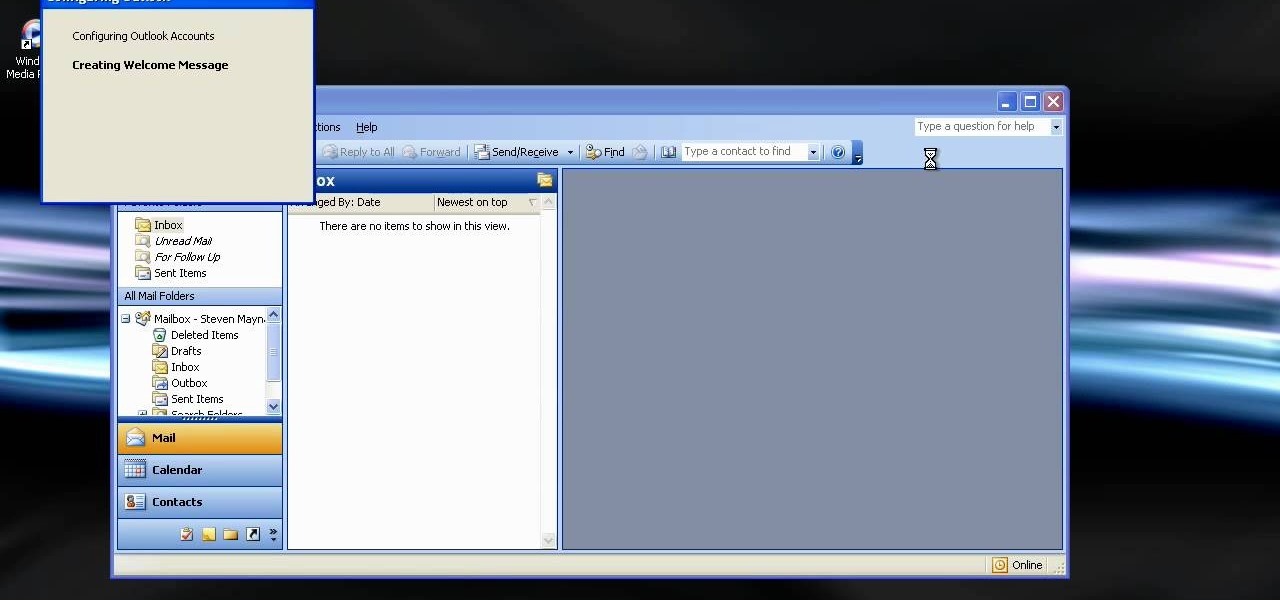
This how to video shows you how to configure Microsoft Outlook 2003 to access an exchange server. This is useful if you want to use the program with an exchange server and do not know how. First, open up Microsoft Outlook 2003 on your computer. On startup, click next and yes. Select Microsoft Exchange server and click next. Uncheck use cached exchange mode and enter the server name. Enter your user name in the correct form and click check name. It will not be filled in. Click next and then se...

In this episode you will learn how to exchange opinions in English: how to ask for it and express your own views. This video is great for advanced, intermediate, and beginner learning to speak the English as a second language (ESL).
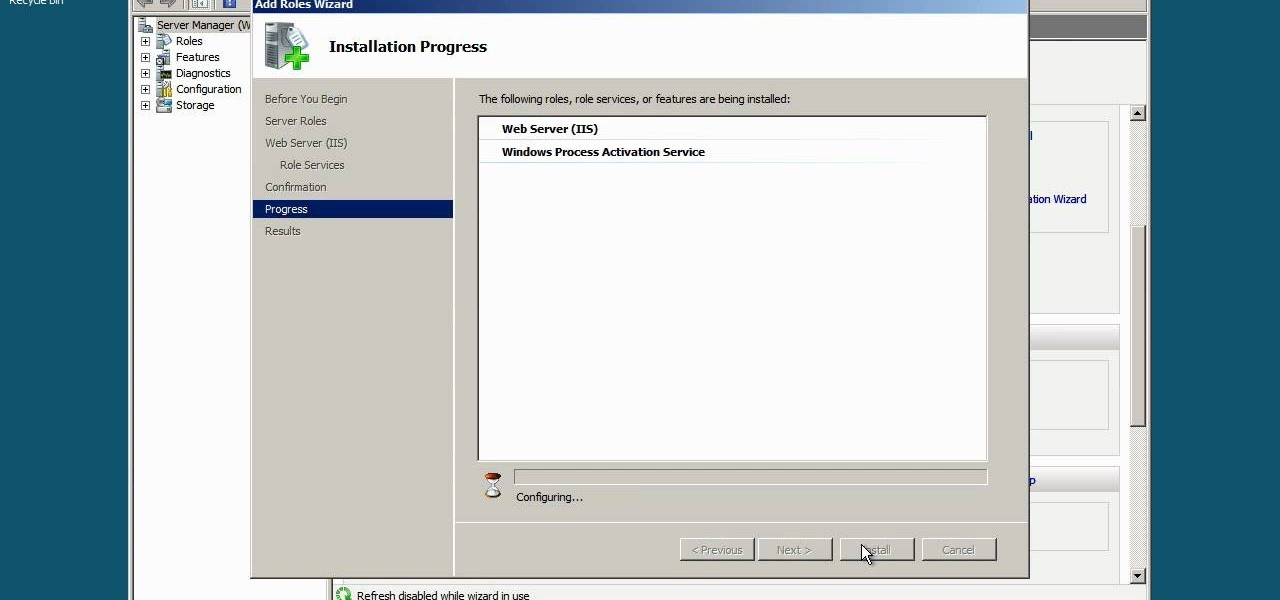
Need to know how to get a Windows Server 2008 server ready for the Microsoft Exchange Server 2007 service pack? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over five minutes. For more information, including complete, step-by-step instructions, take a look.
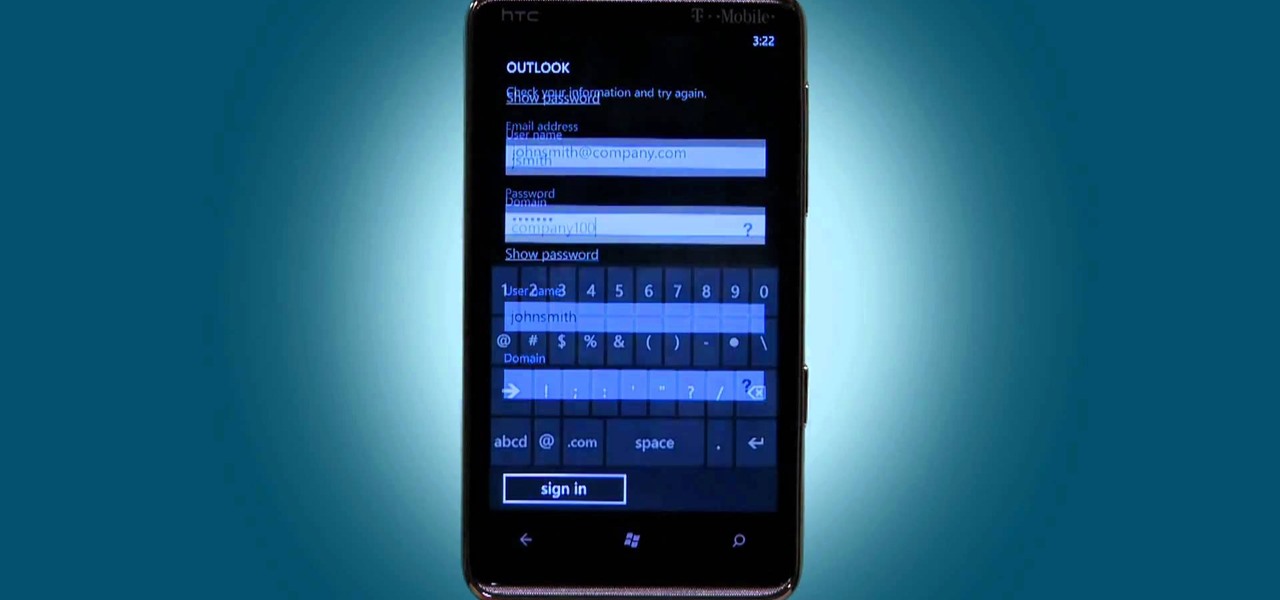
Set up a Microsoft Exchange email address on the HTC HD7! This clip will teach you how. Whether you're the proud owner of an HTC HD7 Windows Phone 7 smartphone or are merely toying with the idea of picking one up in the near future, you're sure to be well served by this official video guide from the folks at T-Mobile.

Use your Exchange email account on your [/topic/myTouch-4G] myTouch 4G! In this clip, you'll learn everything you need to know to configure a Microsoft Exchange email account. Whether you're the proud owner of a T-Mobile myTouch 4G Google Android smartphone or are merely toying with the idea of picking one up sometime in the near future, you're sure to be well served by this brief, official video tutorial from the folks at T-Mobile. For complete instructions, watch the video!

In this free video economics lesson from Salman Khan, you'll learn about international exchange rates and why they vary. For all of the relevant details, and to learn more about the causes and effects of currency value fluctuation, watch this clip.

In this tutorial, we learn how to receive Exchange emails on an Apple computer running the Mac OS X operating system. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

This instructional video demonstrates the following flair bartending trick: the tin roll exchange.

This instructional video demonstrates the following flair bartending trick: the bottle tin exchange.

Learn how to flair bartend. This flair bartending video demonstrates the two bottle exchange with a forearm bump and tin snatch. Practice and you will soon master this flair bartending move.

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Watch this tutorial video to learn how to get your work e-mail on your iPhone using the latest firmware upgrade. New iPhone users will find this how-to video particularly helpful because it shows an easy way to set up Exchange email on Apple's iPhone.

Watch BBC's Ray Mears to learn how to participate in some traditional product exchanges that have been passed down through Nomadic generations in Mongolia.

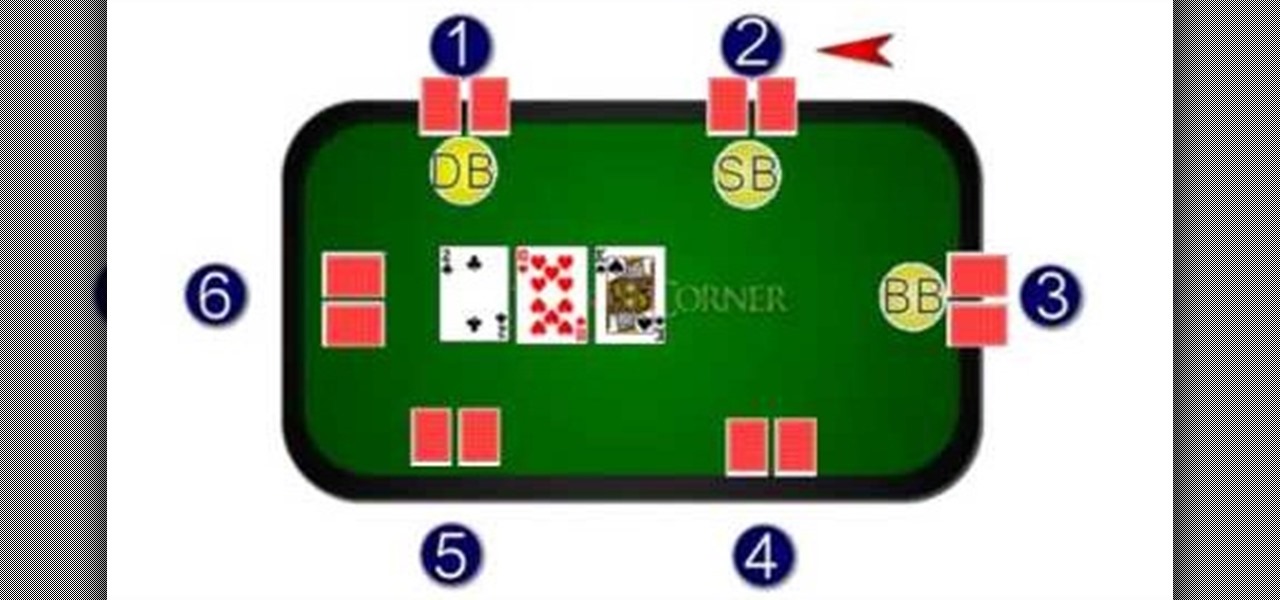
This video is sponsored by My Poker Corner and introduces the novice into how the game "Texas Hold 'em" is played. The complete process of the game from the number of players and their positions such as the Dealer are explained. The Small Blind position and the Big Blind position in the game are forced to place blind bets before they view their cards. Different betting rounds of the game such as "The Flop," "The Turn" and "The River" are explained and how the betting works and the option the ...

In order to stump drunk people with a cork trick, you will need the following: 2 corks per person. Tuck the cork between the thumbs and forefingers. The rules are that you have to switch out the corks without using any other fingers, besides the thumbs and forefingers, and the exchange must be simultaneous.

This square dance video teaches the following plus level square dance calls: Chase Right, Spin Chain & Exchange the Gears, 3/4 Tag the Line.

One of the best ways to learn the Hebrew alphabet is to use the alphabet song. But this twist on the song incorporates "Twinkle, Twinkle Little Star" in order to better remember the alphabet. "Twinkle, Twinkle Little Star" is the song that most English speakers learn their alphabet to, so why wouldn't it work with the Hebrew "Aleph-Bet"? The Aleph Bet has 22 letters which are all consonants. Get more details here. There are actually three videos here, the first is slow. The second if medium s...

This video will show you how to perform a great bar trick/puzzle/proposition bet called the "Three Knife Scaffold". This trick is super easy, it just takes a bit of know-how. In this tutorial, learn how to place your knives in order to fool your friends and win any bets they might make.

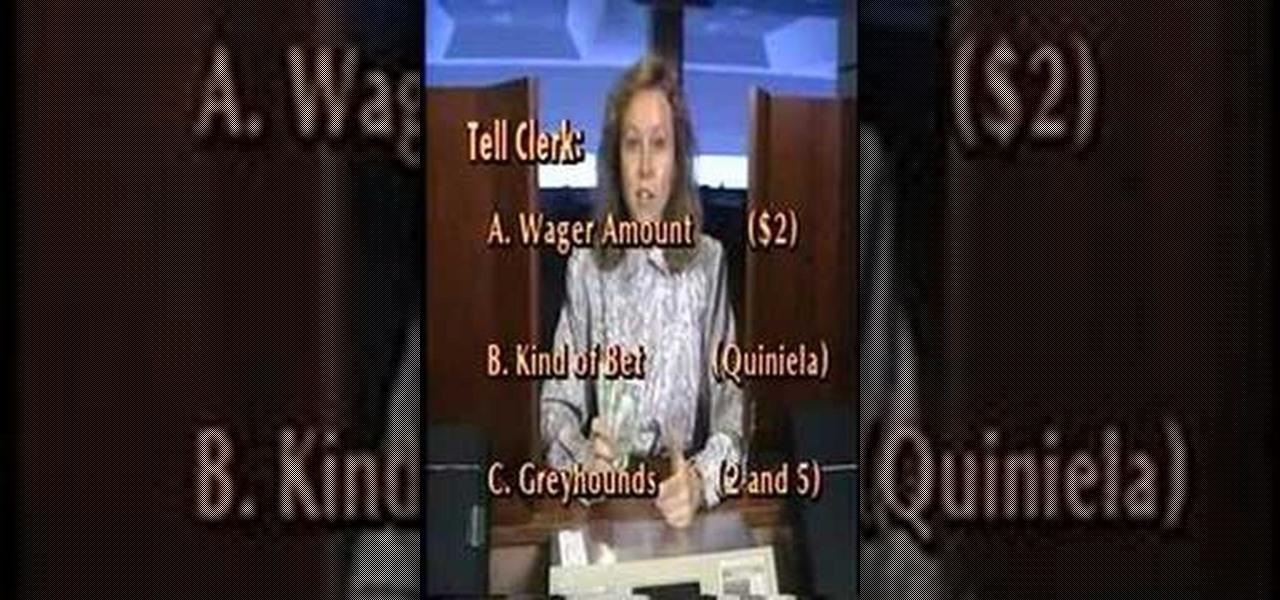
Learn different ways to bet at the greyhound racetrack.

Learn a bar bet trick in which the bet is that you can pull a bill from between two bottles balanced on top of one another.

In this two part video, learn how to build a scaffold or a bridge between two glasses that is strong enough to support another glass on top of it.

Short on cash? Why not trick someone into buying you a free drink if they can't do everything you do. Learn the simple trick to this mirror bet. Watch this video magic tutorial and find out how to do the mirror bet bar trick.

Learn what to play before the first round of betting. Understand how to bet, when to bet, and in what increments to better your position and your hand.

Make lightning and generate tens of thousands of volts in your own kitchen at home using ordinary household objects! Mr. G demonstrates the amazing Triboelectric Effect and explains the electron exchange via adhesion and separation that makes it all possible.

Suckers bets are the easiest way to makes some money. You only need to be able to do something that seems impossible, but is exactly the opposite.

Even if you and your office cohorts don't exchange cutesy valentines on Valentine's Day, you can still indulge in the vibrant, lovey dovey holiday by crafting one of these three paper favors for your kid's class.

Continuous Defense drill keeps your body squared to the offense. It's a point exchange drill that emphasizes positioning in defense for Australian rugby.

Greeting someone in English is very simple. Check out this instructional video to learn how to greet someone in English. "Social English" is a series of four short videos that deal with common face-to-face English situations at Fujikin. This is the second video in the series and will show you how to exchange greetings in English.

You're about to learn some incredible close-up magic tricks from Close Up Card Tricks that you can perform right away. You don't have to be a professional magician to do these card tricks, and you don't even have to practice them that much!

Whether you use Google Calendar, Exchange, iCloud, or any other service, you need a good Android calendar app to keep you organized on the go. For many folks, the obvious answer was always Sunrise Calendar, but Microsoft purchased the company behind this awesome app in a classic acqui-hire move, and now, Sunrise has officially been shut down.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Become the most feared gunslinger in the West! This Flash game is quite easy - just exchange six-shooter shots with your enemy. The video shows you several cheat codes you can enter for extra ammo, life or other goodies in Gun Blood.

The White Elephant gift exchange is a popular game to play at holiday parties, and there are several variations to the rules. This vidoe gives you a quick description of each, so you can decide which version is the best for your own party.

The foreign exchange, or forex, market is a relatively safe place to invest money, but like with any investment research and understanding indicators are key to making profits. Watch this video to learn how to use forex trading spreads to read the market and make sound investments.

In this trick, bet someone that they can't transfer two corks between their hands and separate them without getting stuck. Unless you know the trick, you won't be able to do this. Check out this tutorial and let Scuba show you exactly how to do this funky illusion and win many bets.

If you are looking to win an easy bar bet, check out this video. In it, you will learn how to link two paperclips together using magic and without ever touching the clips!

Ever try your hand at betting on the ponies? It's a hard sport to bet on if you're just starting, and you should know everything you need to before you start, or you're just going to be throwing your money away.

Make someone write something on a note without you watching. Bet that person you have a note in your pocket saying the exact same. Great for Bets. Win Beer.

Wanna know how to get a shot at any bar for just a dollar. Mr. Magicpants gives a wealth of barroom strategy. You gotta botch the first bet. Wager a $1 on a drink. Then lose the bet. The mark gets to drink it. Walk away and he's left paying the bill!

PDF files are a great way to exchange documents over the web and between platforms. Now, with Apple Preview in Mac OS X Leopard, you can preview, rotate and extract pages. To learn more about manipulating PDF documents from the Apple Preview program in OS X Leopard, watch this how-to.