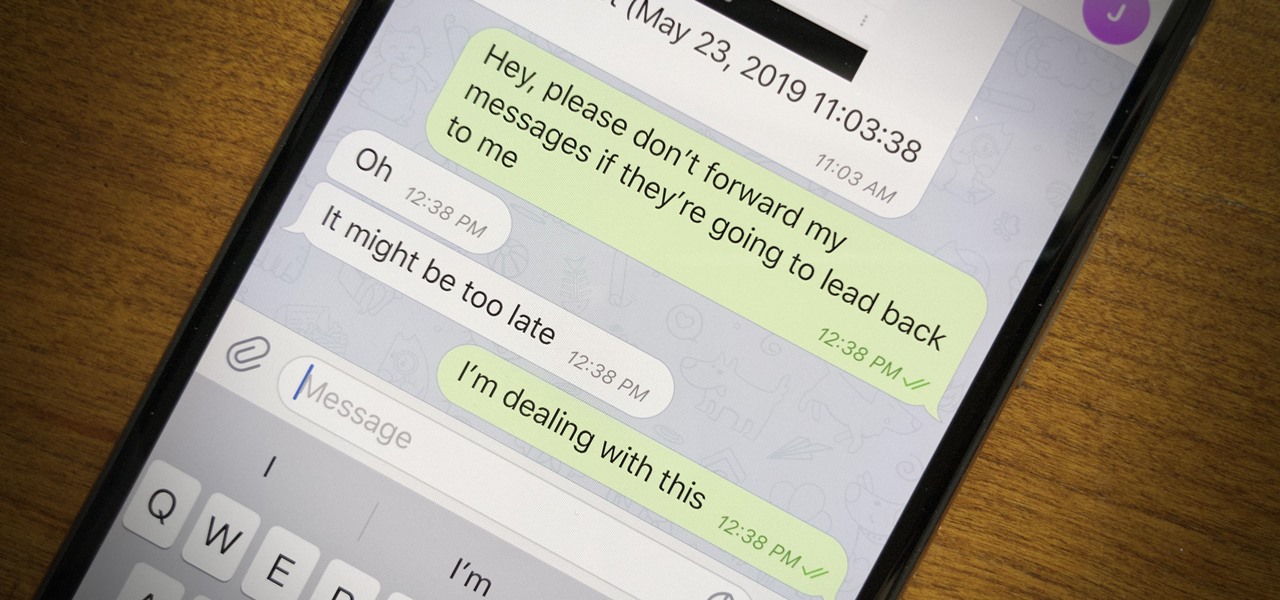
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Luckily, you can make your messages anonymous, so anyone receiving messages of yours that are forwarded won't be able to see you originally sent the message.

When someone sends you a funny video, image, tweet, what have you, often the first thing you want to do is share it with someone else. Instead of copying the link and jumping over to another chat to do so, WhatsApp makes it easy to share content right from the thread you received it in, via the forward feature.
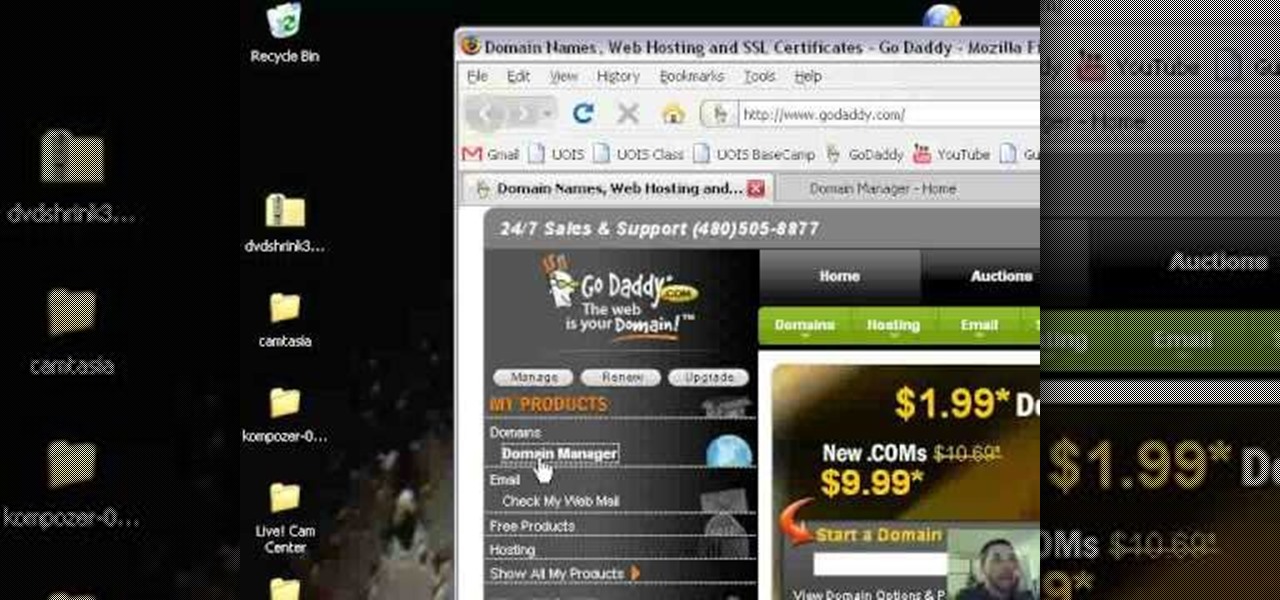
Ken Appleby demonstrates how to forward a domain with GoDaddy. First, open your web browser and log onto your GoDaddy account. Click the domain manager option on the left hand side of the home page and log in if necessary. Choose the domain that you would like to forward. Find the forwarding option which is located on the top central portion of the domain manager window. Tick the enable forwarding box. Then, type the address that you would like to forward your domain to in the forward to box....

For those of you who are unaware of who Kakashi is, he is a popular character in the media franchise Naruto and is the titular character's teacher.

In this how to video, you will learn how to play Borderlands LAN online using Tunngle. You will need Borderlands and Tunngle in order to do this. First, open Tunngle and then log in to Borderlands. Go to LAN game and select your character. From here, join a game. You are now ready to play. If your friend is not showing up, press E to refresh the list and make sure the port 11155 is being forwarded by the host. To get the in game mic to work, you must go to online game and make sure you log in...

This video teaches you how to make a steampunk bunny. You want to start off by making a blob with a fairly light color. Then you want to use a sharp stainless steel tool to create a round head. Make sure to make the head of the bunny is forwarded a little bit so that it looks like a bunny. Next, using your hands create a tail in the back of the bunny. Insert one of the bigger eyes using the little wire. Go ahead take your tool and carve out the nose, the cheeks and the mouth. Next you want to...

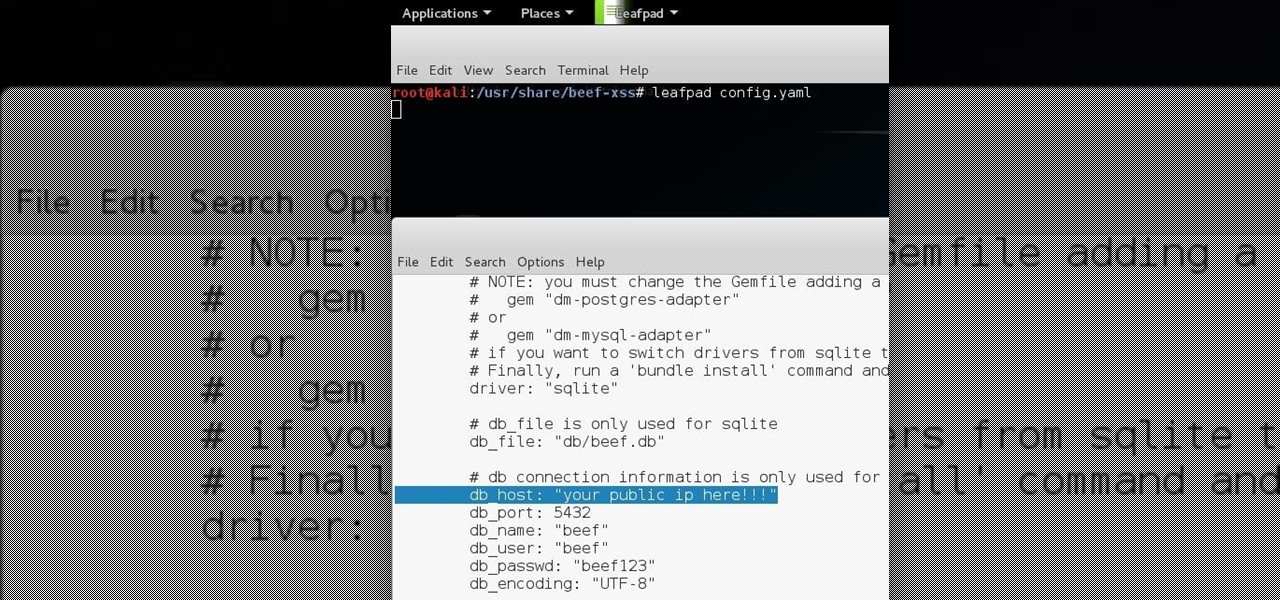
Hello all Just thought id share how ive managed to get beef working over the internet.

This is a walkthrough of the hunt for our solar system and home planet Earth. The searching is fast forwarded. Saw a picture on the net of a vague location of where it might be. This is an Easter egg in Spore.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

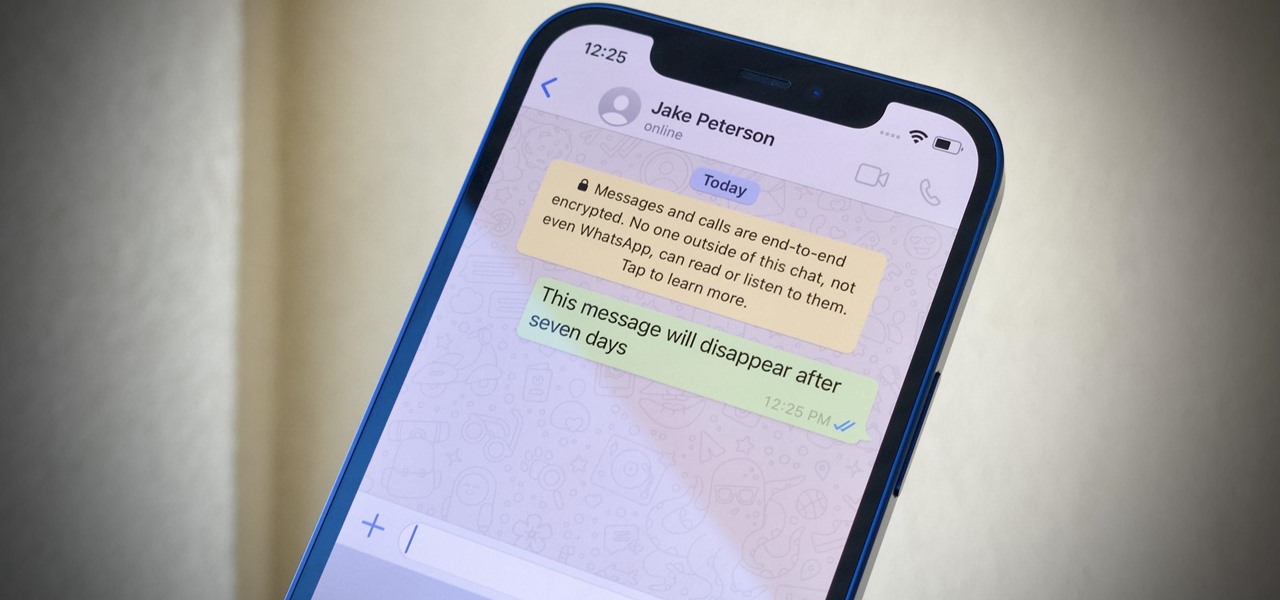
Sometimes, keeping every message comes in handy. Maybe you want to relive fun conversations from months or years ago, or perhaps you need to recall a piece of data such as an address, name, or link. However, not all chats need to stick around forever. Whether you're concerned about privacy or just keeping your threads clutter-free, WhatsApp's "disappearing messages" may be what you're looking for.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

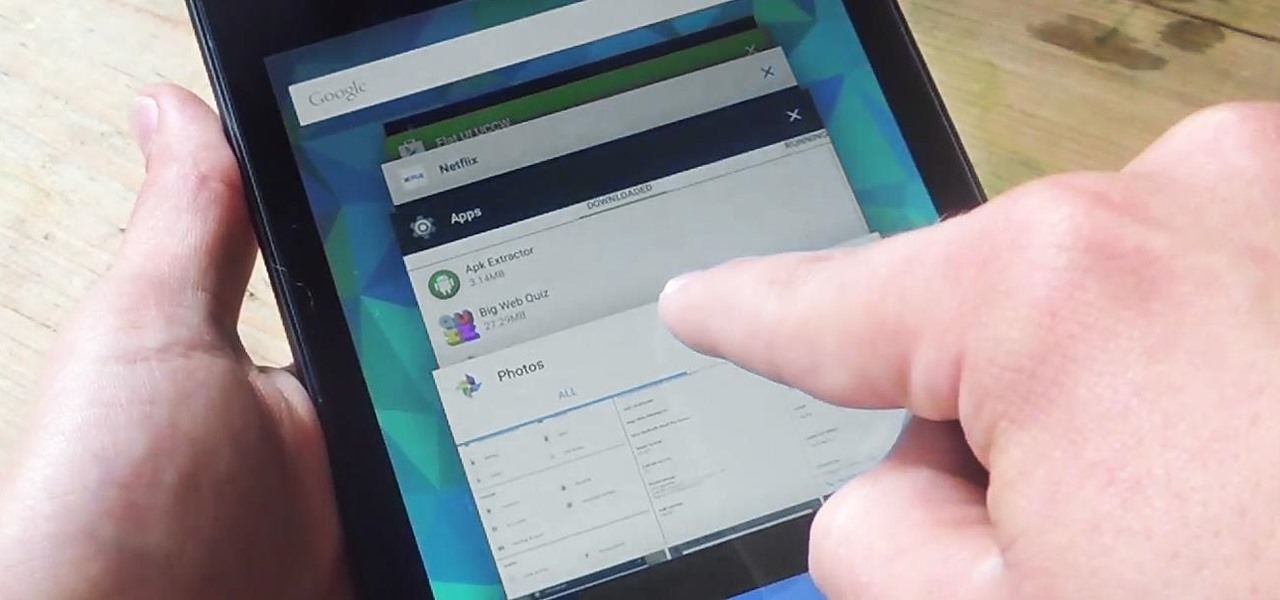
On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data.

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

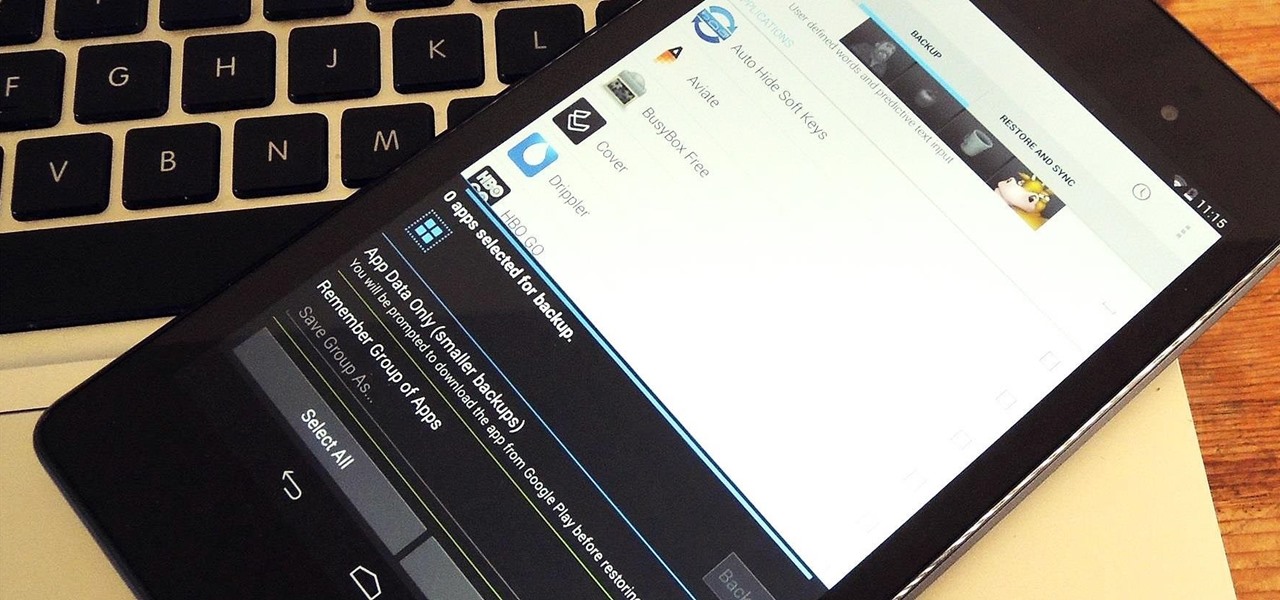
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

There are some calls you really don't want to miss. Whether it's "I'm going into labor" or "We have some questions about your résumé," not being able to answer or respond to certain messages can cause some serious problems.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Here's a routine that I'm sure all of us smartphone users go through at least several times a day. You notice your Samsung Galaxy S4's notification LED blinking, grab your phone to see what it is, and enter your PIN. Only instead of anything important, you find that it's just some online store enticing you with sales promotions, or some other email that you could have easily done without.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Whenever you buy a newer iPhone model, you get a set of Apple EarPods with remote and microphone built-in. Aside from their comfortable design and high-quality sound they provide, these headphones offer additional functionality beyond just pausing and playing music.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.