Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my rookie hackers!

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

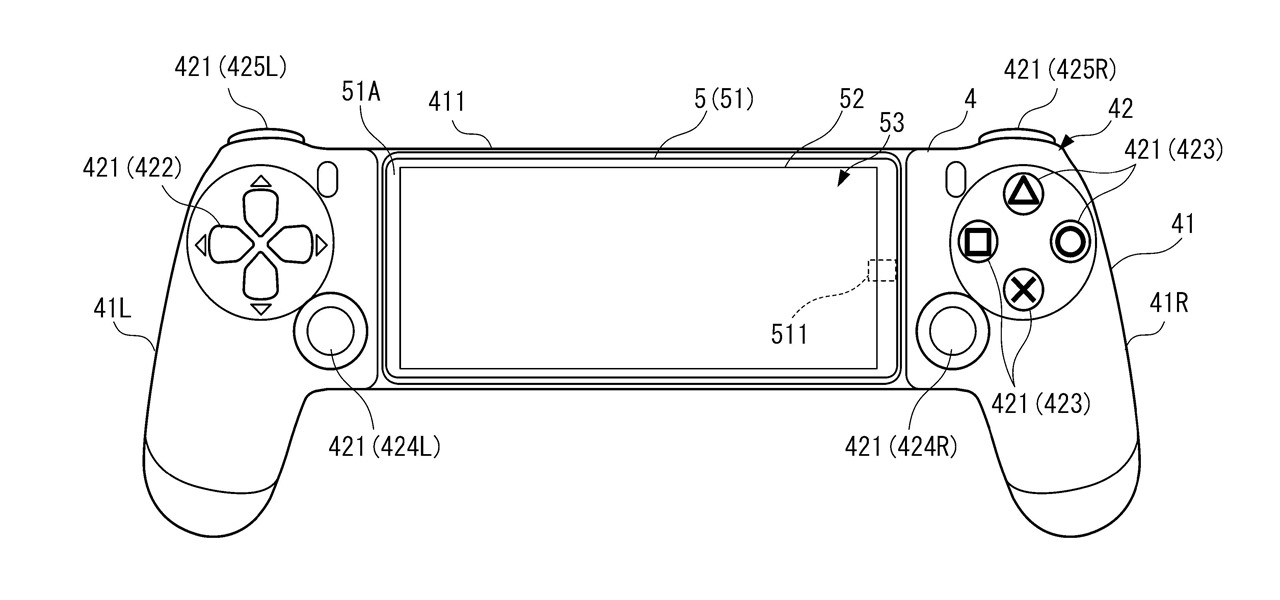
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator.

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

In this video series for puppeteers, learn how to start your own puppet company home business, with tips on where to get puppets, what equipment you need and how to train puppeteers to put on a successful puppet show. Also learn how to market your company to schools and corporations, and how incorporate yourself.
Scroogle was shut down this month due to " a combination of throttling of search requests by Google and a denial-of-service attack by an unknown person or group."

So... The MPAA, who are (obviously) in favor of SOPA, are crying about how the anti-SOPA blackouts are being caused by the ''big corporations'' and any who support it are apparently turning into pawns of said corporations.
Here is an amazing website dedicated to uncovering the dirty little secret of large corporations such as Nike and the Gap.
Monday 27 February, WikiLeaks began publishing The Global Intelligence Files – more than five million emails from the Texas-headquartered "global intelligence" company Stratfor. The emails date from between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal’s Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agenc...

Name your price for 5 indie games!http://www.wolfire.com/humble This event will run for a week and the money raised will go towards two charities. The Humble Indie bundle is a collection of five indie games where you can set your price! Want to buy the whole package (worth $80 retail) for $10, $5, $1, or even a penny? sure, go ahead, you can pay as much or as little as you want. Some have payed over a hundred for the bundle, but the average is around $7-$8 dollars.The games:

Xe Systems, the Private-Defense-Contractor-Formerly-Known-As-Blackwater, has been busy attempting to re-brand themselves. They have a new name, several new sub-names, and have at least titularly shifted their focus to training rather than mercenary work. Controversial founder Erik Prince is no longer with the company, which is now owned by a large investment consortium.

How to dress for a job interview is important to know before you go in. Watching the video will establish ways to assess company culture, exceptions, accessories to dress at a job interview and how to play it safe and professional.

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

An information technology degree from Kaplan University could be the first step towards a potential information technology career.* Earning an IT degree online can seem like a daunting task, but Kaplan University faculty and staff are available to students through email, instant messaging, and phone calls as well as weekly online seminars.

When beginning her journey at Kaplan University, Michell Sturgis was unsure how the demands of working full time and college coursework would impact her life. Kaplan University’s flexible learning schedule and online degree programs allowed her to complete her assignments at her own pace while still being able to spend quality time with her daughter. Michell took the next step forward from her associate’s degree to earning her bachelor’s degree online.

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

Not every DIY project is as executable as, say, making a potato gun. Occasionally, we observe a quixotic project that is just plain wonderful. Consider rich guy Philip Anschutz and his eponymous Anschutz Entertainment Group (AEG). His ambition to bring an NFL team to Los Angeles is a Fitzcarraldo-sized DIY project that, if the stars align, might happen in time for the 2016 season.