The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

The National Security Agency is storing all electronic communications and analyzing them in real time, according to former NSA employee turned whistleblower William Binney, who warns that the federal agency has a Google-style capability to search all conversations for keywords. » Whistleblower: NSA Analyzing Conversations In Real Time.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.
Check out this video on color theory: analyzing color. It is important to understand color relationships and harmonies when designing everything from brand advertising, websites, video games, fine art, clothing and interior decoration. Tutorial video from Sessions Online Schools of Art & Design's "Color Theory" course. Part of Sessions' Graphic, Web, Digital Arts, Marketing, and Multimedia Arts Design certificate programs.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

This half-hour episode of Hak5 covers several topics: Using a DSLR camera to create HD footage, building your own Google TV, unlocking & copying locked files with Lock Hunter, using PicPick for screen capture, using WinDirStat for analyzing & cleaning your hard drive, setting up a secure FTP server with Ubuntu Server, and secretly copying data from USB drives with USB Dumper.

This video explains how tree growth rings function and what they can tell us.The growth rings are formed in 2 (sometimes 3) layers of wood that are the spring growth and the summer growth. Ring width can vary depending on the specie of the tree, the environment in which it has grown and the amount of water it has used. By counting the rings you can tell the age of the tree.By analyzing the growth rings, you can see the years in which there was a drought where the tree once stood, because the ...

This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.

Your childhood is arguably the stage of development where you look most cute and naturally perfect for photographs, so it makes sense that your parents compiled albums after neverending albums depicting several hundred different angles of your cute little tushy (grimace).

This tutorial looks at how to describe a linear system without actually graphing it. In order to do that, you will need to convert both equations of a problem into the Y=mx+b format. Once you have done this, you will be analyzing the m and b values. There are a few rules to follow. If the slopes (or m) and the Y intercepts (or b) are equal, there are an infinite number of solutions (or dependent equations). A second rule is if the slopes are equal and the Y intercepts are different, then the ...

These two videos focus on analyzing chess positions, and generating candidate move orders from the position without moving the pieces or using computer analysis. The goal is to improve the ability to generate lines and variations mentally during a game, and to try to come up with a move that either maintains equality on the board, or paves the way for a slight positional edge.

Discover how After Effects redesigned Motion Tracker (After Effects Professional only) gives you more power to synchronize motion between two elements in a composited scene. Learn how Motion Tracker works by analyzing the moving pixels in each frame and then using that data to control the motion of a new layer. Set as many tracking points as you like or choose from a list of defaults. Also see how Motion Tracker's interface and controls have been simplified to be faster and easier to use.

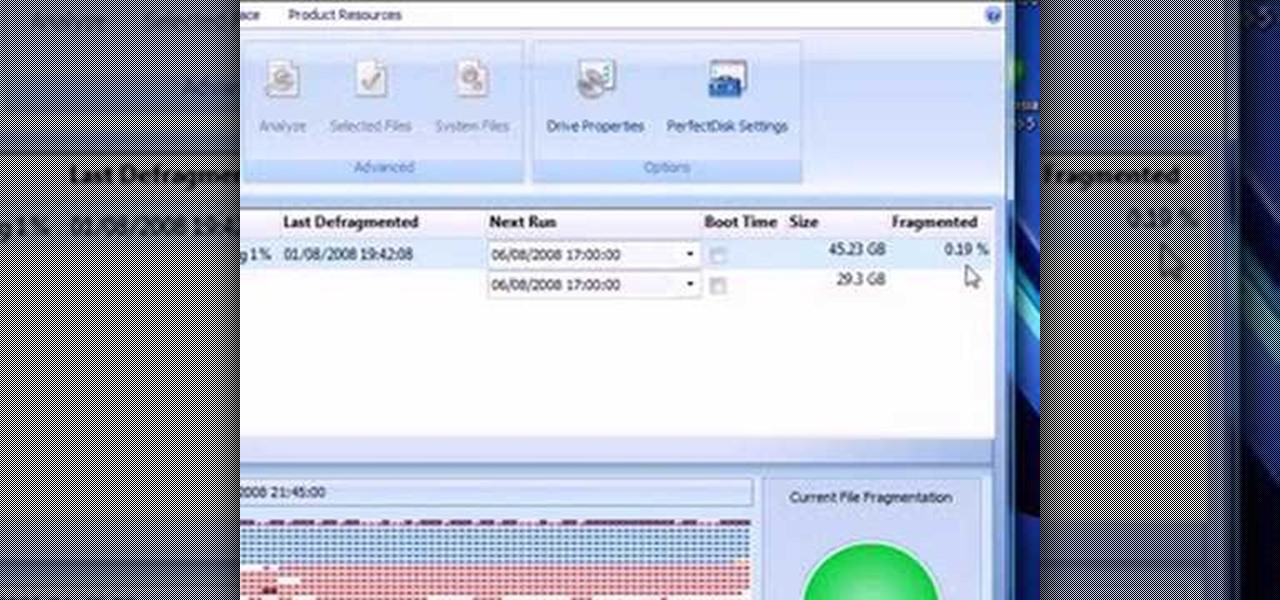
This video presents how to defragment and shrink a Windows Vista partition using Perfect Disk 2008 Professional program.First you need to download and install software application named Perfect Disk 2008.Type Perfect Disk 2008 into Google search engine, choose first link from the list.On the Raxco software home page choose Free Evaluation option from the list to the right.Download and install Perfect Disk 2008 Professional.Once it is installed, run the application. From Menu choose Analyze op...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Analyzing a play can help actors, directors, or scholars to understand everything about a given play. Learn how to write a play analysis in this free theater video from a college professor.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

On June 5th, robotics firm Aldebaran and SoftBank Corp., the Japanese giant that owns Sprint (and possibly T-Mobile), unveiled an emotion-sensing robot named Pepper.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

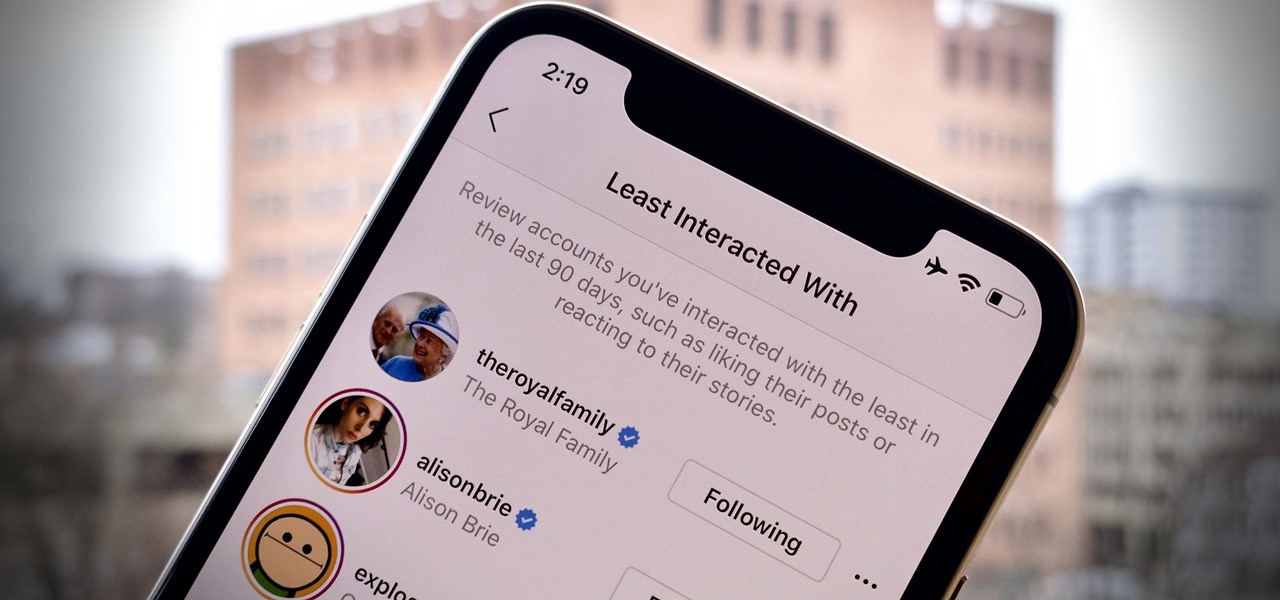
Is your Instagram feed a bit cluttered? Maybe you're seeing posts from people you don't even recognize. Perhaps the content isn't interesting. Whatever the case, it's common after years of having an account to follow too many users whose posts just aren't doing it anymore. Luckily, Instagram has an easy way for you to purge unwanted accounts from your following list.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

When it's hard to hear what's being said, subtitles give you clarity where audio falls short. Thanks to Android 10, your Galaxy S20 now lets you enable a live transcription of your phone's internal audio stream, meaning you can get closed captions in virtually any app — even if the app doesn't otherwise support them.