Active Posts


News: iPhone 14 Series Leaks and Rumors: Everything We Know About Apple's 2022 Lineup
Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.
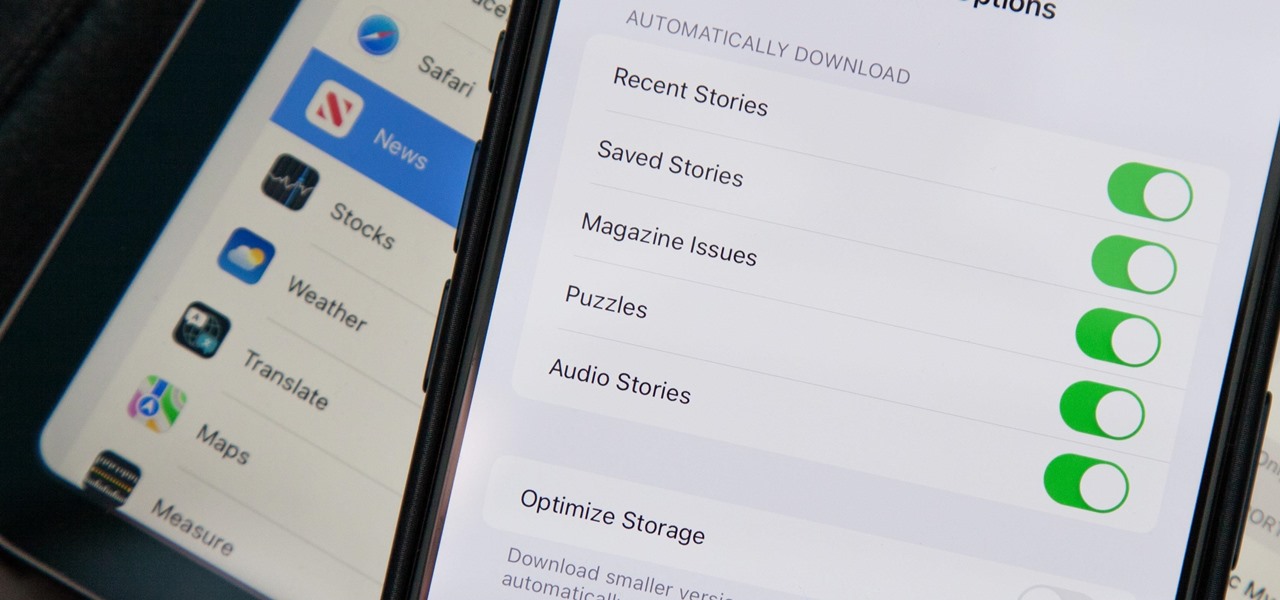
How To: Apple News Gives You More Options for Automatic Downloads on iOS 17.5
In the upcoming iOS 17.5 software update, there are new features for EU countries and mobile device managers only, but there are also more widespread user-facing changes to Books, Podcasts, and other apps. News is one of those other apps, and it's giving us more preferences for automatic downloads.
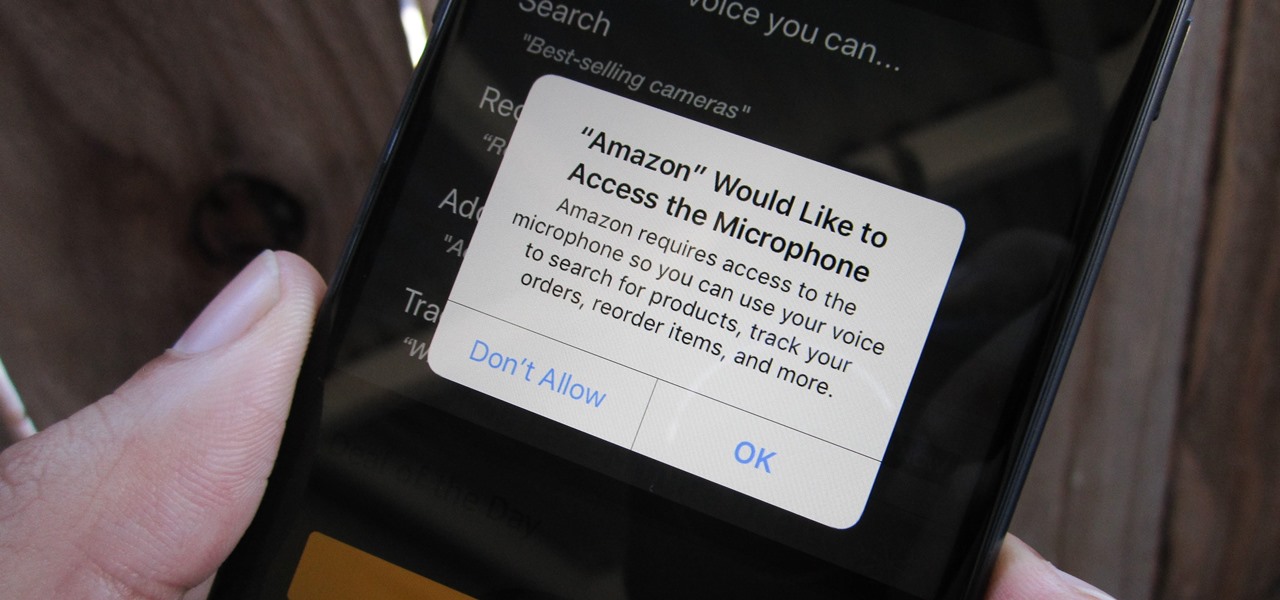
How To: Prevent & Stop Apps from Using Your iPhone's Microphone & Enhance Your Privacy
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

How To: Your iPhone Has a Secret Button That Can Run Hundreds, Even Thousands of Actions — But You Have to Unlock It First
An invaluable button on your iPhone can do hundreds, even thousands, of amazing things, but most iPhone users don't even know it exists. You can't push it. You can't click it. You can't press it. But it's the largest button on your iPhone, more powerful than the versatile Side button, and it's hiding in plain sight.
How To: 27 New Features and Changes Coming to Your iPhone with iOS 17.5
Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently in beta, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be coming in the stable build.

News: Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
Apple's spring event, where the company will announce a new iPad model, is just around the corner. We also expect to see the long-awaited Apple Pencil (3rd generation), also known more simply as Apple Pencil 3, with several significant enhancements that promise to make it an indispensable tool for anyone who uses their iPad for note-taking, sketching, illustrating graphics, and more.

How To: 11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
The app getting the most significant update on iOS 17.5 is, by far, Apple News. While there are a few changes in Books and Settings, as well as minor changes in apps like Podcasts, Apple News has at least 11 new features and changes you should know, some of which are worth getting excited about.
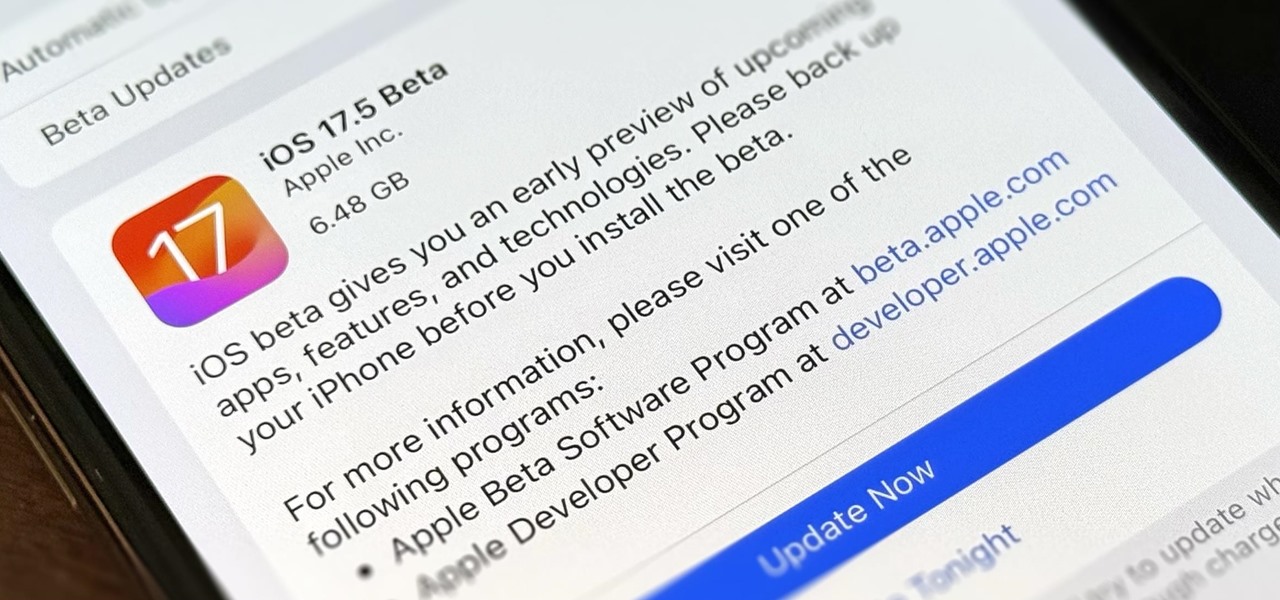
How To: Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
Apple is still not finished with iOS 17. We're just a few months away from its developer conference, where iOS 18 will be revealed, but there are still things to be fine-tuned on your iPhone until then. This brings us to iOS 17.5 — now available to try on your iPhone.
How To: Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
Apple's developer conference, where iPadOS 18 will be revealed, is just around the corner. But before we get there, there's still work to be done on iPadOS 17. That brings us to iPadOS 17.5 — and you can test drive it on your iPad right now before the masses.

How To: If You Keep Valuable Information in Apple Notes, You Need to Read This
Apple's Notes app has an important feature many users overlook, yet it's arguably the most crucial thing you should use for all your notes synced across iOS, iPadOS, macOS, and iCloud.com. And Apple makes the feature much easier to use than years before, so there's no reason you shouldn't be using it.

How To: Hide Private Photos on Your iPhone
When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

How To: 15 Hidden iMessage Features for iPhone You Probably Didn't Know About
There are many things Apple doesn't tell you about its products, and that's definitely the case when it comes to its Messages app. Hidden features lurk in your SMS and iMessage conversations just waiting to be found, and we've unearthed some of the most secret ones.

How To: If You're Going to Make Homemade Peanut Butter, You Better Use a Wok
If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut.

How To: Turn a Tortilla into a French Crêpe
Making a good crêpe takes practice and commitment. The batter is rich—most recipes incorporate melted butter, whole milk, and several eggs—and the cooking of the crêpe requires good technique. You have to learn to deposit and swirl just the right amount of batter to get the thinnest possible crêpe, and then learn how to loosen the entire circle and flip it over without tearing or snagging.

How To: The Two Things You're Not Doing for Perfect Macaroni & Pasta Salad
The noodle is a noble thing. And while I love ramen and pasta, I have a real soft spot in my heart for macaroni salad (especially the kind that comes with Hawaiian plate lunch) and the type of pasta salad that's dished up during picnics and barbecues.

How To: The Secrets to Giving Day-Old French Fries a Delicious Second Life
French fries, like mashed or roast potatoes, are the type O blood of the food world—they're compatible with just about everybody. That's why it's so sad to bring home leftover frites (that's French for French fries) and have to toss them out the next day because they don't taste as good when they're reheated. Warning: Do Not Ever, Ever Use Your Microwave

How To: Make Homemade Jerky Without a Dehydrator
Jerky is one of the tastiest snacks in existence. It's packed with richness, saltiness, and spiciness, and it's one of those things that you can't stop eating once you start. It's also fairly expensive, unless you're opting for the gas station variety which is… er… jerky in the same way that Folgers is coffee.

How To: Make a Self-Freezing Coca-Cola Slushy (Or Any Kind of Instant Soda Slurpee)
In my last quick clip, I demonstrated how to take a bottle of soda and freeze it on command. I received many requests for a more detailed article on this, so here we go. This "super cool" trick works with cans of soda too, not just bottles!

How To: Revive a Stale Baguette Using the Miraculous Water Trick
Everyone talks about how great sliced bread is, but there's nothing better than the taste of a just-baked loaf of crusty French bread. Like most beautiful things in life, however, the beauty of the baguette doesn't last. The next day, it's rock-hard, and good for very little except for croutons or breadcrumbs. But there is a trick to make it like fresh again.

How To: The Messaging Trick You Never Knew You Needed
Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

How To: 3 Easy Steps to Fixing Stuck Buttons on Your Phone or Tablet
As we go about our daily grind, our smartphones and tablets take a silent beating. Dirt, dust, oil, and grime that our hands have picked up immediately gets transferred over to our shiny pocket-sized computers every time we check the time or look for new notifications, and over the course of months, this can have a very noticeable adverse effect.

How To: Keep Your Night Vision Sharp with the iPhone's Hidden Red Screen
Night Shift, Dark Mode, Reduce White Point, and Zoom's Low Light Filter all help reduce the harmful effects on your body's clock that bright iPhone and iPad screens have at night. But there's another option on iOS and iPadOS that turns your entire display red, and it's useful for so much more than just late-night browsing in bed.
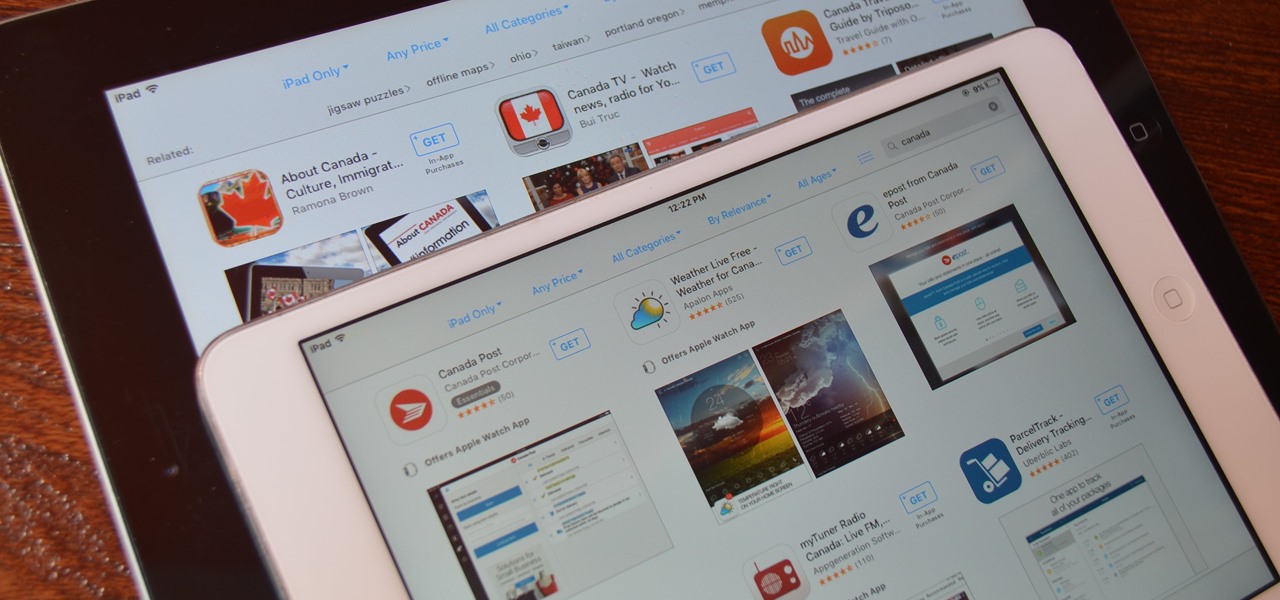
How To: Change Your App Store Country to Download Region-Locked Apps & Games on Your iPhone
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

How To: Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
If you're not using Control Center on your iPhone, you're missing out on a powerful tool that can streamline how you interact with your device, make certain tasks more efficient, and give you quick access to system tools, switches, and sliders for quick changes no matter where you are or what app you're in.

Hack Like a Pro: How to Hack Facebook (Facebook Password Extractor)
Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

How To: Assemble a model car
Learn how to assemble model cars, including what tools you'll need and how much precision is required in this free video series.
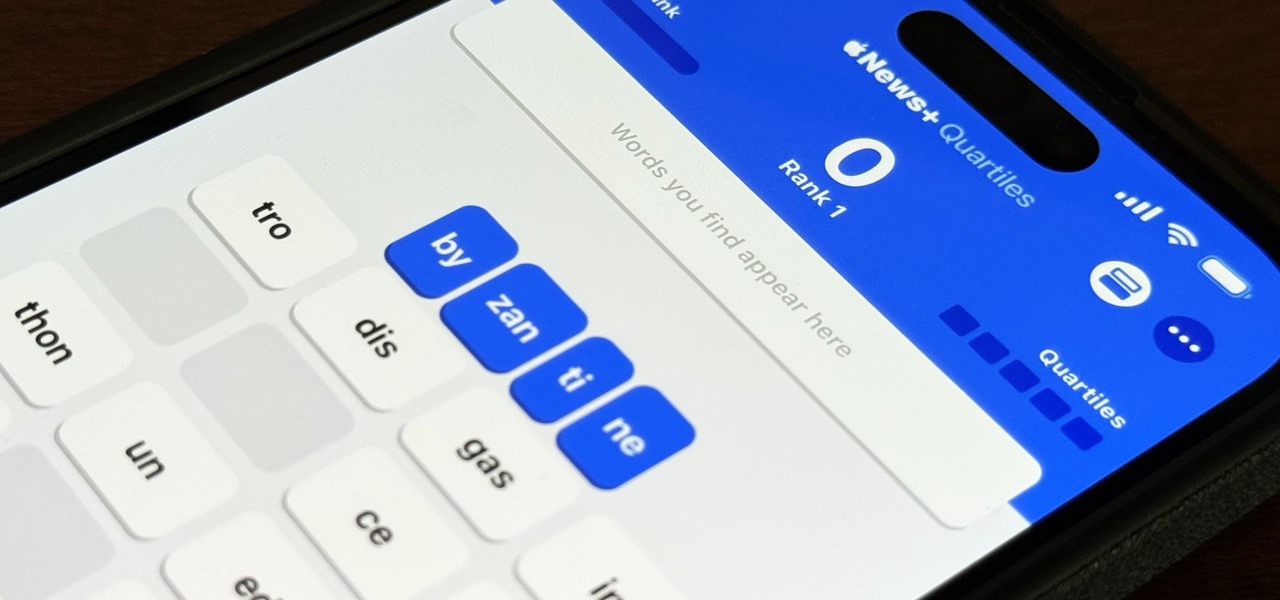
How To: Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
Apple's next software update, iOS 17.5, is relatively minor. Still, it includes one killer new feature for people who like word games: another lexical challenge to complement the crossword puzzles that Apple News already has.
How To: Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
Your iPhone is going to get a few significant improvements with the iOS 17.5 software update, but my favorite is Apple's enhancements to the Apple News app, which is making its Puzzles section even more fun with Game Center integration and even a new type of word puzzle.

How To: There's a Handy Shortcut for Typing Fractions on Android
If you're using the default Samsung Keyboard on a Samsung Galaxy smartphone or Gboard on a Google Pixel or any other Android device, here's a cool trick you should know about.
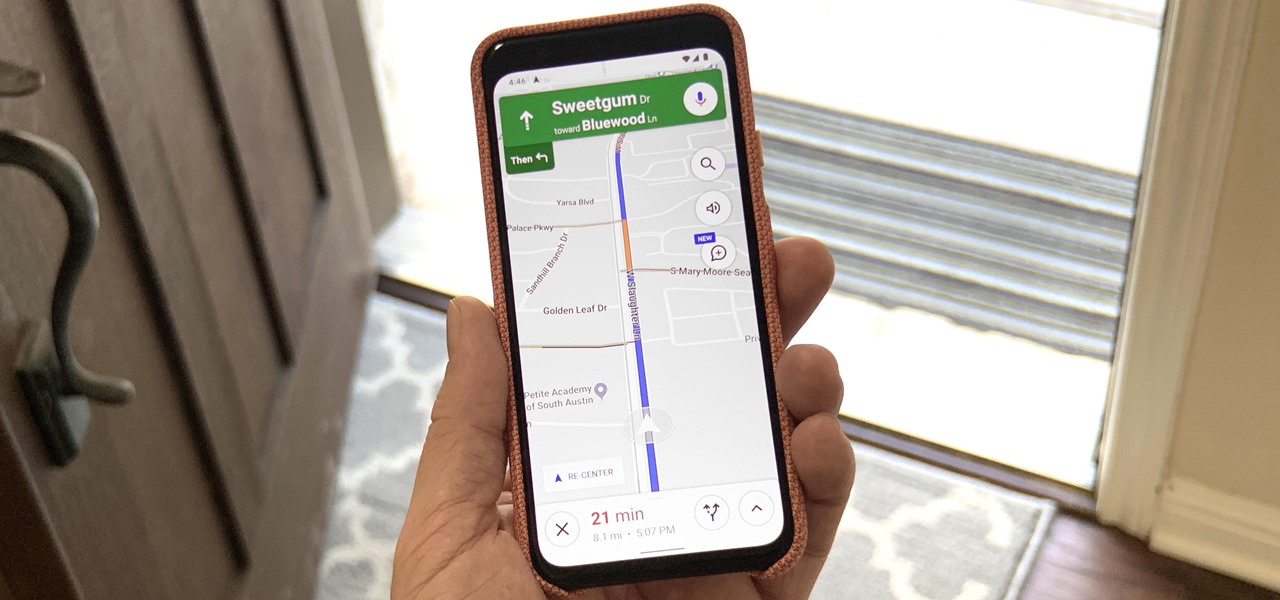
How To: Navigate to Home or Work in 1 Tap with Google Maps
Even if you're totally familiar with all the routes you can take to go home or work, you'll still want to use Google Maps to find the fastest route in current traffic conditions. If you're on Android, there's an extremely fast way to do this.

How To: Trigger iMessage Effects with Just a Keyword
One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

How To: 5 Things Cold Baths & Showers Can Do for You That Hot Ones Can’t
If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

How To: Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
Since Shazam became available on iPhone, it's been easier than ever to identify a song playing somewhere in the background. You could hear something you like while watching a movie or sitting in a coffee shop, and all you have to do is open the Shazam app and have it listen for you. But what about music playing on your iPhone via Instagram, TikTok, and other social media apps?

How To: Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
There's a lot you can customize on your iPhone's Lock Screen — wallpapers and photos, widgets, the display mode, notifications, and even the time's font and color. But there's another feature that lets you add custom text for whatever you want, whether it's an inspiring quote, a reminder, a warning to anyone who dares touch your iPhone, or even just your name.

How To: Every Hidden Special Character on Your iPhone's Keyboard That You Can Unlock Right Now
Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

How to Hack Wi-Fi: Disabling Security Cameras on Any Wireless Network with Aireplay-Ng
Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.
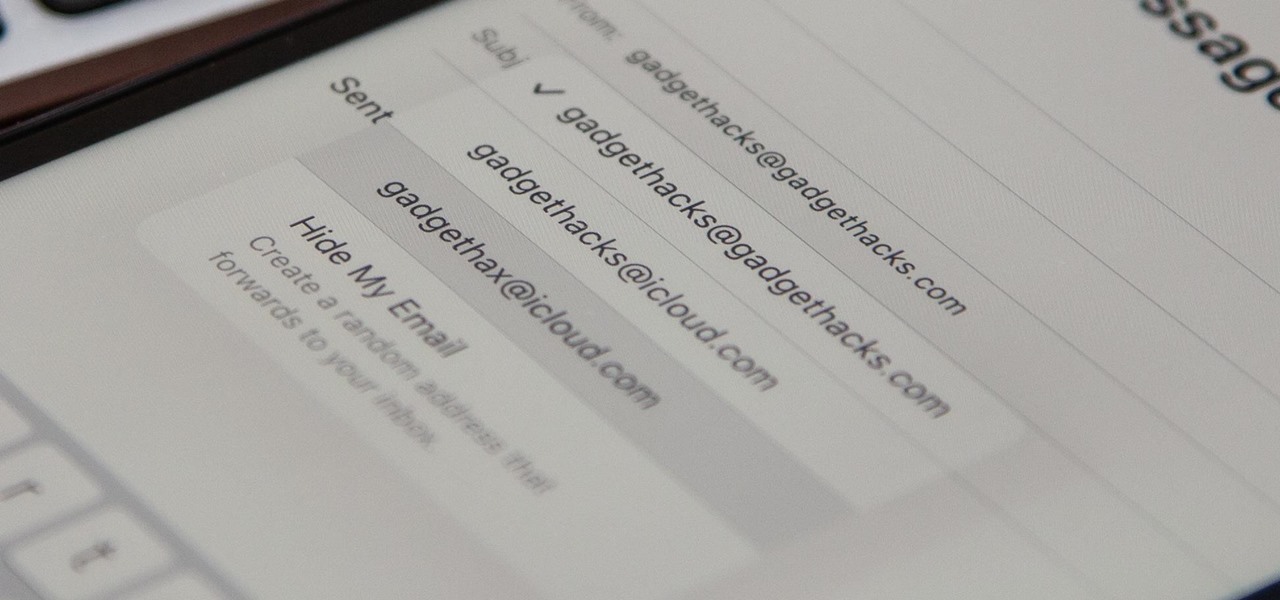
How To: Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
On your iCloud Mail account, you can easily use subaddressing to create hundreds of new iCloud email addresses to give to companies and other parties, all of which go straight to your primary iCloud email address's inbox. The problem with these types of alternative email addresses is that you can't ever respond to emails with the plus tag intact. But Apple has another alternative for you to start using.
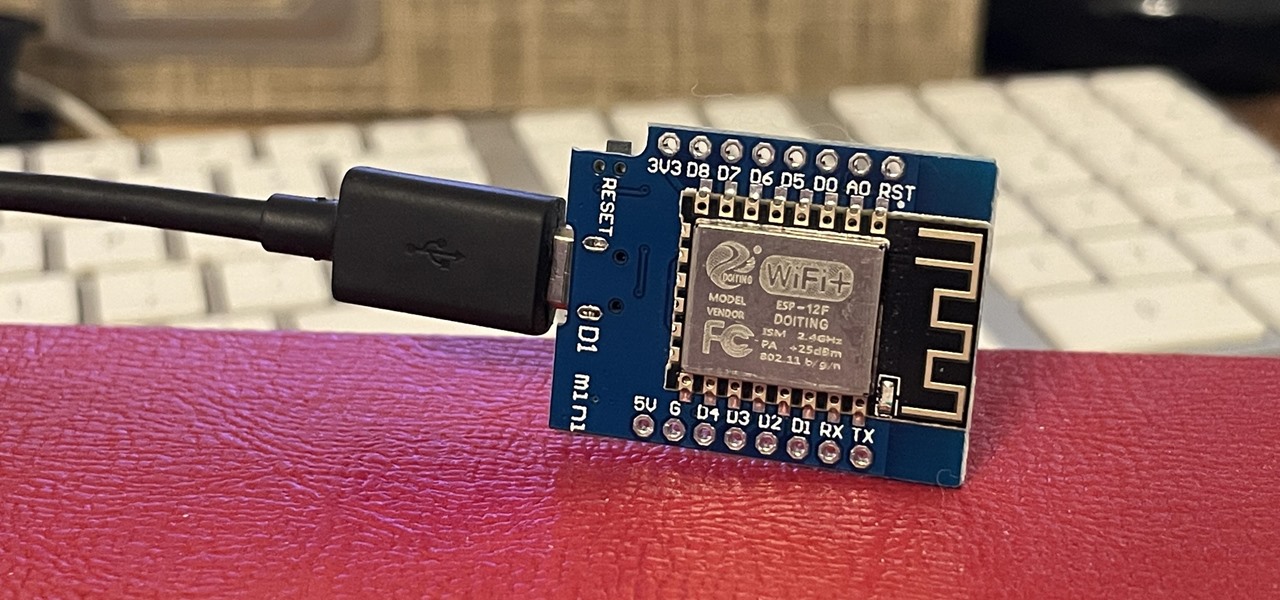
How To: Generate Crackable Wi-Fi Handshakes with an ESP8266-Based Test Network
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.
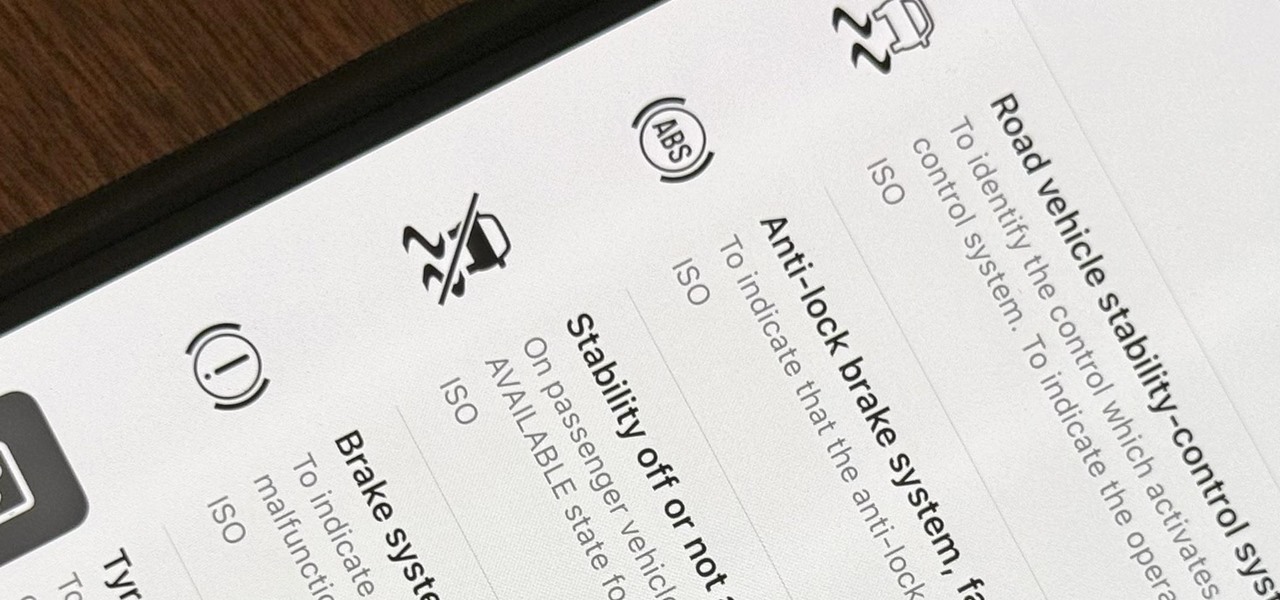
How To: Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
When you encounter a mysterious laundry care symbol or alarming vehicle indicator light, you might just ignore it rather than ask somebody, search online, or open a user manual for the answer. If you have an iPhone, there's an easier way to decipher the meanings behind perplexing symbols and signs—and it only takes a few seconds.
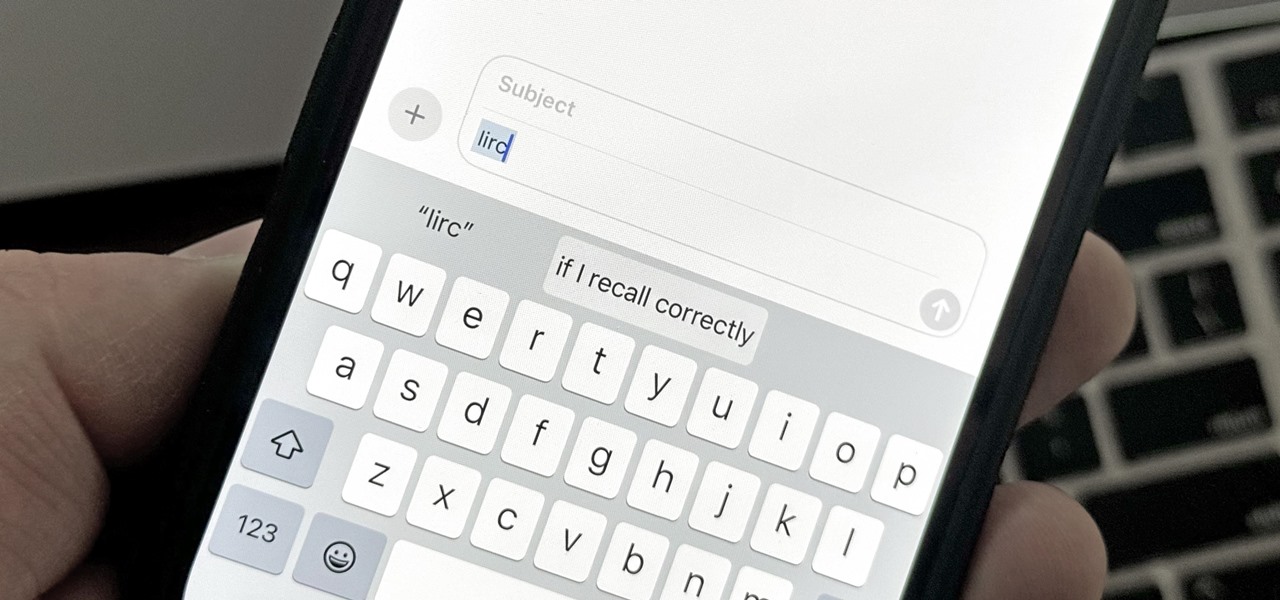
Text Replacements: The Secret Weapon to Typing More with Less on Your iPhone, iPad, or Mac
There are plenty of tools that'll help you type faster and more efficiently on your iPhone or iPad, such as Slide to Type, Dictation, and even a case with a physical keyboard. But one of the best tricks will help you type frequently used words, phrases, sentences, email addresses, and more faster, and you can sync your settings with your Mac so you can type more with less effort on all your Apple devices.




