
How To: Executive Privilege
In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.


In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Suturing wounds is one of the most important parts of any doctor's job, and learning how to do so should be among the first priorities of any medical student. This three-part video covers all of the basics of suturing a wound in a hospital setting. It features information on infiltrating anesthetic, choosing how many sutures to use, and other techniques.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Looking for an easy way to share big files over the Internet without having to pay for the privilege? With the right Internet services, it's easy. This home computing how-to from the folks at CNET TV presents an overview of a number of the better and most popular file sharing websites, some of which will permit you to upload files in excess of 1 GB. For more information, and to get started sharing your own big files over the web, watch this free video tutorial.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

Admin accounts are given special privileges to change the system (like installing programs) that user accounts are not. This tutorial shows you a quick way to check using Windows 7's calendar, and also how to go through the Control Panel to find out if you're an Admin or general User on your computer.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

According to Dr. Lindsey Fitzharris of The Chirurgeon's Apprentice, hospitals during the first half of the nineteenth century were known as "Houses of Death."

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.
Like everyone, you're on Facebook. And, also like everyone, you'd like to control the access your Facebook apps have BEFORE you even install them. Well, you can, with a sweet little Firefox add-on called FB-Secure. Take control of Facebook app privileges before they read your secret diary.

Driving is crucial to survival, but it's also a privilege, not a right. Contained in this video are the crucial steps that you'll need to take to ace that driving test with flying colors and get that license. Practice makes perfect!

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.
There's a fine line between order and chaos in group chats. With all the cross-talk, threads can easily devolve into a random mess that has nothing to do with the original discussion topic. WhatsApp group chats certainly aren't immune to this problem, but they've recently taken a step in the right direction.

Facebook knows who all of your closest friends and family are. When you backpacked across Europe last summer, they went along on the trip. Remember that break up two years ago? Yeah, they were there. The breakfast you ate this morning? They probably have a picture of it. They're even right under your own feet.

Skateboarding trick tips on how to do Casper Flips and Hospital Flips.
Are you willing to do whatever it takes to gain host privileges in COD: Black Ops Annihilation Shangri-La Zombies? If you answered yes to that question, this is the video for you. Watch and learn how to use a lag switch to become host.

While numerous examples exist of hospitals deploying the HoloLens to assist doctors, surgeons, medical professionals, and students while treating patients, California's Lucile Packard Children's Hospital Stanford is actually using the augmented reality headset to improve the patient's experience.
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.
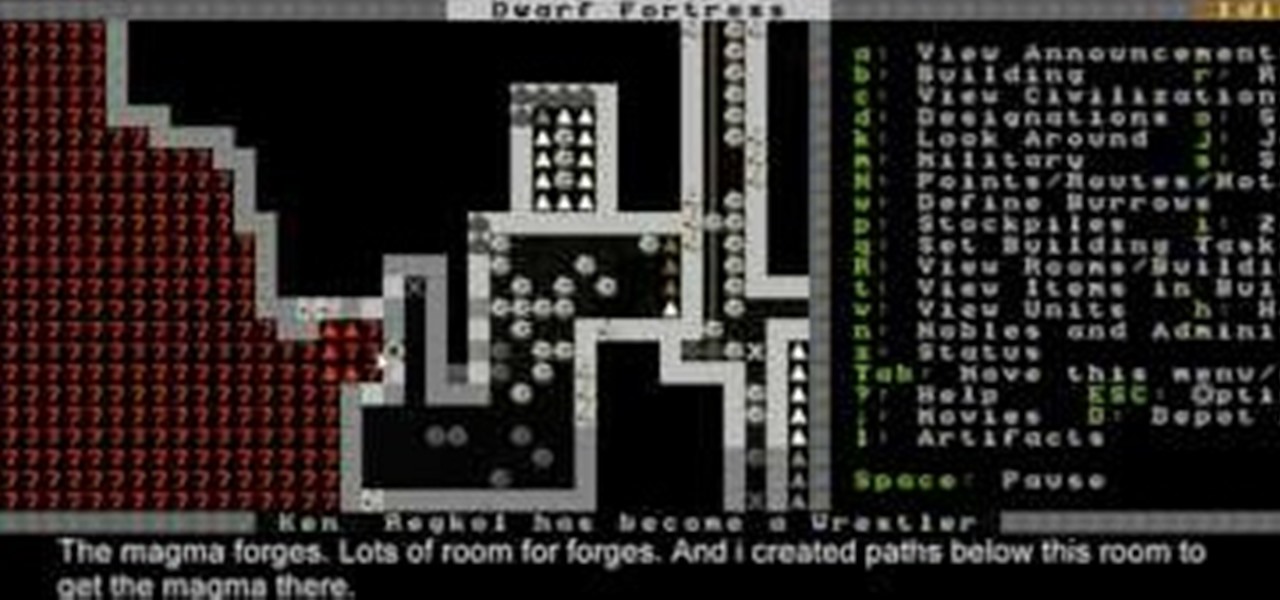
This video will show you how to build and use hospitals to take care of your dwarves in Dwarf Fortress 2010. It also discusses what happens when you abandon and then reclaim your fortress.

In this video, we learn how to make a hospital bed while it's occupied. First, take the top blanket off then take the linens off and make sure the patient is lying on their side. After this, roll the linens towards the patient, then replace new ones where the old linens were originally at. After this, put down a moisture sheet and place it under the clean sheet. Now, put the side table up and roll the patient over and let them know there will be a bump in the middle. Now, move to the other si...

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.
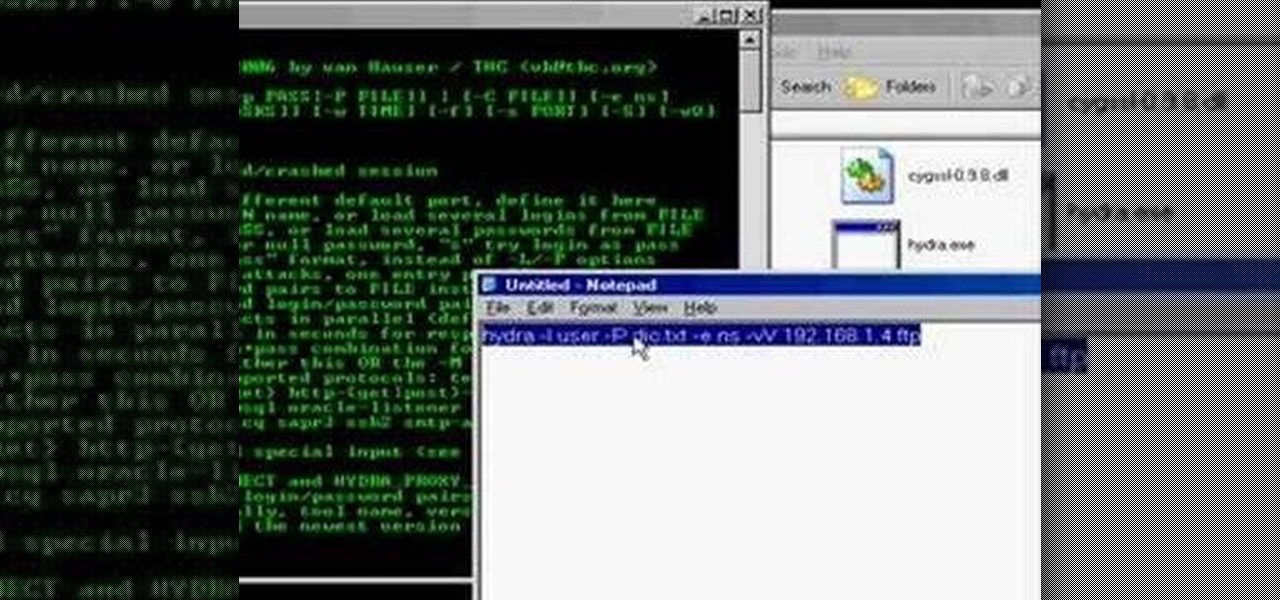
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Augmented reality has given companies worldwide great powers for innovating business practices and engaging customers, but on Monday, Honda demonstrated that with great power, also comes great social responsibility.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Hospitals are places we go to get well, and we don't expect to get sick or sicker there. But a study from researchers at the Cleveland Clinic, Case Western Reserve University School of Medicine, and Cleveland VA Medical Center in Ohio found that hospital floors in patient rooms were frequently contaminated with healthcare-associated pathogens—often dangerous multi-drug resistant bacteria.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.
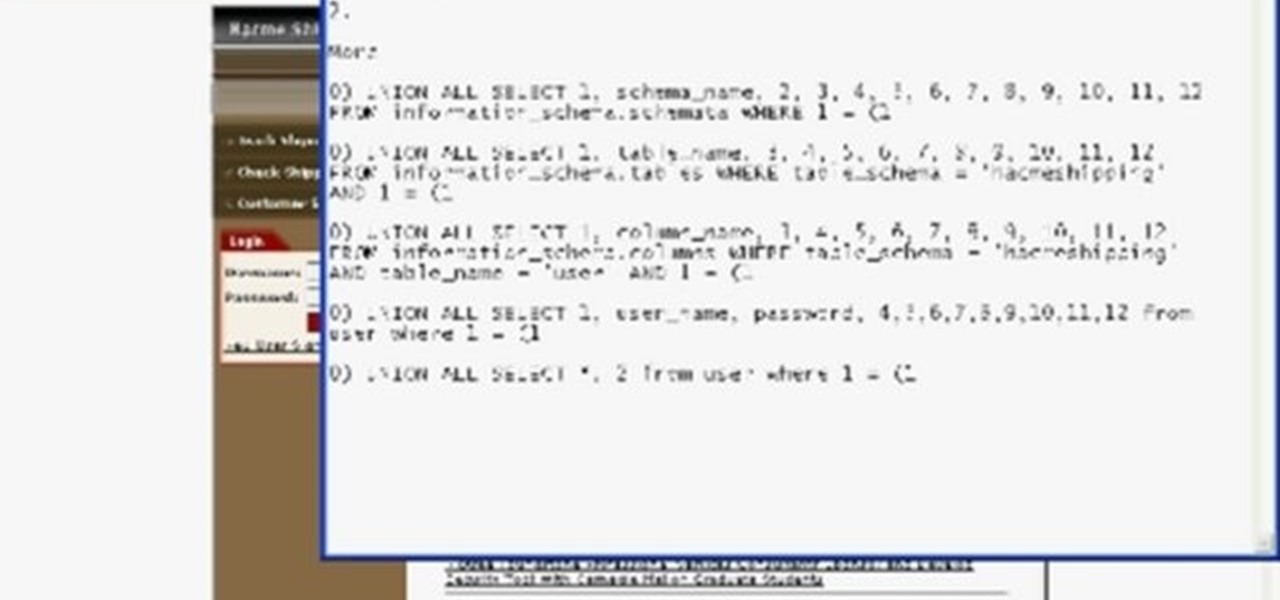
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

Head wounds are among the very worse types of wound, and as a results are very fun and popular subjects for representation in film. This video will teach you how to create an open gash wound on the head of your actor without taking a bottle to it. The wound looks very real, make sure you don't let your actor get near a hospital!

If you've just been shot but can't be bothered with a trip to the hospital you may want to know how to remove a bullet yourself. Learn how to remove the bullet as well as clean and cauterize, and bandage the wound.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.