Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.
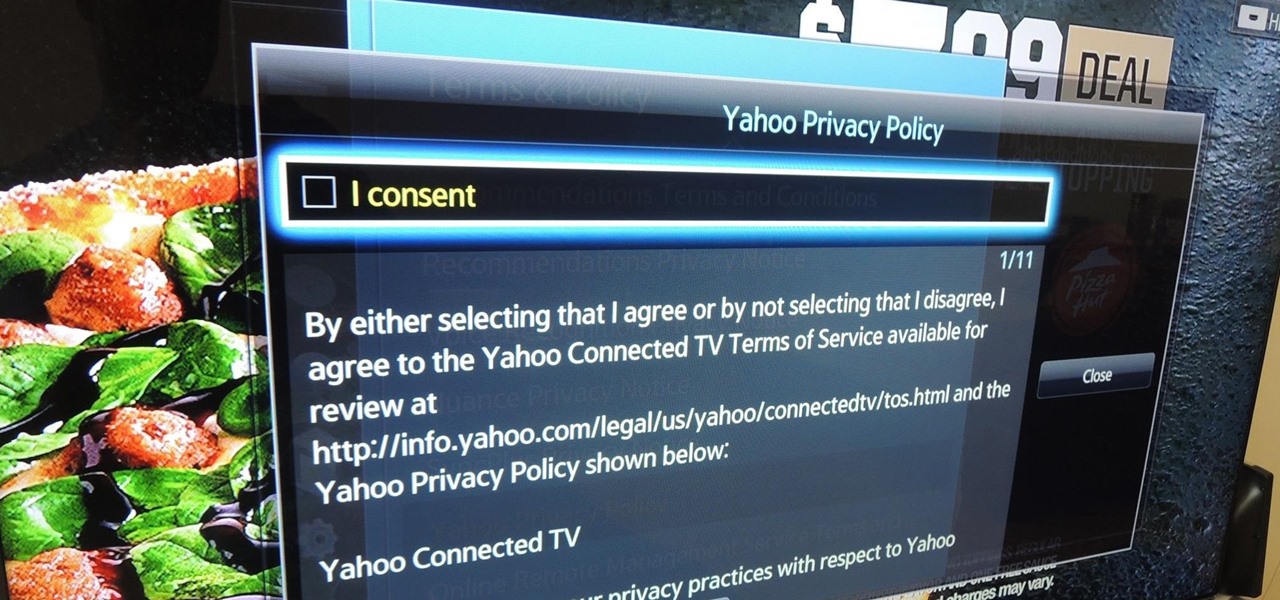
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.

In this economy any job is better than none at all, right? Of course, but if you know you are worth more than you're making, follow this tutorial for tips on how to ask your boss for a raise. You'll never know if you don't ask! Good luck!

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

Check out this video to see how to collect blood with the BD Vacutainer Eclipse Blood Collection Needle.

Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

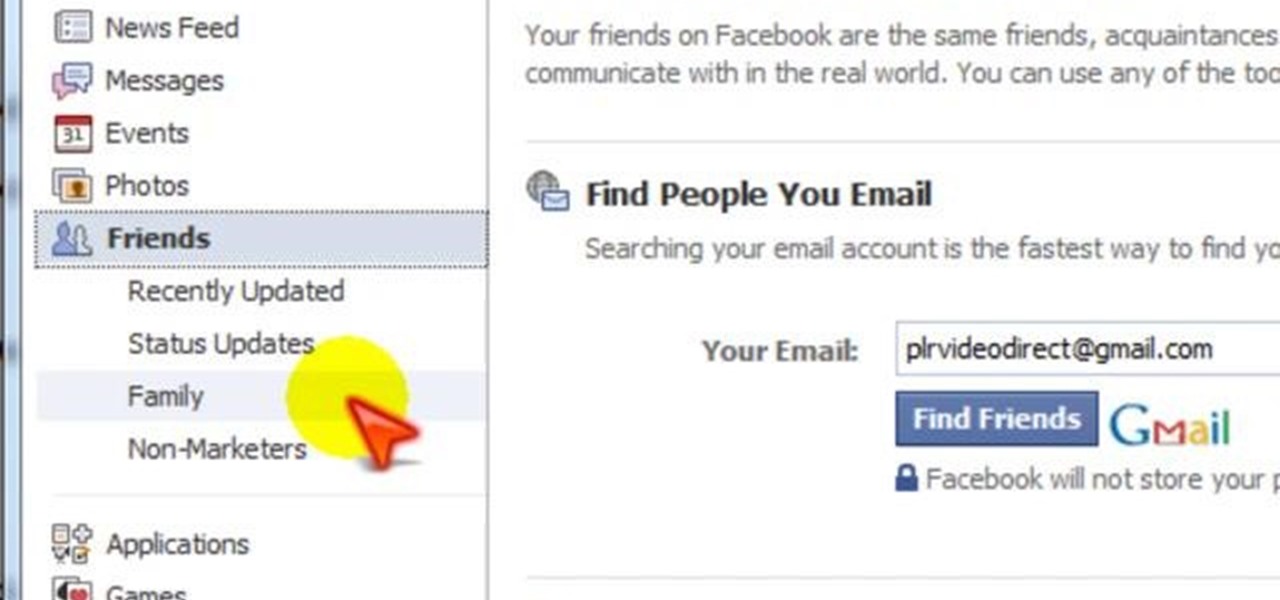
In this tutorial, learn all about Facebook's biggest issue these days: privacy. Check out this clip for a walk through of Facebook's privacy policy and learn how to create friend lists to keep your information safe and to yourself. Don't let your details get in the wrong hands, organize your account and be smart.

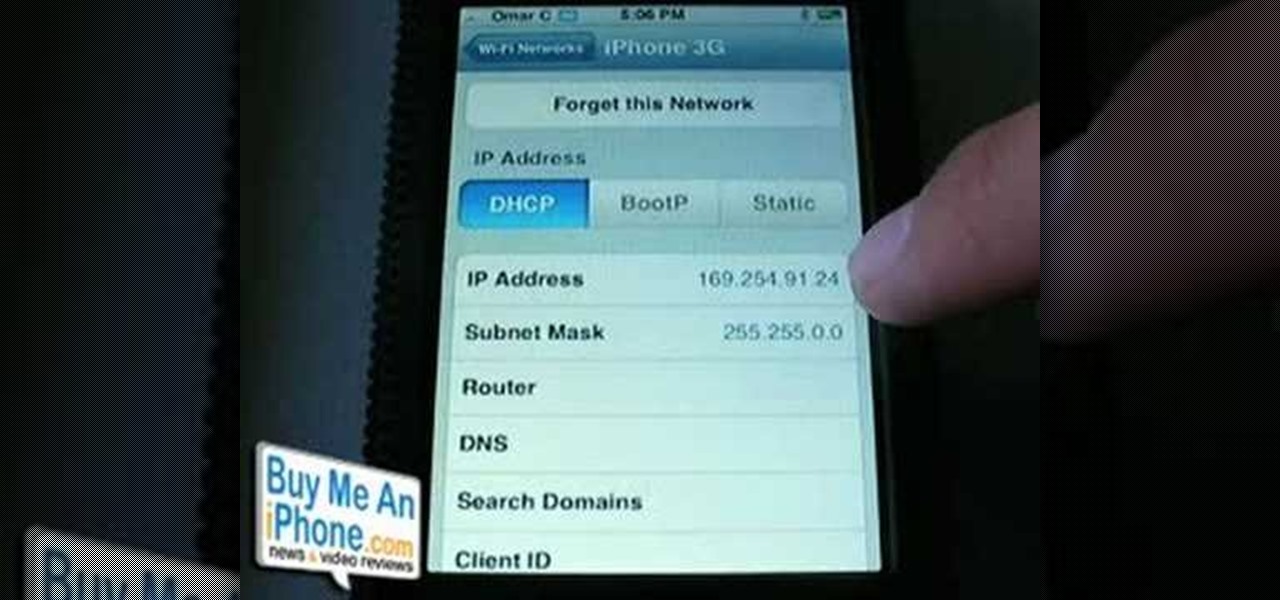
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

Take a folder and organize documents based on the actions required. Actions:

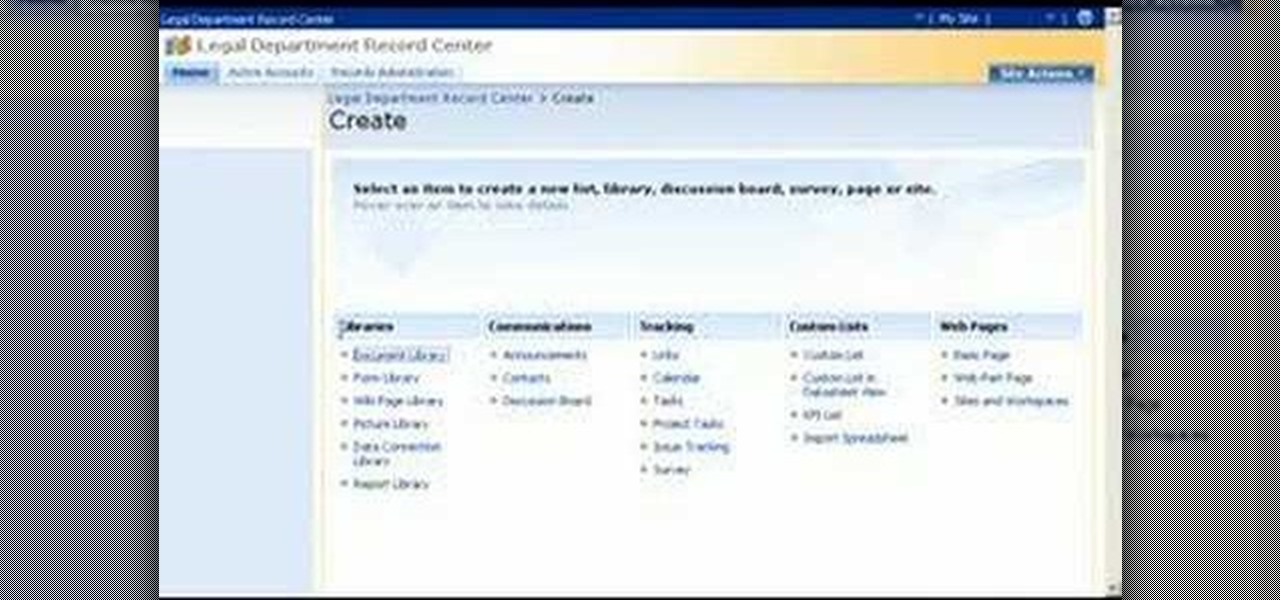
Check out this tutorial and see how to add a library to an existing Record Center site, apply policies to the library, and configure the Records Center site so that submitted documents are routed to the right library.

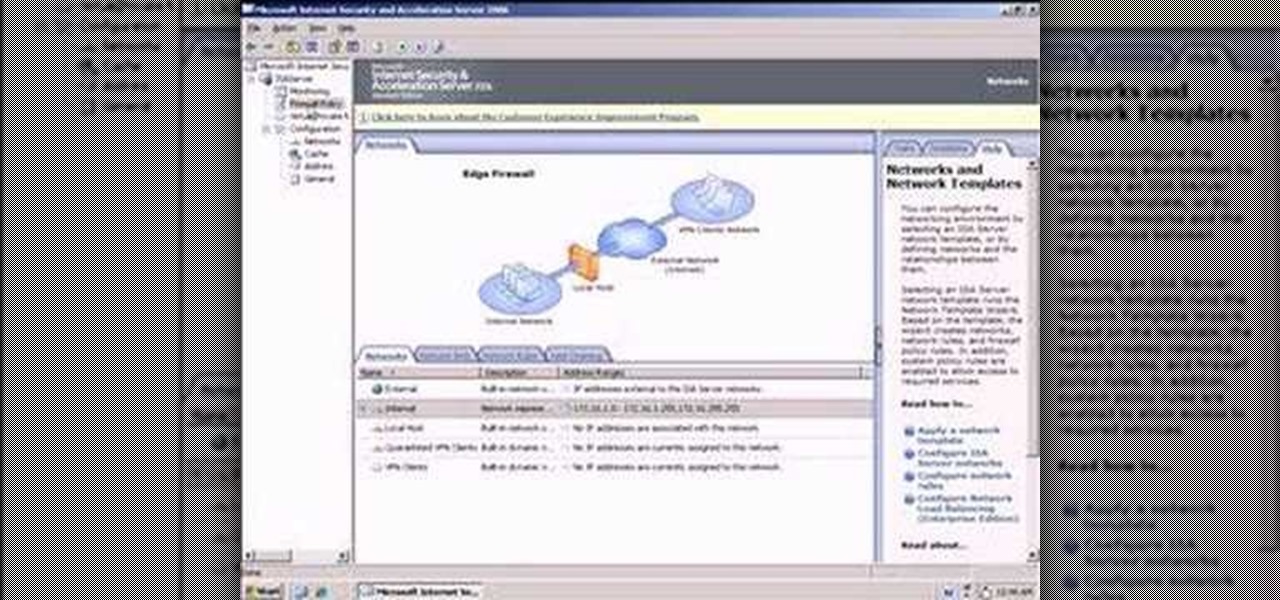
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Check out this video tutorial to see how to collect blood with the BD Vacutainer Safety-Lok Blood Collection Set.

For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

Thanks to augmented reality, fashion companies can let customers try on cosmetics, clothes, more cosmetics, and sunglasses from the comfort of their homes and through the non-judgmental eyes of their smartphone camera.

The east coast is becoming a hotbed for driverless. Sure, the west coast has all of its fancy tech companies testing self-driving cars, but we've got the goods too. Uber has brought the technology to Pennsylvania and will soon do the same in Toronto. (Stratford, Ontario, has plans to test out driverless too!) And today we got some great news: Governor Andrew Cuomo just approved of driverless testing in New York.

Lately, the biggest news in driverless has been the raging lawsuit between two autonomous spearheads, Uber and Google's Waymo. A new bill back by General Motors, however, could take them both out of the race towards driverless.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

In an SEC filing published on Monday, Snap, the company behind Snapchat, disclosed that Imran Khan, its chief strategy officer and a member of the NR30, is leaving the company to "pursue other opportunities."

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

If you are law enforcement or find yourself in an emergency situation you may need to know how to properly conduct surveillance in a rural area. You will have to gather information without being scene and will need different techniques when out in the wilderness.

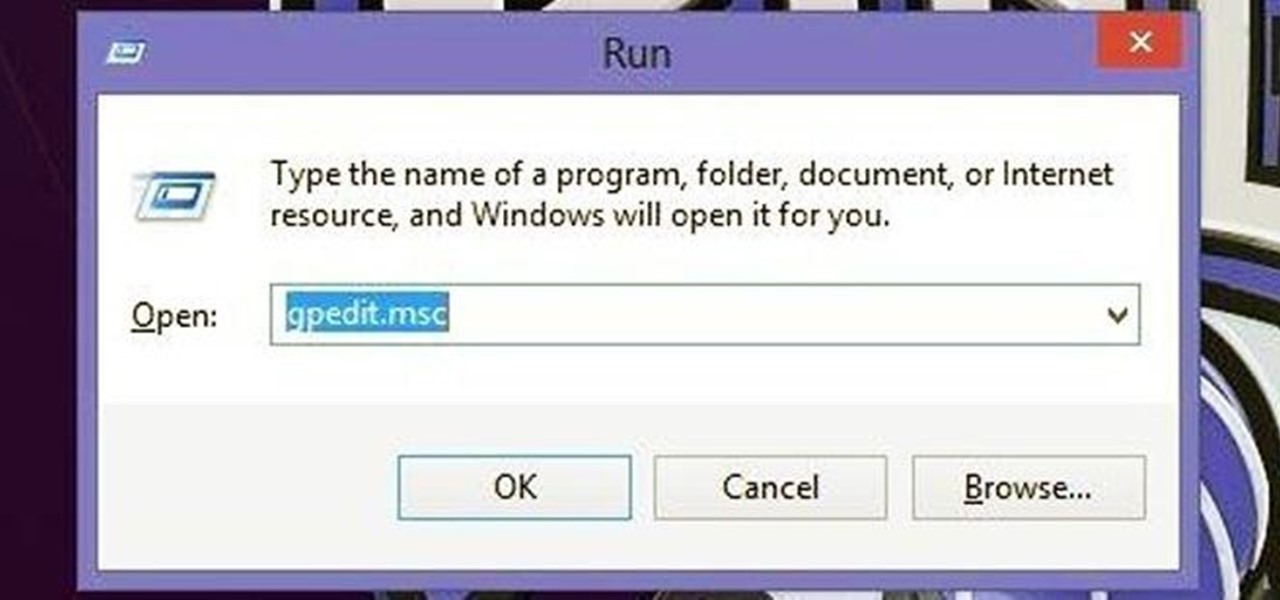
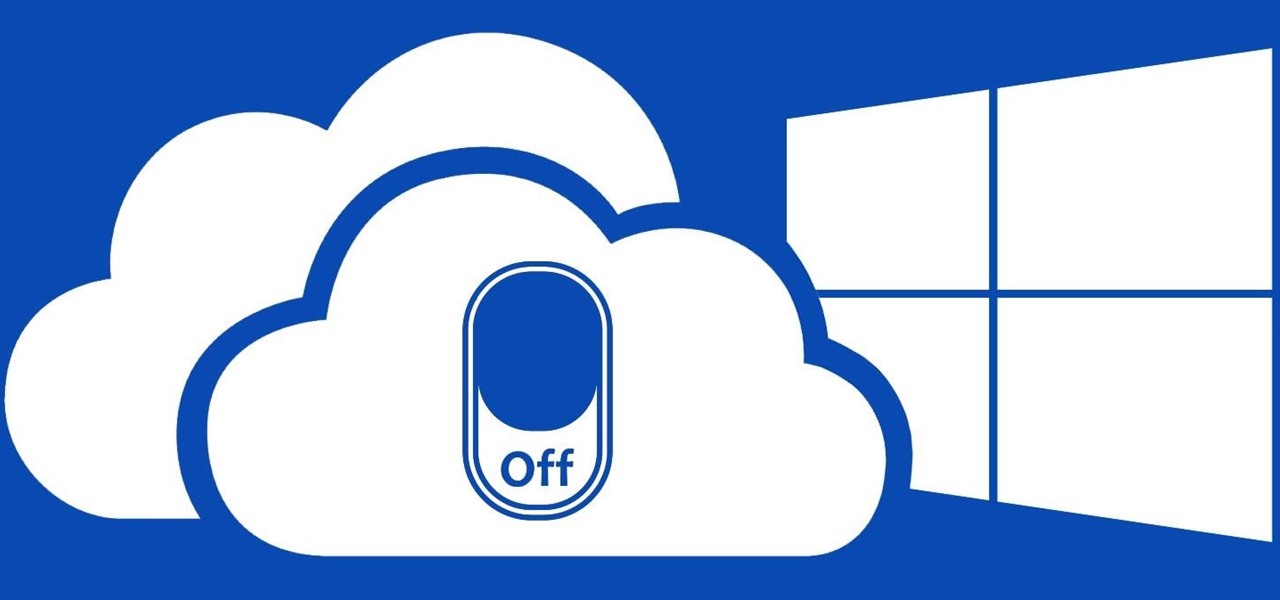
OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

There are a number of ways to give your productivity a kicktstart, from taking a break from your distracting smartphone to just taking a break, plain and simple. Yet finding the motivation to start working doesn't require any effort at all—just a little bit of green.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

In this video tutorial viewers learn how to wear the National Working Uniform. This uniform has a strict policy and all must follow the uniform rules. The basic components of the uniform are: an eight point cap, blue cotton undershirt, shirt, trousers, belt with closed-faced buckle, black boot socks, blousing straps, black 9" steel-toed leather boots, embroider rank insignia and service & name tapes. This video is very detailed and clearly explains all the uniform expectations. This video wil...

While many have their own strong opinions on Apple and their products, few have complaints about the way they embrace accessibility. Apple typically finds ways to make products functional to all customers, regardless of their situation. This philosophy can be seen in Apple's partnership with Cochlear, as the two develop a new cochlear implant sound processor for iPhone.

In this tutorial, we learn how to block a website using a Linksys Router. First, go to your web browser and type in "192.168.1.1" into the address bar. After this, you will need to enter in your username and password to the pop up window. From here, go to the tab that says "access restrictions" and look for where it says "policy name". Type in 'blocked website' to the bar and then click 'enable'. From here, go down to the bottom of the page and enter in the URL of the website you want to bloc...

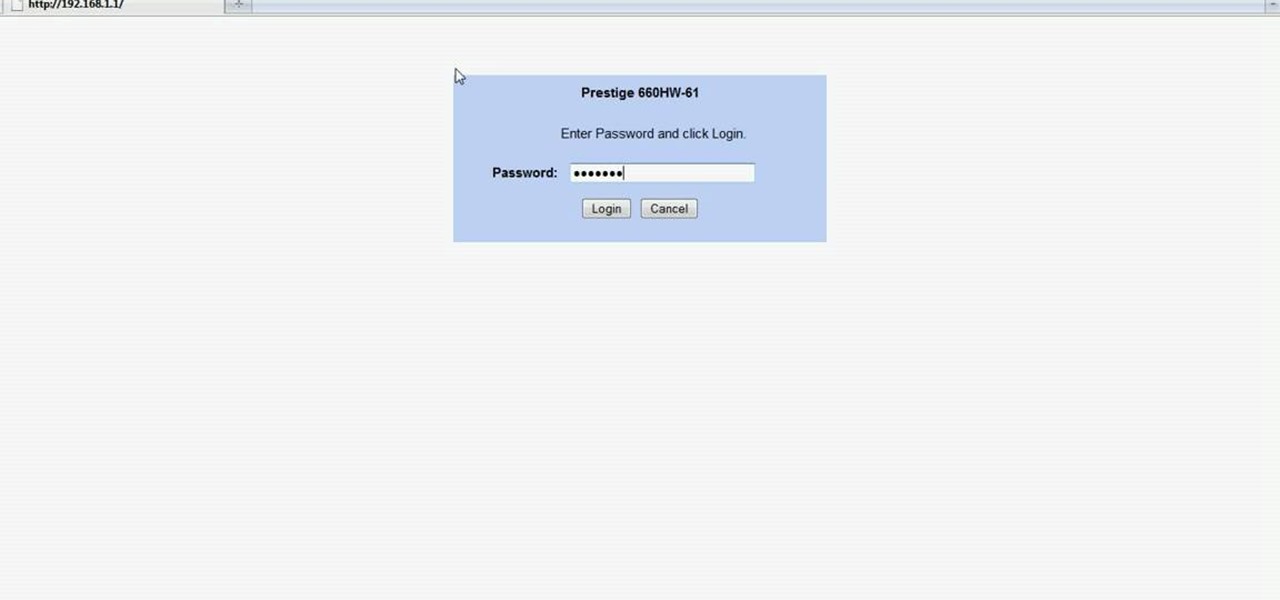
In this Computers & Programming video tutorial you will learn how to easily open your NAT on a ZyXel router. There are three steps involved in doing this. Open your web browser and type in the router IP address which is normally http://192.168.1.1. Then you will get the log in page. The password is either 1234 or admin. It will be written on the packaging of the router. On the next page click on UPNP, then check all three boxes and click 'apply'. Then you click on NAT and set the start and en...