Shopsmith Academy shows you how to prevent tear-out and practice good shop safety while routing. Apply this lesson to your next woodworking project. Watch this video for useful woodworking tips. Search Shopsmith Academy on WonderHowTo for more woodworking videos.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.
Learn some tips on setting up your drums and routing them, also we'll talk about some workflow tips and organization for creating hip hop music in Reason 3.

In this video, we learn how about routing FX using the StudioLive with Brandon Hays. To recall an effect, select the effect button and then page down to gt the list of effects for A and B. Once it's been selected, hit the recall button and then find the mono delay for the vocalist in B. Now, send the channels to these effects and add a snare drum to channel two. Then, add send different levels of drums to channels six and seven. You have sixteen channels to assign different effects to. As soo...

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

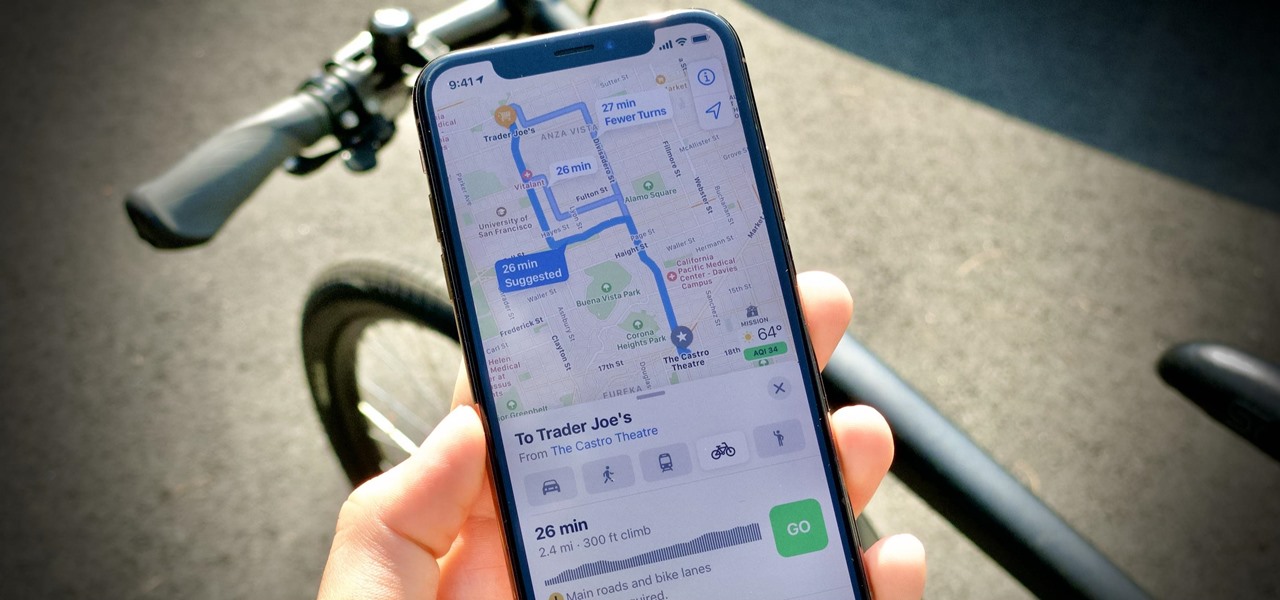
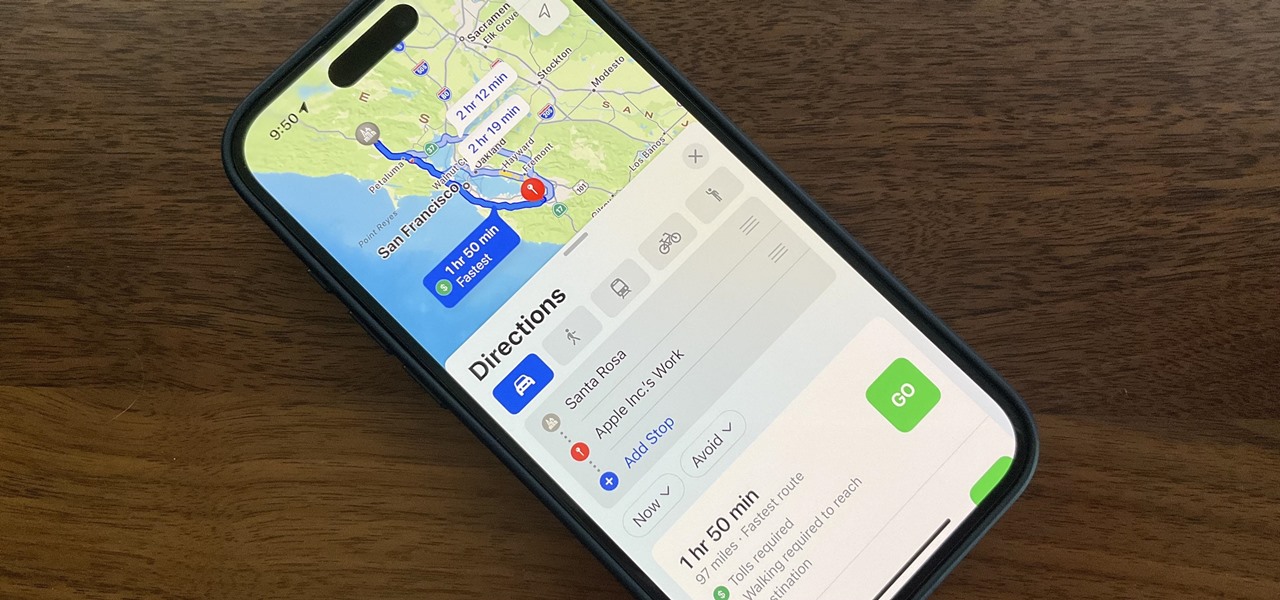
Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

If you're trying to get somewhere fast, taking a toll road or two can definitely help you do that, but at a cost. When you're not in any rush, that would-be toll money will work much better in your gas tank, especially if it's only minutes that are being shaved from your trip. With this in mind, Apple Maps has a simple way of avoiding tolls to save you money while navigating on your iPhone.

If you're looking to rout, or hollow, out a length of wood as part of a DIY project, you'll need a wood router. In this handy tutorial, Darren Baensch reviews the three basic principles while walking you through a cut. Watch this video and learn the basics of plunge routing. Use a plunge wood router.

Thor is the synth of choice for many Reason 4 users, including Dave from Boyinaband.com, the maker of this video. Herein he will teach you how to use some advanced features of Thor to create new and unconventional sounds. These features include the phase mod, wavetable, and FM Pair oscillators; comb filters; and the modulation bus routing section.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

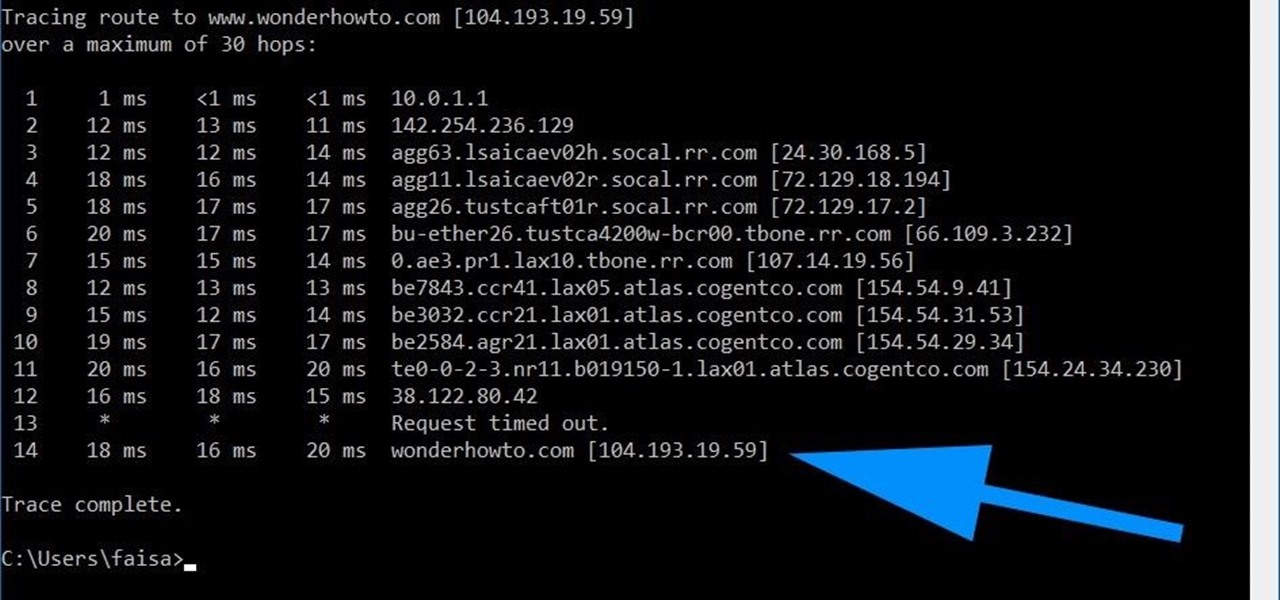
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

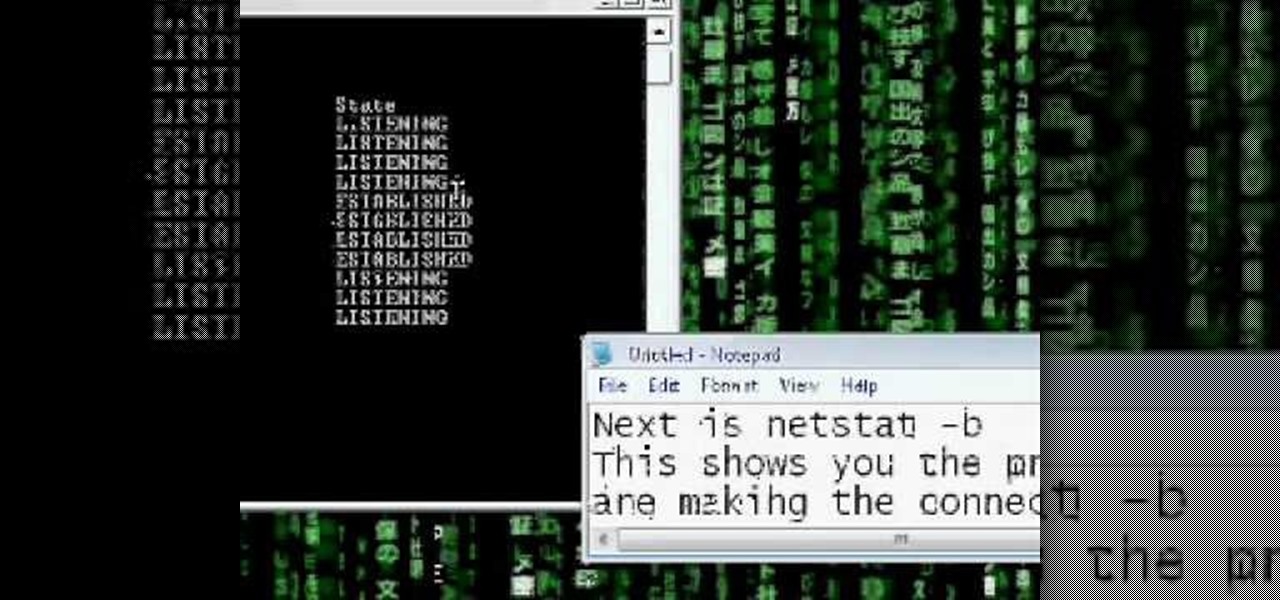
Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Covers convertible cable routing from the trunk for DICE BMW iPod & iPhone integration Kit in BMW 3 Series / M3 (E46).

Worried about your or someone you love's relationship with alcohol? Not all alcoholics fit the stereotype of the down-and-out drunk. Learn to recognize the warning signs in yourself or a loved one.

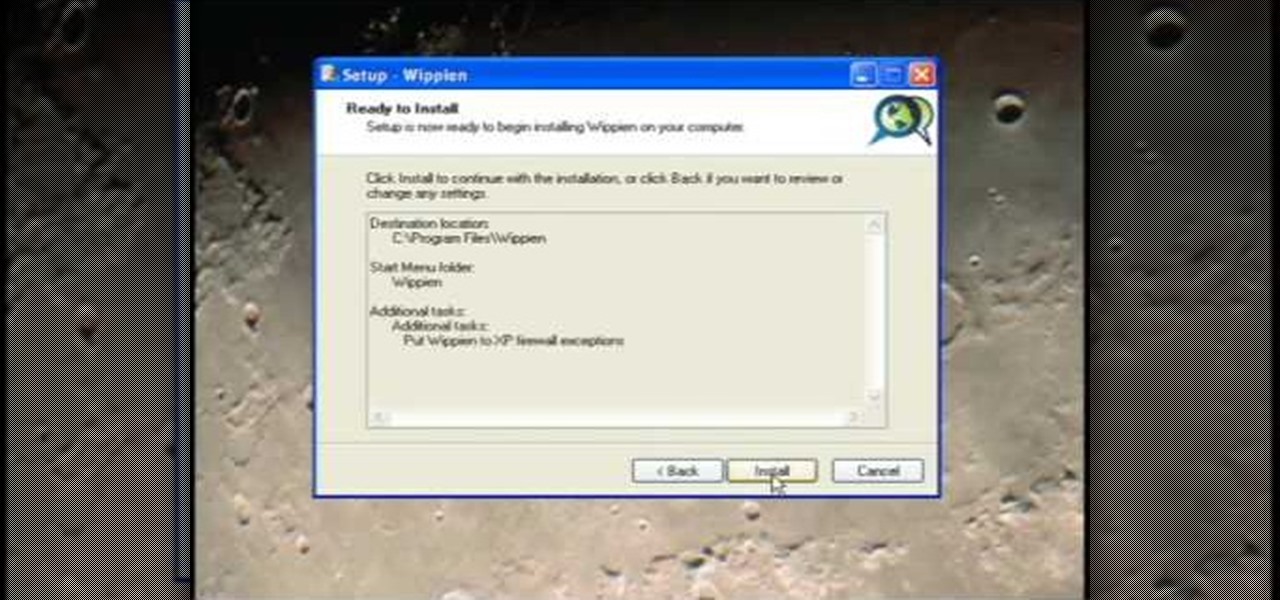
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

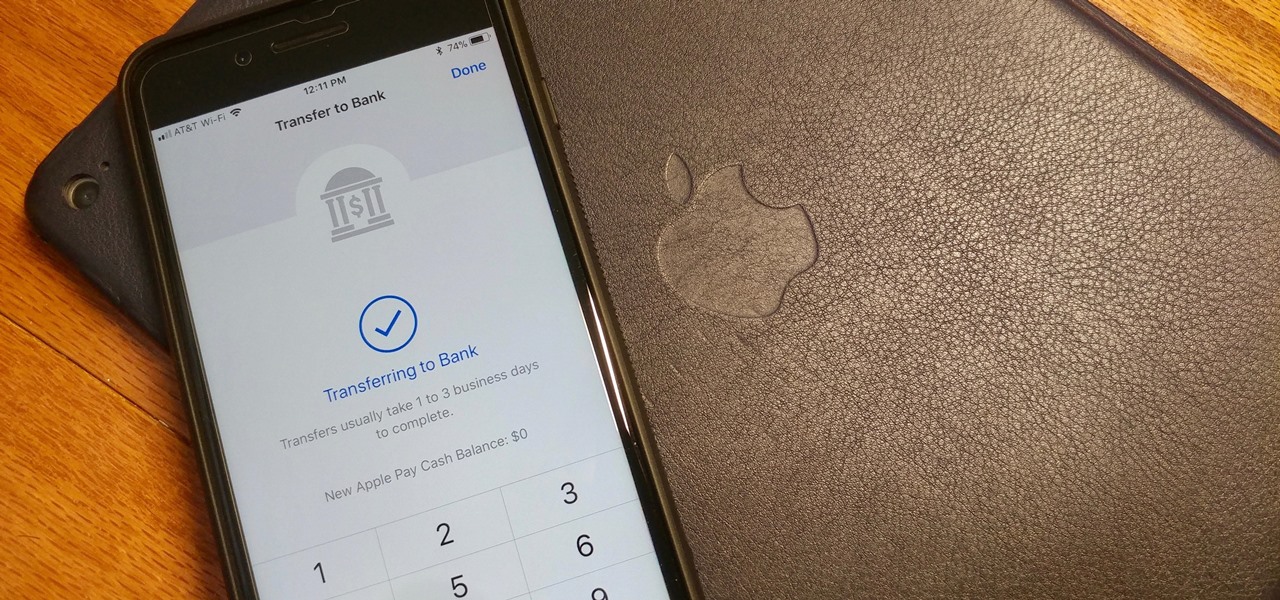
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money to your bank account in iOS 11.2.

By default, when you receive a FaceTime video call on your iPhone, the speakerphone kicks in immediately after answering unless you're wearing headphones. It's the exact opposite when it comes to FaceTime audio calls, but it's pretty easy to remedy if you'd rather have the speakerphone kick in instead of the built-in ear speaker.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If you've ever missed an important phone call because you're hands were too dirty to touch the screen, you won't have to worry much longer about it happening again. Apple is remedying this age-old problem on the iPhone with a hidden feature in iOS 11 that ensures you'll never miss another call again.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.

Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

AirPods not only let you listen to music on your iPhone — they let you quickly stop listening to your iPhone's audio by pulling out a single AirPod to pause. If, however, you'd rather have music, audiobooks, podcasts, and other audio files continue playing when you pull out one AirPod — or both AirPods — one settings tweak can get the job done.

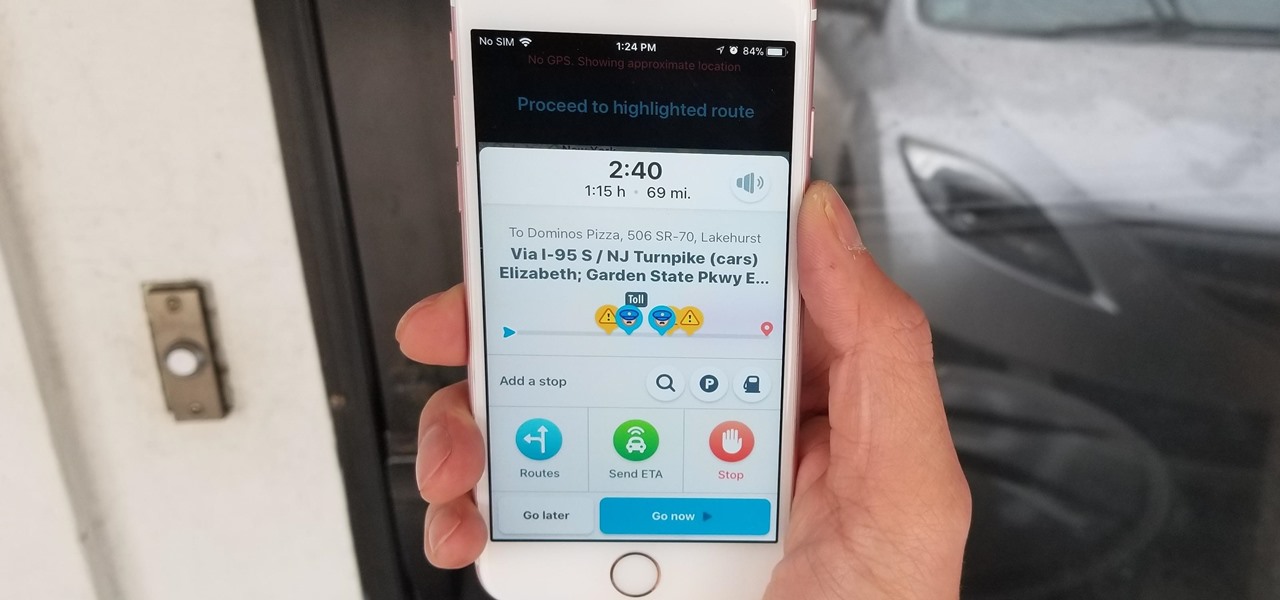
Discovering you're on a route filled with tolls while you're already on the road, with no cash on hand, is never a pleasant surprise. Fortunately, Waze has an incredibly simple solution to nip this potential headache in the bud and save you money while navigating.

When you make or receive a call on your iPhone, you're forced to use the built-in ear receiver at the top of the phone to hear anything—unless you're already connected to a Bluetooth device. If you don't have Bluetooth in your car, or prefer to just use the speaker instead, having to manually switch to speaker mode can get annoying real fast.

While Apple Maps didn't receive as huge of an update on iOS 17 as other apps such as Safari, Camera, Photos, Notes, Weather, and Messages, there are still some very important new features and changes you need to know about.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

At $349 off contract, the Nexus 5 has always been one of the best bang-for-your-buck smartphones on the market. In order to keep the price that low, however, Google had to pass up on some of the minor features that other flagship phones offer.

With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker.