
How To: Play "Crush" by David Archuleta on guitar
Learn how to play "Crush" by David Archuleta, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:


Learn how to play "Crush" by David Archuleta, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

The method demonstrated in this how-to video makes the Bowline knot quick and easy to tie. It is useful when you expect a blow and need to take a few turns around your winch to use as an additional hardpoint. In this case I am simulating a mast winch but the process can be used on a horizontally mounted winch as well. The secret is to form the bowline eye by capsizing an overhand knot. With the standing part in your left hand form a turn around the winch from top to bottom then cross the runn...

Check out this video to see how to collect blood with the BD Vacutainer Eclipse Blood Collection Needle.

Want to impress your doctor? Check out this video and learn a few fancy names for common problems and soon your doc will be in awe of your smarts.

There's nothing tastier than a fresh-picked tomato. Enjoy a bumper crop this year with these tips. Learn how to grow tomatoes in your garden with this Howcast video guide.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Starting a business has to involve a desire to benefit someone else other than you. If all your reasons for starting a business are to benefit you, chances are good that you have missed the big picture. At least one reason you have to want to stat a business needs to be to help someone else. Either use proceeds from the business to help a charity of your choice or to solve a problem or provide a solution to a need for the target group that your business serves. Focus on one issue to start wit...

Over the past 5-10 years, there has been an enormous growth in 4-mallet percussion. With the rapid increase in popularity, there comes the possibility of students moving too quickly through the learning process, or not having adequate instruction. In this installment from his video tutorial series on four-mallet percussion, Gifford Howarth covers the basics of gripping the inside mallet and gives you some common problems to watch out for.

Over the past 5-10 years, there has been an enormous growth in 4-mallet percussion. With the rapid increase in popularity, there comes the possibility of students moving too quickly through the learning process, or not having adequate instruction. In this installment from his video tutorial series on four-mallet percussion, Gifford Howarth illustrates exercises to isolate the interval changing motion of inside and outside mallets on a mallet instrument such as a vibraphone.

Over the past 5-10 years, there has been an enormous growth in 4-mallet percussion. With the rapid increase in popularity, there comes the possibility of students moving too quickly through the learning process, or not having adequate instruction. In this installment from his video tutorial series on four-mallet percussion, Gifford Howarth explains how to handle larger intervals on a mallet instrument like a vibraphone or marimba without getting into bad habits.

Over the past 5-10 years, there has been an enormous growth in 4-mallet percussion. With the rapid increase in popularity, there comes the possibility of students moving too quickly through the learning process, or not having adequate instruction. In this installment from his video tutorial series on four-mallet percussion, Gifford Howarth provides suggestions for an effective warm-up routine.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

Do I really need to tell you that it's a bad idea to play Pokémon GO while you're driving? I really hope it's not necessary, but just in case it is, here you go: It's a bad idea to play Pokémon GO while you're driving.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

This week, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that not only does Samsung have a new virtual reality headset coming, but that Samsung intends to enter the field of augmented reality, too. In fact, Hong talked very little about virtual reality and instead spoke at length about Samsung's move into augmented reality.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

Welcome back, my rookie hackers!

We've all been there; waking up in the morning with a stiff, achy back. Maybe you overdid the yard work this weekend. Perhaps you were a bit too enthusiastic on the Nautilus circuit. Could be the long hours spent hunched over your computer are catching up with you. Perhaps your back pain is indicative of something more serious. Unfortunately, unless you've really injured your spine, your doctor isn't going to be much help; the best he can do is offer you pain medications and tell you to rest ...
So, I wondered whether there was a possibility to integrate Facebook even further into my life! (I still wonder why I wanted that actually...) Here's the way to do it!

Modding you XBox 360 case is not for the faint of heart. There is a real possibility any time you take a saw to your Xbox that it isn't going to work afterwards. For those of you who have moved beyond the fear, watch this video. It will teach you how to cut your CD drive as part of a larger case mod so that you can see the CD spinning in the drive while you are playing. It looks cool, it may actually be cooler, what more do you need?

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...

Whether you're at a concert or on a road trip, sometimes you need to camp out. Check out this video if you are planning a car trip where you will be camping along the way. Car camping requires plenty of preplanning and patience but will be totally worth it in the end when you have one sweet road trip!

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Bruschetta is perfect as an appetizer or an afternoon snack. All you need is bread, olive oil, tomatoes, and some spices. The word bruschetta comes from the Italian term "to roast over coals." So, the most important part is to toast the bread. In modern times, a toaster, broiler, or grill works just fine. I'm placing my bread on a grill. Flip the bread over, and toast it on both sides. You need an Italian loaf or a baguette, garlic, extra virgin olive oil, salt, pepper, tomatoes and basil. Yo...

The year is 2018. You just received your own Magic Leap One: Creator Edition. What now? Rewinding back to today, we know of one specific app that will be available for Magic Leap's device, along with two others that could be tagged as highly likely. Paired with Magic Leap's own experiments and demonstrations, we can get a sense of what the playground for this new toy will offer.
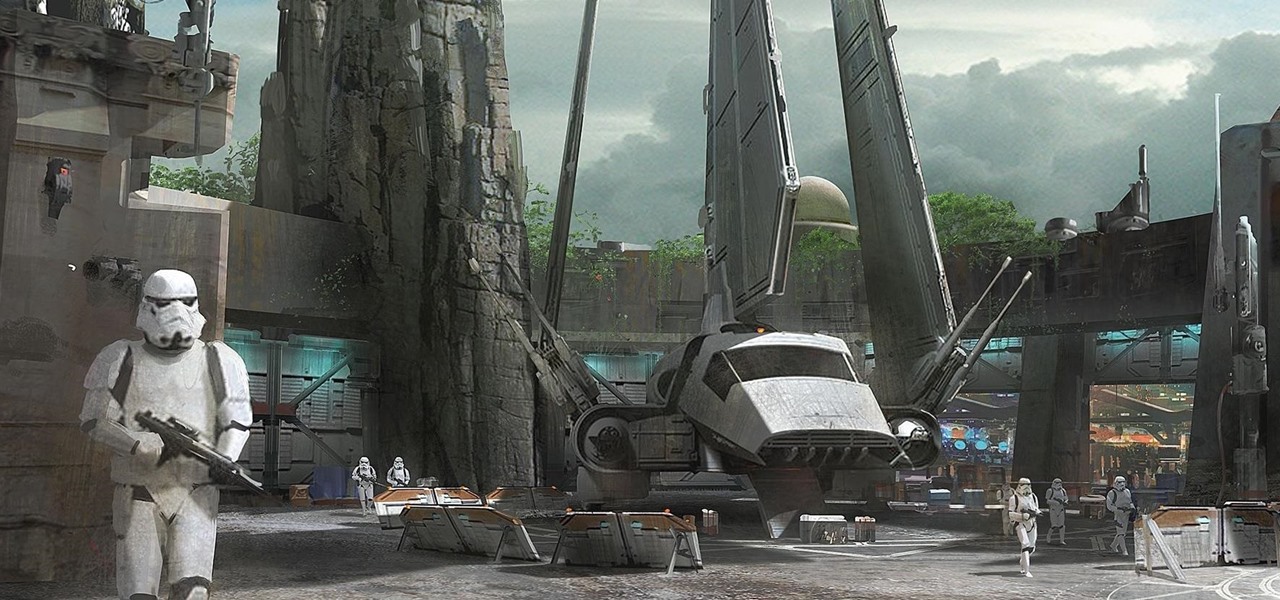
Disney Parks are hard at work bringing the technology from a long time ago in a land far away to life for the opening of Star Wars Land parks in Anaheim and Orlando in 2019.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Lenovo has done a great job preventing leaks of their new Moto RAZR. We've seen a few images here and there, but for the most part, we knew very little about the long-rumored phone. But with the announcement date just around the corner, an FCC filing has given us a look at the new RAZR from almost every angle.

Apple's annual iPhone launch is set for Sept. 10 and iOS 13 is expected to be released soon thereafter, but it appears that the likelihood of a "one more thing" reveal just got a big boost.

While Apple augmented reality smartglasses are not yet official, the tech giant is ramping up its resources by appointing company veteran Frank Casanova to promote its augmented reality offerings.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.