Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.

Video: . Today I bring you my first Christmas themed video!Here there are some DIY ideas to decorate your room for the holiday season. They are really easy and affordable so I hope you like them!

How do you begin to explain the nostalgia that's felt when you play a game from your childhood? You can't. The only thing that will alleviate this feeling is experiencing it again.

Before you start a paint job you will need to prime the surface of the wall. Priming is necessary if the wall is a dark color or stained or bumpy at all. Once you've decided to prime and paint, check out this tutorial for advice on how to go about it.

Make your own custom characters for Icy Tower! It's as easy as drawing stick figures, believe it or not. Only stickman don't look as cool, unless of course it's a stickman that you want to use as your Icy Tower character.

This guide is all about hacking Icy Tower. You will need to download Cheat Engine 5.5 before you can try this hack. See what you can do.

Find a way to get a combo achievement in Icy Tower… by cheating. With Cheat Engine, it's easy to hack Icy Towers. See for yourself.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Today I decided to try out a cool new DIY craft! But seriously, Superwowstyle and DIY crafts! Did you expect? Nah! Neither did I! But these bling shoes were a DIY fashion that I simply could not resist when I realized what potential these old shoes have. the shoes decoration just had to happen once the idea hit my head!

First inspired by the Team Traeger recipe, I decided to make my own video recipe so as many people as possible can make their own version, too.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

This is an amazing appetizer, called Tot Chos. This is for anyone and everyone that love bacon, tater tots, gravy, and cheese. Such an awesome combination! You can't go wrong. An explosion of flavor with every bite. I was first introduced to these over a year ago at a burger joint here in AZ. It was hooked after the first bite. So I decided to make them. Enjoy!

Barbie is all set to go for her party. With her sparkling dress, she is going to intoxicate everyone. The only thing that would add to this, would be Barbie accessories. So why not make some beautiful headbands for Barbie that would add more grace to her attire. This video is for all who love dressing up their dolls.

Work and School can be boring at times, that's why we do what we can to keep ourselves entertained. So I decided to come up with this funny prank so you can make school or work fun again. You will need a water balloon and someone's clipboard which contains important documents! This is a very mean prank and can definitely get you in trouble so make sure you know what you're doing. Watch the video tutorial provided to get an idea of how to pull this off.

The other day I was perusing my Instagram when I came upon a curious hashtag... #OnePotPasta. Intrigued, I investigated further and discovered a whole world that was previously unbeknownst to me.

We recently showed you the Misfit Shine, a no-charge, app-oriented fitness tracker that you can grab for a hundred bucks. Sony has also decided to get in on the action with their Smartband SWR10—but this thing is so much more than a fitness tracker...the Smartband wants to "log your day, every day".

You've been there. Those precarious few seconds between dropping your expensive smartphone right on its face and reaching down to survey the damage. Or maybe you got thrown in a pool while your device was in your pocket, or you dropped that sucker right into the toilet bowl. Heck, I've managed to accidentally wash two devices by leaving them in my pants pocket when throwing in a load of laundry.

PULLED GARLIC CHICKEN TASTES LIKE GARLIC HOT WINGS Video: .

The following video is the result of months of viewer requests to create a single-shot airsoft rifle. The design I decided to film the video around ended up being quite durable, and very capable of being loaded with single pellets, or multiple pellets to operate as a shotgun.

What is the universe made of? What is the biological basis of consciousness? What is the reason for our existence?

Thought I would cross-post a piece I did a while ago.

Not having internet sucks! We do a ton online these days, from working, shopping, studying, and collaborating, to watching fail videos and endlessly clicking through memes.

Wouldn't it be awesome if your glasses could detect when it's bright outside and automatically darken? Well, the technology has been around for a while, but it'll set you back a few hundred bucks.

No one can deny that Bashar Al-Assad’s regime has been responsible for violence. But in failing to equally acknowledge the fact that NATO-backed rebels have also carried out innumerable atrocities is not only dishonest, it represents a deliberate effort by the press to manipulate the narrative of unfolding events in Syria as a one-sided war crime rather than the truth – which is the fact that Syria is in a state of civil war.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

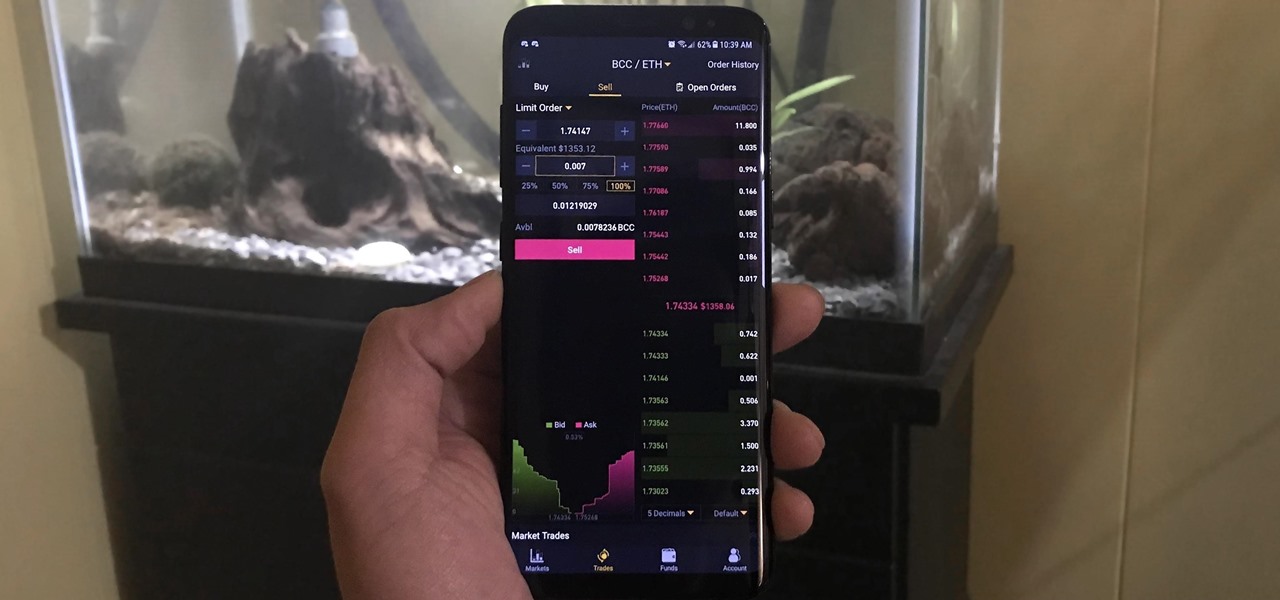
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

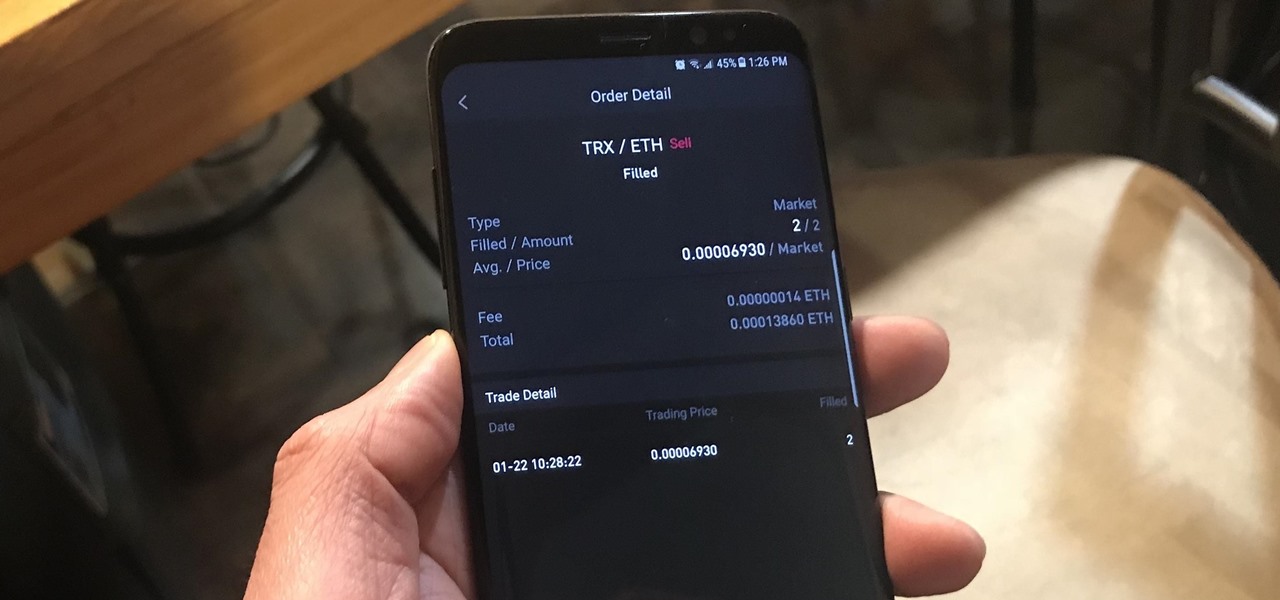
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.