Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

In this video, Mike Craft from Lowe's teaches us how to build a fire pit. First, check to make sure there are guidelines permitting you to place a fire pit outside of your home. Then, make sure you have a clear area to place the fire pit. Once you have a spot picked out, you will need to make a paver base for your fire pit to lay on top of. After this, lay a circle of blocks around the cover for the fire pit. Layer three sections of blocks, then line with bricks on the inside and place in the...

Las Vegas is known as the city of sin, a place for gambling, fine dining, and decadence. Now, you can add another notable characteristic to that list: West Nile. You may want to hold off on scheduling your trip to the Sin City — or at least stock up on bug spray — because health officials have reported that mosquitoes in Southern Nevada have tested positive for the virus.

If you own an iPad 2, a 3rd or 4th generation model, or original iPad mini, then you won't be able to utilize the new multitasking elements introduced in iOS 9. Although many iPads can use the Slide Over and Picture-in-Picture features, only the iPad Air 2, iPad mini 4, and iPad Pro have the ability to perform Split View.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

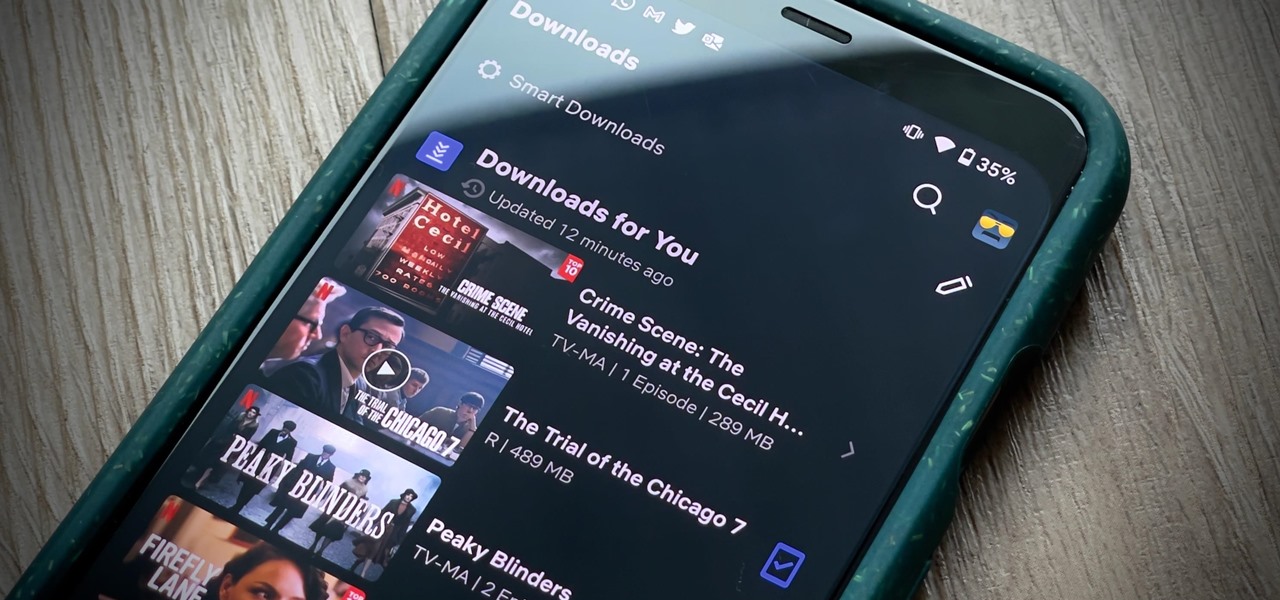
These days, there's more content than ever, and the sheer amount of titles out there can make picking something to watch seem near impossible. Netflix does provide suggestions based on content you've already viewed, which helps, and the company believes so much in its algorithms that it now gives you the option to auto-download videos on your devices based on your interests, no decisions required.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Giving a speech in front of a large crowd doesn't need to be the nightmare everyone imagines it to be. We speak to many people every day and yet it is still very common for a person to be nervous when delivering information in front of several people. This fear can be overcome by practicing how to give a speech and being prepared.

The Mechanic character class is now live in Global MapleStory (GMS), the international version of Nexon's popular free massively multiplayer online role-playing game. Celebrate the release by building a super-powerful Mechanic to call your own! No idea how to invest your skill points? No problem! The build guide excerpted below eliminates the guesswork, permitting you to focus on what matters: playing the game.

Umbra, penumbra. Not exactly abracadabra, but if you've taken an astronomy class, you know exactly what the umbra and penumbra are. And any Earthling would agree that the umbra is the best place to be during a solar or lunar eclipse.

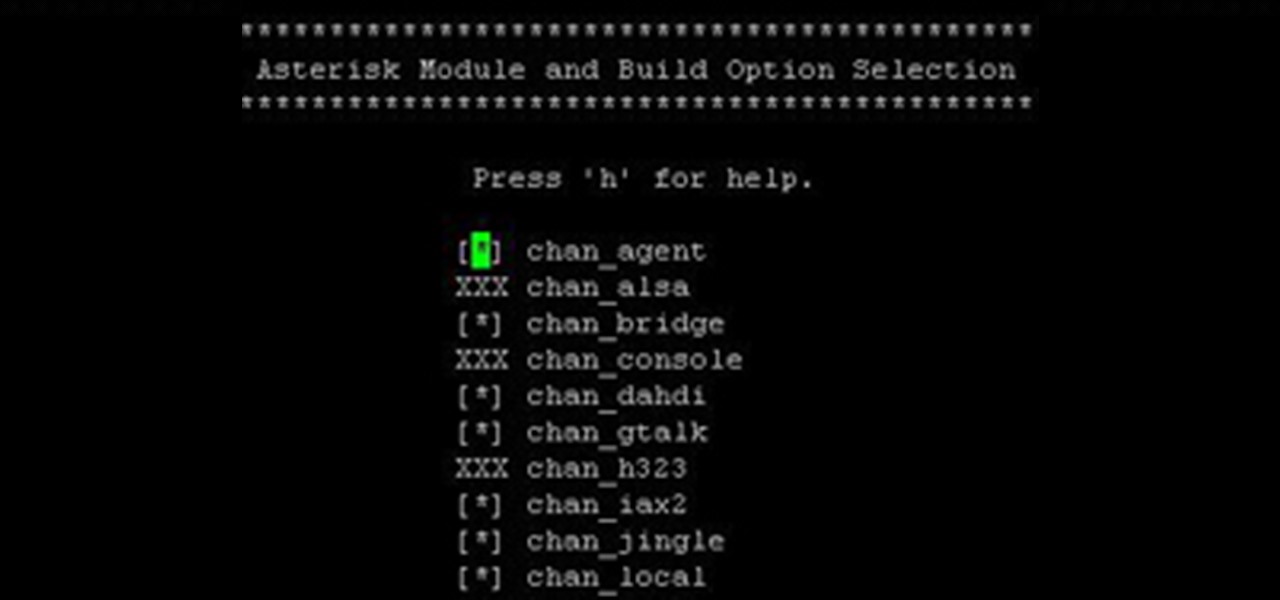
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.