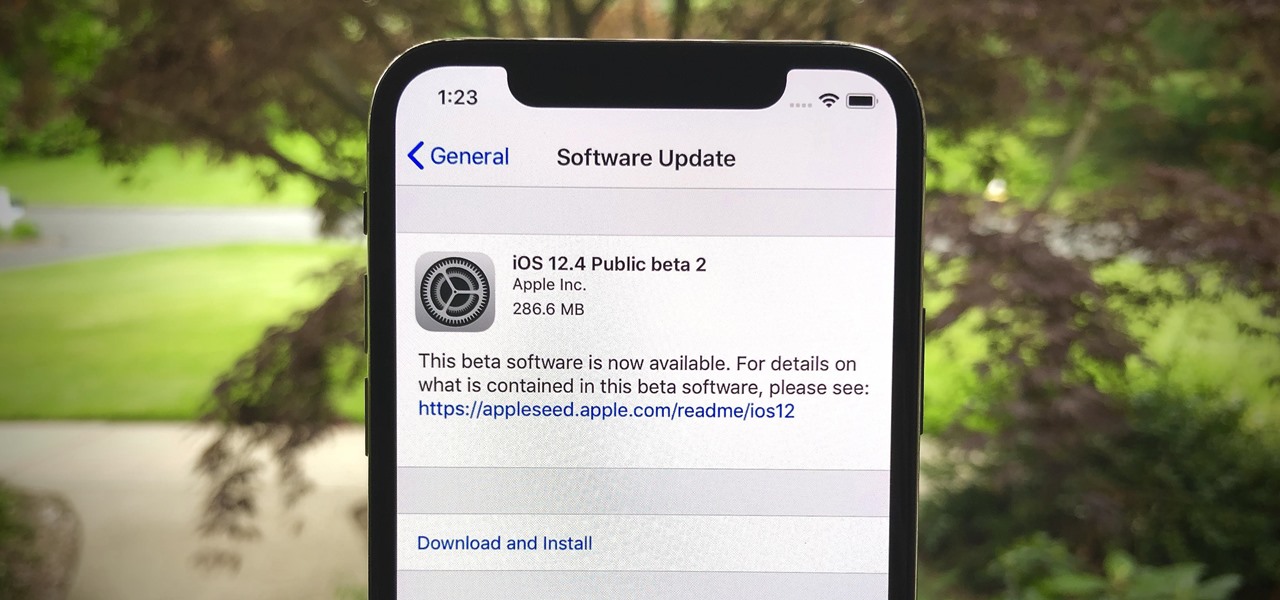
Public beta testers, you're in luck. Apple just released the second iOS 12.4 public beta today, May 20. The update comes five days after the release of the first developer beta for iOS 12.4 and seven days after the release of iOS 12.3. Public beta 2 and dev beta 2 were both released at the same time, something that doesn't happen often.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

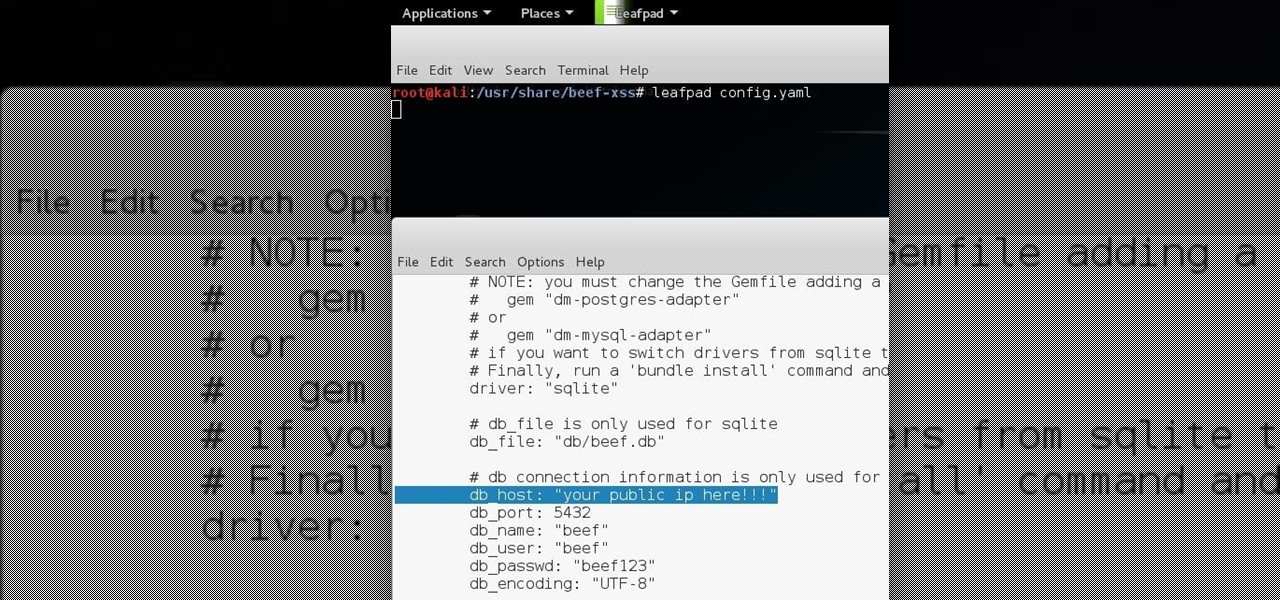
Hello all Just thought id share how ive managed to get beef working over the internet.

Here's how to find and use Free Public Domain Movies and old TV commercials in your work. Also in this episode, a few inexpensive utilities that will convert video formats so they are ready for editing in your editing program of choice.

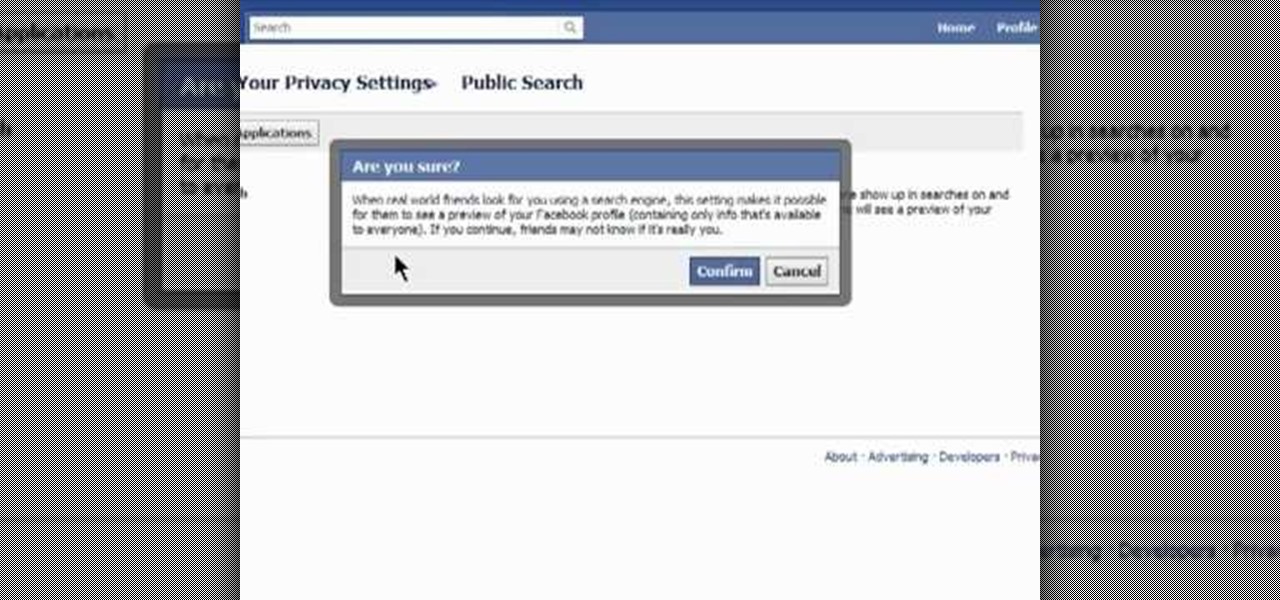
Looking for a guide on how to secure your public Facebook profile? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.