While iPhone sales are expected to dip for the first year ever, Apple is reportedly planning to release a souped-up, 4-inch iPhone 5 in hopes of boosting sales for users who prefer a smaller handset.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.

Similar to the feature that lets you dim the light on your PS4's DualShock controller, your Playstation 4 is filled with useful tricks that you may not know about, especially when all you want to do is pick up and play. One of these useful tricks is the ability to turn your TV on using the PS4 controller.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.
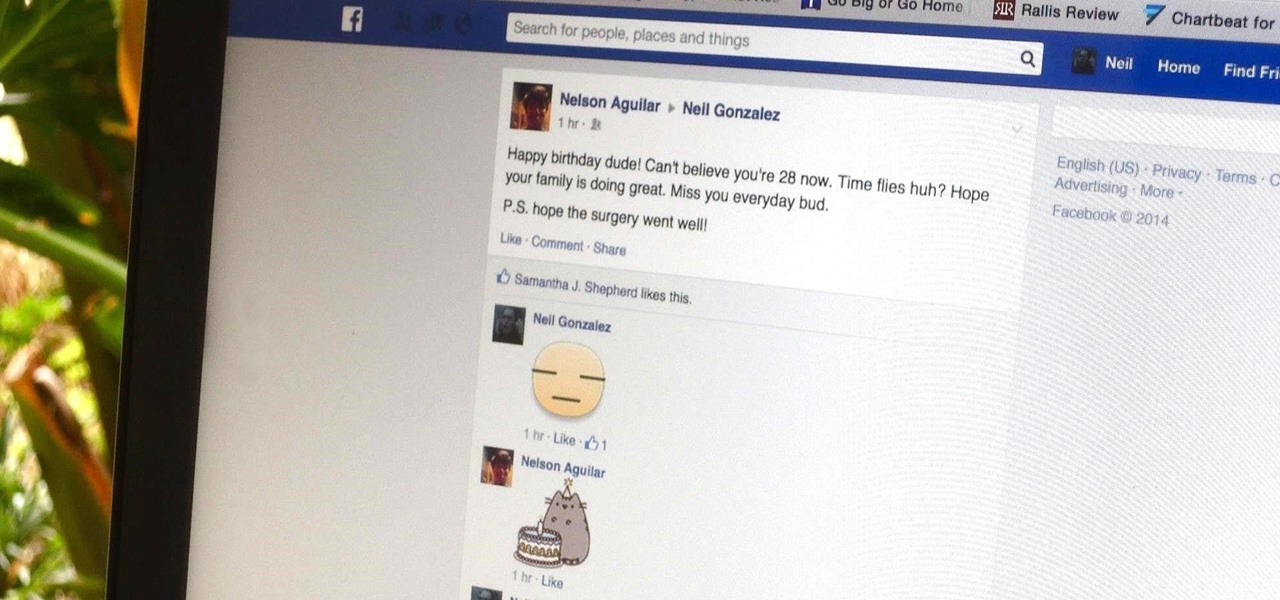
While stickers have long existed in the messages section of Facebook, they've only just recently rolled out sticker capability in comments for events, groups, and timeline posts. That means you can now reply with a cute sticker of a cat eating a slice of pizza on someone's status instead or writing something more thoughtful. While an animated sticker can show off enthusiasm and excitement that words or a too-simple emoji may not be able to convey, you can bet that your comment section will qu...
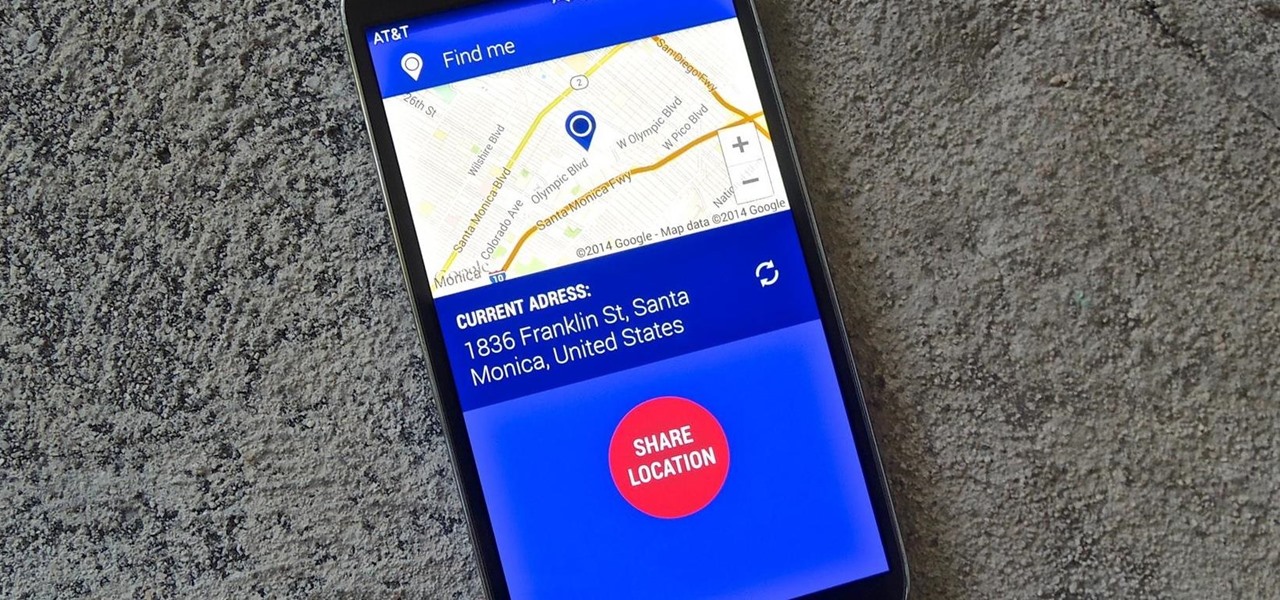
Whether it's a chaotic family day meetup at the beach, barhopping with buddies, or getting stranded in the middle of nowhere with a dead car battery, being able to share your exact location with others using your smartphone makes life easier and less stressful.

The new operating system for your Mac is here, and it looks fantastic—OS X Yosemite. At Apple's WWDC presentation, we were shown the new iOS-like aesthetics, as well as other awesome enhancements to the operating system. Improved Aesthetics

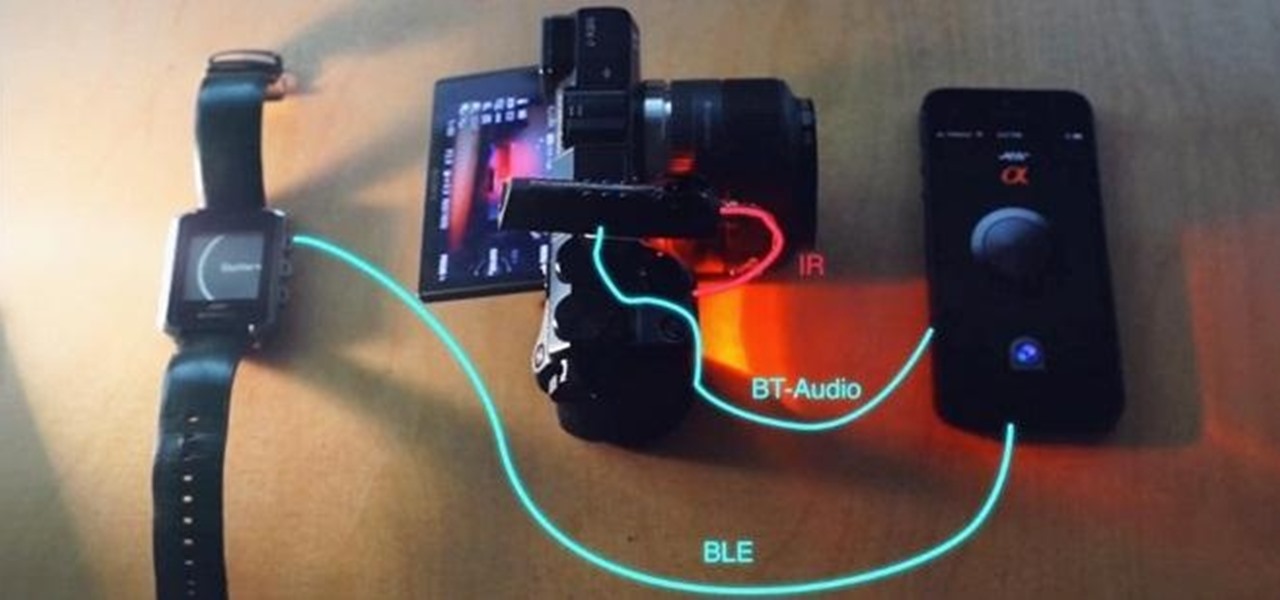
You can add Bluetooth capability to an old stereo, a retro mouse, or even your car's cassette deck. If you can think of a device, someone has probably found a way to control it with Bluetooth.

The car is arguably one of the worst places to receive a text message. You know you can't resist looking, and when you do, your attention is no longer on driving, it's on reading the latest gossip or whatever. You take your eyes of the road for just a few seconds and you could get an expensive ticket, or even worse—an accident. But you can't just ignore that notification sound or vibration, can you? So, if you just have to know what it says right then and there, why not at least do it in a sa...

Most of us have given up our big, bulky stereos in favor of smaller, sleeker models, but how many of us actually get rid of the old ones? If you don't like the idea of throwing out or giving away electronics you spent good money on, you can always upgrade them instead!

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Snapchat is probably used to Facebook copying its features by now, but Apple borrowing a page out of its playbook is likely a bit more surprising.

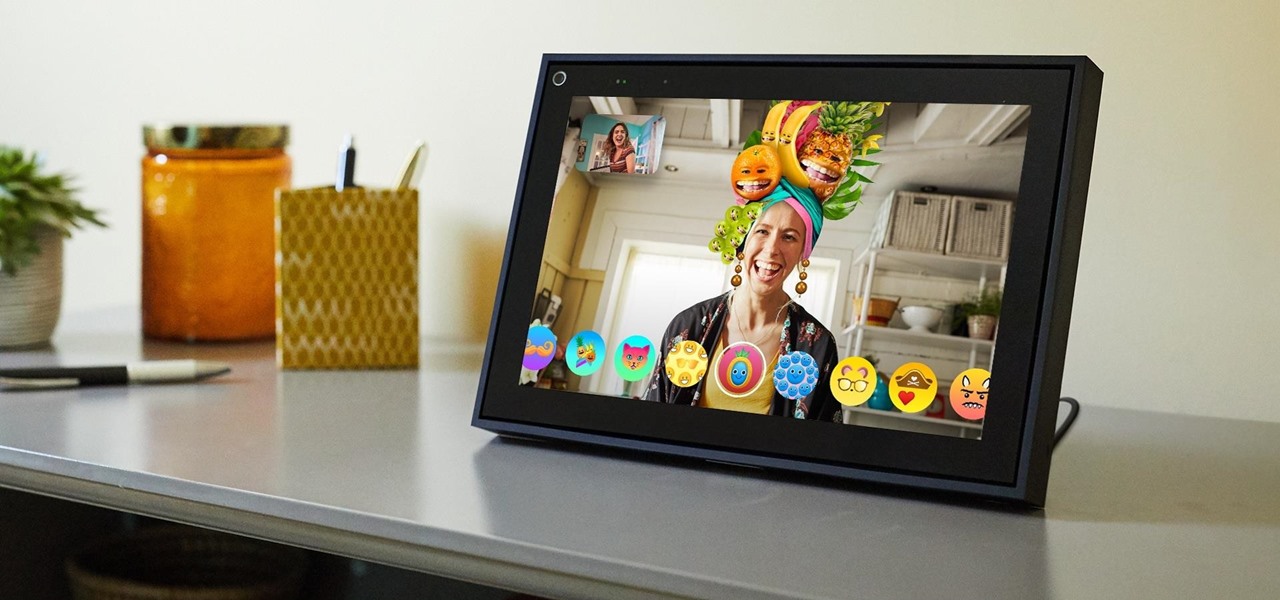
Friends and family receiving new Portal devices for Christmas will have some extra stocking stuffers in the form of new AR features.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

After one of Britain's "Brothers Bling" bought Blippar out of bankruptcy, the mobile augmented reality company is getting back to business with the addition of web-based AR capabilities to its platform.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

After raising more $100 million in funding from some of the tech world's biggest names, Mojo Vision is finally ready to show the world the building block of its "invisible computing" platform.

Alongside its official unveiling of the lower-cost Pixel 3a smartphone at Google I/O, Google took the opportunity to extend its early preview of AR walking navigation in Google Maps to all Pixel devices.

Spring is here across the US, but, through the lens of Snapchat and augmented reality, winter is coming to New York.

Visitors to the Unity booth at the Game Developers Conference in San Francisco will get a special augmented reality treat courtesy of Magic Leap and Weta Workshop.

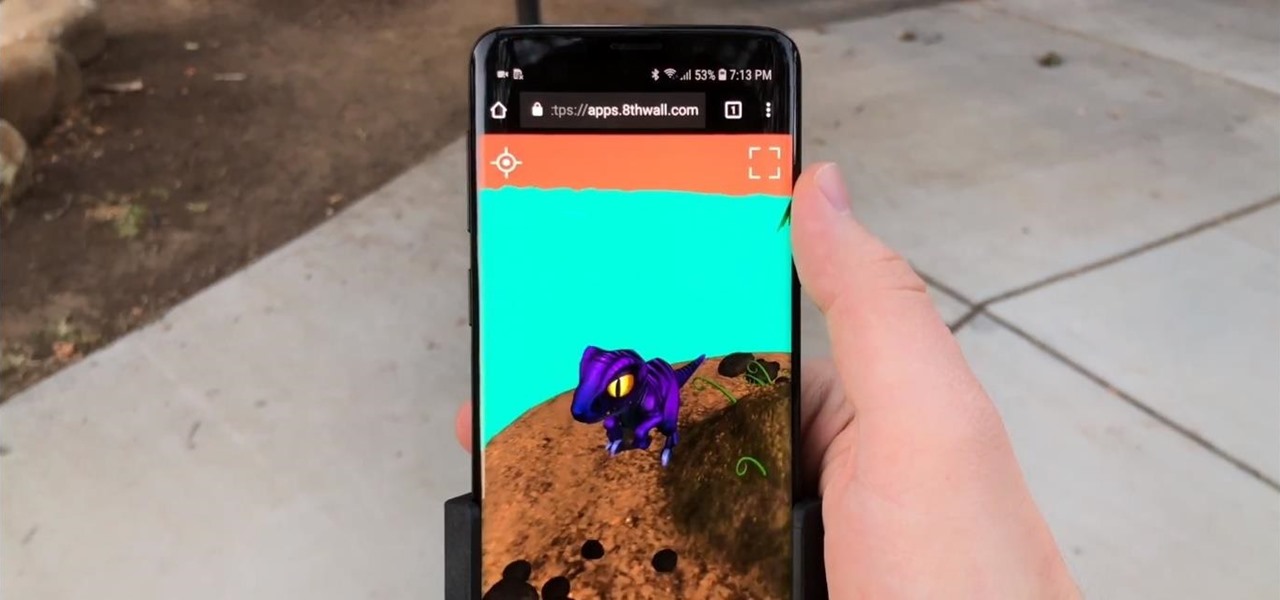
In the past few years, augmented reality software maker 8th Wall has worked to build its platform into a cross-platform augmented reality toolkit for mobile apps, as well as web-based AR experiences.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

On Thursday, Magic Leap decided to step up its efforts to foster its developer community by launching the Independent Creator Program.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

In the latest update to its augmented reality platform, Wikitude has introduced new plane detection capabilities that can anchor virtual content to surfaces at any orientation.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Less than 20 days after the launch of Magic Leap One, Mapbox has jumped at the chance to provide its map services to Magic Leap developers through its Maps SDK for Unity.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

On the one year anniversary of the introduction of ARKit, Apple is planning to reveal major updates its augmented reality toolkit for mobile apps at its Worldwide Developers Conference in San Jose, California next week.

If two hands are better than one, then two hand-tracking SDKs must be better than one as well. After uSens announced its Hand Tracking SDK at the Augmented World Expo in Santa Clara on Thursday, ManoMotion unveiled the latest version of its own SDK. Both technologies give apps the ability to track hand gestures with just a smartphone camera.

As Facebook, Apple, Samsung, and others offer augmented reality selfie effects and content that challenge its platform, Snapchat has continued to innovate with its augmented reality capabilities.

On Tuesday, at Google's I/O developer conference, the company announced a huge update to its ARCore augmented reality toolkit that matches the latest features of ARKit, and surpasses Apple's AR platform via support for shared experiences.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

A report from app data firm Sensor Tower reveals that more than 13 million ARKit apps have been installed on iPhones and iPads within the first six months since the toolkit launched with iOS 11.

Google's AI investment arm, Gradient Ventures, has joined a $10.5 million round of funding for Ubiquity6 and its platform for shared augmented reality experiences, just weeks after Google's GV fund backed a competing AR cloud platform.

A recent update to Facebook's News Feed could significantly broaden its reach when it comes to delivering augmented reality content.

If you're an Android user, you're very likely jealous of your iPhone friends who have access to the wide, wonderful world of augmented reality thanks to ARKit.

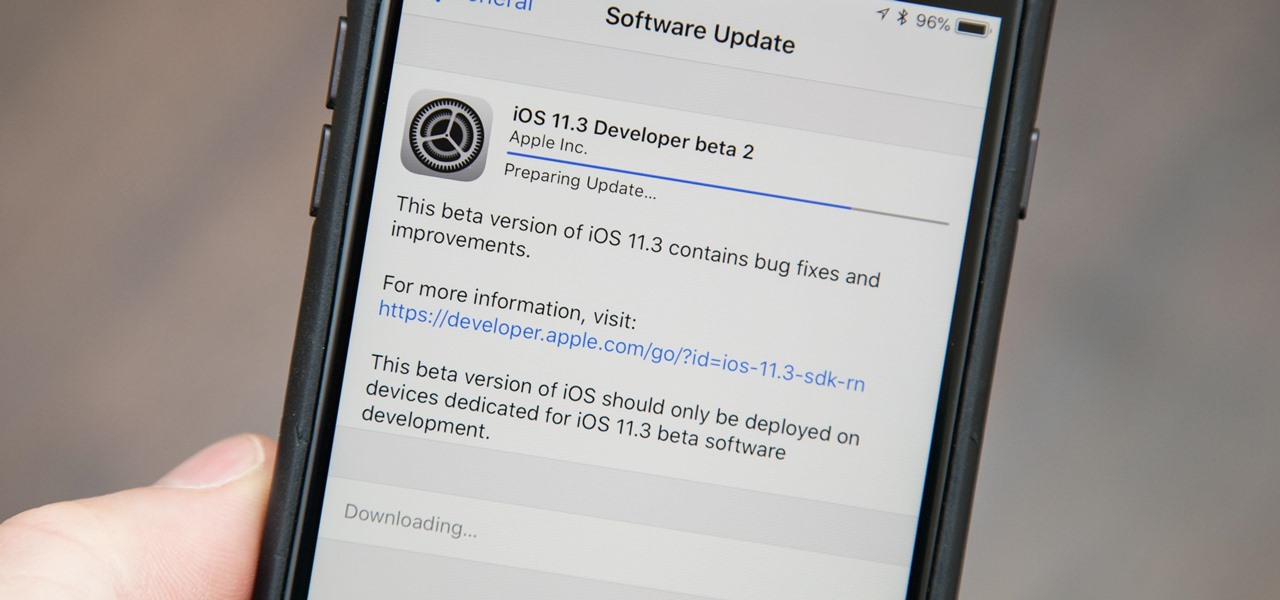
Apple released the second beta for iOS 11.3 on Tuesday, Feb. 6. The update comes two weeks after the original announcement and release of the iOS 11.3 beta, which brought new Animoji, Messages on iCloud, and Apple Music Videos, among other features. One glaring omission was the promised battery health tool, but iOS 11.3 beta 2 just introduced it.

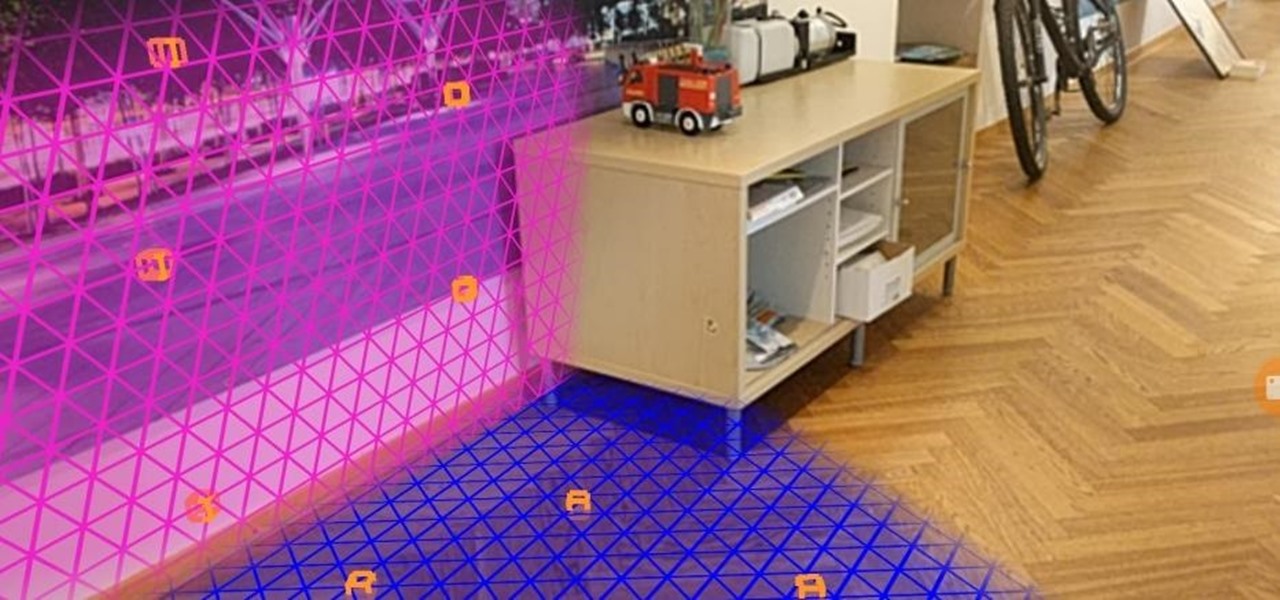
When Apple unboxes the next major update to its mobile operating system this spring, iPhones and iPads will gain some significant new features for augmented reality experiences: verticality.