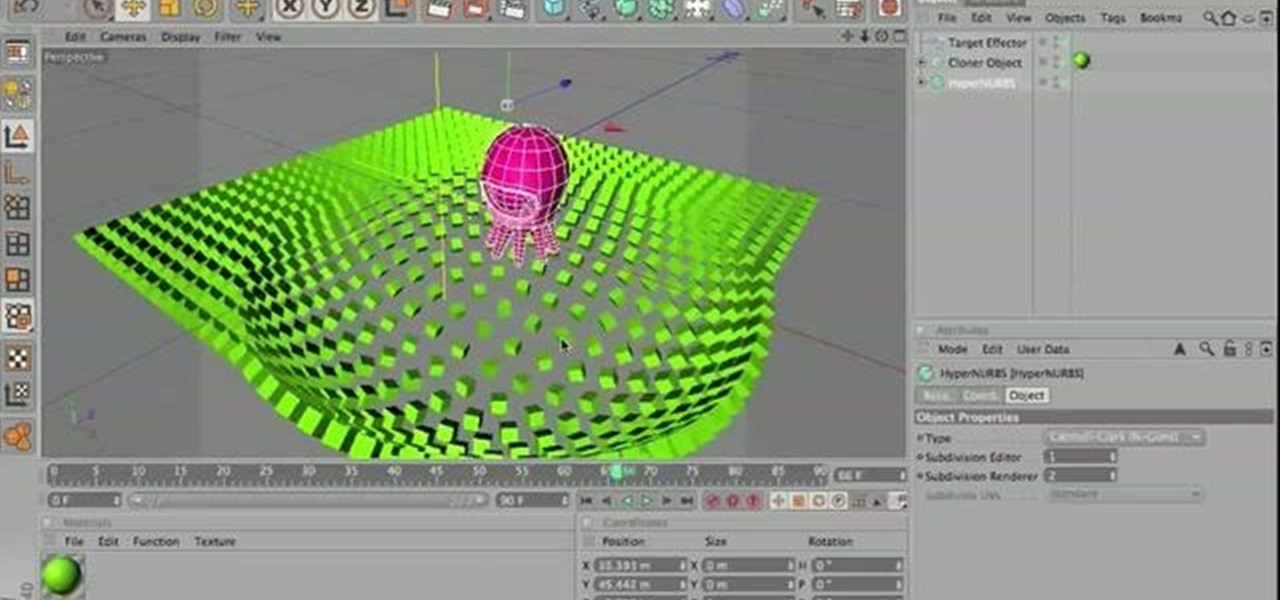
In this Cinema 4D tutorial, you'll see how to create a Target Effector MoGraph which is amazing. With only 4 simple steps, you can create a very special scene. Primitive Object, Cloner Object and Target Effector will be used in this tutorial. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get sta...

There is not better way to get in shape and target trouble zones than with the help of some experts in fitness and some simple workout equipment. In this how to video tutorial SELF Magazine shows you how to tone and sculpt your body with a simple beach ball. Tone difficult areas with tilt-a-whirls, dipsy dos, squeeze play, close reaches, reverse lunges, pendulums, hold your own and tummy toner exercises.
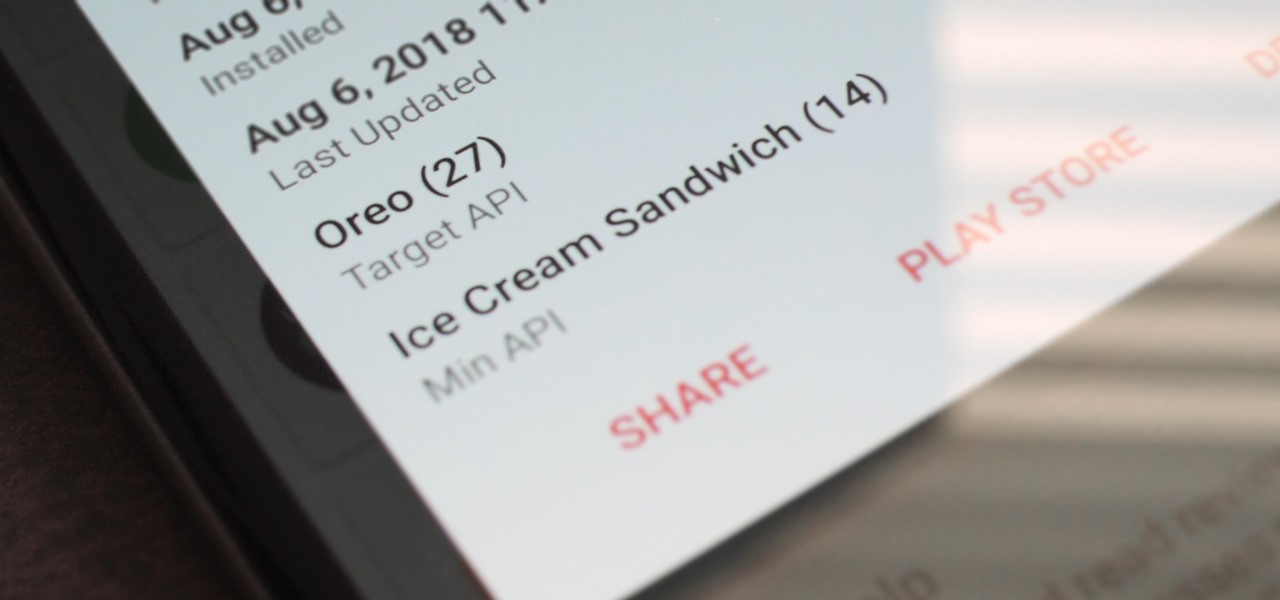
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.
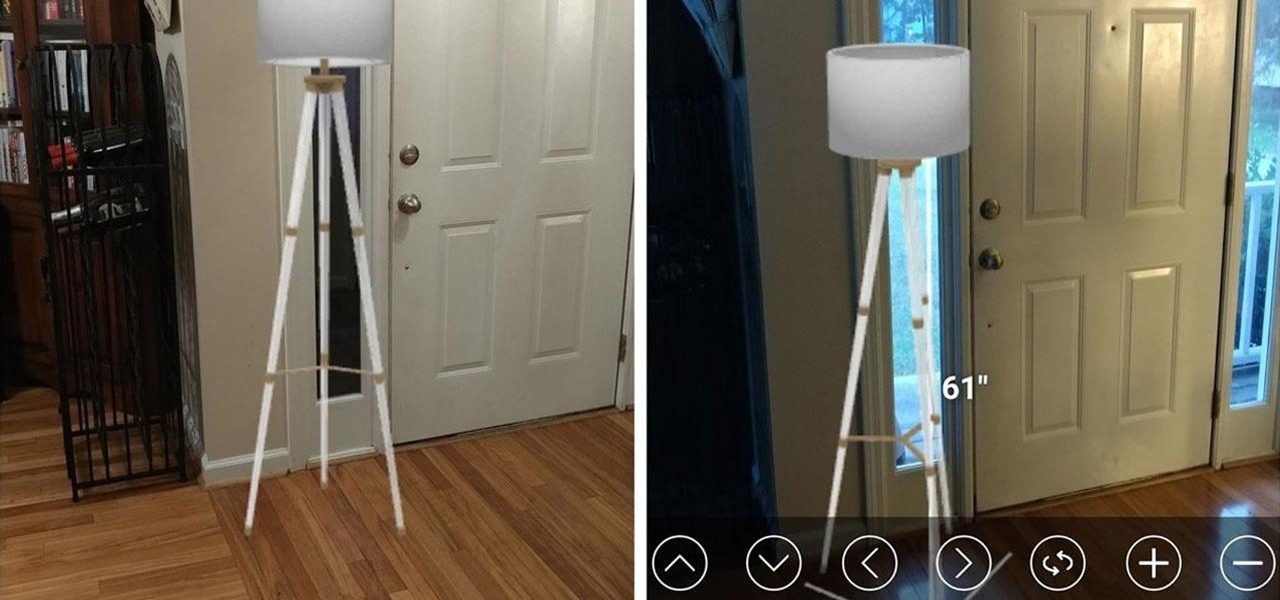
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

This clip demonstrates a simple Reformer-based Pilates exercise routine to target your legs. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates.

This clip offers a demonstration of a simple Reformer-based Pilates to target your flexor muscles. Whether you're toying with the idea of opening up your own Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

To do a hippie jump on a skateboard, first find a good hippie jump target. A good target is something that your board can easily fit under. Approach the target rolling at a comfortable speed. When you are near the target, jump straight up so your skateboard continues rolling under the target. You will then land on your skateboard on the other side of the target and roll away. Make sure that you don't jump forward because it will cause your skateboard to roll backwards and you will not be able...

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

The silent film era ended long before anyone had conceived of something like machinima, so your machinima movie had better have some talking! This movie will teach you how to use morph target in 3DS MAX to give your imported World of Warcraft characters facial expressions and animate their mouths to make them appear to be talking. You'll also learn how to make your model sneer, smile, and perform other facial actions.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

The Recon character class in Battlefield Bad Company 2: Vietnam is a thinly veiled sniper, and utilizing their target-spotting functionality is key to effective sniping in this game. This video is a complete guide to effective Recon play, teaching you about all your abilities, guns, and how you can spot targets to make yourself much more effective from much further away.

A lot of the available shooting benches on the market today are well-made, but it's really hard to find one that you're completely comfortable with. That's why it's best to make your own custom shooting bench, made especially for you, how you want it.

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...

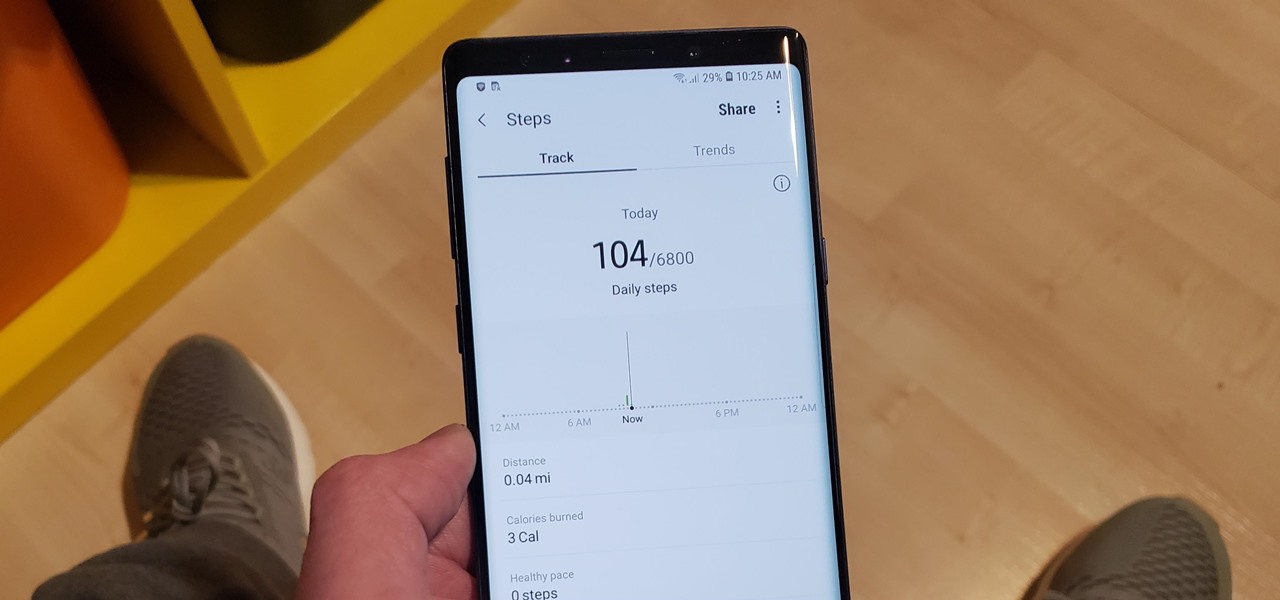
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Want to perform an unplugged version of Blink 182's "Easy Target"? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its chords. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Easy Target" on your own acoustic guitar, take a look!

Traveling often is super fun, but sitting through 13 hours on the flight from California to Bangkok is killer on your skin, especially since the airplane recycles air and therefore dries out your skin.

You must have a certain attitude to appreciate practical jokes and pranks. Your friends (or targets) may not appreciate pranks as much as you, especially messy ones. The messy pranks are the ones that are less likely to provide a laugh from your victims, at least not right away. This ketchup prank is one of those.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

In this Sports video tutorial you will learn how to take away your slice in golf. Pam explains the potential causes and cures for the shot that goes to the right. A lot of people take the club too early to the inside thereby taking all width and circling to the right side. When you take the club inside, you will have to compensate to get back to where you want to be. To correct this, you can do a simple drill. Place another ball one and a half to two feet behind the target ball. The goal is t...

This clip offers instructions on how to tone your shoulders with a simple Reformer-based Pilates exercise routine. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, g...

This video demonstrates a simple tower exercise that targets chest and arm muscles. With pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exercise video a ...

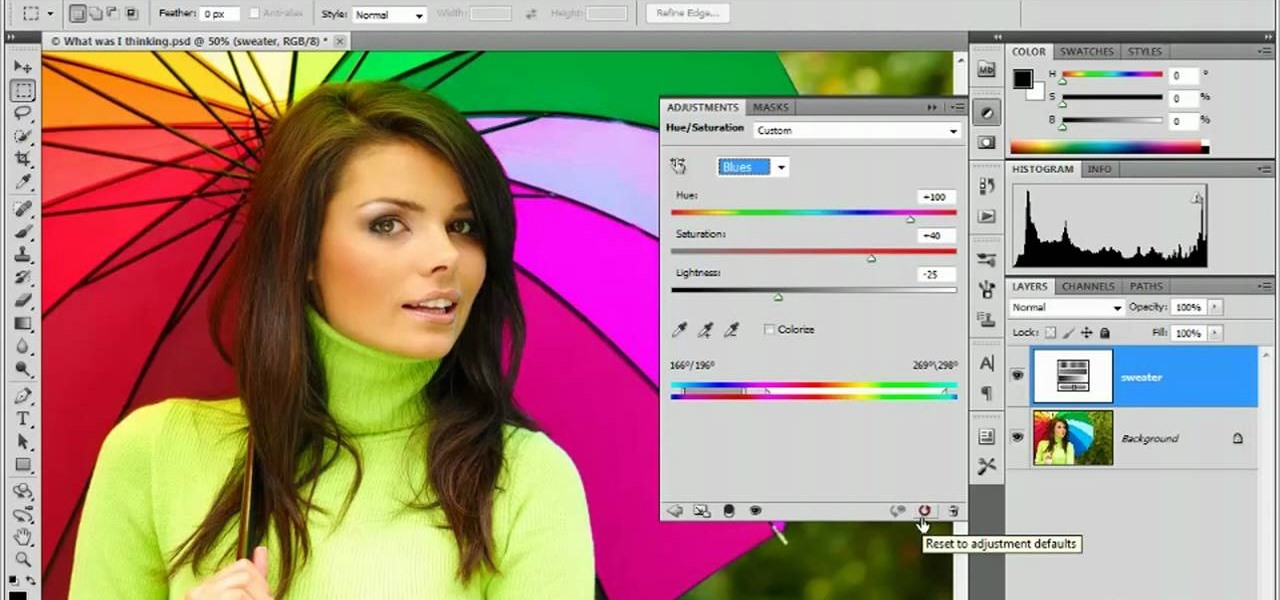
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.