Focus groups strike fear into the hearts of even the most season marketer, and with good reason. In a world where everything is subject to change based on public opinion, from movie endings, to popcorn flavors, to logo colors, focus groups can make or break a new idea, but it doesn't have to be that way. A focus group is just a way to gather opinions in a vigorous way and can be very useful. Watch this video tutorial to use a focus group to develop and test a new brand name or corporate ident...

Voters look to candidates for long-term plan to fix economy - CNN.com.

According to Electrek, Tesla CEO Elon Musk, in a covert conference call with a select few investors, commented in detail about his plan to have Tesla's Model 3 driving on the road earlier than we all expected.

Apple has finally seeded the release candidate for iOS 14.4 to iPhone developers and public beta users, build 18D52. The update adds scanning support for smaller QR codes in Camera, the ability to classify Bluetooth devices to improve audio notifications, and alerts on the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max for if the camera is detected not to be genuine. There's also a short list of bug fixes.

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

I'm not much for politics, but I do like to keep tabs on our elected government officials from time to time, since I am a registered voter and believe that every one should vote (unless they're just voting to say they voted). This pretty much means I pay attention to my local and state officials, the presidential candidates, and of course, any political scandal that makes me chuckle.

At a loss as to whom you should vote for in the next election? In this clip from TekZilla, we learn about VoteEasy, a web app built to help United States citizens determine which candidates' views align most closely with their own. For details, and to get started learning which candidates are most like you, watch this video guide.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

Answer “Why should we hire you?” in a job interview John Heaney from The Job Shopper discusses how to handle one of the toughest questions you will face in a job interview: “Why should we hire you?”

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

For many of us, being the interviewer is as nerve-racking as being the interviewee. You can keep your cool and quickly weed out unqualified applicants.

The last presidential debate of 2012 is over between President Barack Obama and Republican nominee Governor Mitt Romney. Now it's up to you to choose your candidate by election day on November 6th, 2012, and more importantly—VOTE!

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

The Unicode Consortium just unveiled 72 new emojis that will be included in the upcoming Unicode 9.0 release, but we're not here to talk about the winners. Instead, let's take a look at the five poor emojis that will have to wait until at least next year to join the Unicode roster.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Video: . Marley Hair is Super Cute Curled so I decided to Curl it.

Video: . This Video will Show you how to Stretch your Natural hair with no Heat. I love doing this Method it is just as good as blowing your hair out. It gives your hair length without putting heat to it.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

Sure, Tony Stark was able to build the original Iron Man suit in a cave with a box of scraps, but can the average do-it-yourselfer replicate the EDITH smartglasses from Spider-Man: Far From Home in a similar fashion?

NASA is going going to Saturn's moon Titan, and the space organization is using augmented reality help them do it.

At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

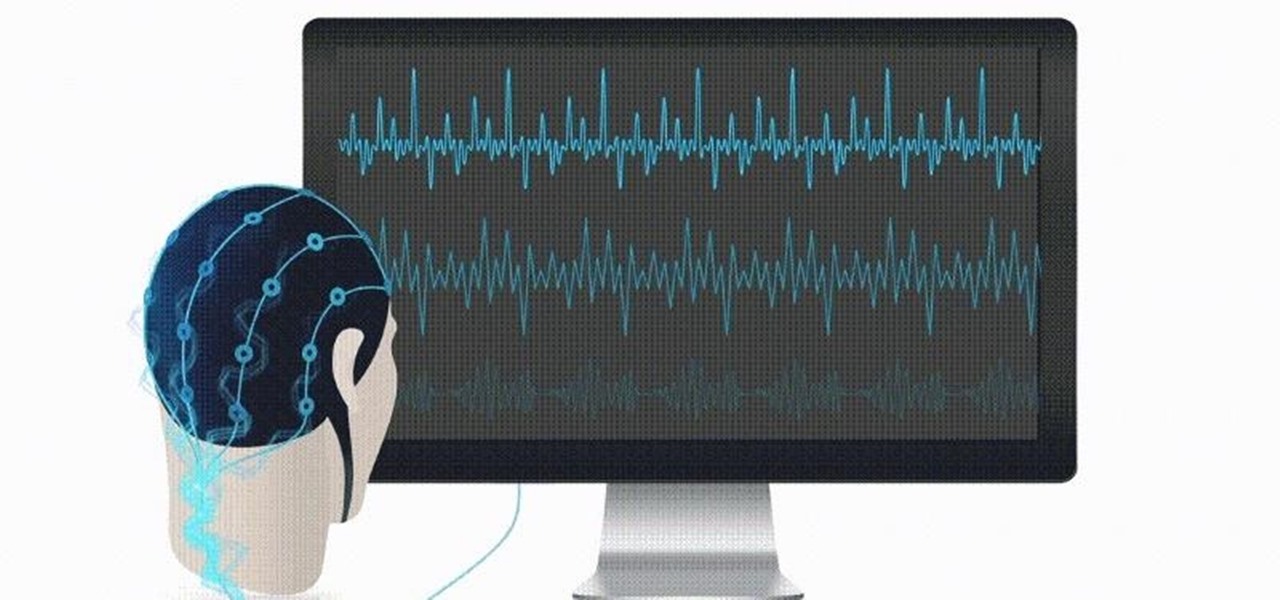
As promised earlier this year, Neurable has introduced limited beta of a Unity-compatible software developer's kit (SDK) for its brain control interface (BCI) for augmented and virtual reality.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

Plastic red cups are synonymous with college parties, beer pong, and generally a good time. The reason these cups are so rampant in the party scene is because they're cheap, easily disposable, and, well... who wants to drink out of a blue cup?!? Oh, to be young and in debt.

So many times, you turn on your computer, you open your front door, or you sit down on the couch to watch some well-earned TV, when you think -- Gosh! If only I could do this or this, life could be so much easier! And then, if you were a boring person, you would slouch even further down on the couch and continue to watch those reruns of The Sopranos.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Between acquisitions, hirings, patent applications, and insider reports, all signs point to Apple building a smartglasses product that could ship as soon as 2020, but the company has not officially confirmed such plans.

To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

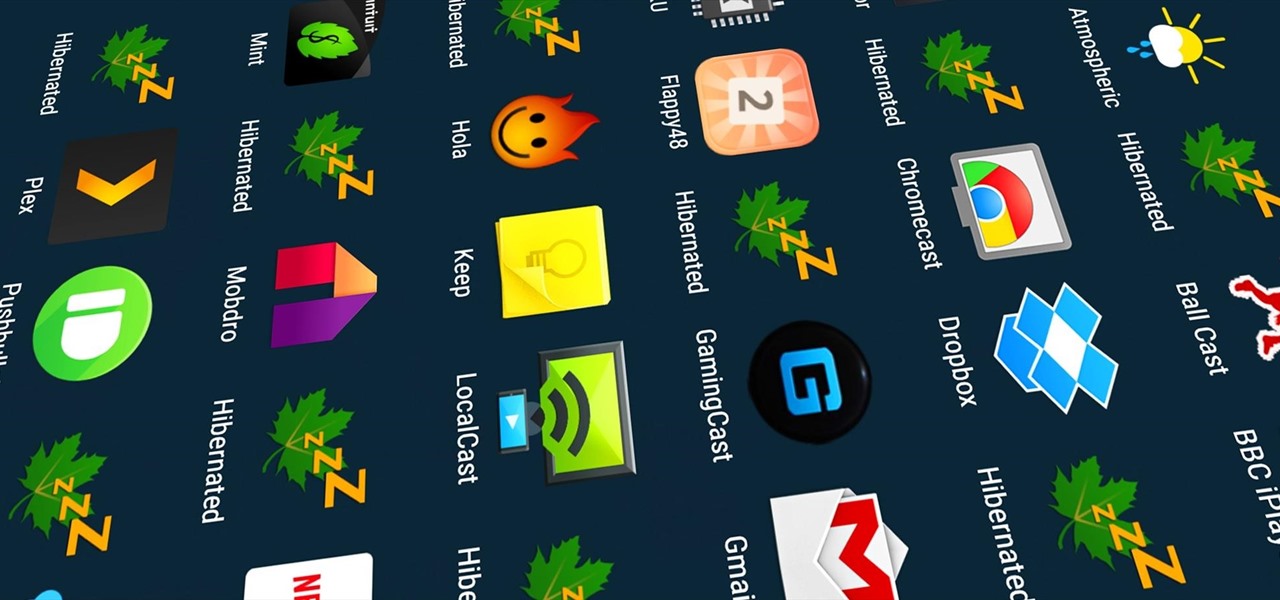
Greenify is a terrific app that allows you to put battery-hogging apps into "hibernation." Effectively closing the problematic apps and preventing them from running until you explicitly launch one of them, hibernation is a great way to save battery life while you're not using your phone.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Believe it or not, the 2012 Presidential Election is (finally) almost over. While most of us are breathing a collective sigh of relief (no more political ads!), it still seems like it hasn't been that long since the last election results were announced. This time, though, one of the biggest differences is how people will watch. Since traditional cable is on its way out, and mobile devices are getting more popular every day, a lot of people will be watching this year's election results online ...

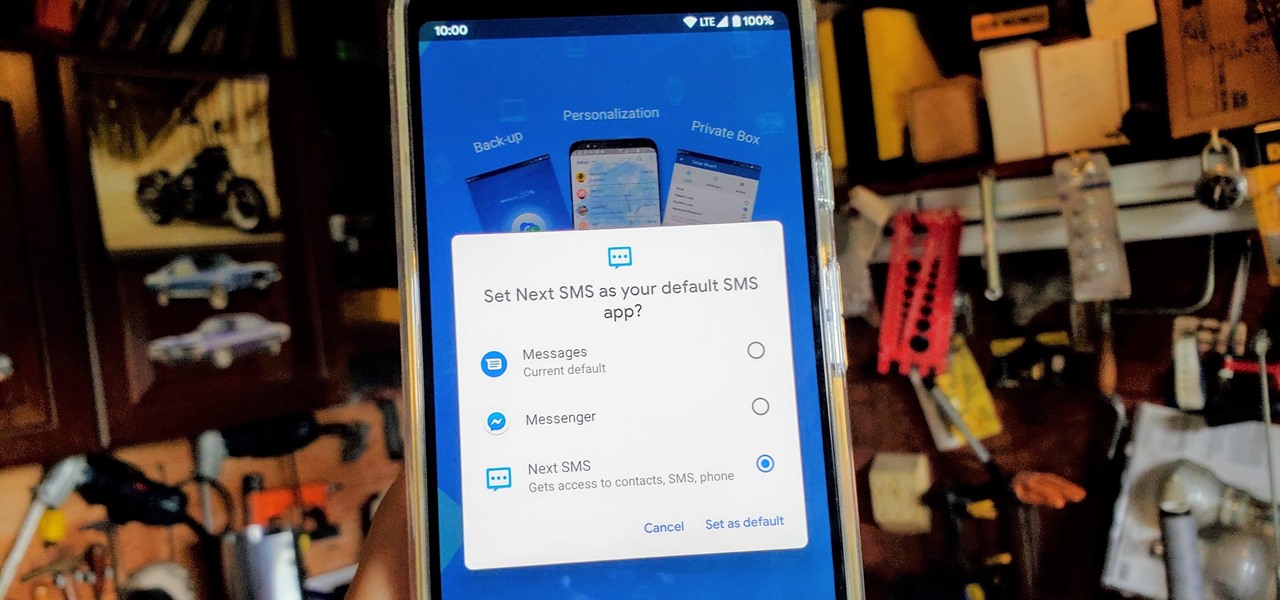
One of the best things about Android is being able to control everything you want, from your wallpaper down to the default apps you use for every action. Changing the default SMS app from the one that came with your device can drastically alter your messaging experience. Many SMS apps have loads of themes to pick from while also offering other features you can't find anywhere else.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.