Cytochrome P450 (P450s) are proteins found in nearly all living organisms, which play roles that range from producing essential compounds and hormones to metabolizing drugs and toxins. We use some of the compounds synthesized by P450 in plants as medical treatments, but the slow growth and limited supply of these plants have put the drugs' availability in jeopardy and jacked up prices.

After awarding $410 million to the company that supplies it with VCSELs and LiDAR sensors, Apple has made another strategic investment into a company that may contribute to future augmented reality hardware innovations.

Driverless partnerships continue to appear as Continental AG, leading German automotive manufacturing company, has signed a strategic cooperation agreement with global electric startup, NIO. The goal of this partnership is to research, share, and develop autonomous technology, among other developments.

We're going to look at 2 great core strengthening exercises. The Core Area, the abdominals, definitely corresponds with a stronger back so it's something that you want to do several times a week, once the body is warmed up, and remember to keep breathing so that you're supplying oxygen to those working muscles.

With the advancement of technology nowadays, cars are able to do things better than before. One area is the use of a key. Instead of supplying just a regular key to unlock and lock doors, they now have intelligent keys that make opening and closing much easoer. THey also make starting the car easier as well. So in this tutorial, you'll find out how to use one on a 2010 Nissan Murano LE AWD. Good luck and enjoy!
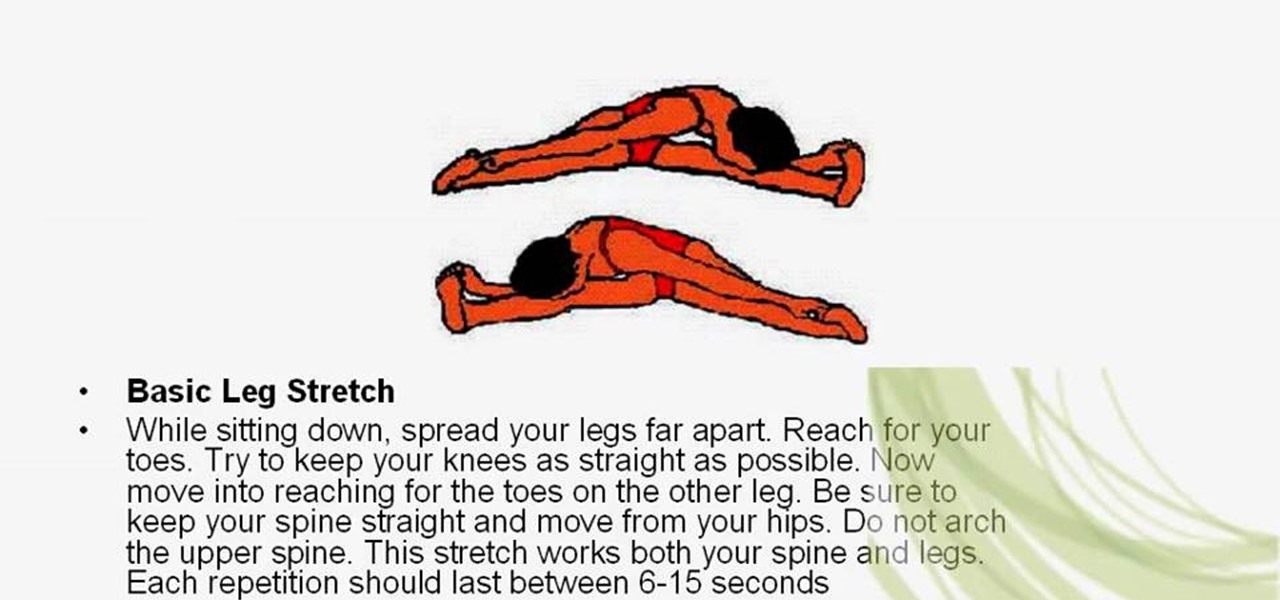
Almost everyone wants to be a little bit taller. By following the simple stretches and exercises outlined in this video we learn that it's possible to gain that inch or two simply through straightening your spine and posture, and through overall muscle health. Listing a dozen mostly yoga related positions, ranging from the Cobra position to the Yawn stretch to the Downhill, along with supplying health diagrams for each and every one, this video shows you how to get the most out of your body's...

Young children have growing bodies and need healthy snacks for supplying nutrients and energy, especially preschoolers. Their little stomachs just can't handle it. Therefore, it's very important to incorporate some snacks into their daily routine. Try these tips for buying snacks for preschoolers in this nutrition how-to video.

Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.

In order to register a domain name at Name.com, you will need to set up an account at Name.com. When you have set up an account, by supplying a username and password, you will need to log in. You will be able to check to see if your domain name is still available by typing it in, in the orange search bar, near the top of the page. After you type it in, click on search. Try ".org" first.

This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

While Modiface, YouCam, and others have been playing in the virtual make-up marketing pool for a while, here comes Google ready to splash down with a cannonball.

On Thursday, Osterhout Design Group (ODG) revealed a new, specially-crafted oxygen mask that uses the same augmented reality technology from its smartglasses to assist FedEx Express pilots navigating dangerous conditions.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

Sure, it's the giving season, but sometimes you've just got to treat yourself to some cosmetics. If you're shopping at Walmart, L'Oreal just made that a shade easier when shopping for Garnier hair color products with an assist from Google Lens and the Modiface AR platform.

Just as Apple, Snapchat, and other tech giants are working on augmented reality wearables in the race to replace smartphones for the future of mobile computing, so is Samsung.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

If you have an Apple Watch, you might know that the activity awards you earn can be shared with your friends as iMessage stickers on your iPhone. However, you first have to earn achievements in order to use them as stickers. That changes somewhat with iOS 12, as Apple added animated activity stickers for all Apple Watch users, whether they've earned award badges or not.

Among the revelations uncovered during the December unveiling of the Magic Leap One: Creator Edition was the fact that the Lightwear augmented reality headset would be tethered to a wearable computer called the Lightpack.

From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

Oh, Uber. It's not often to hear your name in the news and have it mean something good. You're being sued, you're crashing, your driverless program is falling behind. But I have to hand it to you; when the world is crumbling around you, you continue to fight against it. You've even made it to Canada.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

It's the holiday season, and the tech industry is giving consumers several AR products and apps as gift-giving options.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

Transparent display maker Lumus has reached a deal to license its augmented reality optical engine models to Quanta Computers for mass production of displays for consumer smartglasses.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

Technology ages rapidly. We're conditioned to refresh our iPhones every one or two years, and why wouldn't we? New iPhones are fast, and our old ones inevitably slow down, sometimes to an unusable degree. However, it turns out, there's something we can do about that, and it doesn't involve buying a new iPhone at all.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.