Check out this instructional Russian language video to learn Russian as Russians speak it. This is Theme 10, Lesson 4 in the series. Practice your Russian listening skills by listening to the dialogue presented in this language video. Learn words related to your health with a doctor.

Learn the basics of airplane landings and how Newton's laws of motion apply. NASA -- the National Aeronautics and Space Administration, gives this quick, informative video on Newton's laws pertaining to aircraft landings, specifically the approach. The powerhouse of space exploration explains all.

The powerhouse of space exploration, NASA (National Aeronautics and Space Administration), sheds light on Newton's laws of motion as pertaining to drag force on aircrafts. This is a great source for any aeronautics major. The infamous government agency breaks drag down for you.

This is a special four-part series on the human head, neck and skull. Medical students can greatly benefit from watch this anatomy video series. Dr. Gita Sinha "dissects" all of the information pertaining to the head and neck. Dr. Sinha is Assistant Professor for the Department of Anatomy & Neurobiology at Dalhouse University. Each of these videos cover a different topic:

Check out this instructional Russian language video to learn Russian as Russians speak it. This is Theme 8, Lesson 2 in the series. Practice your Russian listening skills by listening to the dialogue presented in this language video. Learn travel related words in Russian.
Check out this Korean language tutorial video to practice your vocabulary with words pertaining to the kitchen. This instructional video is a part of the picture/vocabulary series to help learners practice their Korean language skills. This video is a great lesson for advanced learners who want to listen to native speakers, but it is also helpful for advanced beginners to build up their vocabulary skills. Watch as this instructional Korean language video provides pictures supplemented by voic...

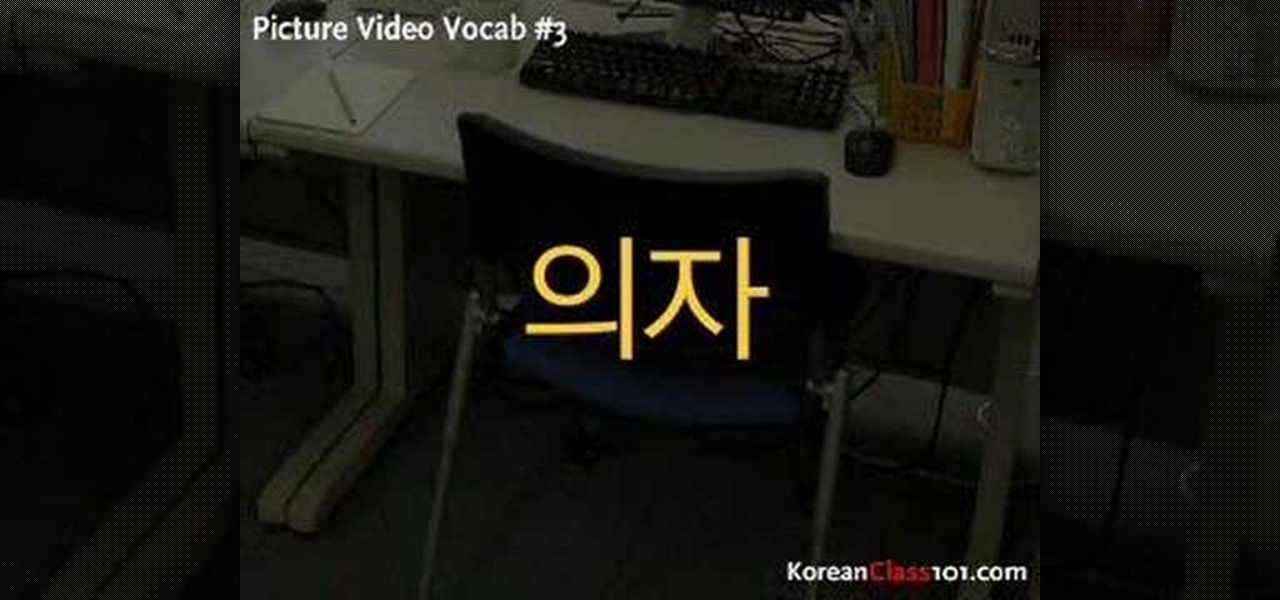
Do you work in an office? Learn Korean words pertaining an office in Korea! Check out this Korean language tutorial that shows you how to pronounce office related vocabulary words. This video provides another great way to learn Korean, and continues with the Picture/Video Vocab series to go over some Korean vocabulary in the office place! Offices in Korea are very similar to those found elsewhere in the world. So listen in to today's Picture Video Vocab Lesson, and learn some Korean words tha...

Kids love sports drinks, but are they healthy for them? This video answers that question, and dissects all of the information pertaining to the diet, nutrition and metabolism of a child playing sports. Healthy eating is important for any sports player, but there are some special considerations for young children. Variety is important, but you need about 40 different nutrients to keep the kid playing well. And believe it or not, chocolate milk is actually one of the best recovery foods.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

If you watched a YouTube video on your Android device today, you may may noticed something just a little different. If you haven't, go check out the app in your drawer or homepage. Google today pushed out an update to their YouTube app, but by all accounts, it was never meant to hit the public. This is labeled a dogfood build, which is a term used to describe products going through in-house testing, in effect "eating their own dogfood".

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

Apple just pushed out iOS 11.2.5 beta 7 today for iPad, iPhone, and iPod touch to both developers and public beta testers. On Wednesday, Jan. 17, beta 6 was released, and there were two betas the previous week. With Apple promising a patch for "ChaiOS" next week for everyone, it's like iOS 11.2.5 will be that update.

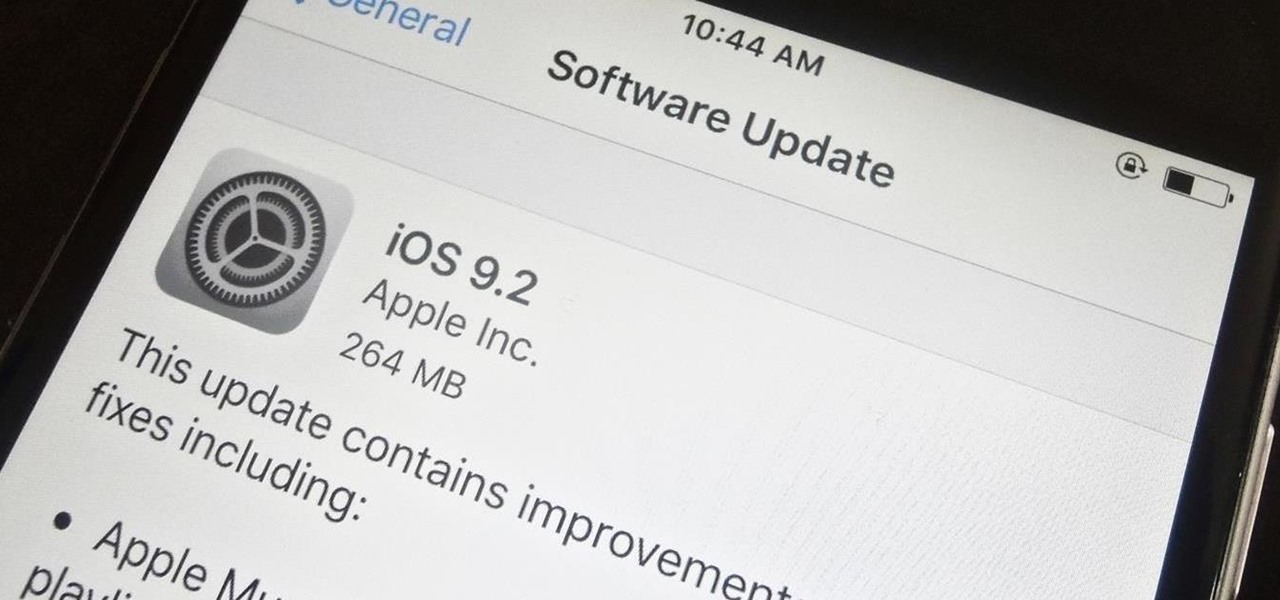
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

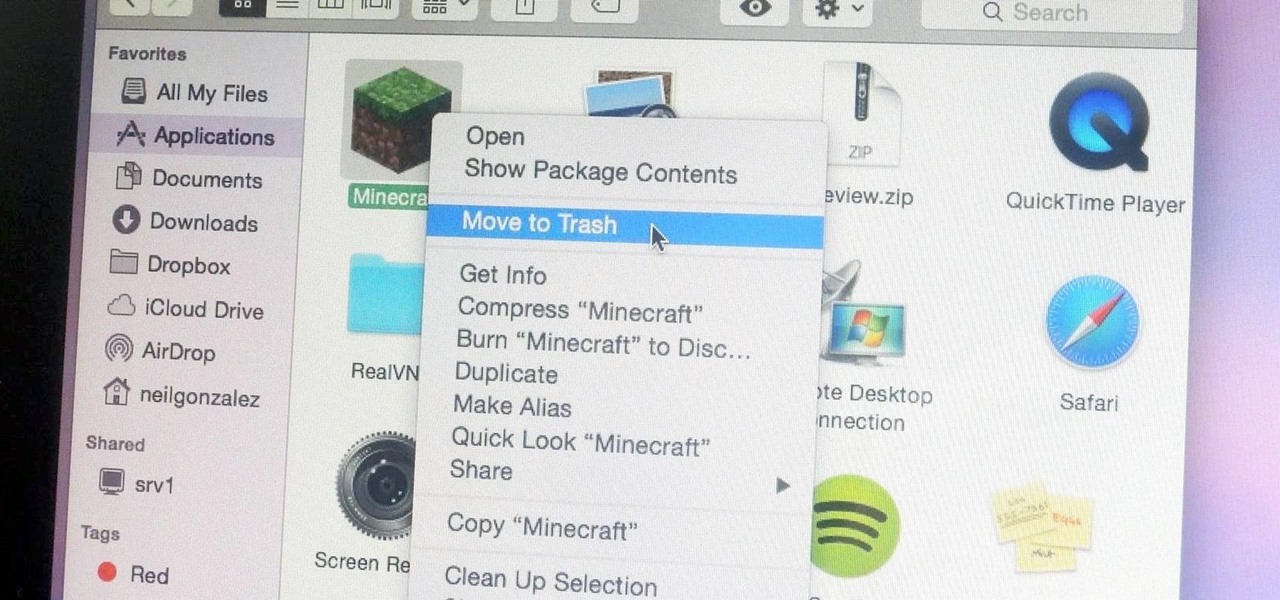
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

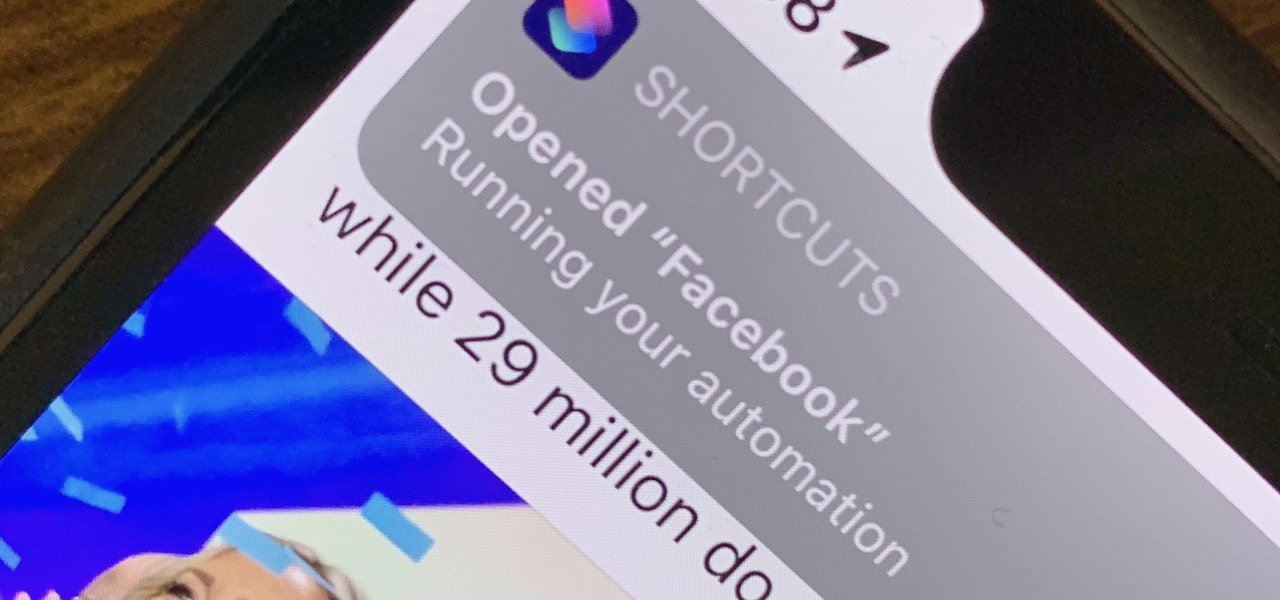
There are a lot of cool shortcuts you could run on your iPhone, but in iOS 13 and iOS 14, you'll likely see a notification any time you try to run an automation. Shortcuts should feel seamless when their actions are performed, and getting a banner alert each time one initializes takes away the seamlessness of it all. But there is a way to block them.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

In this video you will learn how to say words pertaining to water and health in Mandarin Chinese and then see how they are used in conversation.