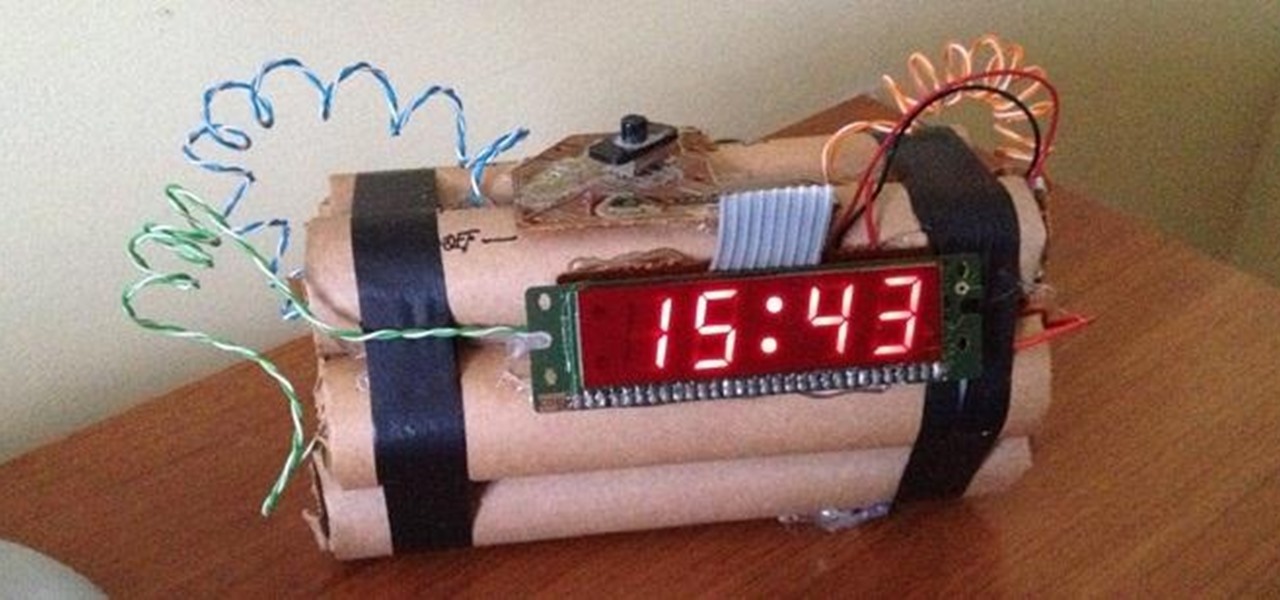
Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Once you contour your face you never go back. That's because contouring - or using varying shades of makeup (bronzers, foundations, highlighters, concealers) that are lighter or darker than your skin - helps define your features. Alternatively, contouring can also fake features you don't have and cover up features that you're less fond of.

Sometimes it may not be the best idea to apply foundation before going out. It may sweat away, get all over you clothes, or just be uncomfortable on those hot and humid days. This video will show you exactly how to achieve a flawless, concealed look without using any foundations; just moisturizers and powders.

Even, natural-looking foundation that covers up redness and flaws but doesn't look caked on or fake is the desired basis of any makeup look. But it just so happens that the rudimentary skill of applying foundation evenly is one of the hardest for women to master.

In order to make your own Tinted Moisturizer, you will need the following: lotion and foundation. In advance, you will need to select an appropriate foundation and moisturizer. The foundation that you choose should be very close to your current complexion. Mixing it with lotions will dilute it a bit, but it will still need to be close to your current complexion to blend in well.

Improve your skin’s appearance by choosing the right foundation formula and shade. You Will Need:

Just starting to use makeup? Or never found the perfect foundation for your skin tone. We will show you how to pick the right foundation for you.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

In this how to video learn to assess some problems that plague house foundations. Learn how to avoid and treat them with this tutorial.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Want to play the Foundations' "Build Me Up Buttercup" on your ukulele? Learn how with this free video ukulele lesson from Ukulele Mike, which presents a complete breakdown of the song and its chords. Whether you play the ukulele or bass kazoo, there is no better way to improve your chops than by learning to play your favorite songs. Not only is it more fun and much easier than running drills or memorizing a chord book by wrote, it's obviously also a wonderful way to build your repertory of so...

The author of this video explains how to combine a puff stitch and a drop stitch while crocheting a six by six inch square. She goes step by step, first showing how to create a slipknot, and then by showing how many slipknots will be needed in each chain across the square, which make the foundations. She then shows how to make a slipknot of a new thread of yarn, and how to insert it on the hook, into the original chain while creating the puff stitch. The chains are repeated, as are the puff s...

The correct position is the basis to everything. Check out this instructional wakeboarding video that shows you how to wakeboard in the correct position. Without the right foundations, achieving the advanced tricks will never happen. Learn the perfect basic position when wakeboarding by watching this tutorial video.

Ron Watson of Positive Vibe dog training studio in western Michigan with Frisbee Foundations and Dog mantic Dog Training TV explains how to do vault, stall, and rebound discrimination dog training. First, add value to a barrel by using eye contact. When the dog goes to where the reinforcement happens, feed it treats. Then order the dog off the barrel. When the dog jumps up by its own volition, then you know the technique is working. Then, set a linear vault by saying, top, and tossing the tre...

Okay, so you probably think it's majorly weird that this skincare tutorial is inspired and based on Kurk, the openly gay and cutesy Glee club member from "Glee." But actually it does make a lot of sense: Kurt has the best skin of anyone on the show.

Get tips on how to make your home more eco-friendly, especially if you plan to renovate it.

In order to re-create Nene Leake's glitter eye makeup look from the Real Housewives of Atlanta, you will need the following: lipstick, blush, false eyelashes, eye shadow, primer, foundation, tape, powder, glitter, eyebrow pencil, lip gloss, lip liner, and black eyeliner.

Modern dance moves have foundations in ballet, but are modified to create a unique movement. Learn modern dance moves with this free instructional dance video series.

Watch this instructional video in basic Buddhist Vipassana (Insight) Meditation. In this how-to video there is an explanation of the four foundations of mindfulness and a guided walking meditation based on creating a clear thought centred on the present reality. Learn all about how to practice walking meditation.

This tutorial video will show you how to contour and highlight your skin with makeup. Contours are "shadows" so you want to go darker than your actual skin tone.

In this series of expert video clips, you will learn how to do a bunny hop, one of the foundations of BMX freestyle tricks. Get tips on various stunts and variations on the bunny hop move from an expert freestyle rider.

Prior to this year, Time primarily relied on image markers in the magazine to trigger its special augmented reality features

The internet was ablaze this week after it was found out that evasi0n's newest jailbreak for iOS 7 secretly came bundled with a highly obfuscated Chinese app store. The application, called Taig, was filled with pirated software and was rumored to have permissions capable of tracking your information and sending it elsewhere. It was reported that the team at evad3rs financially benefited from this move, netting them a very high six-figure number close to a million dollars. The controversy incr...

Ever since the planet went crazy trying to find augmented reality creatures in Pokémon GO, we've been waiting for the next virtual object game capable of delivering a similar hit. And now, we might finally have one coming, direct from the magical world of Harry Potter.

The first alarm clock in recorded history can be traced back to ancient Greek philosopher Plato, known for laying the foundations of Western philosophy and science. Plato was said to possess a very large water clock with an alarm signal similar to that of a water organ.

Noted analyst Gene Munster is predicting that Apple's initial entry into the augmented reality wearables category will be a year later than previous reports have estimated.

"I want to make video games" — Is there anyone who hasn't ever thought that? It's almost universal among gamers to want to get on the other side of the screen and design the games themselves, especially those of us who have played less than impressive games and thought that we could do a better job. But it's hard to know where to start — or how — when it comes to creating our own games.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Only a handful of food products are impervious to spoilage—dried rice, salt, sugar—but even among those, honey is unique in that it remains edible without any preparation necessary. It's like this: if you came across honey in an Egyptian tomb, as archaeologists have, you could taste it and never guess it was thousands of years old.

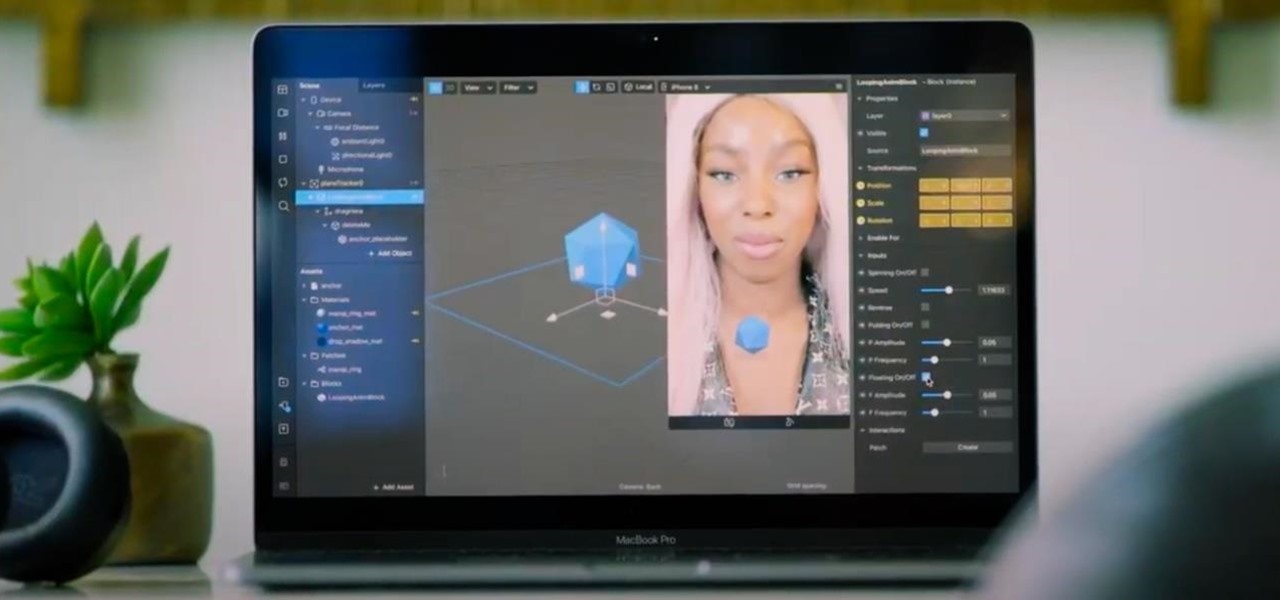
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.