Learn how to strike your attacker when facing a hand gun attack. This is step three in surviving a hand gun attack, following how not to get shot, and how to gain control of the weapon. Learn how to get inside the gun's danger circle using different strikes and stay in there. Also learn what to do against a two handed gun grip.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

This video details how to survive a knife threat from behind. When threatened from behind with a knife, do not attempt to move the body first, this will result in the attacker maintaining the capability to thrust the knife into the body. When threatened, place arms out and low in a submissive position, this is to be followed by moving the left arm backward in a sweeping motion to push aside the arm which is holding the knife. Once the arm is moved, turn the body and bring the elbow up into an...

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Ideal garage doors have four things in common. They're beautiful, durable, easy to maintain and well insulated. To discover how to find your ideal garage door host Meghan Carter visited Clopay to get the insiders tips for selecting the best type of garage door for your home.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

Ever wanted to know how to disable an attacker? The trick to getting away from an assailant – even one who's bigger and stronger than you are – is to hit 'em where it hurts.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

In order to play the game Risk, begin by setting up. Name a banker. Players choose a color. The number of players determines the number of armies. Remove the jokers from the country card packs. Shuffle the cards. Deal them face down. Players may not get an equal number.

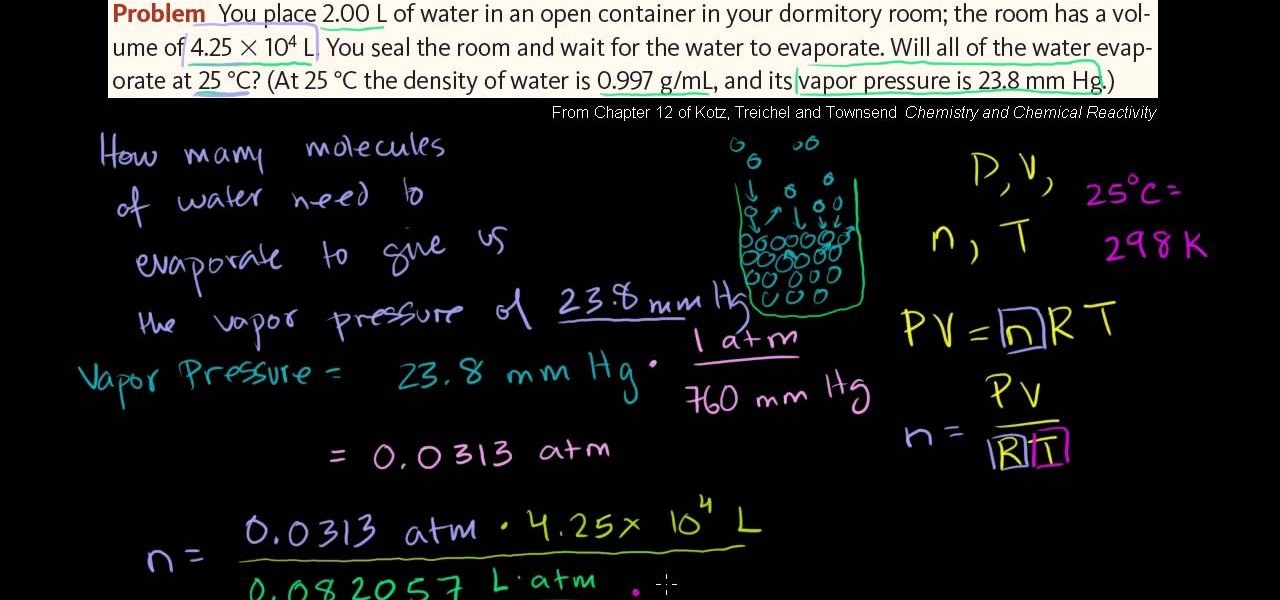
In this free video chemistry lesson from Salman Khan, we learn about vapor pressure and the ideal gas law. Whether you need help studying for that next big test or could just use a hand finishing your homework, you're sure to be well served by this video lesson. For all of the details, take a look.

An ideal favor for parties or showers. Layers of colorful sea salt in a plastic champagne glass topped off with a layer of soap. A few sprinkles of colored salt and a bath oil bead add the final finishing touches. An ideal favor for baby or wedding showers. An easy soap making craft for kids.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

In this tutorial, we will teach you how to defend yourself against an attacker with a knife. It's the best MMA for self-defense, especially for teenagers.

Learn some other tackle technique for players defending around the fringes. From a low position he's looking to get him off his feet. Attacker must stay as close to the ball as possible. The defender is looking to get his weight on top of the attacker.

4v3 Moving Defenders drill is a great drill to get defenders and attackers on their toes for Australian rugby. It is important to match up fast on this drill as offense / attackers strike quick and defense doesn't want to be caught on their heels.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

This video shows you how to tune the ACME attacker 1/8th scale nitro engine buggy. Use the high end valve and the idle speed screw as show in the film. Turn the engine and get it to the operating temperature and drive round to the see how the car performs. If the acceleration is sluggish then the low end valve should be adjusted. If the engine is having too much RPM then the idle speed should be reduced using the idle speed screw. If the engine bogs down and makes noise on full throttle and i...

The low price of speakers and MP3 players today make them ideal for adding a bit of sound to different items, and this tip from CNET reveals a few ideas. Add an MP3 player and a pair of speakers to a decoration, for example.

The low system requirements of Minecraft make it ideal for playing on an Android smartphone. If you're looking to find out how to download, install, and play Minedroid, a version of Minecraft designed for your Android phone, take a look at this walkthrough and check out the download options below.

Check out this video for creating a one piece mold using a repro laminating system. This is a professional video not for beginners. The repro laminating system is ideal for working on medium-sized projects, this process is easier, faster, and more economical than the epoxy laminating system. This process can be used in automotive, mechanical, fine art and film special effects uses.

Check out this video to learn how to make a professional epoxy fiberglass layup and epoxy laminating systems. This process is ideal for working on larger projects, a typical 'fiberglass layup' is a popular process for those who need a large, strong, and lightweight tool.This process can be used in automotive, mechanical, fine art and film special effects uses.

Check out this video for how to create simple one piece silicone rubber molds. This technique is ideal for smaller projects (less than 12" x 12"), this is the easiest process for creating parts, patterns, tools, & molds. We demonstrate creating a silicone rubber mold and then the casting of parts with Repro, epoxy casting resins and polyurethane elastomers. This process can be used in automotive, mechanical, fine art and film special effects uses.

Katherine and Kimberly Corp show you how to do a thirty minute (30 min) pilates workout to tone your abs, strengthen your core, and improve spinal flexibility. This is ideal for beginners, and advanced practitioners looking for a challenge.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

This video demonstrates some advantages and limitations of sticks when using it as a weapon and when faced with an attacker with a stick.

Kelly Campbell explains the disarm while doing gun from behind defense. This time when an attacker is pushing you forward.hing gun from behind at a distance defense. Krav Maga is the same brand of self defense used by Matt Damon in the Jason Bourne movies.

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.