
Gary, RV Dr. tip #9 is describing about his new tool called HepVO for the kitchen and bathroom sinks, for the better flow of water and to prohibit the bad gases to come in. Mr. Gary is explaining that how this HepVo can replace P shaped traps. Because the traps are necessary for the flow of water.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.
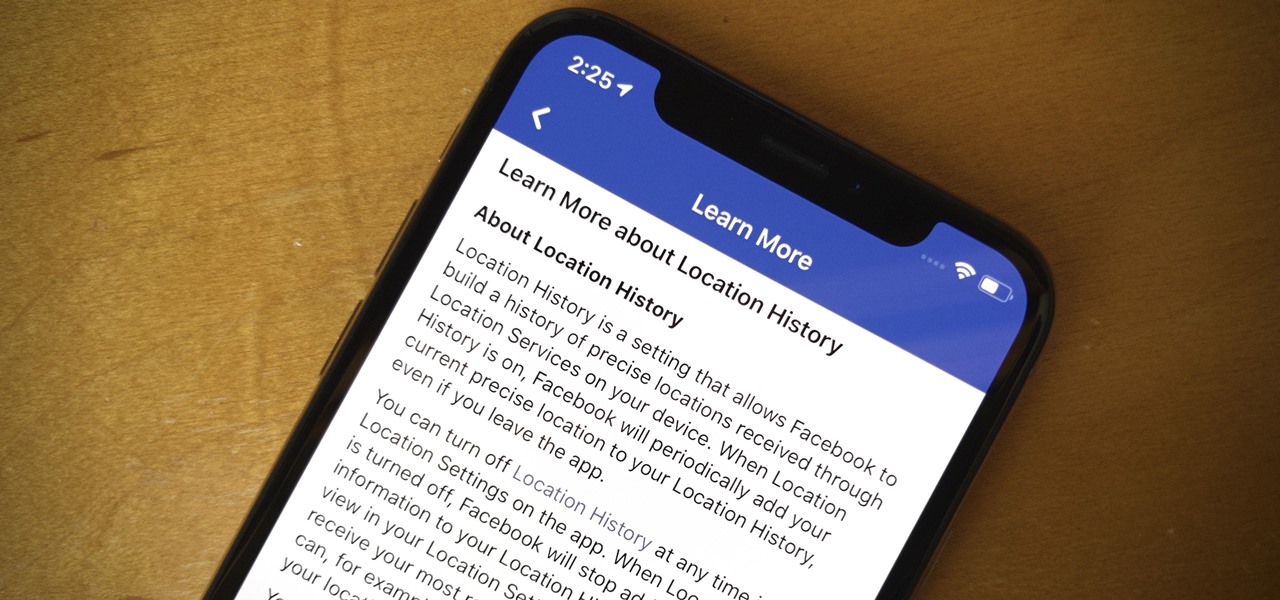
When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.
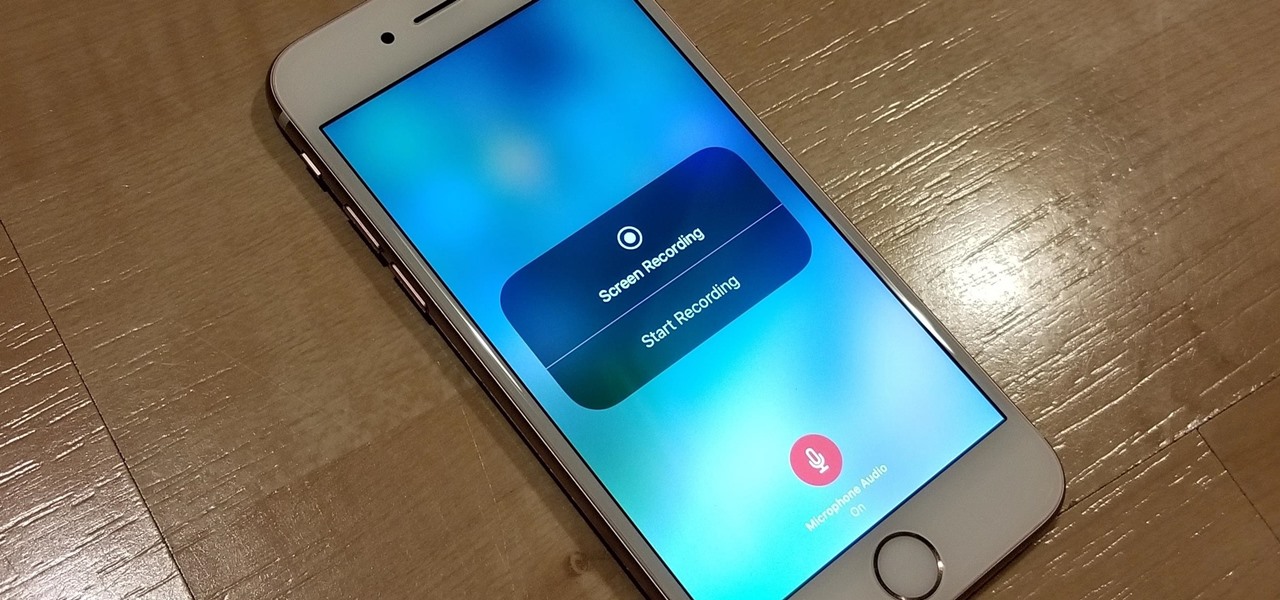
The only official way to record your iPhone's screen before iOS 11 was to hook it up to a Mac and use QuickTime Player to do the recording for you. If you wanted to record your iPhone's screen without an external device, there were unofficial apps you could use, like AirShou, but they required complicated installations. Now, in iOS 11, iOS 12, and iOS 13, Apple has an official, native screen recording tool.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

It's easy to copy text from webpages, messages, documents, and other views on your Android device — except when it isn't. Many apps block or prohibit text selection, forcing you to take screenshots or write out the whole excerpt manually. But you don't have to resort to those methods since there's a simple workaround to selecting and copying text from uncooperative apps.

Most of you have probably wondered at least once who has been checking out your social media profiles. While most platforms prohibit you from seeing who's viewed your profile, such as Facebook, Instagram, and Twitter, TikTok is one of the few places that lets you track profile visitors. And unlike with LinkedIn, you don't have to pay for the privilege.
The House of Representatives has approved an amendment to the draconian National Defense Authorization Act (NDAA) that will limit the Department of Defense from using data collected by unmanned spy drones against Americans.
In what has become a rare scene in Washington, a group of bipartisan lawmakers joined President Barack Obama today at the White House for his signing of the Stop on Congressional Knowledge Act.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

Little Ethiopia is the place to get ahold of authentic African cuisine. African food mainly consists of spices and fresh ingredients. Ethiopia is a country in Africa that demonstrates the use of spice in its cuisine. The Ethiopian cuisine follows the Islamic rules, the religion Ethiopians are accustomed to, and its old custom, which is the caressing of the earth. The Ethiopian Islamics prohibit the eating of pork so their meat choices are limited. The Ethiopians are specialist whenit comes to...





















