In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Mastering the concepts of the BOOT.INI file (the boot loader) in Windows XP to better control your Windows configuration.
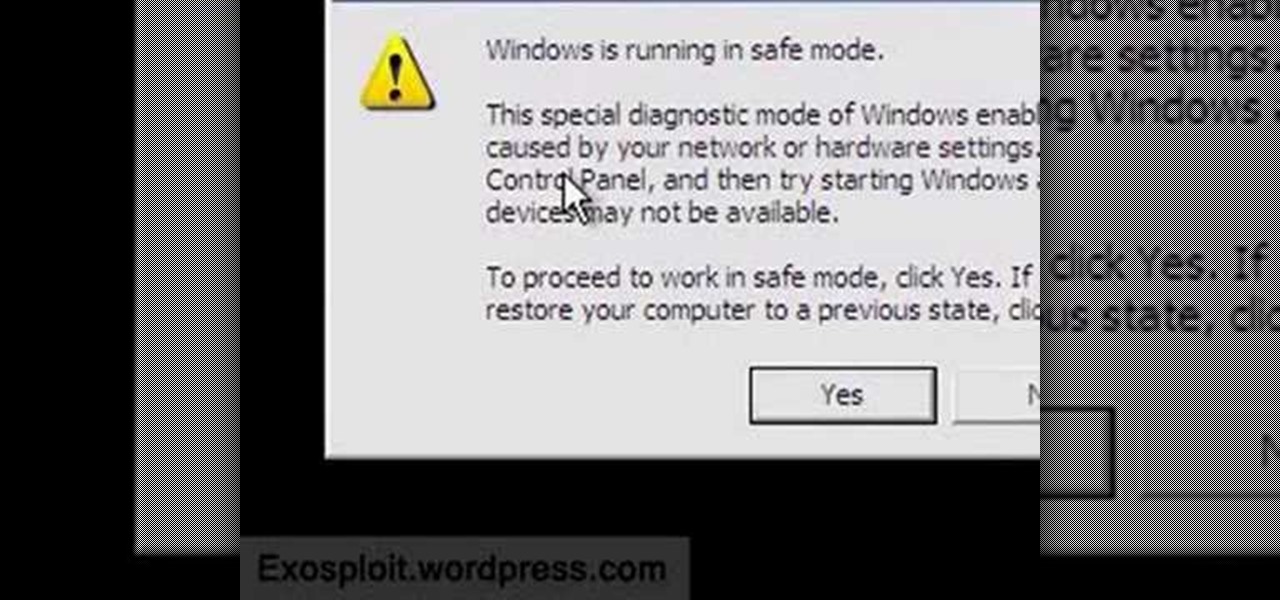
This video will show you how to boot in safe mode on Windows XP. Just follow these instructions from the video. Now go to Start -> Run and type in msconfig. and click OK. Now select the BOOT.INI tab and select /SAFEBOOT, click apply and close and then it will prompt you to restart. After you restart a message will appear. Click Yes and you will notice that your screen resolution is small and you will have the classic theme. To return to normal mode just repeat the steps and uncheck the BOOT.I...

In this tutorial, we learn how to clear an internet cache with Don Schechter. First, you need to click on the start menu, then find the "run" link. Type in "Msconfig", then click "ok". Now, click on the "general" tab, then click on the button next to "selective startup". Now, unclick the check marks next to "process systyem.ini, process win.ini, and load startup items". Click "ok", then restart your computer. Now, go to the "system tools" program in your Control Panel and select the file you ...
In this tutorial, learn how to fix a missing or corrupt ntoskrnl.exe file on your PC. Cause:
Check out how to save your user settings in Microsoft Visual Studio using C# programming, that way when you restart the program, it can remember some of your important information. This will specifically show you how to save your user settings using the .NET Framework instead of working with custom INI files.

If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...

If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

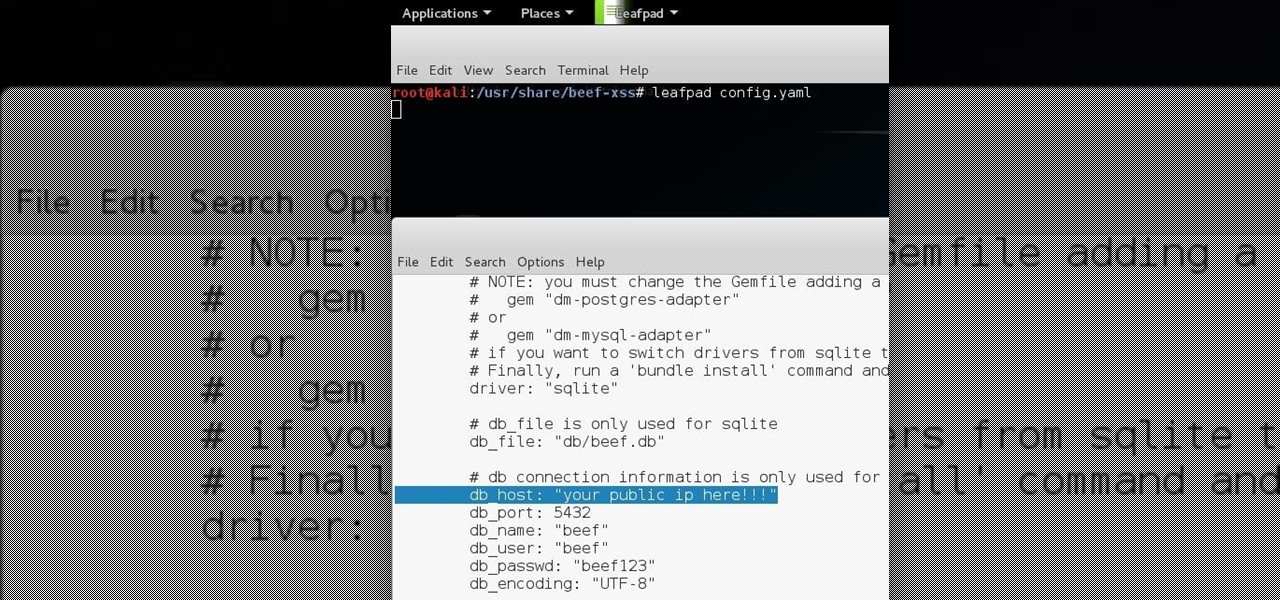
Hello all Just thought id share how ive managed to get beef working over the internet.

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).