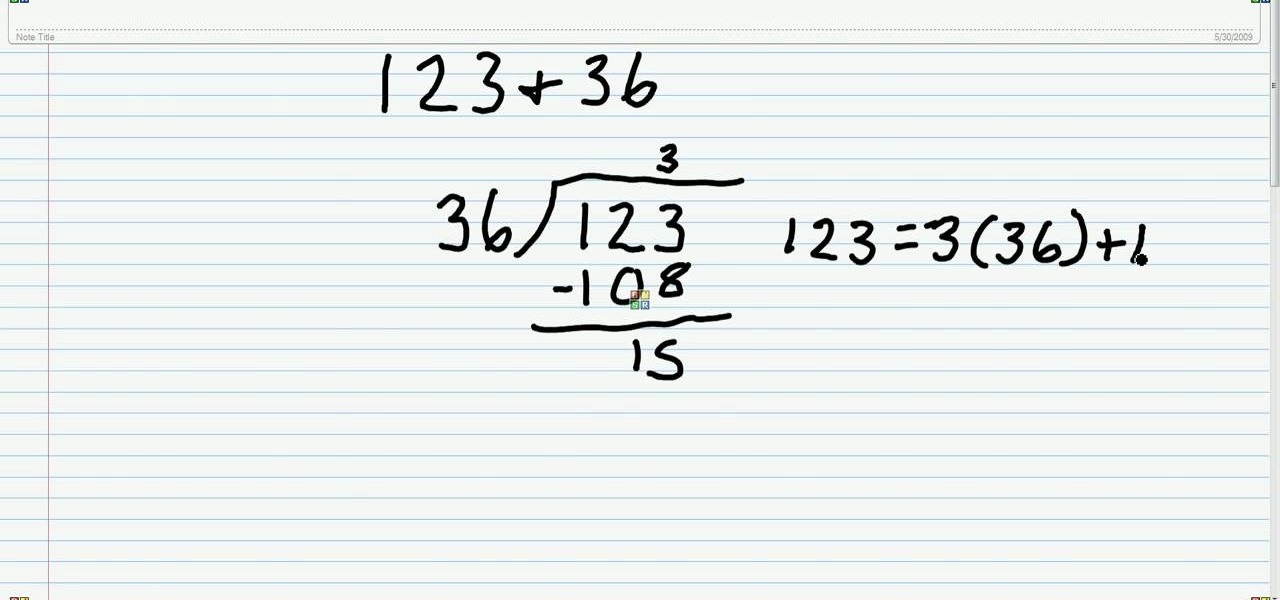A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

This video tutorial is for beginner puzzlers who are getting more advanced in their speedsolving of the Rubik's Cube. When solving the Rubiks Cube, there are these mathematical equations called algorithms, which I'm sure you already know, but in this algorithms you may find the need to mirror them, or reflect them, to get the exact opposite, forming a new algorithm. Well, this video will teach you all about how to reflect or mirror algorithms for the Rubik's Cube.
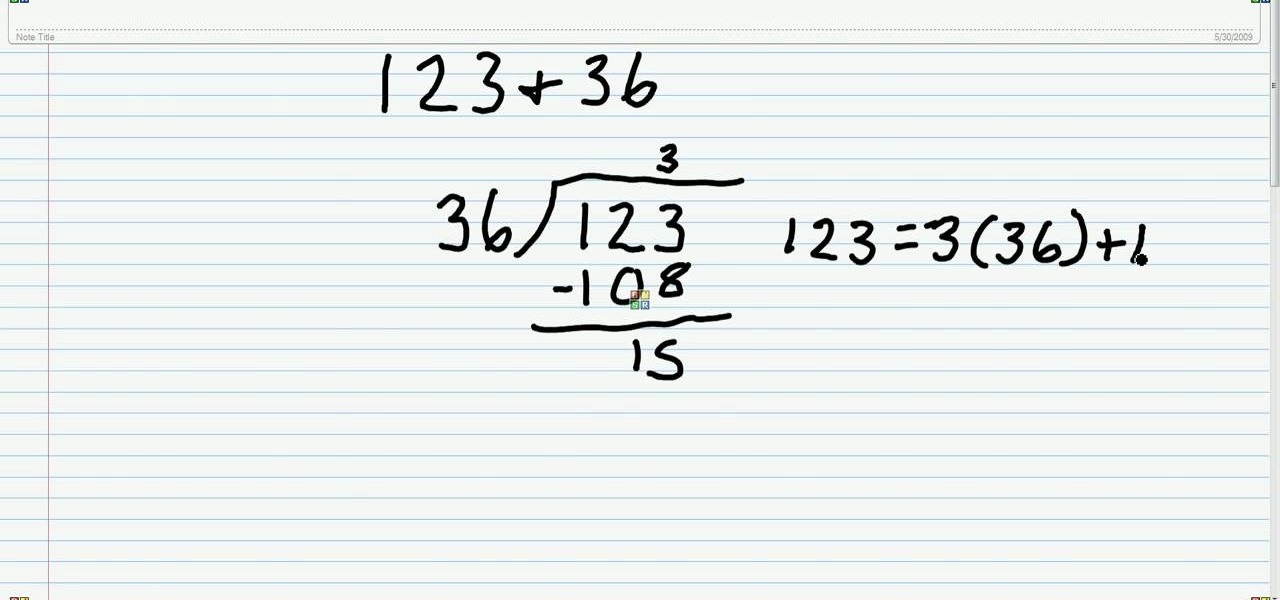
Here's a neat trick. Learn how to find the greatest common factor for a number set using the Euclidean algorithm! From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test).
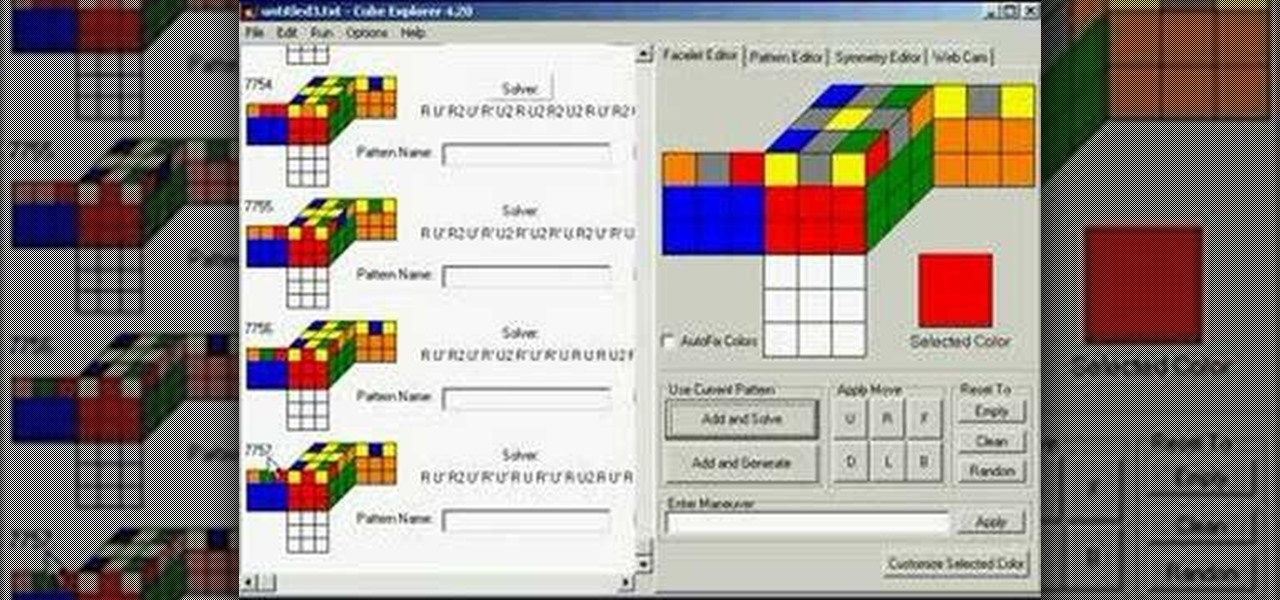
This is a basic tutorial on using the Cube Explorer computer software to create your own custom algorithms for different 3x3 Rubik's Cube patterns. And just when you thought the Rubik's Cube couldn't get any more fun!

Learn to solve a Rubik's Cube in no time flat with these easy algorithms to fix those puzzling problems. Whether you have a color that just needs to move a few spots or the proper placement is just a few places off, you can follow these step by step turns of the cube done slowly enough to follow along. The algorithm is even displayed on the bottom of the screen for people savvy in Rubik's Cube terminology. He explains several issues and scenarios that most people encounter when trying to solv...

http://www.seonorthamerica.com Find out about Google's algorithm and why it has to keep using it. What is Google's problem?

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

By "God," I mean Morley Davidson, John Dethridge, Herbert Kociemba, Tomas Rokicki and about 35 CPU-years.

Have you ever wondered how credit card numbers work? I mean, how they really work? How do they come up with the numbers? Credit cards actually follow a very specific pattern. Let's take a look at how they're set up.

Guiding internet users to useful content is one of the most lucrative businesses in the world. This process is called aggregation. Google and other search engines form the top of the food chain, aggregating all of the content on the web in response to queries. There are all sorts of other important aggregators though, and you probably use at least one every day: Fark and Reddit for web content, Rotten Tomatoes for movie reviews, and Metacritic for a variety of media, but most importantly, vid...

As the best-selling toy of all time, the odds of you once playing with a Rubik's Cube are pretty high. And if you're like me, or even the cube's inventor Erno Rubik, your first attempts likely ended in futility. Every twist, every turn, the cube just gets more and more mixed up. Is there really a solution?

So, you can solve the Rubik's Cube, good for you, but what about the Square One? Erno Rubik is nothing compared to Karel Hršel and Vojtech Kopský, who invented the Square One puzzle, also called by its full title, "Back to Square One", or its shorter name of "Cube 21". It's shaped like a Rubik's Cube, but it's cut like a freak show, adding that layer of difficulty that challenges you.

This video tutorial is for beginner puzzlers who are getting more advanced in their speedsolving of the Rubik's Cube. When solving the Rubiks Cube, there are these mathematical equations called algorithms, which I'm sure you already know. But wait... what do algorithms have to do with notation? Well, in an algorithm you have a sequence of letters that tell you which sides of the cube you want to turn. Each of the six sides of the Rubik's Cube are associated with a letter and a symbol that tel...

Watch this how to video to figure out how to solve the 4x4 Rubik's Cube Revenge. So, get out your Rubik's or Eastsheen Cube and watch this tutorial.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

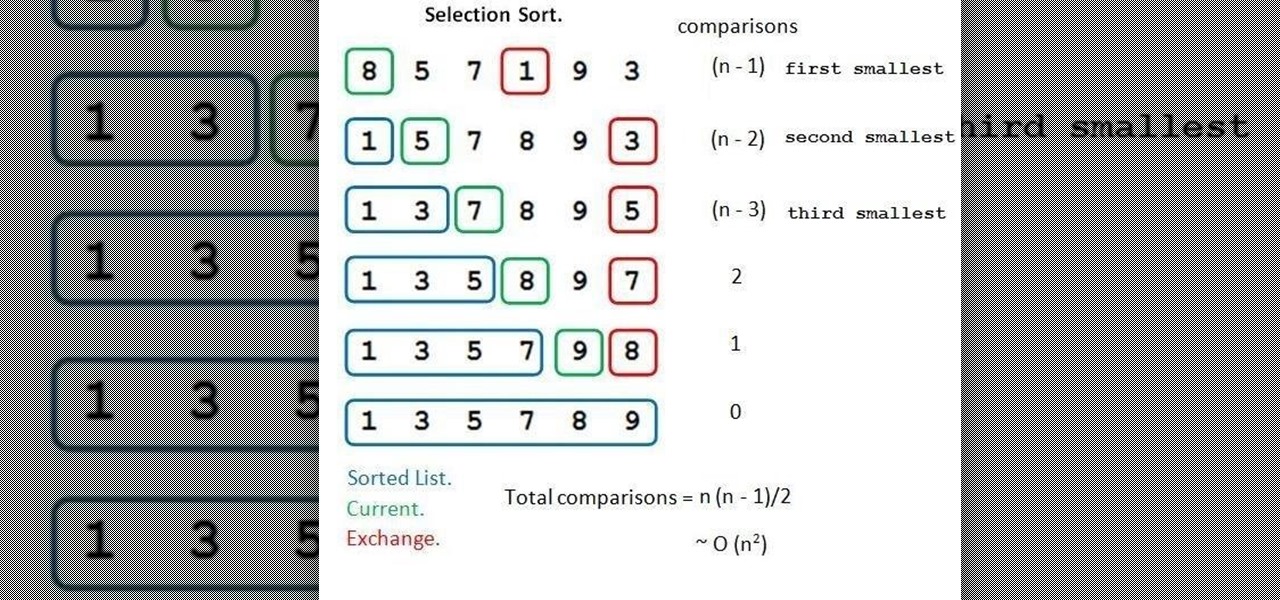
Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

In order to solve a 5x5 Rubik's Professor Cube, you'll need to, of course, already know how to solve a 3x3 Rubiks Cube. First, you'll need to get the centers solved first, then you pair the edges (with the algorithm 2D*, R, F', U, R', F, D'*), and solve parity (with the algorithm 2R*, 2B, 2U, L*, 2U, R'*, 2U, R*, 2U, 2F, R*, 2F, L'*, 2B, 2R*), then you continue to solve it just like a normal 3x3 cube until it looks brand new, out of the plastic box.

This is a Google Tech Talk from March, 26 2008. Timothee Cour - Research Scientist lectures. Movies and TV are a rich source of highly diverse and complex video of people, objects, actions and locales "in the wild". Harvesting automatically labeled sequences of actions from video would enable creation of large-scale and highly-varied datasets. To enable such collection, we focus on the task of recovering scene structure in movies and TV series for object/person tracking and action retrieval. ...

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Find out a new way to solve the Rubik's Cube made famous by Erno Rubik, master puzzle maker. Try to get the OLL (Orientation of the Last Layer) using a new method that lets you look at the cube and figure out a two algorithm move solution to orienting them correctly. Just watch this video tutorial to see how to solve a Rubik's Cube with the Compound OLL method.

This episode of Full Disclosure demonstrates how to hack/crack MD5 password hashes. MD5 (Message-Digest algorithm 5) is a hash function commonly used by websites to encrypt passwords. MD5 is a one-way hash; therefore, to crack the password you most try every possible dictionary word and if that does not work, every possible letter/number/symbol combination. The programs used to crack the passwords are Cain and MDCrack-NG.

First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

This is a demonstration on how to use the PLL method to solve a Rubik's cube. The author informs that what people do before and after applying the PLL technique is very important. According to him, people usually tend to first align as many faces as they can, when they see a partial algorithm and then apply the PLL method, which is very time consuming. Instead, one should stop one step short of alignment, apply the Pll method and then align the faces completely. The author, however, points ou...

Want to learn how to solve the mysterious Rubik's Cube? Well in this video, the viewers will be taught how to do so with the "Ortega method". The video provides a demonstration of this method with a 2x2x2 Rubik's Cube. At each step, the video breaks down the cube into different situations and which algorithm to use for which. The video demonstrates how to recognize each situation, what to do in each case and the fastest way to do so.

In this video the author shows how to solve a Rubik's Cube using Peter's method. He says that he is not going to give any algorithm or step by step procedure but that he intends to give an over view of how to solve a Rubik's Cube. He starts with the basics of Peter's method. He starts with explaining few pointers like the tiles in the middle of each faces of cube never really move and he tells the basics of how to hold the cube. He goes on and explains how to solve the cube by starting from a...

After Uber noticed that if you walked to a more convenient pickup spot — instead of your exact location — that it would save you time and money, they decided to make a change to their system.

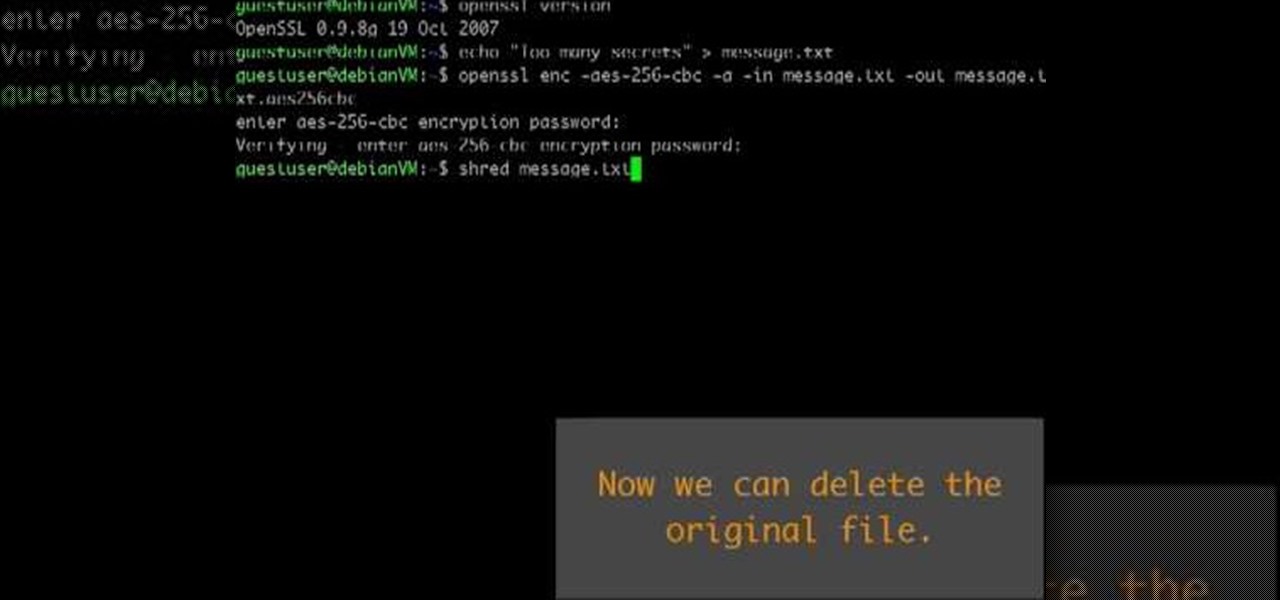
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Why solve the Rubik's Cube if you can't do it blindfolded, too? Don't be a loser. Learn memorization technique in this first video, then learn the algorithms.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.

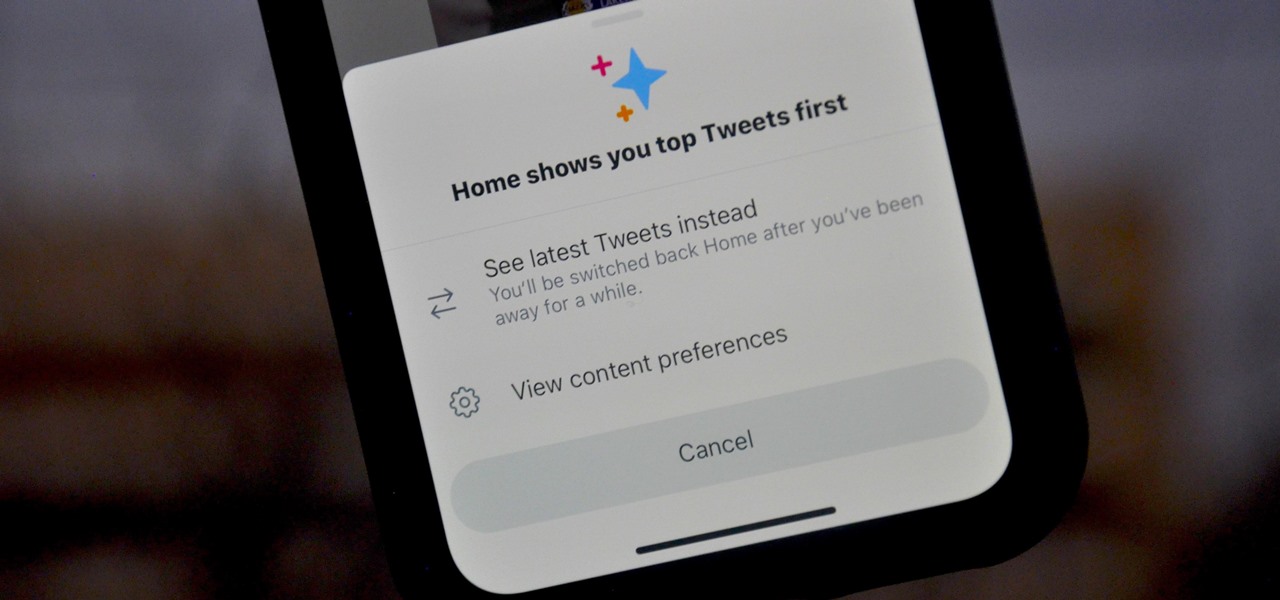
If you're tired of the so-called "top" tweets appearing first in your Twitter timeline instead of only the latest from the people, companies, and bots you follow, there's a way to get rid of them.

This year, as part of the Next Reality 30, in partnership with Snap, we're spotlighting an up-and-coming innovator in augmented reality. Specifically, we were searching for an independent developer or creator who embodies the bleeding edge spirit of AR and its ability to leverage machine learning. This year's honoree is Aidan Wolf.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.