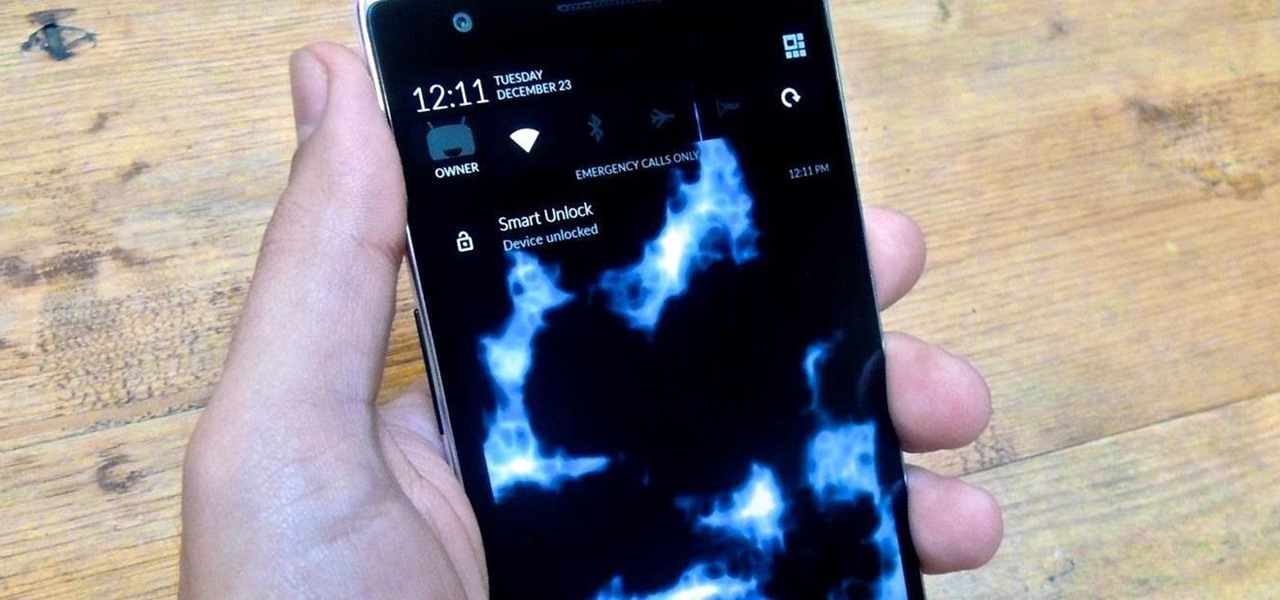
OnePlus One's CyanogenMod firmware comes packed with personalization options that standard Android devices could only achieve with root-level access. By simply entering the Settings app, OPO owners can make changes to their lock screen, status bar, and notification drawer, as well as apply themes and gestures to make their device a little more customized.

If you utilize strong passwords—which you absolutely should be—you've probably had to go back and forth between keyboard screens multiple times to input various letters, numbers, and symbols.
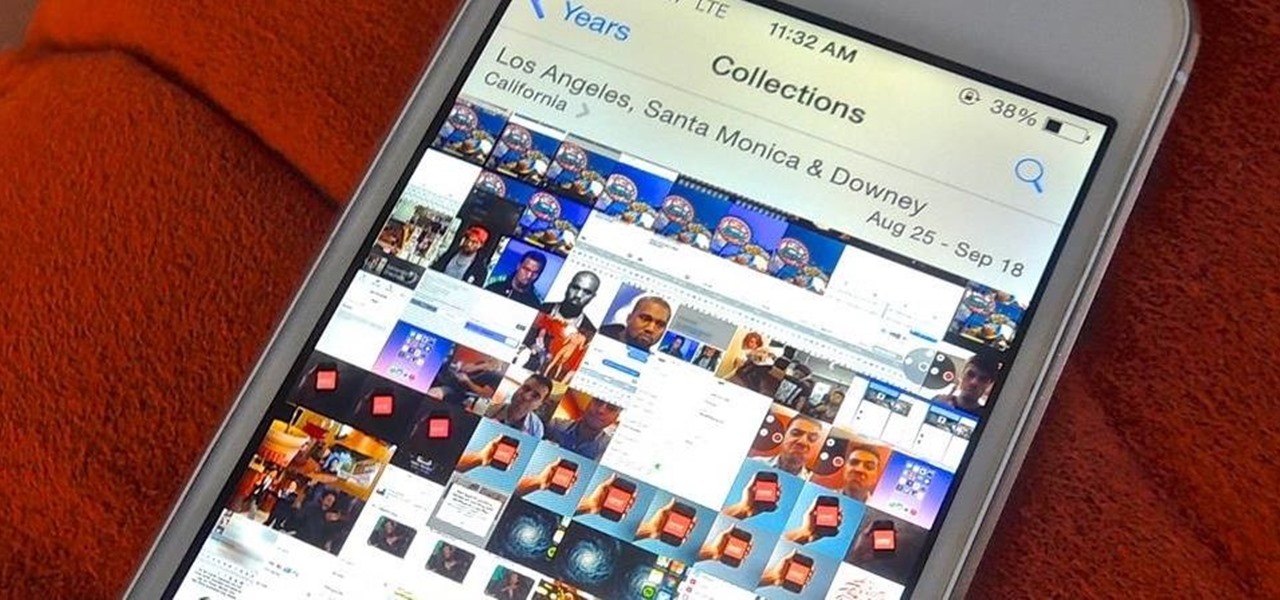
After updating to iOS 8, some of you have probably noticed that a lot of your pictures and videos are missing from the Photos app. Even if you were to restore your iPad or iPhone to your last backup, they would still be missing. But don't worry, that's just because albums work differently in iOS 8—all of your old photos are still there, just not as in your face as before.
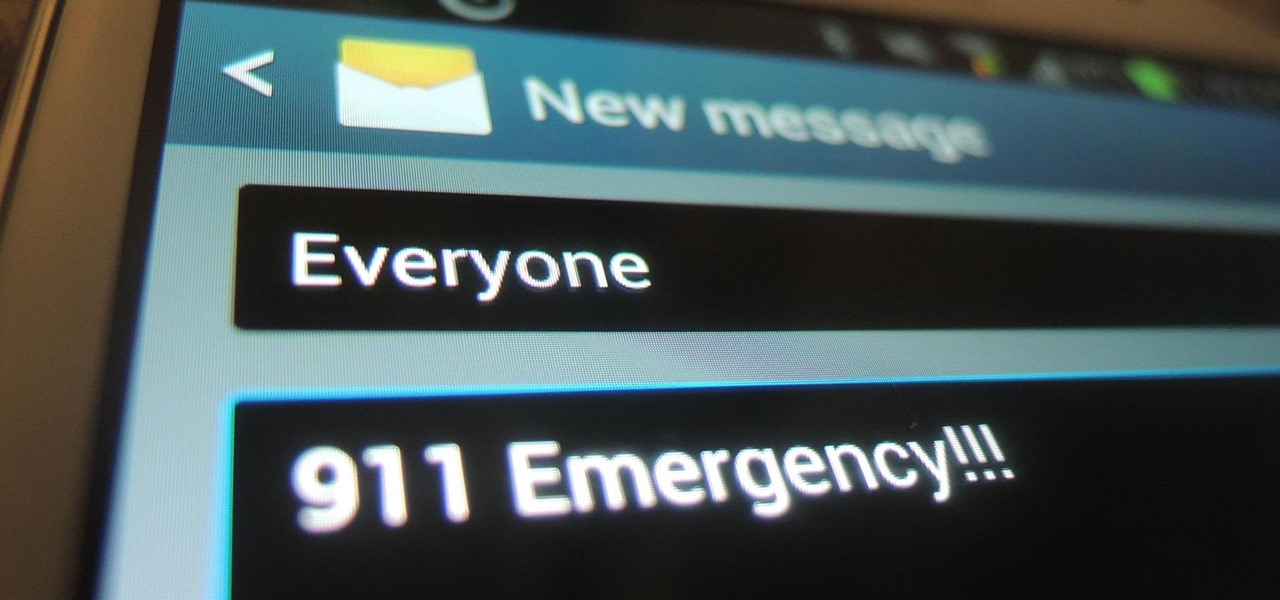
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

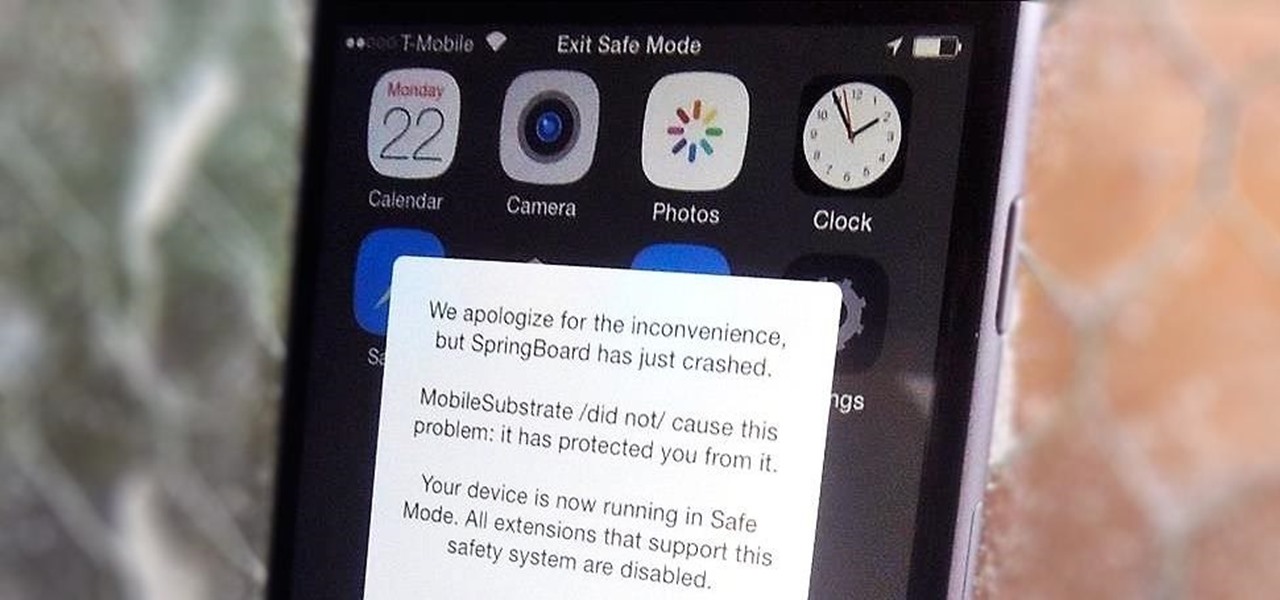
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

Back in the day when computers relied on CRT monitors, having a static image displayed for too long actually resulted in the image being burned into the screen. For this reason, screensavers were developed, which display animated images in constant motion to prevent burning in when you stepped away from your computer.

Sense 6 is great, don't get me wrong, but sometimes I start to miss the vanilla Android experience that comes with Nexus devices. You can always convert your M8 to the Google Play Edition, but then you'd have to ditch all the Sense exclusive features, and we wouldn't want that.

When choosing a phone or tablet, I always take in to consideration what my music experience will be. Unfortunately, the Nexus 7 doesn't have Beats by Dre technology, which some may view as overrated, though it's definitely one of the better ways to get perfect-sounding tunes with headphones. But it's not all about the Beats. There are many other ways to make listening to music on your Nexus 7 tablet a better experience, and we'll highlight some of the options and add-ons that you can try out.

When you listen to music, you don't just want to listen to your favorite songs and artists — you want to hear them perfectly. The same goes for videos you're watching, games you're playing, calls you're in, and anything else in which audio plays a key role.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Over the years, mobile gaming has become a phenomenon, rivaling in magnitude with its console and PC-based counterparts. We even have mobile versions of Fortnite and PUBG now, games that require lots of processing power to run. But when you just want a quick game to play in the grocery line or even on the toilet, try these simple, quick games that you can play right on your lock screen.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

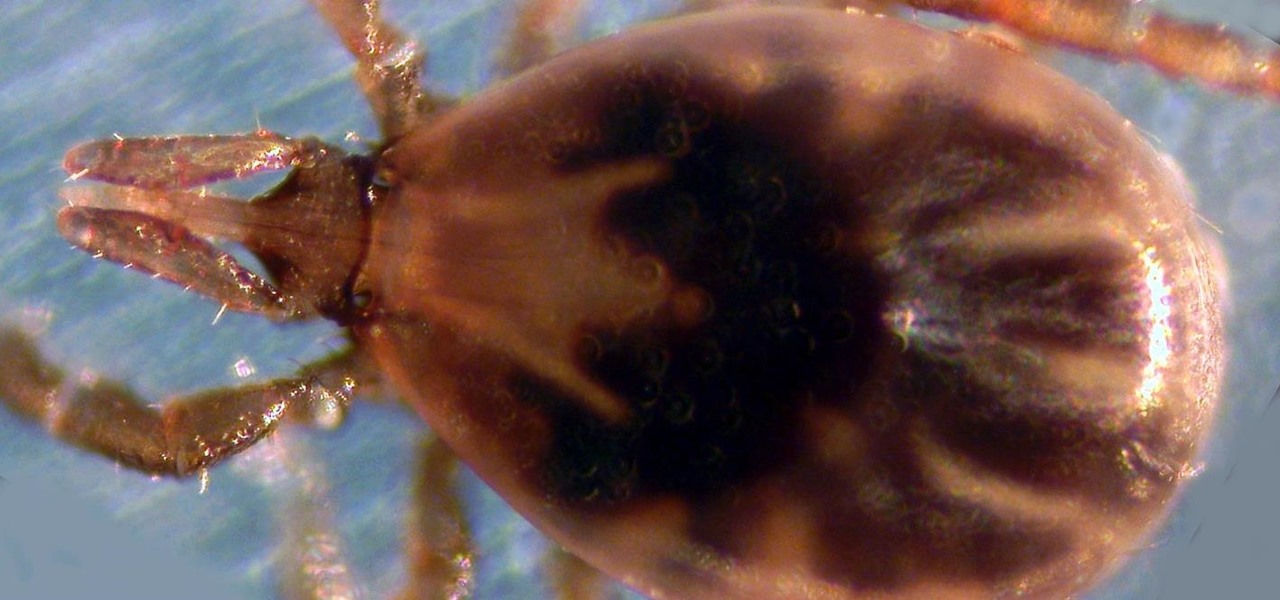
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.

We Nexus users are fairly spoiled. There's a ton of third-party development for our phones, which translates to a virtually endless stream of custom ROMs being made available to us.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

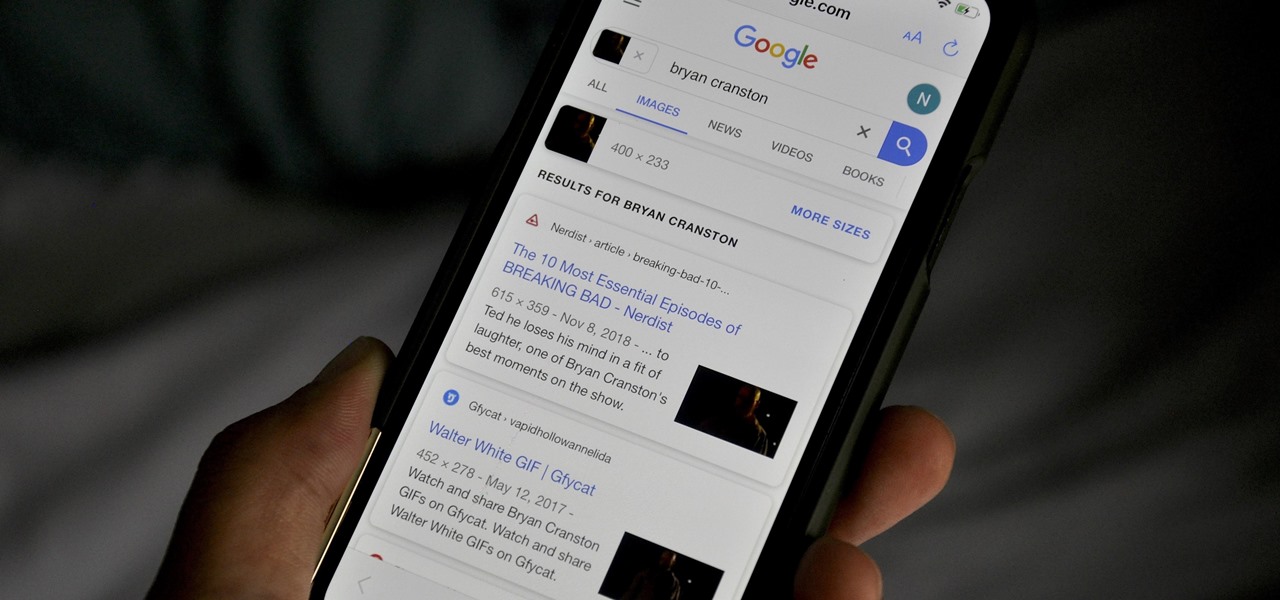
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

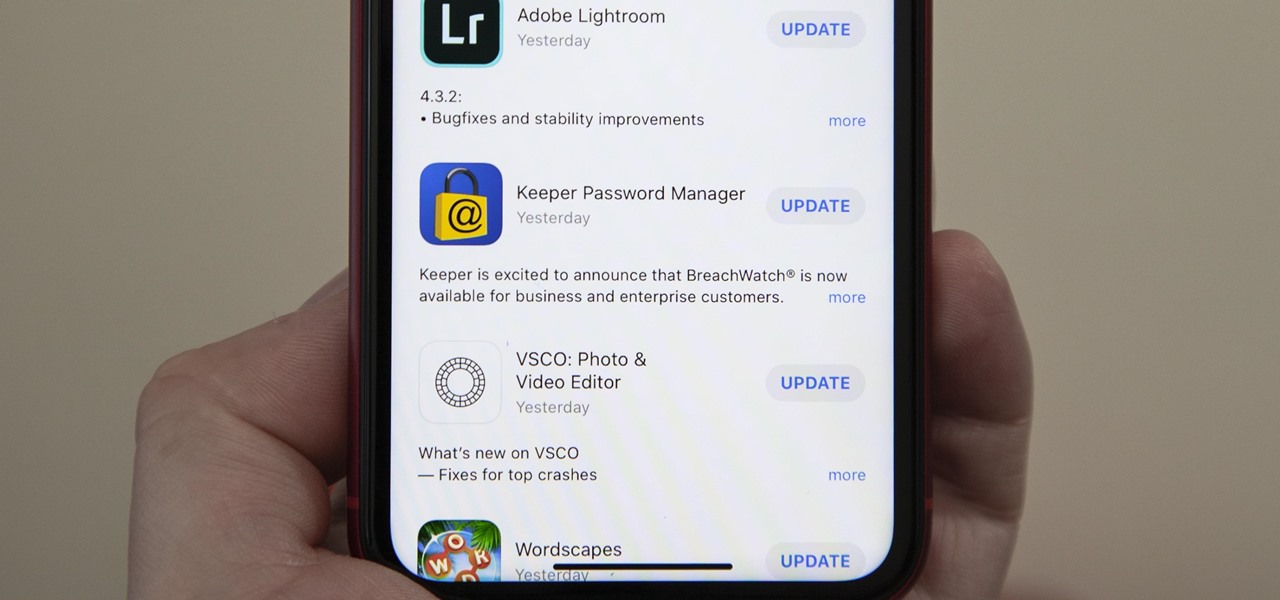
Viewing available app updates and recently updated apps on your iPhone is more confusing and less obvious on iOS 13 than it was in iOS 12 and older.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

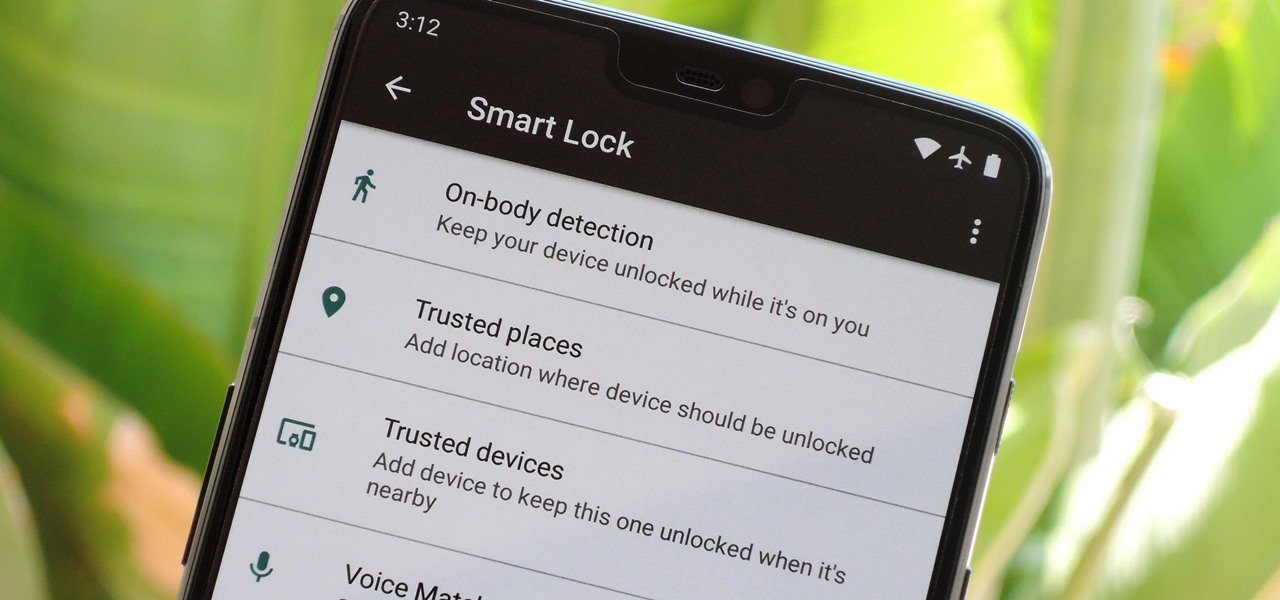
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

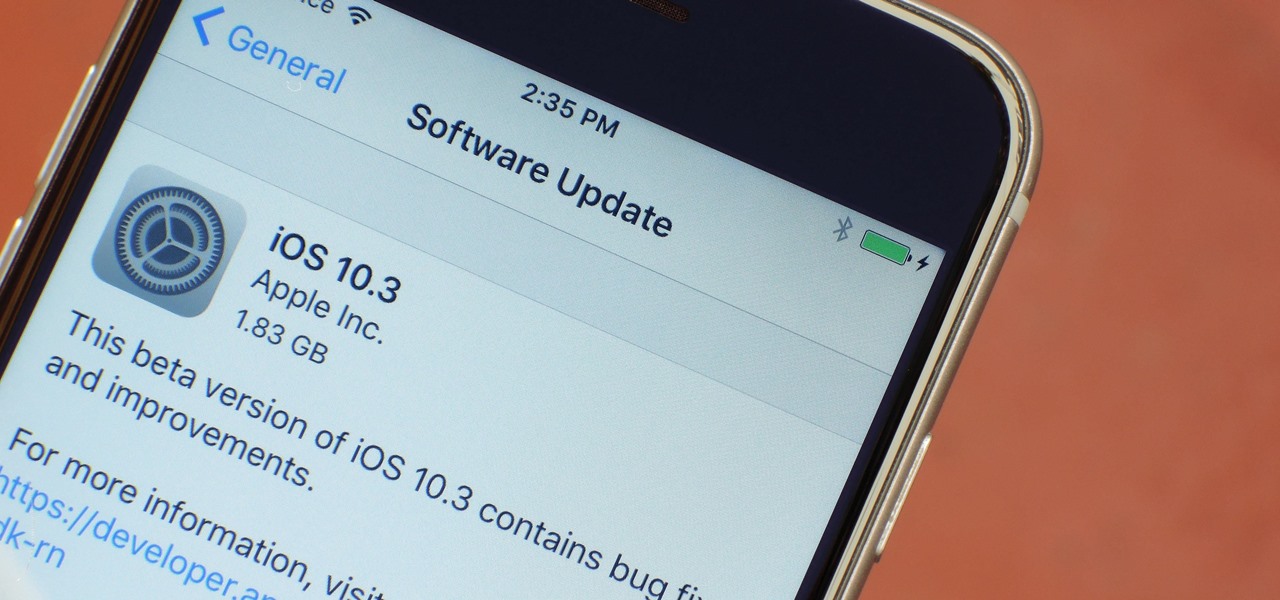
Apple just pushed out the iOS 10.3 update to everyone on March 27, so if you haven't installed it yet, make sure to do so by going to Settings -> General -> Software Update. Trust us, you'll want to.

Ask anyone that works on the development of driverless vehicle technology and there is a very good chance that AutonomouStuff will have supplied something to their project.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

The stock Camera and Photos apps are great for taking basic pictures and doing some quick edits, but if you're serious about making your iPhone photos the best they can be, you can't stop there.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.