Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Turn your American Apparel Le Sac dress into a cute Gathered Mini. It's a fun look and really easy to accomplish. The Le Sac dress has at least TWELVE different configurations for you to enjoy, which means more closet space, and less laundry! It can be a totally new dress each day of the week. Follow along and get this easy, sexy style that's perfect for summertime.
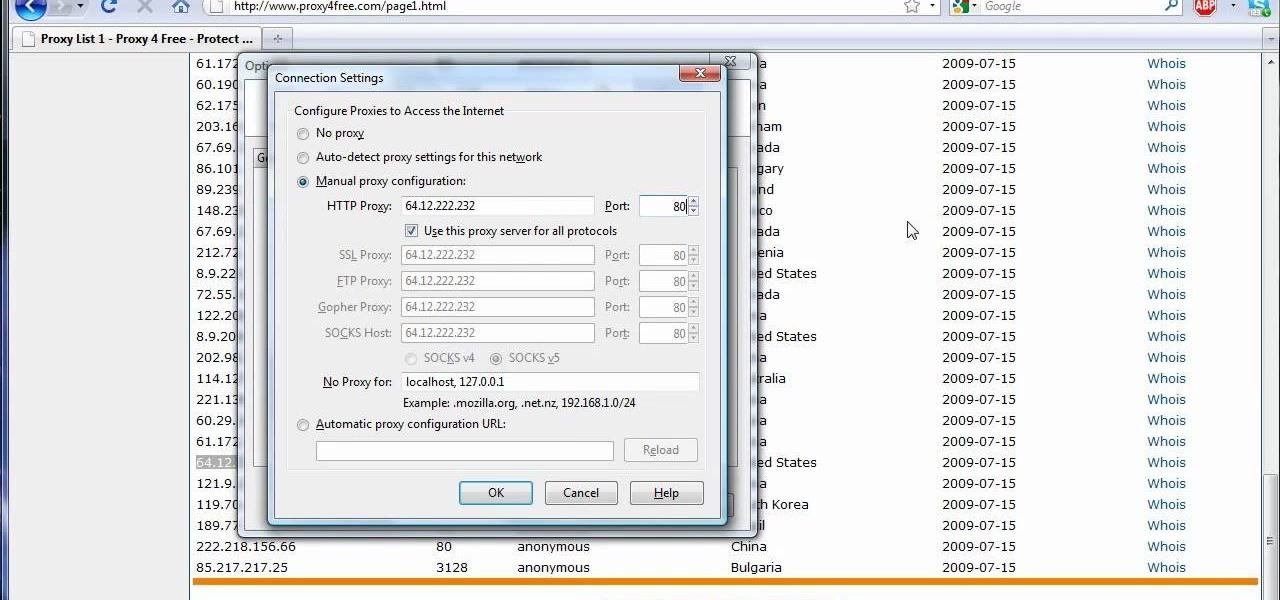
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search the free proxylist and then you can select a proxy from the one which is related to the country you are residing in. Then copy that proxy server and then go to tools and click on options and under advanced tab click on ne...
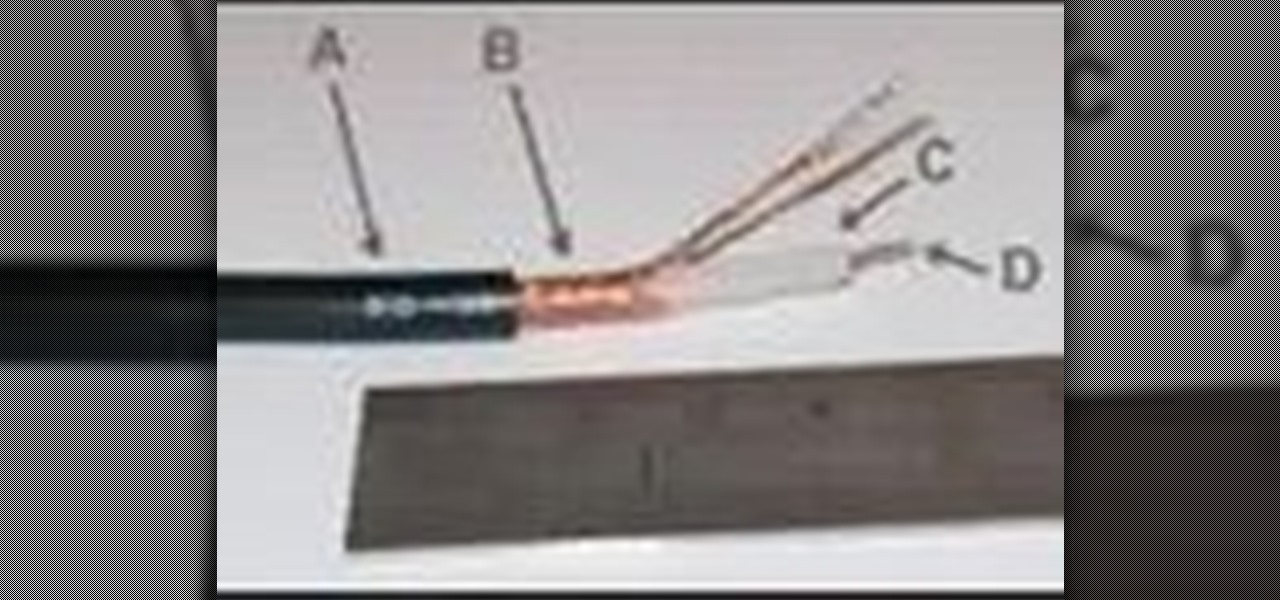
This video is about electrical wires. It describes common types, configurations of wire, and wire terminology. It explain the gauge system of rating wire size (diameter), circular mils, current capacity, and others.
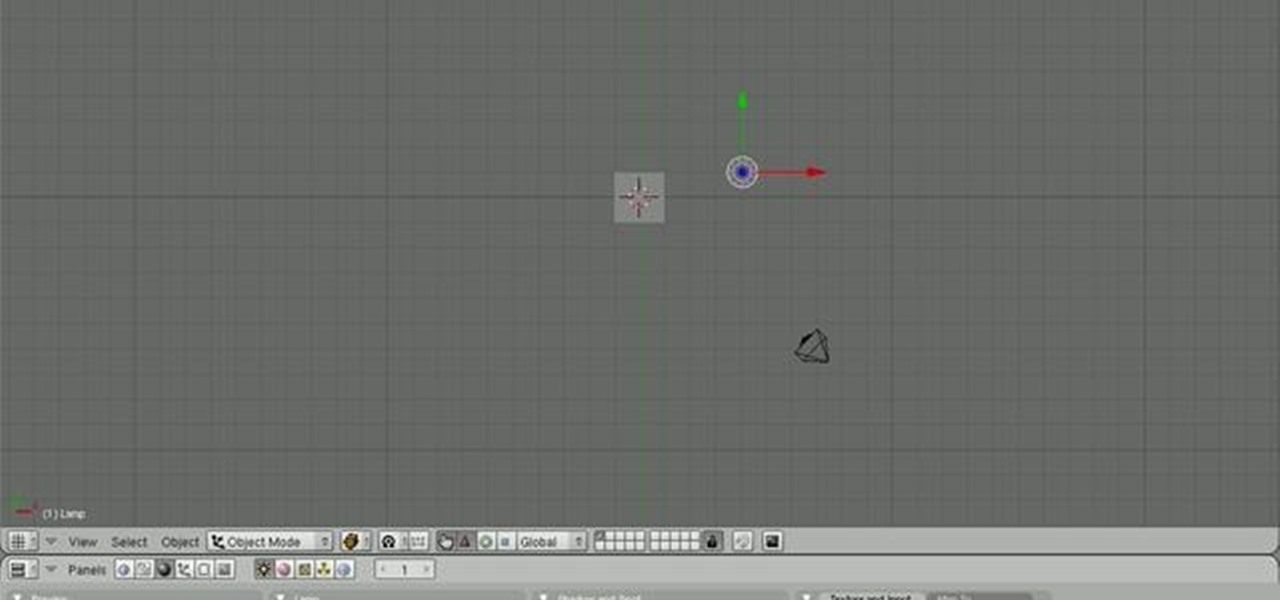
A good lighting setup is essential to effectively displaying your model. Without it your hard work might as well be for nothing. This tutorial takes a look at how to make a good three-point (+) lighting setup in Blender. The tutorial covers the different kinds of lights within Blender, the different configurations needed, and some general tips and tricks to creating a good setup within Blender. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application...
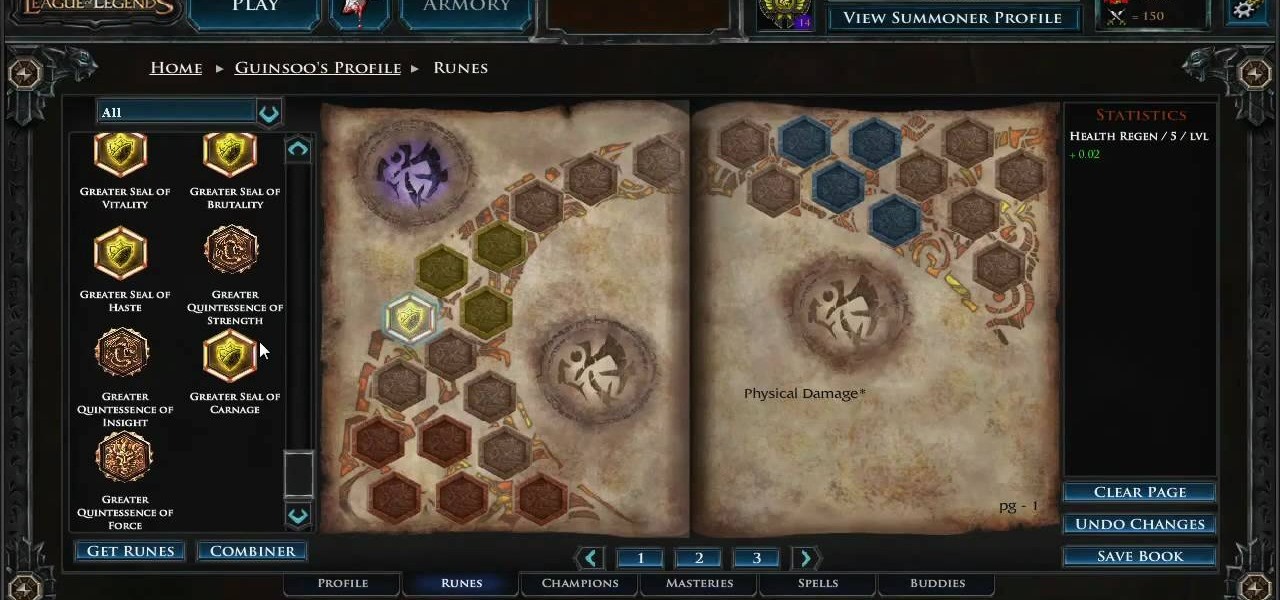
Runes are special abilities in the game which allow you customize your summoner in League of Legends. Here's how to equip runes and unlock the abilities to accumulate more runes. You can even save rune configurations in your tome and combine them to create special runes!

This cinematography tutorial explains how to setup the Redrock mircroShouldermount for the first time. The video covers two basic configurations: for a stock video camera and for an existing camera setup. The Redrock shoulder mount is a modular system designed to meet an individual's customizable needs.

In the first video, it introduces the principles and terminology of mechanical electrical switches. It covers terms such as contacts, normally open, normally closed, poles, and throws.

A video from HelpVids that shows how to disable Windows Aero visual style in Windows 7. Nero makes your windows look more beautiful by adding effects like transparency / translucency, live thumbnails, live icons etc. All these effects however use valuable system resources like memory (RAM) and processor time. This may lead to a noticeable decrease in performance in some PC configurations especially those in which the processor speed and the amount of RAM is low.

Unlock hidden feature settings and configurations in Mac OS X for the Finder, Safari and other native apps by using TinkerTool. Veronica from Tekzilla Daily introduces you to this cool new tool which brings you loads more options to customize your Mac.

Apple's range of iOS devices have something for everyone, even musicians, and especially guitarists. The AmpliTude App for the iPad and iPhone, along with the AmpliTude iRig is sure to win the hearts of tech-savvy guitar players. In these two videos, you'll learn how to use the application to make some sweet mixes.

Putting together a tattoo machine is not a matter of life or death, but it just as well may be, since you're aggregating tools for sticking a big fat needle into a person's back. And each customer, depending on his/her selected tatoos, will require a different assembly. So check out this video to learn how to assemble a tatooing machine.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

For anyone experimenting with music, learn how to create a basic synthesizer using Reaktor 5.1. This video tutorial shows us step-by-step how to create a modular synthesizer beginning with showing how to structure various instrumental sounds at different pitch levels using the software system. The pitches can be ordered in all different kinds of configurations allowing you to play around with sounds until you find the ones you want. Follow the steps outlined in this tutorial to learn how to c...

If you want to run multiple windows operating systems at the same time you first need a Windows computer, the installation disk for the operating system you want to run, and Windows Virtual PC 2007. To install this, first type in Virtual PC 2007 to Google, go to the Microsoft link and download and install the program. Now, open the Virtual PC and click next on the wizard. Name your hard disk and click next until you choose where you want this at. Now your virtual hard drive is created. Now, p...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup and load Wii games for the Dolphin Emulator.

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

Jeff Schell shows you some of the options and configurations available when working with images that do not match the dimensions of your program monitor in Premiere Pro CS3. In addition, Jeff will introduce you to the 'Automate to Timeline" feature that helps you quickly create a photo montage or slide show with the click of a button.

In this video tutorial the instructor shows how to browse the internet faster on your PSP. The normal browser built into the PSP is very slow because it does not use full ram of the PSP and because of its internal settings. These default settings of the browser make it pretty slow. So as an alternative to it you can download and use the Netfront Beta 4 browser. Basically it can be used in the same way as the normal PSP browser but as it uses good configurations and settings it makes your inte...

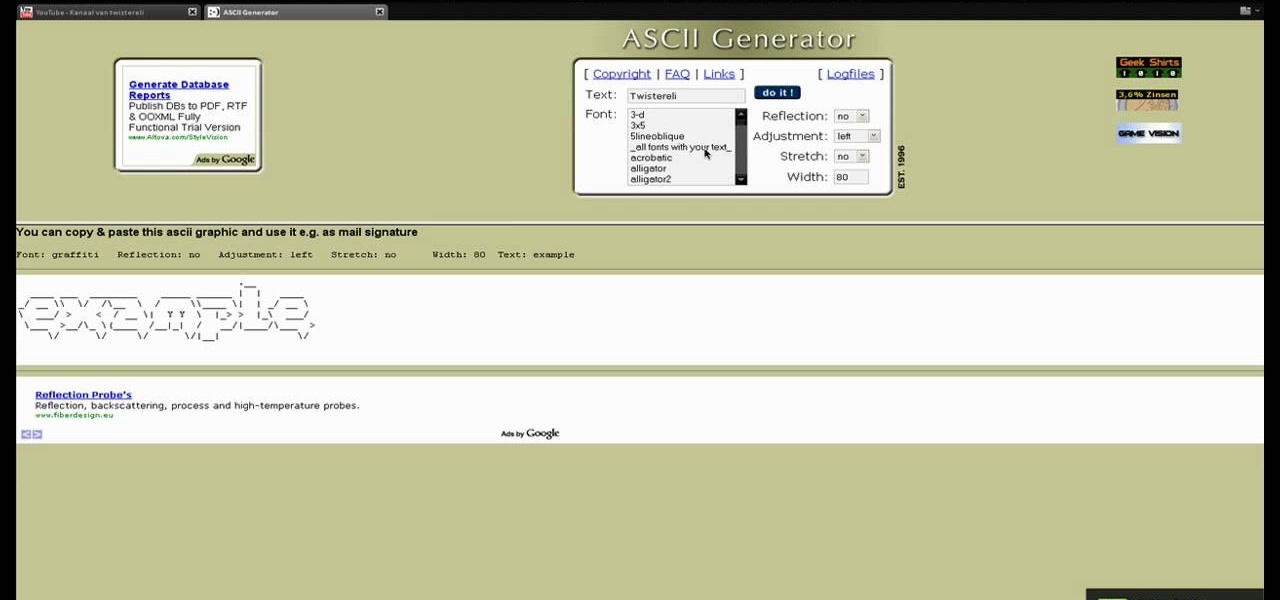
In this tutorial the author shows us how to make your own 'Subscribe' ASCII text for your channel. He says that almost every one has that text on their channels but they usually copy it from somewhere else. So in this video the author how to do this using a web application called ASCII Generator which is found at http://www.network-science.de/ascii. He goes on and shows how to generate that ASCII text using the different configurations and settings available in that web application. He shows ...

If you enjoy modding your Android device with root utilities, custom ROMs, and Xposed modules, then there's a good chance you've had to factory reset your phone when something went awry. Plus, when you're switching ROMs, it's always recommended that you wipe all data, so us modders spend a lot of time restoring and tweaking various settings.

As I said before in my earlier post on how to make a two-tone doorbell, sound is more than just music. Note blocks can create a wide variety of notes and sounds, and those can be used for more than just making a stirring rendition of "Still Alive" from Portal.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The big day has finally come—the new iPhone 7 and iPhone 7 Plus have been officially unveiled. Apple debuted their new flagship devices at a keynote event in San Francisco on September 7, and as we've grown to expect, there are tons of changes in store for the world's top-selling smartphone.

Video: . Optimize your Marketing with a Mobile Website

Apple continues to suffer production delays caused by COVID-19 era factory closures, and the products taking the biggest hit are its customized 14-inch and 16-inch MacBook Pro configurations. Long story short, you'd be lucky to get one of those 2021 MacBook Pro models by the end of June 2022.

It appears that the Project Aero 3D content development tool isn't the only augmented reality project that Adobe has in the works.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

With the 2018 FIFA World Cup underway in Russia, soccer (aka "football") fans worldwide can show support for their favorite teams and players in augmented reality via Snapchat and Facebook.

If you're looking to mix up your home décor with something a little bit outside the traditional cabinet box set, check out the amazing Wave cabinet from NYC-based, Chilean designer Sebastian Errazuriz. This revolutionary design will change the way you think about interior decoration and furniture functionality.

Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

Pie controls are navigation soft keys that can be displayed by swiping up or from the side of your screen, allowing you to navigate, search, call up the power menu, take screenshots, and a lot more. Not only are pie controls functional, they make using Immersive Mode a breeze since the regular nav bar was no longer required.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?