How To: Edit file associations in Windows XP
Did you know you can control which software opens which file extensions on your computer in Windows XP? Learn how to edit file associations and default to your favorite programs.


Did you know you can control which software opens which file extensions on your computer in Windows XP? Learn how to edit file associations and default to your favorite programs.
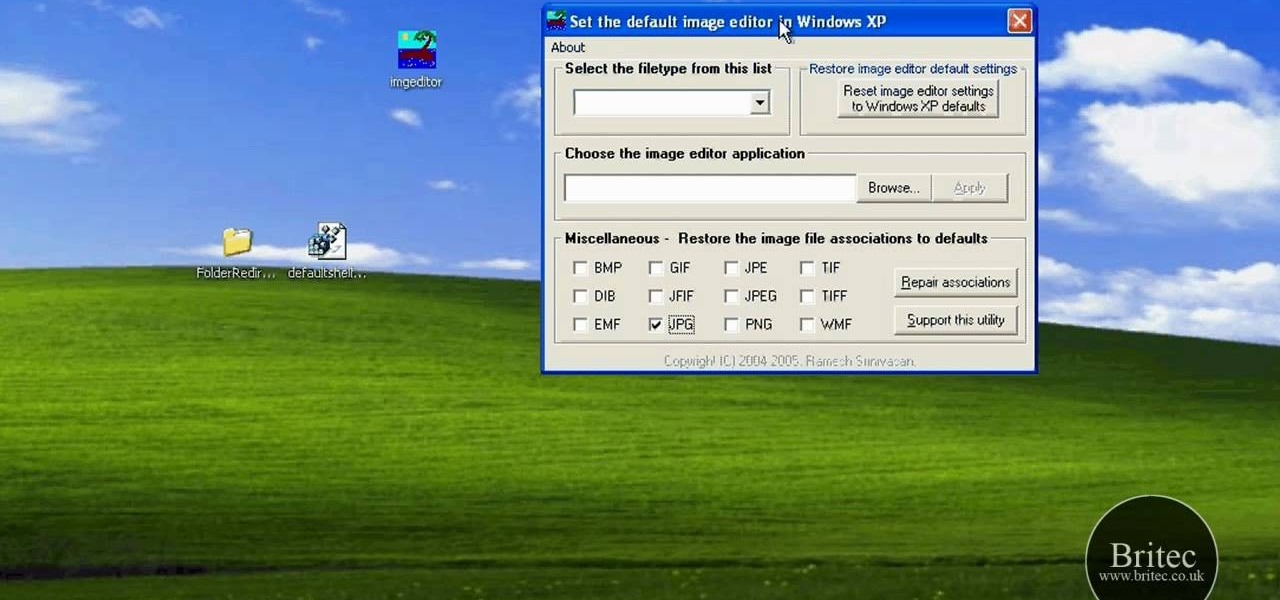
Need help figuring out how to repair file assocations on a Vista or XP PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.
File associations associate a file extension to a file type. In this Dreamweaver 8 video tutorial you will learn how to set file associations, specify Dreamweaver preferences and boot the right program from Dreamweaver. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Set file associations in Dreamweaver 8.
This video tutorial from butterscotch presents how to change file associations on your computer.File association is a link between a certain type of file (.doc, .gif, .txt) with a particular program.For example text files are by default associated with Notepad application.So if you double-click text file it will be automatically opened in this program.In case you want to open this file in a different type of program, you need to change the file association.To do that, right click the file, th...

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

In this video, US Memory Champion Chester Santos teaches you how to expand and improve your memory by using a few simple techniques. Word visualizing allows you to create associations which help to remember individual words. Memory can be increased in a fun and easy way by taking advantage of Santos' cool and unique method of associative thinking. You will hopefully never forget your shopping list again!
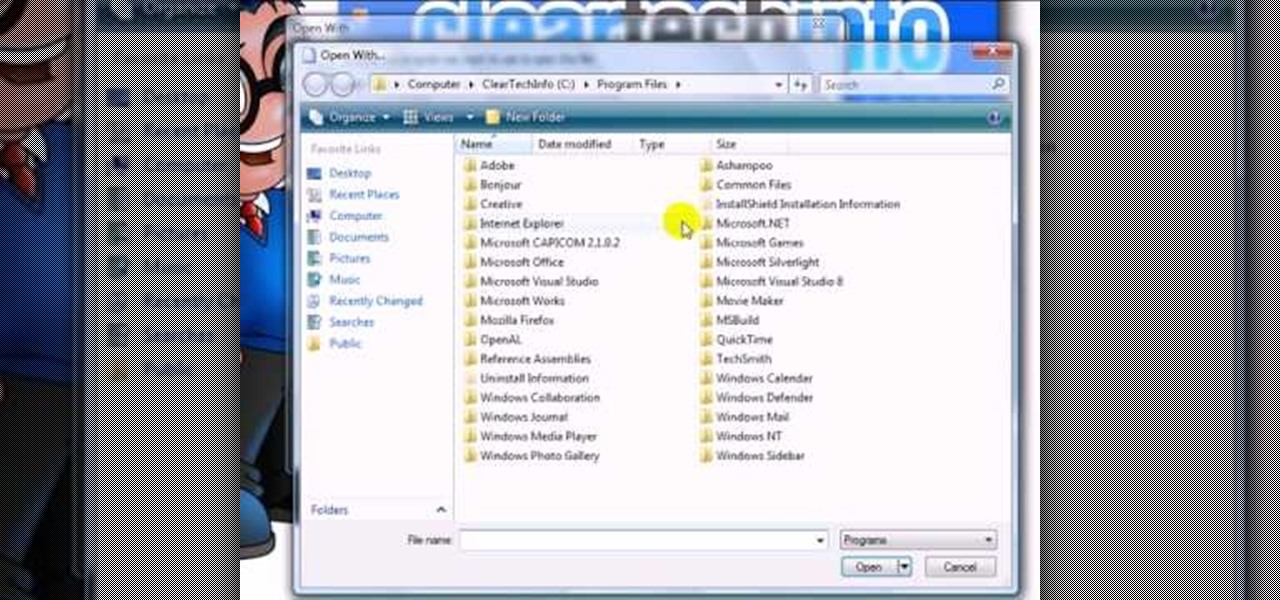
This video shows you how to easily change the default program associations of any file type. The movie shows you how to change the default program association of a JPEG file, but you can use it with any of the known file types. The first thing you have to do is right-click the desired file, hover your mouse to Open With and wait until a sub-menu appears. There, click Choose Default Program. Then, choose any other program that you want to open that specific file extension by clicking the Brows...

You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.
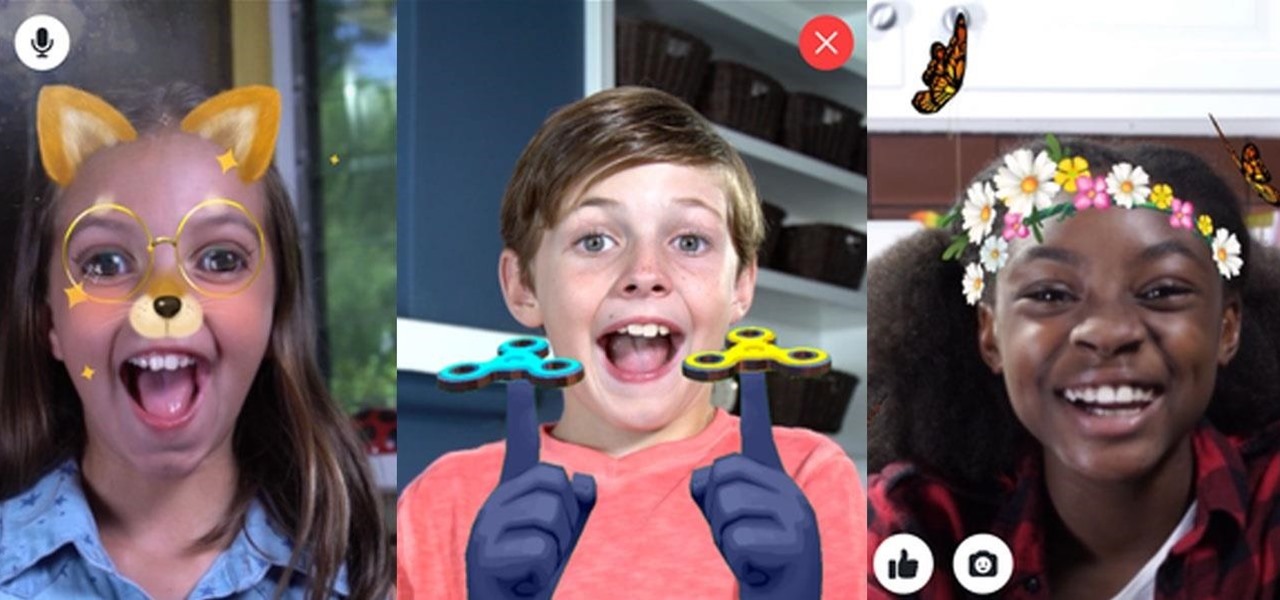
Next to millennials, one of the groups most coveted by brand marketers is "Generation Z," the consumers of tomorrow who were born between 1996 and 2010. On Monday, Facebook established a beachhead with that demographic in the realm of augmented reality by launching Facebook Messenger Kids.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Augmented reality was recently named the "Mobile Disruptor of the Year" for 2017 by Mobile Marketer, but the technology is showing no signs of slowing down as we head into 2018. In fact, the technology appears to be gaining momentum.

For many of us, pets are important family members. They give us loyalty, companionship, and comfort. Now, researchers have given us another reason to welcome them into the family: Babies from families with furry pets — the majority of which were dogs — had higher levels of two types of beneficial gut bacteria.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.

Seeing that you probably can't go ten minutes without lying (according to this study), you're probably interested in becoming a better liar. The best way to do so is to learn what makes a bad liar, and then do the opposite.

What would you say if I told you it was entirely possible—even desirable—to cook anything from a simple dinner to a great loaf of bread without using measuring cups, spoons, or a scale?

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

If you're someone who frequently awakes in the middle of the night trembling in terror, you might want to consider swapping sides. According to research done at Yüzüncü Yil University, those who sleep on their left side experience more nightmares than those who sleep on their right.

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.
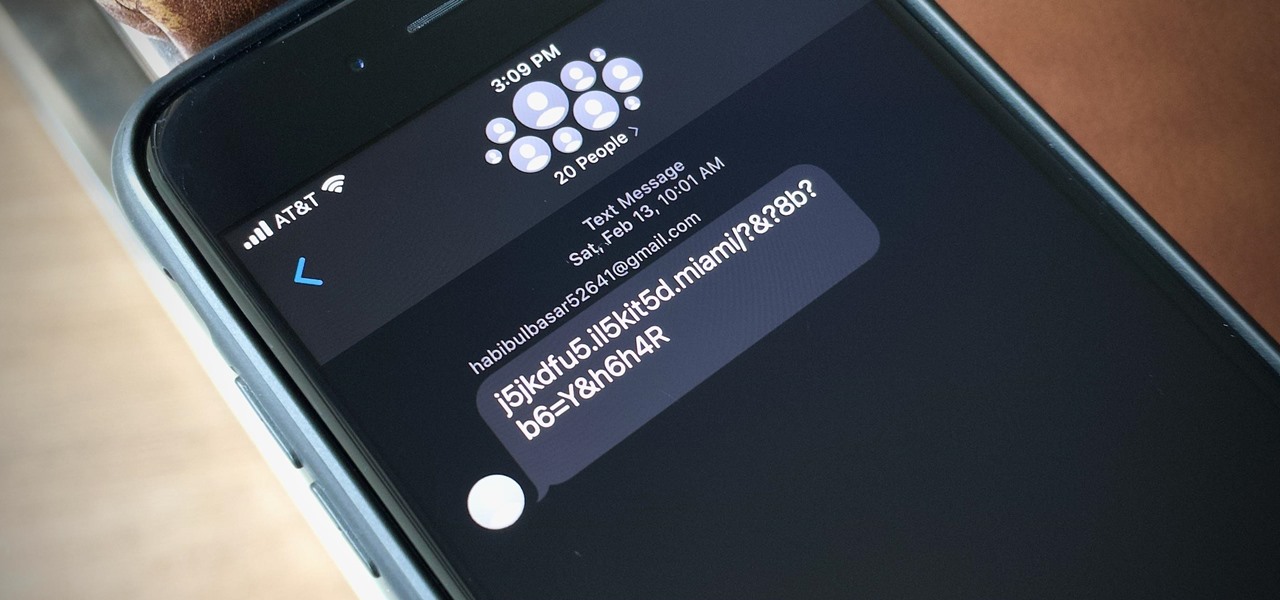
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

What is a cataract? A cataract is the clouding of that internal lens of the eye which is normally clear. That internal lens helps focus light as it comes through the pupil that when a lens starts becoming a little cloudy, patients sometimes complain that their vision seems a little foggy. There are certain risk behaviors that you can avoid to reduce the risk of getting cataracts. Get professional tips and advice on cataracts in this medical how-to video.

There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.

Whether it's your credit card, your parents' new zip code, or a new work phone number, number sequences are everywhere. Sometimes it's important to actually remember them instead of always relying on a smartphone or the internet to remind you.

Video games were blamed in the death of Chris Staniforth last May, but now things have gotten worse as video games take the blame for a more recent tragedy...

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...