Understand how binary numbers work, including how to read binary numbers, and create your own. This mathematics or computer programming tutorial is a zip to get through. It covers practical and theoretical use and need for binary code understanding. Binary means zeroes and ones in a series. This is paramount to digital transmission versus analog that transmits in a sinusodial wave form.

Understanding the Binary Numbering System and how to decode binary numbers.

Watch this instructional magic card trick tutorial to learn how to perform the binary routine. This is an original series of user-created moves. There are 9 phases of the Binary Routine, 6 of which are false, and the other 3 are closers that involve a color card change at the end. This video provides instruction on 2 false cuts and 1 closer, along with some possible variations. Just keep in mind, there is room for adjustment with these phases. If you find a better way to do a certain move, th...
"There are 10 types of people in the world," the old joke goes, "those who understand binary, and those who don't." In this tutorial, you'll learn how to read and write binary code. With this neat tutorial, you'll join the former group. Make sense of the 1s and 0s of binary code, the symbolic atoms of machine language, with this how-to.

Check out how to read a binary clock in this how to video. You'll see how to read the BCD (binary-coded decimal) format like so many can't. Just watch this if you have trouble determining the hours, minutes, or seconds on your binary clock. You can read it in standard or military time if you'd like.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

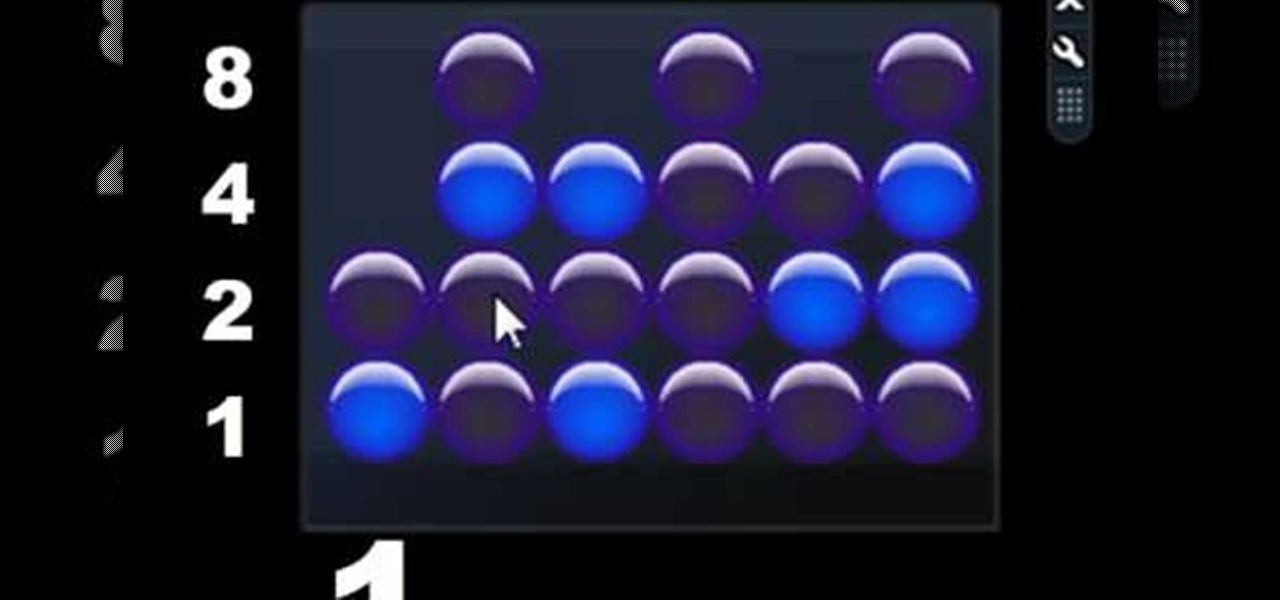
Sydus 93 teaches You Tubers how to read a binary clock by demonstrating the following process: A binary clock is made up of four rows and six columns of colored or uncolored dots. The rows, from bottom to top, represent the numbers one, two, four and eight. From left to right, columns one and two represent hours, three and four minutes and five and six are seconds. In order to tell time using the binary clock, begin at the left of your chart and simply determine which dots are filled in and a...

Buried deep in the code of many Google apps is a set of debugging options. These options, which are designed for developers to help test the way their apps interact with Google's own, are normally hidden from view.

Check out this video on how to read a binary clock, courtesy of glassgiant. The current binary clock comes in both java and flash. So, check out this tutorial on how to actually tell time with a binary clock, because we all know it is quite confusing. Some people even have trouble with analog clocks, yikes!

This video tutorial demonstrates how to install OpenSceneGraph, the high-performance graphics toolkit, in Mac OS X from the binary package. While this how-to is particularly geared towards non-expert users of Mac OS X, it is certain to benefit anyone interested in stalling the OpenSceneGraph toolkit.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Ever wonder how to read a binary clock? First, you must learn that in binary code there are only two numbers, one and zero. A binary clock has six columns and tells time in military time. The first two are for the hour. No light means zero. A light that is turned on is one. The first column has two dots the second column has four. if the second dot from the bottom in both columns is lit, it is 22:00 or ten o'clock. In the third column the light closest to the bottom is lit which means one. In...

This lynda.com video tutorial shows how to use container fields with FileMaker Pro 10. When you want to create fields in FileMaker database you have the choice on what kind of fields you want to make. Many general fields are self explanatory like text, date etc., but there is a special kind of field called the container field. FileMaker Pro container field is a versatile data type in that it can store any kind of binary data. Container fields can be used to hold binary data in four broad clas...

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Geohot's Towelroot exploit made rooting the Galaxy S5 so easy that it was almost unreasonable not to try it out—even for the first-timers out there. This, of course, meant that folks who didn't truly need root for their usage went ahead and got Superuser privileges anyway.

A video from PC Mech that shows you how to install application in Sabayon Linux, a Linux flavor that is based on Gentoo Linux and is known for its ease of use.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Final Effects Complete 5 AVX brings Ball Action, Mr. Mercury, and 100+ other legendary visual effects to Avid editing and finishing systems as an AVX 2.0 plug-in set. Supporting both Windows and Macintosh (Universal Binary), the new FEC 5 AVX takes full advantage of AVX 2.0's power and performance. New features include support for 16 bit-color processing, AVX 2.0 real-time filters, native on-screen controls, multi-processor acceleration, a number of new wipe transition filters, and hundreds o...

Wondering how to create an app bundle in Mac OS X? In this two-part video tutorial series, you'll learn how to create an application that is completely self-contained and is drag-and-droppable/relocatable. Frameworks, PlugIns, and Resources are embedded in the .app bundle, thus avoiding the need for installers and avoiding issues like dll-hell. There is also a quick demonstration on how to enable Universal Binary building at 15:46. Take a look!

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

In this video, we learn how to dress chic like a geek! Dressing like a geek is becoming one of the hottest ways to dress! Some of the modern geek fashions are shirts with binary on them, old school video game shirts, geek shirts and many others. You can visit websites including ThinkGeek, which has a section dedicated to geek clothing. They also have shirts that relate to computer geek information and talk. Zeestuff is an apparel site that has game wear apparel for gaming geeks. There are als...

In this Labrats video tutorial the instructors Andy Walker and Seab Carruthers show how to undelete the deleted files and recover them. When you save data to your computer, the computer stores the data in the binary format on the hard disk. To keep track of the files, the Operating System maintains a file table that shows the location of the data on the hard disk for a specific file. There are many file formats like FAT, NTFS etc. So when you are erasing the file only the entry in the file ta...

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

If you've running iOS 11.1 through iOS 11.1.2, whether you have an iPhone X or an iPhone 5S, you'll notice that Apple's Calculator app can't keep up with your calculations. That's a because a bug has seriously slowed it down so that operation buttons won't always trigger when you press them. Luckily, there's something you can do about it.

Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions.

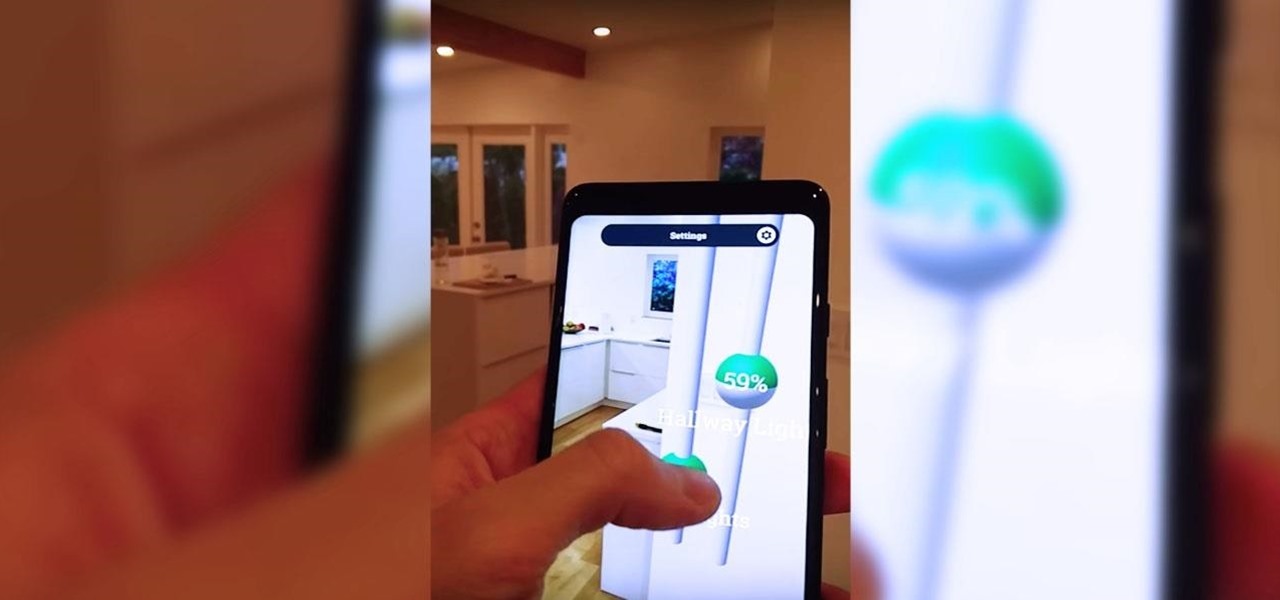
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.