While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.
This video will show you how to protect Google Chrome password from others. If you don't protect them from others anybody using your PC could access all your account detail. Now you can realize this is dangerous. Watch the video and employ the technique in your PC.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

This video will show you how to protect and clean the plastic fenders on your ATV or dirt bike. This is very easy to do and only takes a few minutes.

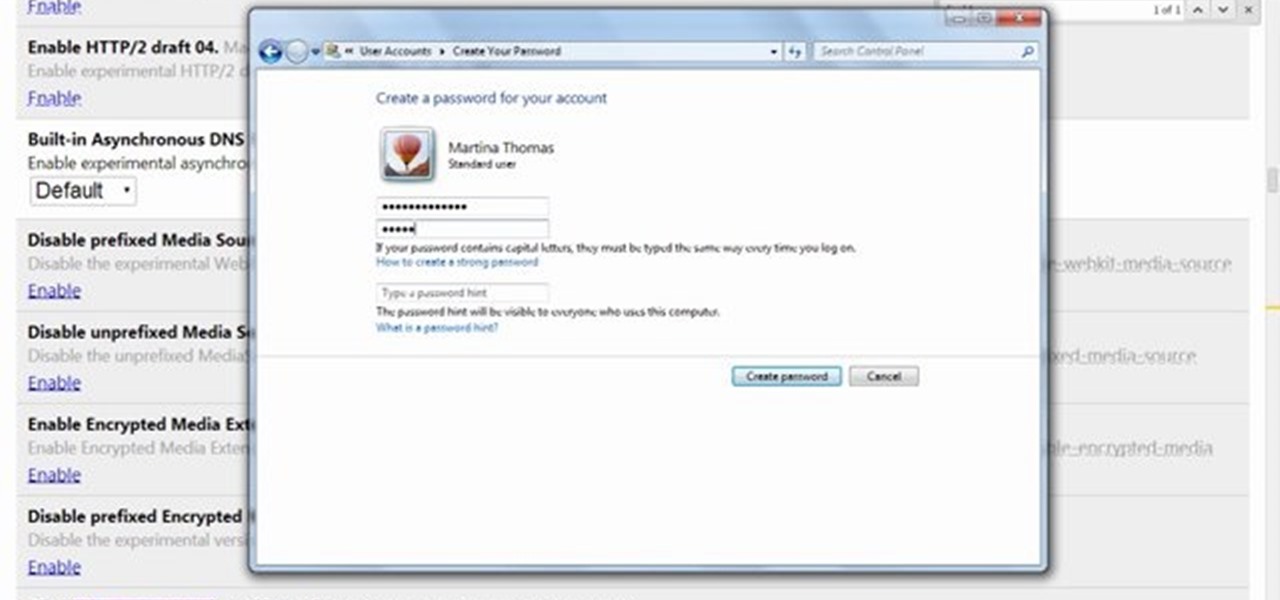
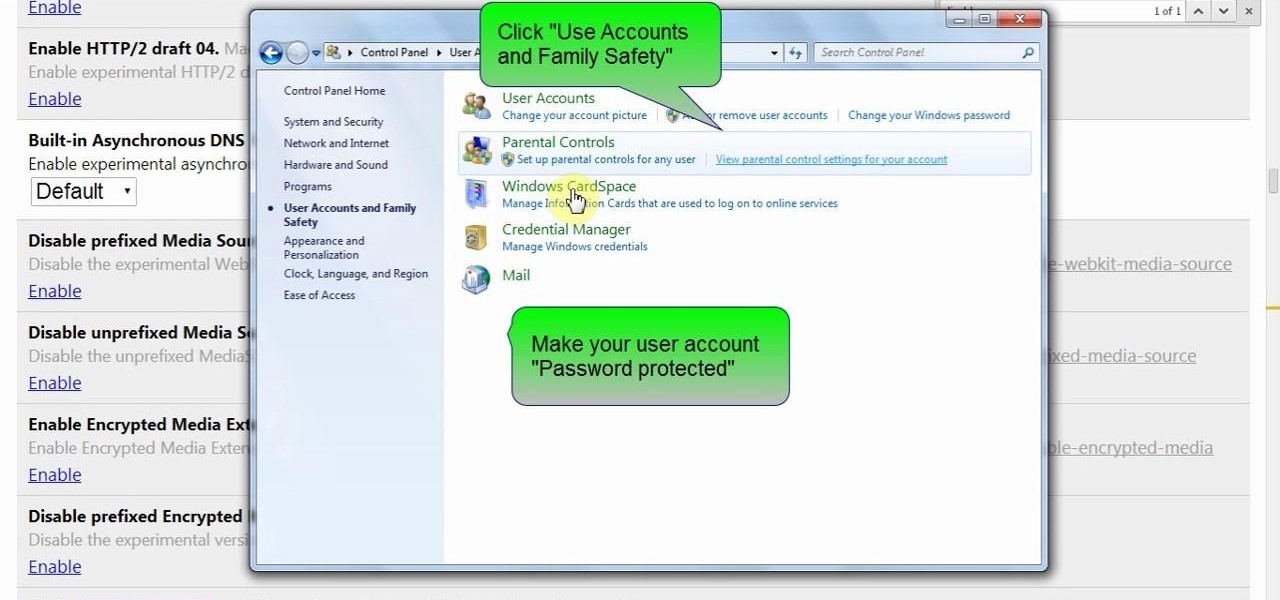
This video will provide an idea how to protect your ms word document with password. Whenever anyone wants to open the document it will ask for password.

If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

While no longer native to the United States, hospitalization from malaria occurs in this country more than most would believe. Why is that, and what can you do to protect yourself when you travel abroad to regions where malaria is active?

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Apple announced four different iPhone models during its Oct. 13 web-only event, but only two of them can be purchased this month: the iPhone 12 and iPhone 12 Pro. Preorders have already started for the two smartphones, and you could have one in your hands as early as Oct. 23, if you're lucky. To help keep your shiny new iPhone protected from scratches and cracks, try one of these cases.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Pertussis, or whooping cough, is a highly contagious disease that can be life-threatening for young children. New research backs a recommendation that all pregnant women receive a pertussis booster with each pregnancy, as it can help their infants fight off the infection.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

Normally, "restricted access" is something you despise. No one likes to be told they can't do something, especially when it comes to the Internet. Unfortunately, having web access at all times can not only eat away at your wallet, but make your day less productive overall, so some sort of moderation is needed.

Reddit user craigyboy2601 knows a thing or two about airline baggage handlers. After all, he is one. So, when he offers some tips on how to protect your luggage from loss or damage, you should probably pay attention! Here are the highlights from his post.

Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

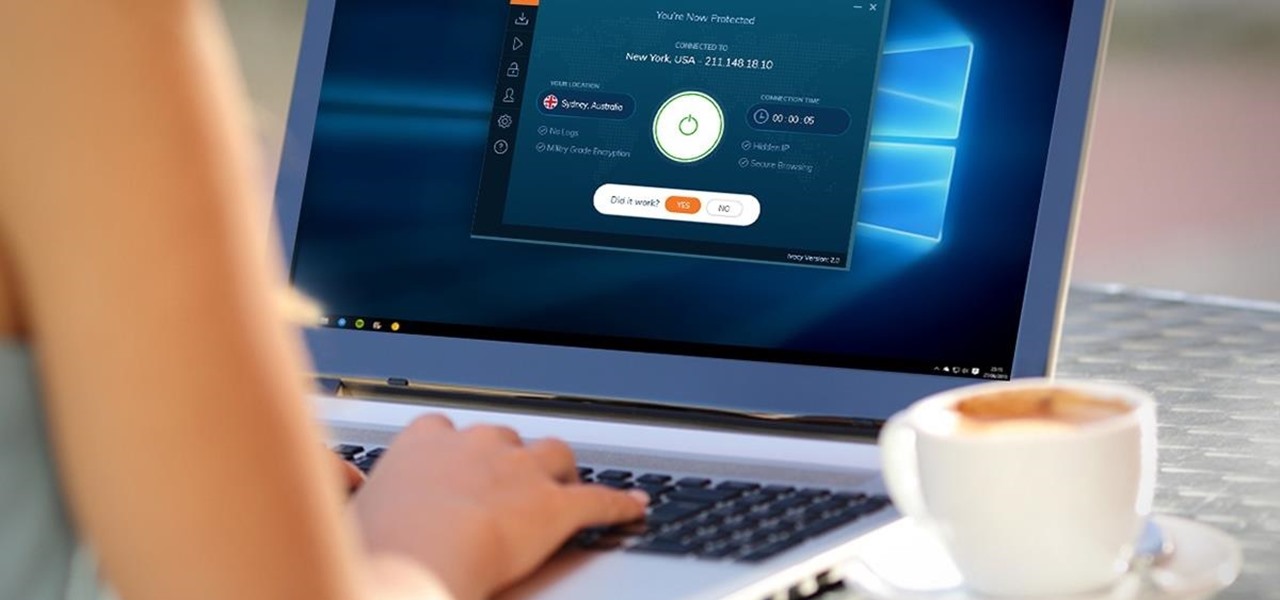
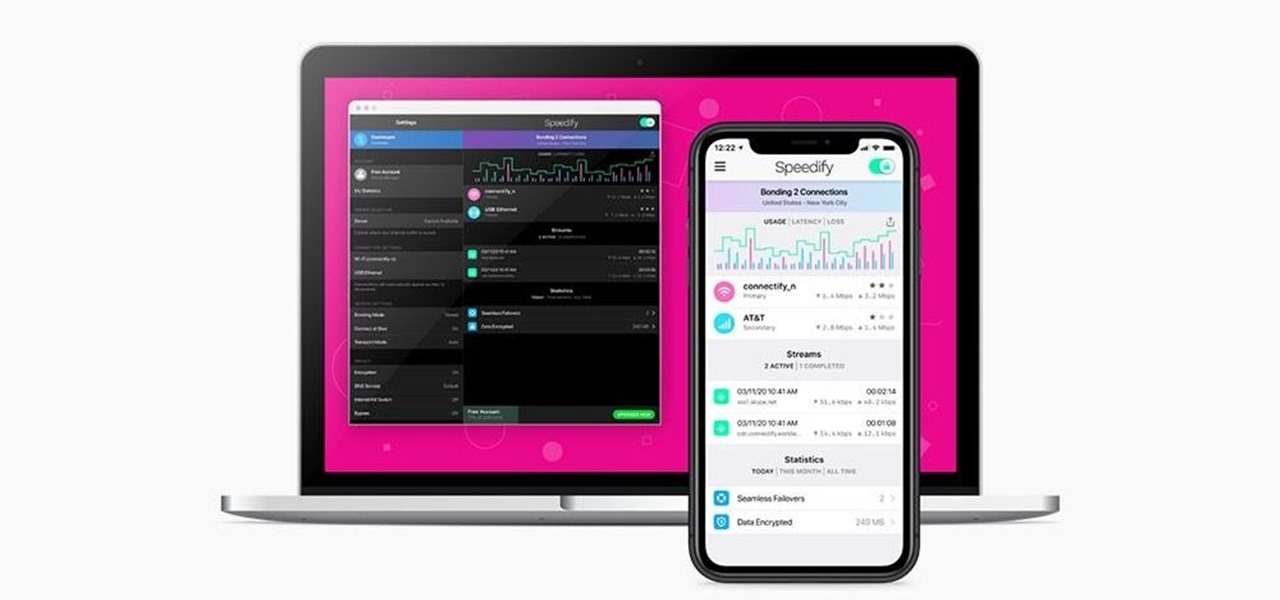
Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.