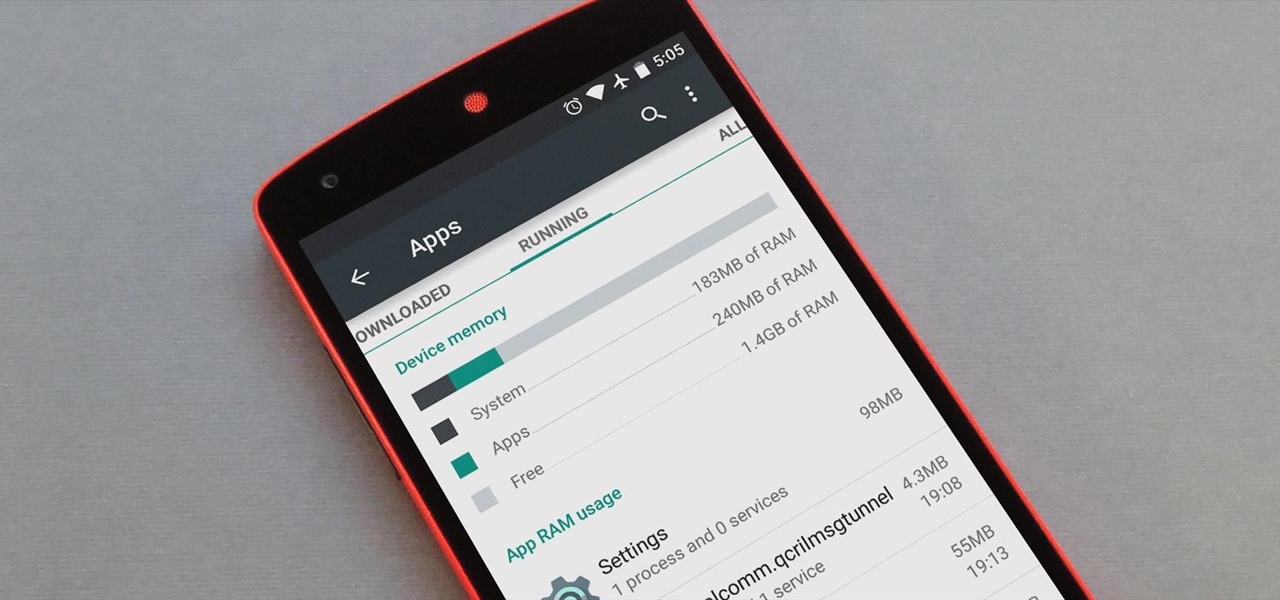
Back when 4.1 Jelly Bean came out (boy, how time flies), Android introduced expandable notifications. Depending on the notification, a simple swipe down with your finger could expand it and show extra content, like Delete and Reply buttons for Gmail messages.

This video gives you a basic understanding of how to use Radio Frequency Identification (RFID) and text to speech modules. Learn how to integrate your home PC with external modules for security and fun!

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

This video demonstrates the installation of memory in a 13” Macbook Pro (mid 2009 model). It’s easy to perform and takes about 10min time. You’ll require a #00 Philips screwdriver (available in the Newer Technology 11- piece tool kit). Take care to work in an anti-static work space. Close the Macbook Pro and flip it over with the hinge side up. You can note 10 screws along the border. Start unscrewing the 3 screws on the right on the top edge, these are longer than the rest. Now unscrew the r...
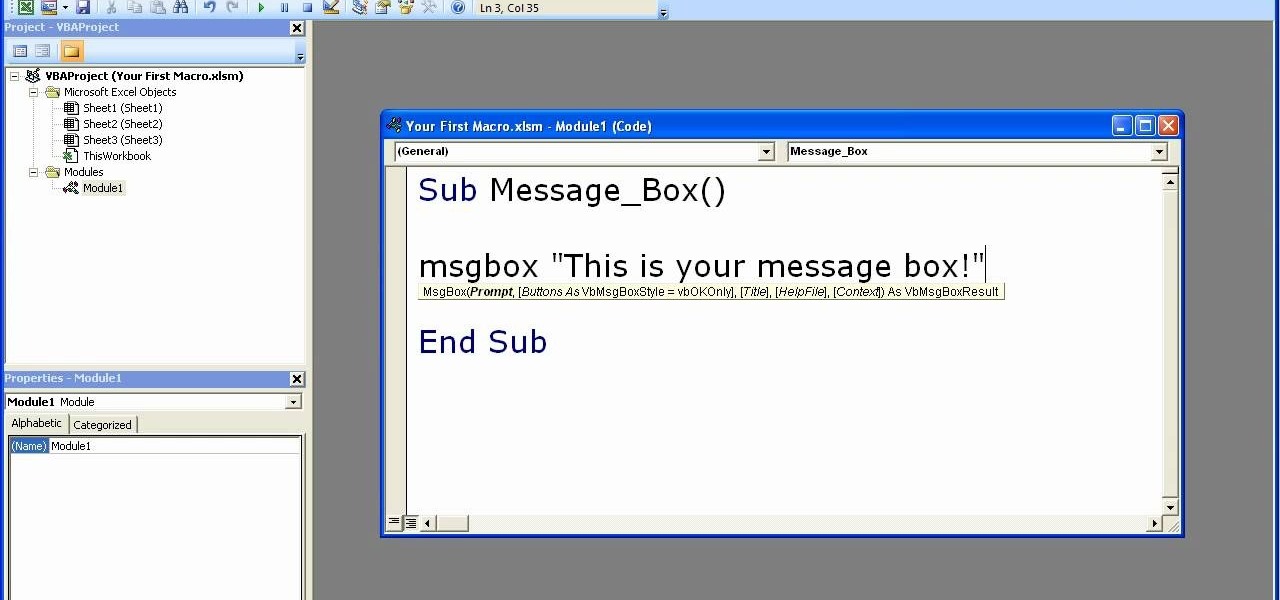
The speaker in this video introduces the concept of macros used in Excel, very simply and lucidly. Two sets of shortcut keys are used, one set to create the macro and the other set to run it. The first shortcut opens up the VBA window (Alt+F11), with a workbook along with the 3 default sheets. This video puts the macro in a module. The procedure starts with typing sub and a name which can be easily recalled. The rules for naming the macro are also covered briefly. After the macro code is writ...

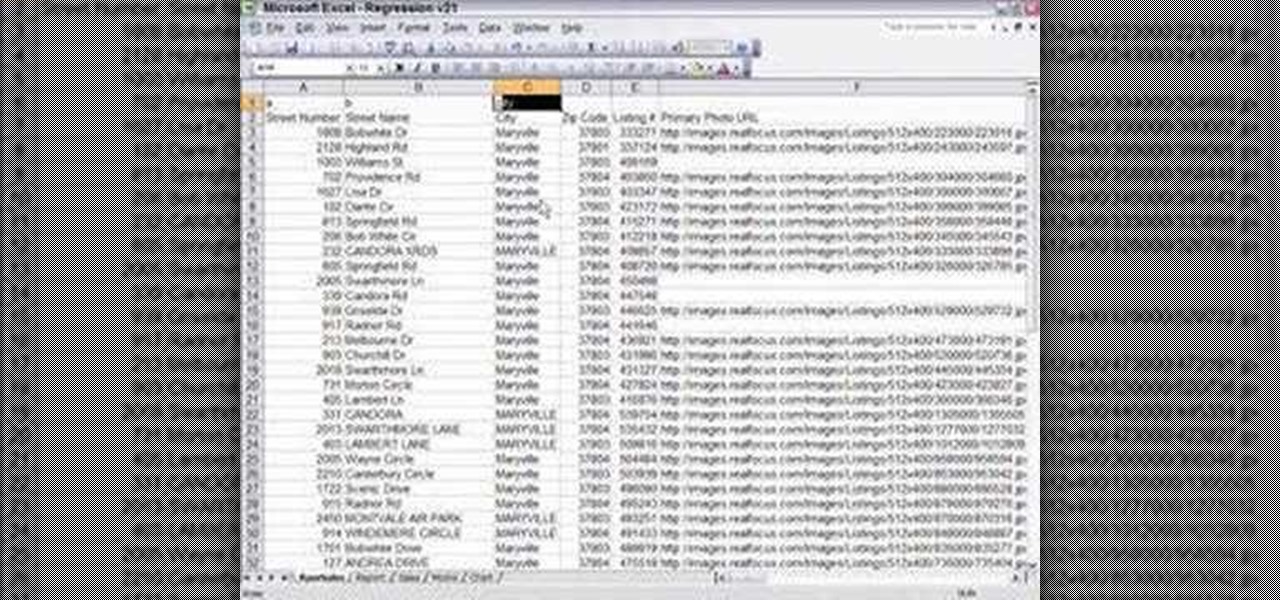
Are you in real estate? Take a look at this instructional video and learn how to run your excel spreadsheet over a regression analysis module. An appraiser who's appraising a house decides to run a multiple regression analysis as an addition to the direct sales comparison approach. The spreadsheet used in this tutorial was written in excel, but could be rewritten in another format. The spreadsheet was exported from an MLS. Once the excel sheet is downloaded, the appraiser will open up the reg...

In this video tutorial, you'll learn to use CKK modules ImageCache and Imagefield to build a system for posting images on your Drupal website. Learn to create a robust and flexible system for handling images and has a bright future with more modules born every day that tap in. (This micro-lesson depends on prior understanding of the CCK module and the Views module.)

A Peltier module allows you to turn heat into electricity. Because you can place it in areas that are normally warm anyway, the electricity created is "free" in a sense, though it does work best when one side of the module is cold and the other is hot. In other words, all you'll need for this project is the Peltier module and a cooler surface such as soil or water, and a warm area such as a well lit window or warm pan.

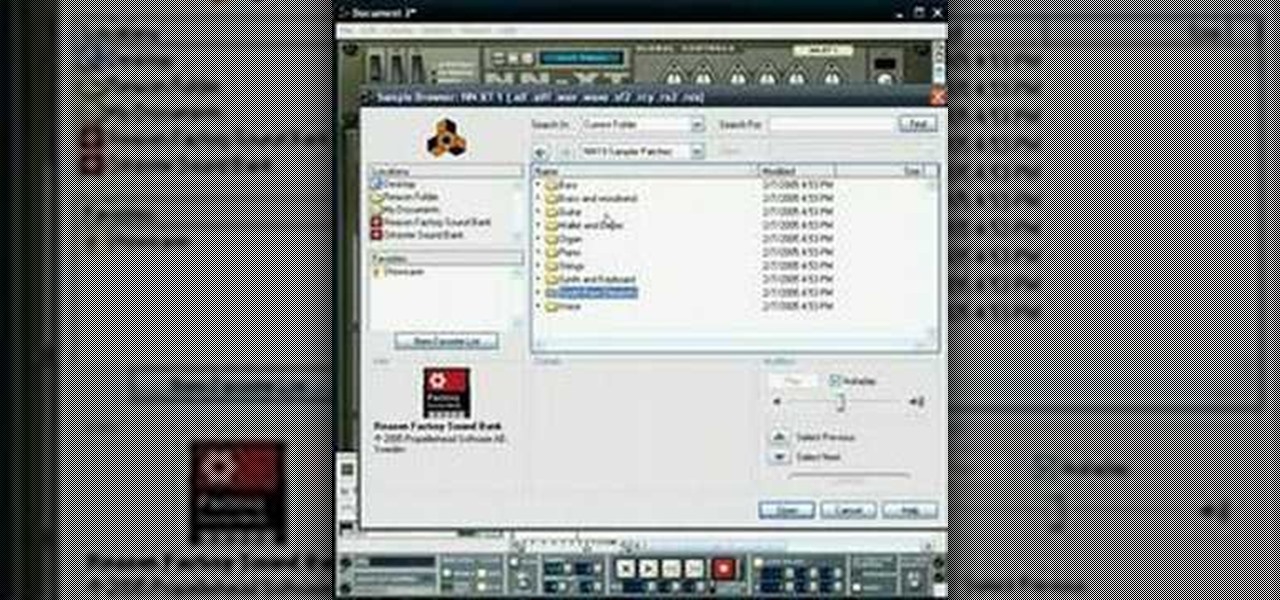
A short tutorial on how to sound design and build samples within the NN-XT to create pads patches. Part 1 of 3 - How to Build samples with the NN-XT module in Reason.

Computer vision technology maker uSens, Inc. has unveiled uSens Fingo, a camera module that enables tracking of hand and head movements for PC-based, mobile augmented, and virtual reality platforms.

Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.

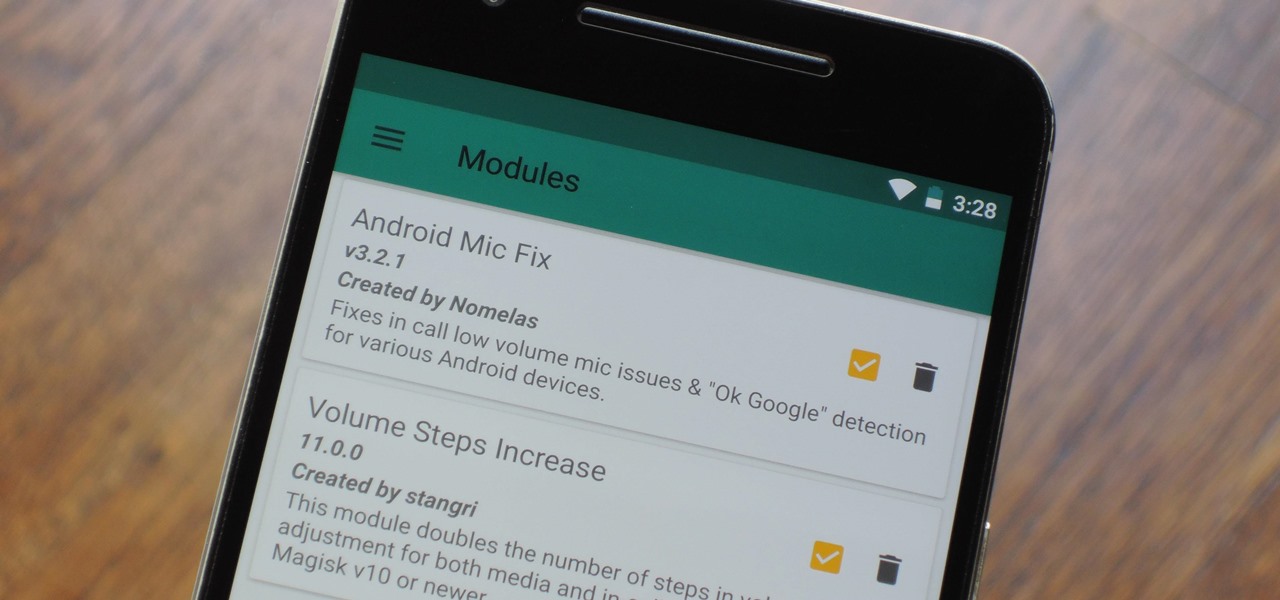
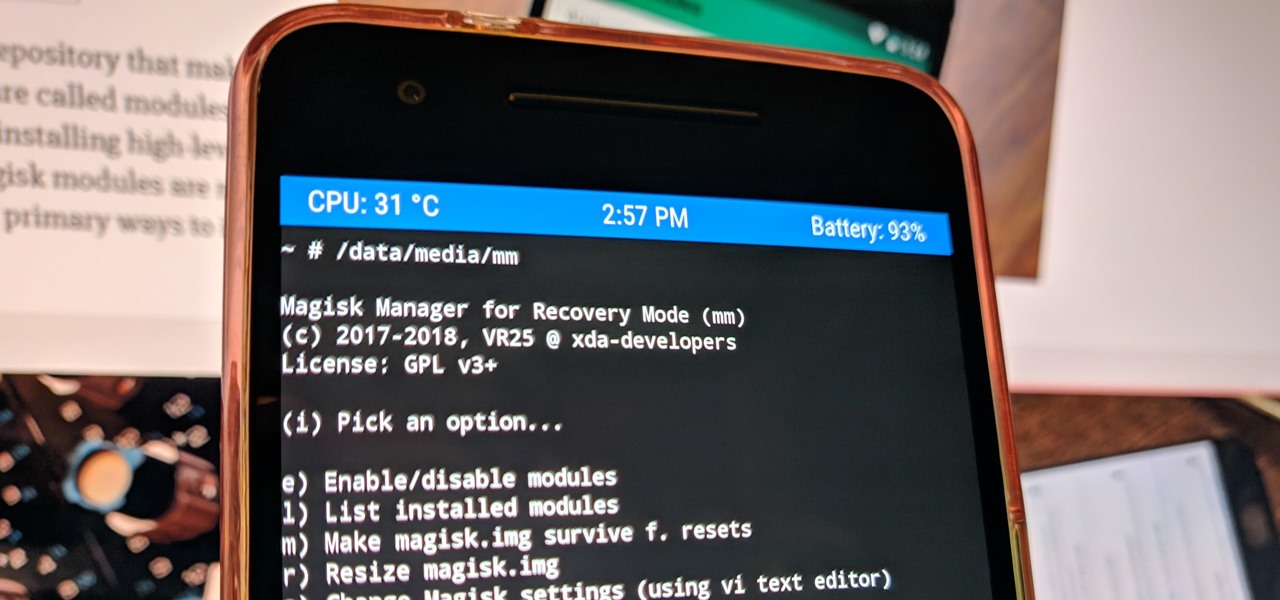
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk modules are not hosted on the official repo just yet, so there are two primary ways to install them.

The Xposed Framework has an official repository for downloading modules which can be easily accessed by searching the Download section in your Xposed Installer app. But not every module is available on the Xposed repo — in fact, many unique and interesting modules are only hosted on third-party servers.

Origami purists will argue that all origami creations, no matter how complex, should be folded from one single sheet of paper, but the rules were made to be broken, right? If you've already mastered the art of one-sheet origami projects like frogs and cranes, challenge yourself to this project: a tetrahedra composed of five intersecting pyramidal shapes.

This video from OWC presents how to install memory in a 17" Macbook Pro.The operation will take about 15 minutes and doesn't require an experienced user.First you need to provide all necessary anti-static precautions - discharge static electricity, use static-free surface.You'll need #00 Phillips screwdriver and nylon pry tool.You can find these in the Newer Technology 11-piece tool kit.To start, shut down the computer, close it and flip it over.You will need to remove 10 screws. Use #00 scre...

First, you will need this tutorial video to learn how to make the modules for this 3D origami project: http://www.wonderhowto.com/how-to/video/how-to-build-origami-modules-for-3d-origami-272338/

The Xposed Framework is a very powerful platform on top of which smaller modules can run to make changes to the Android system and various other apps. Installing modules is just as easy as sideloading any Android app, but afterwards, you'll need to activate the module and reboot your device.

Created by by XDA developer rovo89, the Xposed Framework allows you to quickly search for, download, and install new modules that allow various forms of customization for your Android device.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Chipmaker Qualcomm introduced the second generation of its Qualcomm Spectra image signal processor (ISP), which has gained capabilities that will enable smartphones to facilitate augmented reality apps.

The Xposed Framework lets you modify your phone's software like nothing else. But because of how powerful this tool can be, it seems like things are always in development. This is certainly the case with many Xposed modules, to the point where some have several alpha and beta releases before they go mainstream.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

When Google first introduced Android 4.4, the most glaring user-facing change was a new trend towards transparency. The stock launcher, originally exclusive to the Nexus 5, had transparent status and navigation bars and its app drawer added a touch of transparency.

Go to your Joomla admin page. Now go to extensions, module manager. Now on that page, click on new. Now select login button and click on next. Now type the name and set the position, it depends on the template you use like if you have the help file of that template, you can figure it out by checking that but many free template does not contain the help file. So for now, set the position left and click on save. You can arrange the order of your modules just by clicking the up icon or just by e...

In this video tutorial, viewers learn how to remove the macro warning in Microsoft Excel. When you see the warning, click Enable Macros. Then right-click on of the sheet tabs and select View Code. Open the Modules folder menu. Now right-click on the module and select Remove Module. Click No to prevent the Module from exporting as a saved text. To go back to Excel, click on File and click on Close and Return to Microsoft Excel. Click on Save to save your workbook. This video will benefit those...

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

The Amaryllis flower, also known as the Belladonna lily, is, as its second name suggests, an extremely beautiful and lithe plant native to the Southwest region of South Africa. Recreate the delicate beauty of this flower by watching this tutorial.

PowerBook Medic is the ultimate resource for Mac computers and electronics repair. They have helpful tutorials on most Apple products including the MacBook, MacBook Pro, PowerBook, iBook, iPhone, iPod, and more, covering topics from disassemblies, to RAM upgrades, to replacement hard drives.

Accidents will happen. This brief how-to will guide you through the process of removing the AirPort module from your MacBook Air both quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their MacBook Air laptops without actually disassembling their computers.

PowerBook Medic is the ultimate resource for Mac computers and electronics repair. They have helpful tutorials on most Apple products including the MacBook, MacBook Pro, PowerBook, iBook, iPhone, iPod, and more, covering topics from disassemblies, to RAM upgrades, to replacement hard drives.

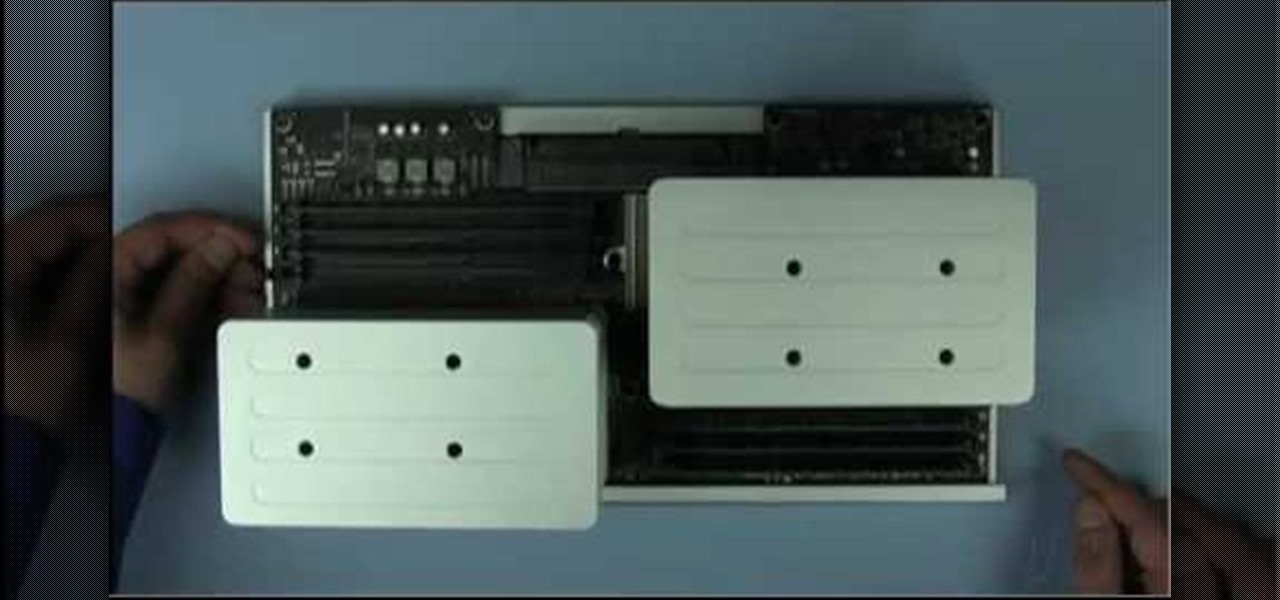
MacOSG demonstrates how to install memory in a 2009 Mac Pro. When performing this upgrade, be sure to take precautions for static by discharging static electricity before beginning. Shut down, unplug and place the Mac Pro on a static-free surface. To access the memory, you need to open the side access door by lifting the latch located on the rear of the Mac until it locks in the open position. You can then the door forward and then remove from the body. The memory is attached to the processor...

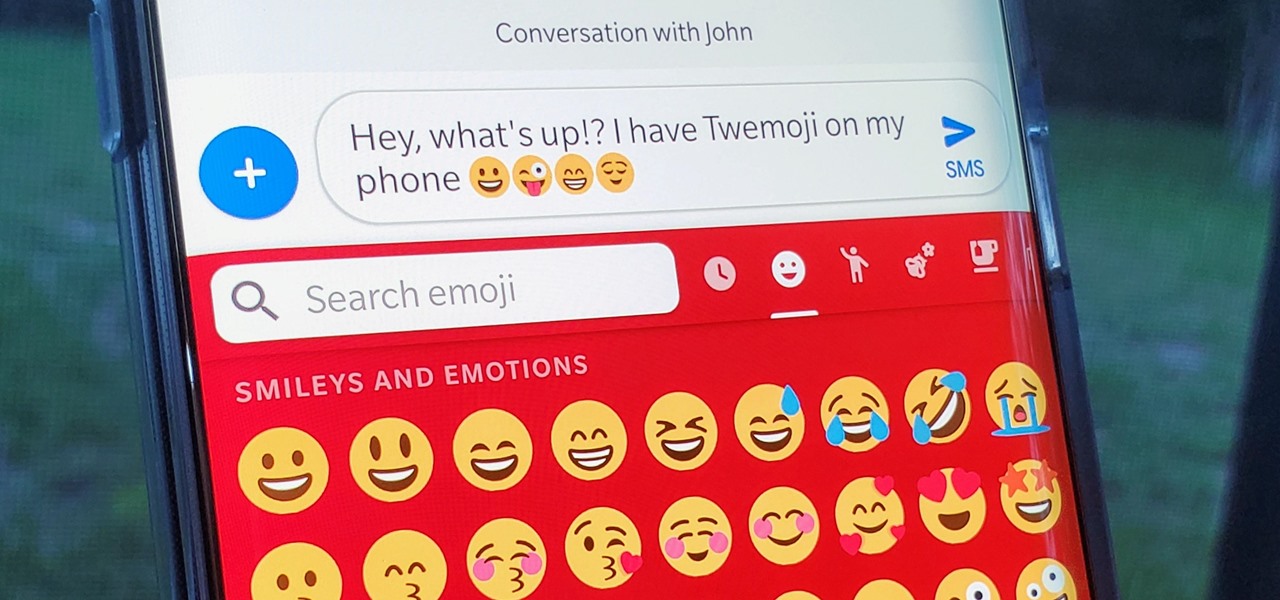
The art of emoji — the next level beyond the simple text-based emoticons we used once upon a time in the not so distant past. We rely upon emojis so much in our always-connected world of today simply because they help portray emotion into our typed out words. They've not been around very long, but have taken the world by storm just as quickly as they made their first appearance in our society.

When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

Android version 5.0 Lollipop introduced a ton of changes to the OS—and of course with new features, there's always a new set of bugs. One of the biggest bugs of all was a massive memory leak caused by the new screen-off animation, which loaded its assets into memory but never cleared them away.

Yes, I know. Nexus owners aren't exactly the biggest Apple fans out there. That "Pure Android" experience was one of the main reasons we bought our Nexus devices. But give the other side some credit—the iPhone's operating system has come along way, and is still the champ when it comes to aesthetic design (at least until Material Design dethrones it this fall).

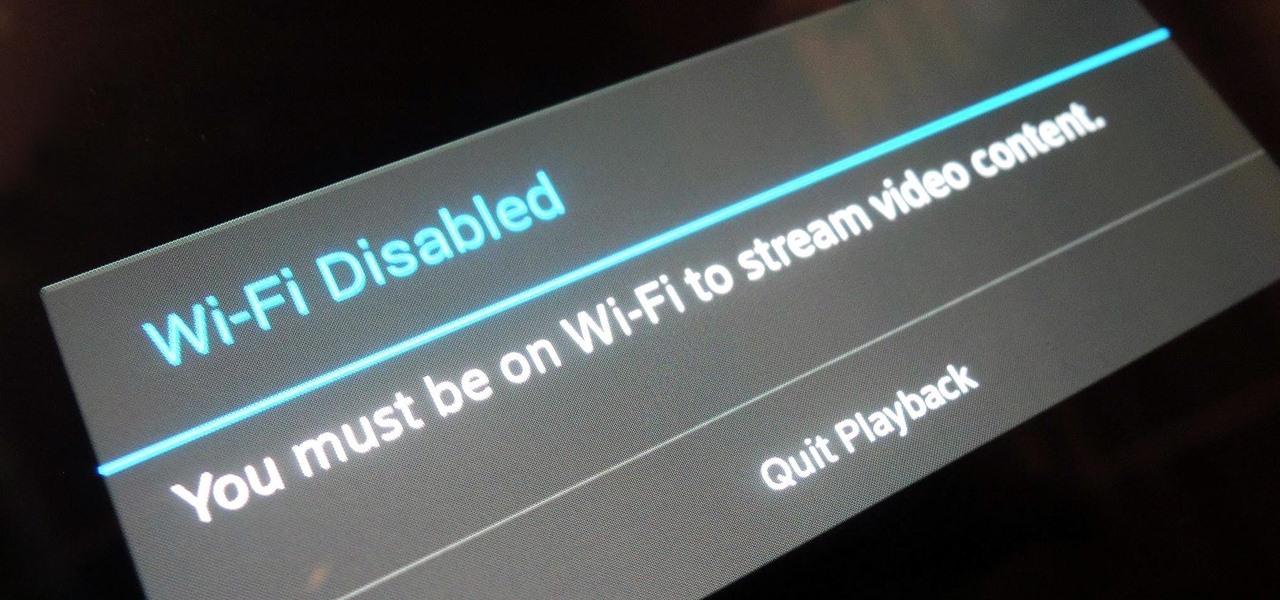
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

Over the weekend, rovo89 and the guys behind the wildly-popular Xposed Framework released a huge update. Leaving practically no UI element untouched, this new version brings a lot of polish and functionality to the revolutionary root softModding tool.