Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

In this video we will show you how to replace the coolant overflow tank on your 93-98 Volkswagen Jetta.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.
On this video I will demonstrate a simple concept of stack base overflows. This is the first part of my exploit development tutorials and after that I will demonstrate seh buffer overflow, ROP/DEP/ASLR, spraying the heap, search for bugs/think different etc.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

This is an awesome joke you can do on an unsuspecting friend or coworker. Learn how to pull a soda prank using Mentos ice cubes. Watch this practical joke how-to video to find out how to carry out the soda prank on someone using a Mentos frozen ice cube and soda. Everyone loves a cold cup of soda, so they won't be able to resist some frozen ice cubes rigged with Mentos inside. Use this as inspiration for one of your April Fools Day pranks!

Many people are intimidated by auto repair, but this video will show you how to replace the radiator overflow bottle on a 1998-2004 Dodge Intrepid. If the coolant tank in your car need replacing you can follow the simple steps shown in this video and do the repair yourself.

In this video tutorial, viewers learn how to check the engine fluids of a car. Begin by checking the engine oil. Begin by finding the engine oil dipstick. Then wipe it down and return the dipstick. Recheck the dipstick and oil level. Now check the automatic transmission fluid. Find the transmission fluid dipstick. Then wipe it down and return the dipstick. Recheck the dipstick and oil level. Only check automatic transmission and not manual. Then check any other important fluids in the engine....

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

The factorial of a number n can be defined as the product of all positive integers that are greater than 0 but less than or equal to n.

!!! READ THIS FIRST !!! - 4 april 2009 -

This video tutorial is in the Home & Garden category which will show you how to save money & water with your toilet flush. The first step is to turn the water off. Then remove the lid of the tank, disconnect the bowl refill supply and make sure that the overflow pipe is open. The next step is to take the new sink, attach it to the water supply point, place the drain in the overflow pipe and position the sink over the flush tank. The modification is done. Now turn on the water supply and your ...

Step1. First of all you need to remove all the borders. Scroll up and then select all the text lines that have 'border' mentioned and then delete them.

Jennifer DiDonato shows us how to make low sugar cranberry sauce in this tutorial. First, grab 1 bag of cranberries and place them into a saucepan with 1 cup of water. Let this simmer for about 7 minutes and now take 1 orange and peel the rind off of it. Now, throw the rind into the saucepan and pour the orange juice from the orange in as well. The last ingredient to add is 1/2 cup Splenda and mix together in the saucepan. Let this simmer for another 7 minutes, watching it to make sure it doe...

To decorate a fall flower centerpiece for your home, create a table centerpiece. Get some dry flowers with attractive colors of your choice. Take a metallic pot for centerpiece. Place a Styrofoam ring in the bottom of pot or vase. Carefully insert stems of dried flowers into the foam. The interior design technique is to be perfect to fall, so that it looks natural. Make sure to have the tallest flower at the center of the pot. Work from the center outwards applying more flowers and stems. Mak...

Here is the famous cold soup of Spain and the solution for that overflow of tomatoes in your garden. Watch this how to video as Chef Jim shows you how to make a healthy chunky gazpacho. Gather some onions, garlic, olive oil, red wine vinegar, tomatoes, bell peppers, cilantro, cucumbers and tomato paste for this delicious gazpacho recipe.

Ever wondered how to make slime? Now you can learn! Make slime just like they use on Nickelodeon for Halloween, pranks, or just to play with! So gather up your ingredients and get cookin'!

http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Check out this video to see our Fantastic Foamy Fountain in action. The experiment uses Hydrogen peroxide and dry yeast. Hydrogen peroxide is similar to water but has an extra oxygen atom. This makes it more dangerous, and only adults should handle the hydrogen peroxide.

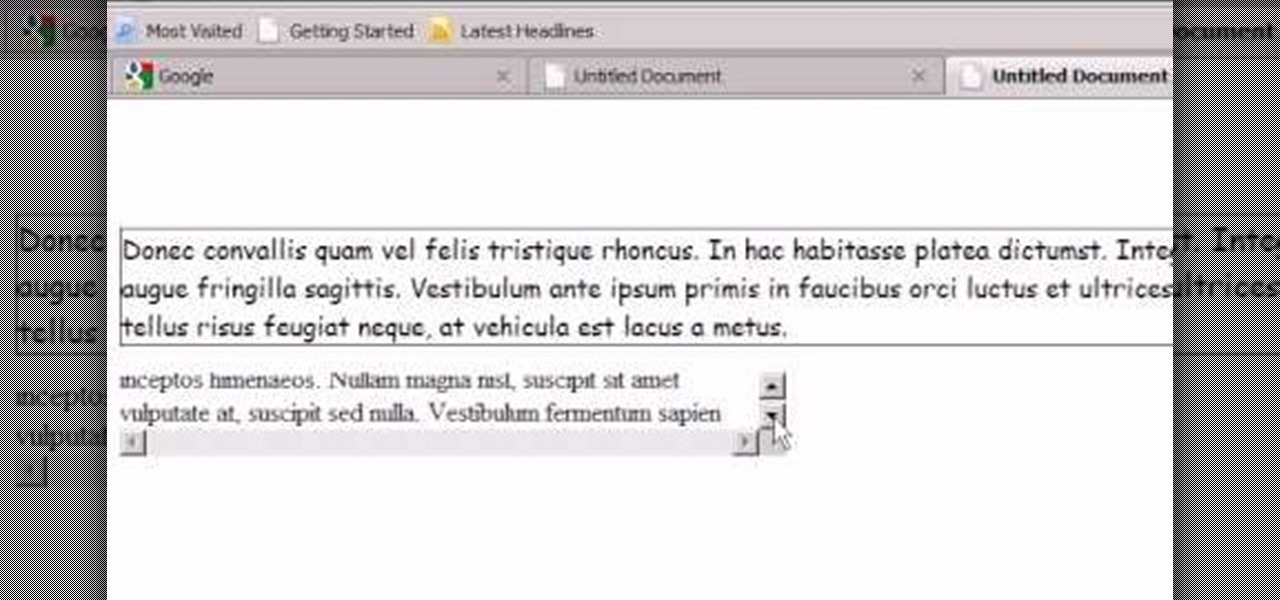
Open up dreamveiwer and click HTML on creat new. If the new page opens then go to design view and then go to insert and then layout object and then diff tag in that then click ok for that. There we have to create a scrollbar content. Then we have to right click there and go to css styles and then go to new. There go for selector type and click class and then name it as you want. Here he just named it as scrolldivstyle then go to go define in and take this document only and then click. Next yo...

Scam School presents four silly beer gags in this how-to video.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible.

Ever since Android 3.0 Honeycomb, Google has been trying to push phone manufacturers to do away with physical menu buttons. Samsung has been one of the lone holdouts, retaining the menu key up until the Galaxy S5, where they finally replaced it with a "recent apps" multitasking button.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

As crazy as it sounds, there are times when bottles of wine go unfinished. I love a glass or three of vino, but am often guilty of not finishing the bottle. Sometimes I don't have the time to finish it, and other times I like it so much that I open bottle number two and can't finish that.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

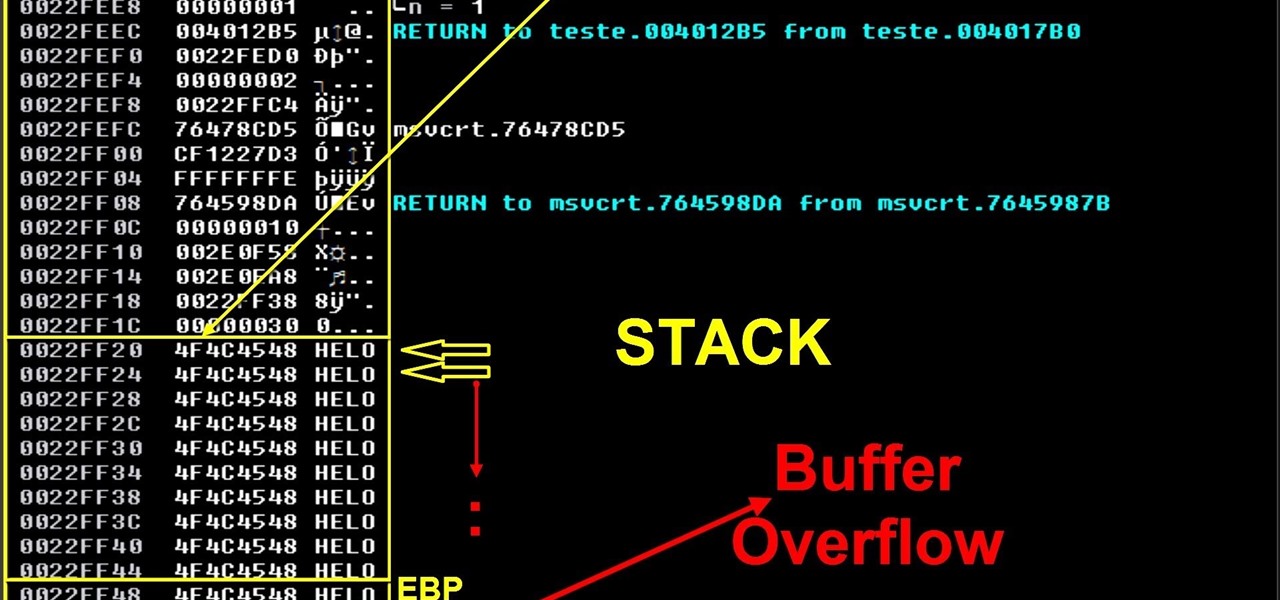
Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

YouTube Music just refreshed the user interface for playlists, seemingly taking away the ability to shuffle the songs in your playlists. While the update has been rolling out for months, you might just be getting the updated look on your smartphone, and there's no giant "Shuffle" button like there was before. But that doesn't mean there's no more shuffling.

Getting gum in your hair is a huge bummer; its an icky sticky mess to clean. Luckily, the days of cutting the gum out of your hair and ruining your style are behind you! This tutorial will show you how to get that gross wad out with a few products found in your kitchen.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.