Going to be a nurse? Then one very important part of your daily routine will involve doing bedside clinical assessments. This how-to video shows you the the technique for completing a bedside assessment. Follow along as Loretta Thrape, NP,MSN, BSN, shows you the proper guidelines for doing this bedside assessment of your patients.

Going to be a obstetrics nurse? Then here is one thing you should know how to do. Follow along with this nursing how-to video to learn how to do a fundus assessment. Watch, learn and practice changing doing the fundus assessment on a patient with a c-section. Remember to explain procedures to the patient before you begin.

Going to be a nurse? Then here is one thing you should know how to do. Follow along with this nursing how-to video to learn how to do a postpartum and newborn assessment. Watch, learn and practice during lab practice. Remember to explain procedures to patient and have all packages open before you begin. This OB postpartum and newborn assessment emphasizes on deep breathing exercises.
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

This video will teach and demonstrate the thyroid status assessment and thyroid gland examination in a patient. As a doctor, you will, at some point in your career, need to examine the thyroid gland in a patient's neck, and some other parts of the body which are effected by the thyroid.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

The key to a great essay or dissertation is a strong thesis. In this two part tutorial from teacher Jennifer Mensink, learn exactly what a thesis is, why it is important and how to craft the perfect one. This video lesson will cover everything including an anticipation set, input and an assessment. Jennifer teaches as though you are her only student, and you will love listening to her step by step breakdown. So, get ready for finals with this refresher course on thesis statements.

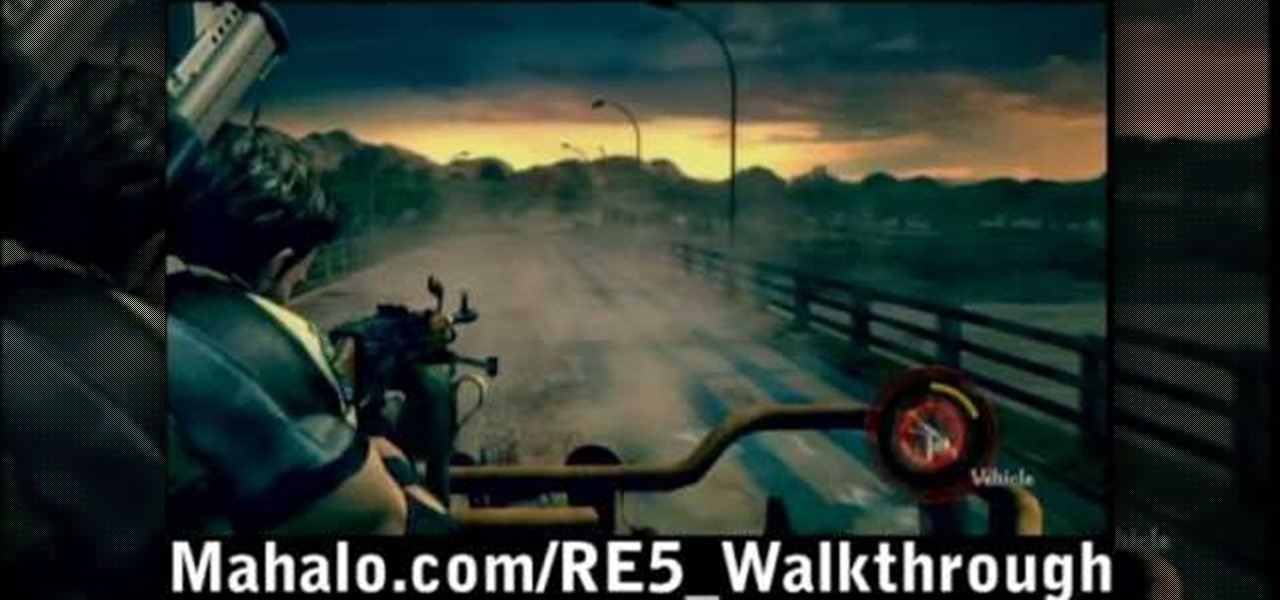
Check out this RESIDENT EVIL 5 Chapter 2: Gigante walkthrough from Machinima.com The behemoth from RE4 returns with some new tricks up his sleeve.

Check out this Mahalo video walkthrough of Savannah in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

In this Autos, Motorcycles & Planes video tutorial you will learn how to inspect hail weather car damage. Paint loss dent repair is the most common method used for this purpose. The first thing to do is to count the number of dents based on half dollar, quarter, dime and nickel size. All you need to do is to place the coins over the dents and count how many dents are there of various sizes. Once you have this information, you are on your way to handle the hail loss assessment correctly. If th...

For most people who deal with seasonal cold weather, it makes sense to prepare one's car brakes/ABS for the winter weather. Ed Kriston from AAA Mid-Atlantic discusses typical brakes and anti-lock brakes. Kriston goes over the general makeup of how brakes work and what components make up the brake system. He goes over how to tell if there is sufficient brake pad to get you through the winter. To make sure your car brakes or anti-lock brakes are prepared for the cold weather, follow the steps i...

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Zika is a threat to unborn babies — the virus can cause neurological damage if it infects a mother during pregnancy. But as with many things, our solutions to the problem aren't always all that much better than the problem itself.

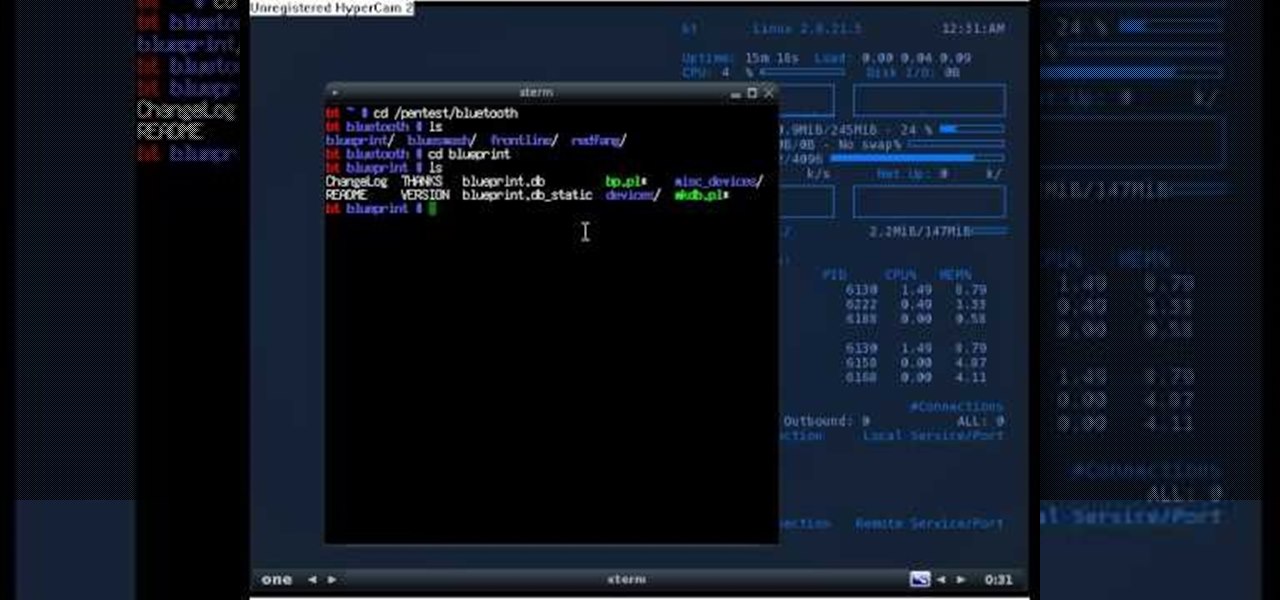
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

This video tells us about annotated bibliography, what it is and its elements. Annotated bibliography is basically an evaluation or an assessment of the article you have read. To make an annotated bibliography there are four steps. The first one is to provide the source, the author, where it comes from and the title. The second step is to summarize your reading. The third step is to show that you know what type of article it is, and that means that you have to assess your resource. The fourth...

Beat the Level 2-3 Boss in Resident Evil 5 via this walkthrough and gameplay. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

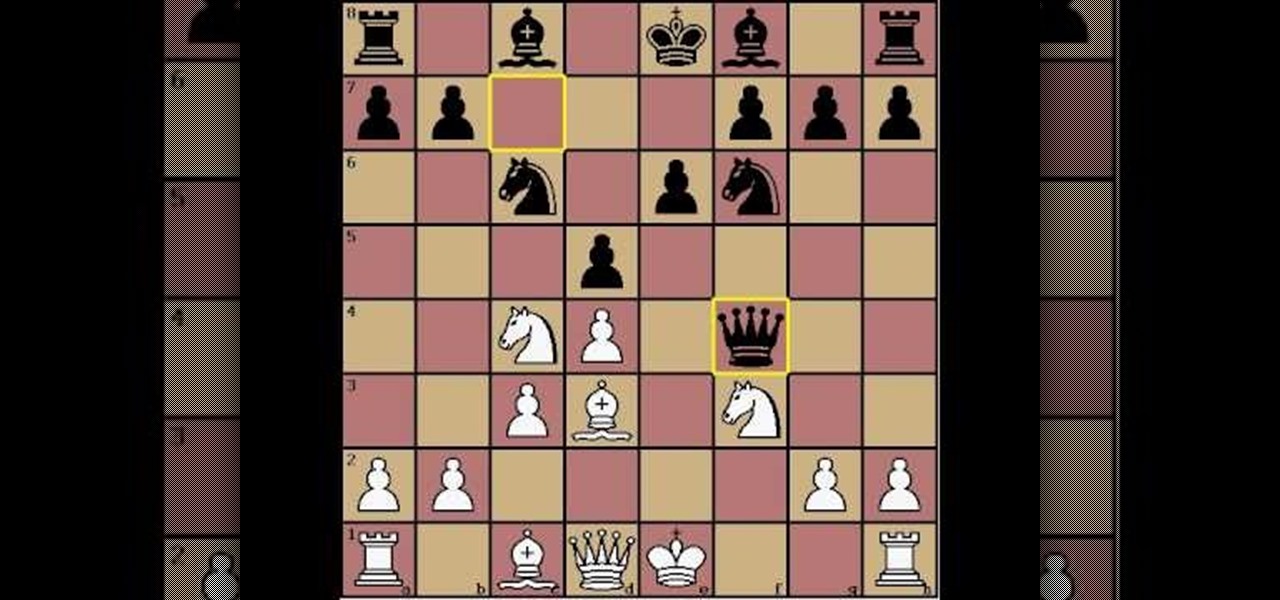
This video features 6...Qc7 in the mainline of the Stonewall, a good move since after the obvious 7.Ngf3, White turns out worse in all lines. Matt suggests an alternate development of pieces including Nh3 and Qf3.

Every physician, medical student or resident, from emergency room doctors and nurses to anesthesiologists, need to know of the most fundamental skill sets: airway assessment and management. But before one can be proficient with this skill set, you need to know the tools of the trade.

ER showed the world what goes on inside the emergency room, and in every episode, we experienced a common but very important procedure— intubation. But ER never made it seems easy; it showed just how hard it is for medical students to successfully intubate a patient due to fear and naivety. And for real-life doctors and medical practitioners, learning the art of airway management is just as difficult.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Check out this 2 part walkthrough of RE 5 Chapter 2-3 Savanna. This Resident Evil 5 Walkthrough is being played on Veterans Difficulty in Co-Op mode with Chris Redfield being played by Reule and Sheva Alomar being played by RavenVanHelsing.

Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Check out this walkthrough of Residential Evil 5, Chapter 6-2: Main Deck. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

This video explains how to answer one of the five toughest job interview questions, this one being "what are your greatest weaknesses?" In it John Heaney of "The Job Shopper" explains that the most important thing about this question is to realize that answering in a way that really paints a negative picture of yourself will negatively impact your potential employment.

Check out this 4 part walkthrough of Resident Evil 5, Chapter 5-2: Experimental Facility. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Check out this walkthrough of Resident Evil 5, Chapter 5-3: Uroboros Research Facility. This is a 5 part video series.

Check out this walkthrough Resident Evil 5, Chapter 6-1: Ship Deck. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

"Buy low and sell high" is great advice, but how do you accomplish it? While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

A new telemedicine application for the Microsoft HoloLens is promising paramedics and EMTs a new tool for diagnosis and treatment of patients in the field.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.