Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.
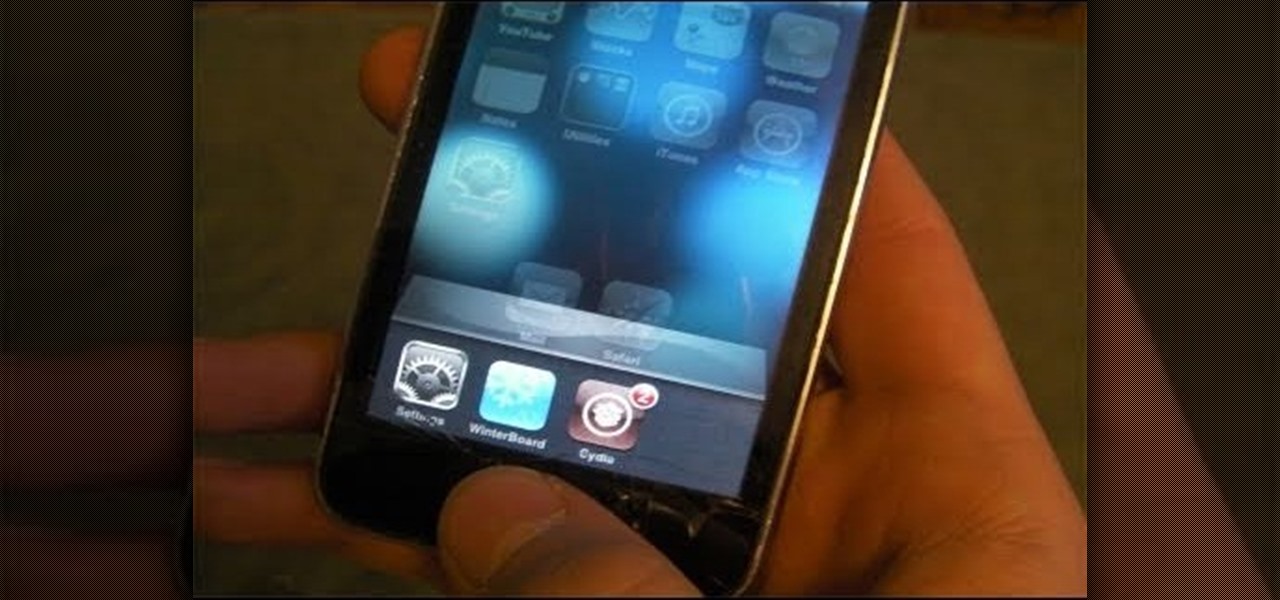
Interested in using multitasking on your iPhone 3G or second-generation iPod Touch? This iPhone hacker's how-to will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to learn how to enable multitasking on your own iPhone or iPod Touch, take a look.
In this clip, you'll learn how to set up and use USB Internet tethering on a Palm Pre mobile phone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started using USB tethering on your own Palm Pre, watch this hacker's how-to.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

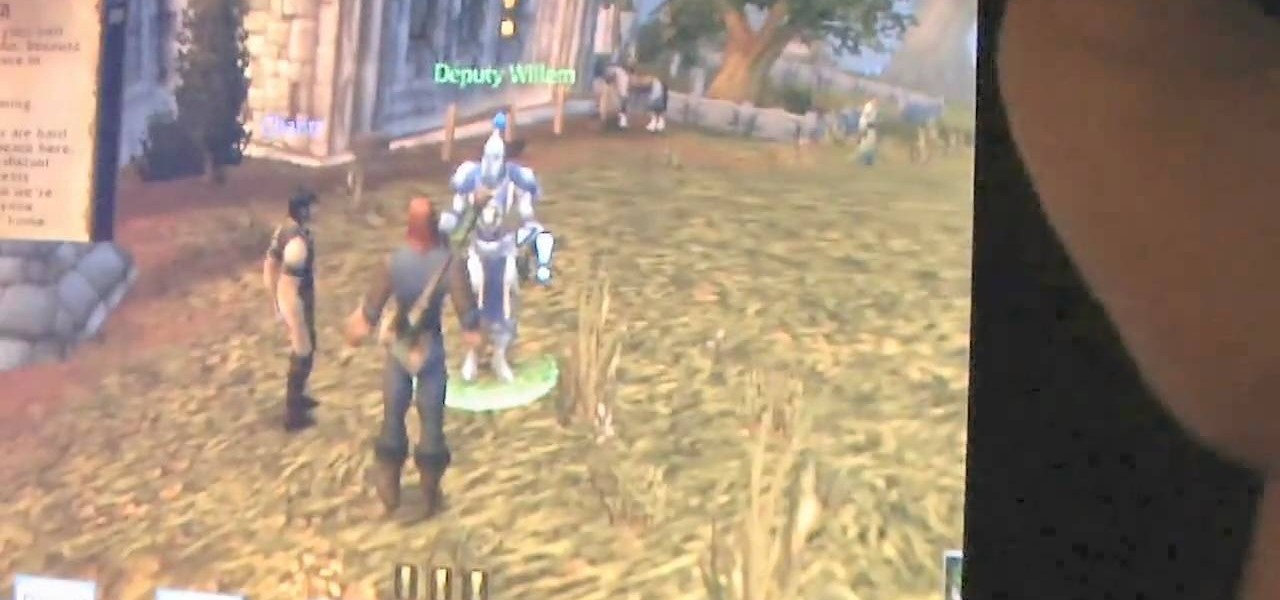
Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to play WoW on your iPod.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to mod a USB flash drive.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

If you're looking for the hacker device on Moon while playing the Rezurrection DLC for Black Ops, take a look at this guide on where to find it. Make sure that you pay attention to the airlocks, as you can only carry the hacker device or the space suit, but not both at the same time.

In this clip, you'll learn how to extract serial data from the $80 Mattel Mindflex or Star Wars Force Trainer. For more information, including detailed, step-by-step instructions, and to get started creating your own working EEG/BCI, watch this very-neat hacker's how-to.

While Google Maps is useful for finding addresses and calculating directions, it's not, strictly speaking, very fun. Unless, of course, you know how to hack it. This hacker's how-to from Tekzilla will show you how to access a number of Easter eggs and hidden features like a geography quiz game.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.

Want to mod your HTC HD2 Microsoft Windows smartphone to use wireless charging—without breaking your warantee in the process? It can be done! And quite easily at that. For complete details, and to get started modding your own HD2 phone to work with wireless chargers, watch this handy hacker's how-to.

In this video tutorial, you'll learn how to add WiFi Internet connectivity to a normal Sprint Palm Pixi smartphone with a quick and easy radio board (radioboard) swap. For more information, including detailed, step-by-step instructions on how to add WiFi capabilities to your own Palm Pixi phone, watch this hacker's how to.

If you have an extra speaker cabinet, a broken XLR cable and a little bit of soldering knowledge, you can create a functional kick drum microphone in just a few minutes' time. This audio engineer's guide will walk you through the entire process. For detailed, step-by-step instructions, and to get started building your own sub mic for extra low-end, watch this hacker's how-to.

Paste this code: shutdown -s -t 10 -c "Your Message Here" One of our viewers brought up that -s would simply shut down your PC, and not keep restarting it. To do so, substitute -s for -r and you should be set!

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.

Learn how to replicate the much-publicized iPhone lock-screen hack (before Apple patches it)! This hacker's how-to will teach you everything you need to know. For complete instructions, including a detailed, step-by-step overview, and to get started unlocking your friends iPhones, watch this video guide from Household Hacker.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

To some, it's sacrilege. To others, just a bit of good fun. In this clip from the folks at Lifehacker, we learn how to install and use Google's Android OS on an iPhone 4 using iDroid. Learn how to run Android on your Apple mobile device with this hacker's how-to.

Interested in rooting your HTC Evo, Desire, Incredible, Aria or Wildfire phone? With the unrEVOked jailbreaking tool, it's easy! So easy, in fact, that this hacker's how-to can present a complete overview of the process in about four and a half minutes. Learn how to root your Google Android smartphone with this video jailbreaking walkthrough.

Learn the secret to running the FaceTime video phone call app over your iPhone 4's data plan with this hacker's how-to. For all of the juicy details, and to get started making video calls over cellular internet on your own Apple iPhone 4, watch this video tutorial.

In this clip, we learn how to jailbreak an Apple moble device running iOS 4.1. This, of course, includes the iPhone 4, iPod Touch and iPad. Learn how to download an run the limera1n jailbreak tool with this hacker's how-to.

In this clip, you'll learn how to jailbreak and unlock an iPhone 3G running iOS 4 for use on the T-Mobile wireless network. For more information, including detailed, step-by-step instructions, and to get started jailbreaking and unlocking your own iOS 4 iPhone 3G, watch this hacker's how-to from Zedomax.

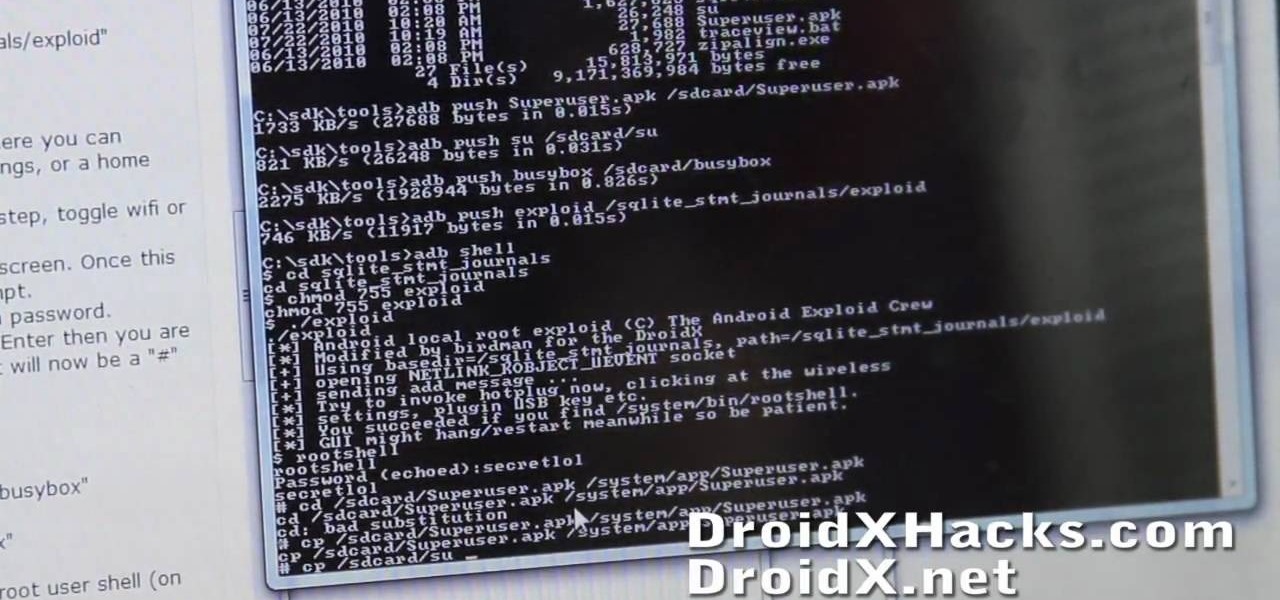
Root your Droid X Google Android smartphone and run custom ROMs! This hacker's how-to presents a thorough, step-by-step overview on unlocking and rooting a Motorola Droid X smartphone. For detailed instructions, and to get started rooting your own Motorola Droid X phone, watch this free video tutorial.

When you sign up with Gmail, Google gives you both an "@gmail.com" address and an "@googlemail.com" address. You can take advantage of this fact to reduce the amount of spam you receive. And this video tutorial from the people at CNET TV will show you how. Regain control of your Gmail inbox with this hacker's how-to.

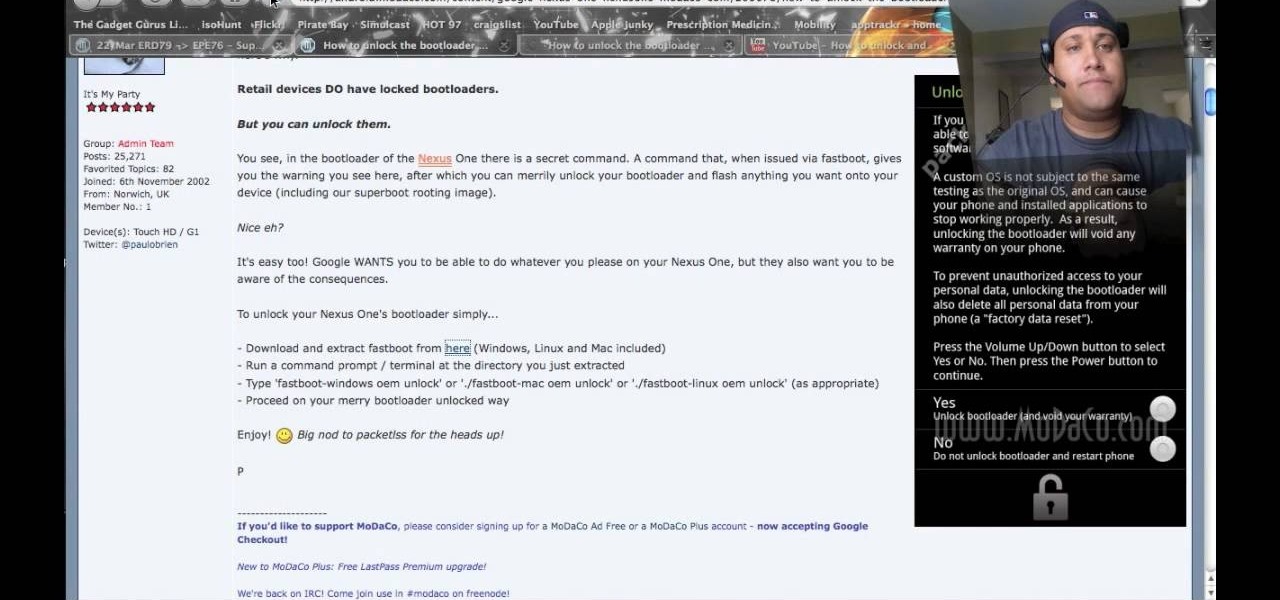
Want to root your Google Nexus One Android smartphone from a Mac? It's simple! So simple, in fact, that a complete walkthrough of the process can be presented in just over eight minutes' time. For the specifics, and to get started running custom ROMs on your own Nexus One phone, watch this hacker's how-to.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Five Phases of Hacking:- The five phases of Hacking are as follow: