In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

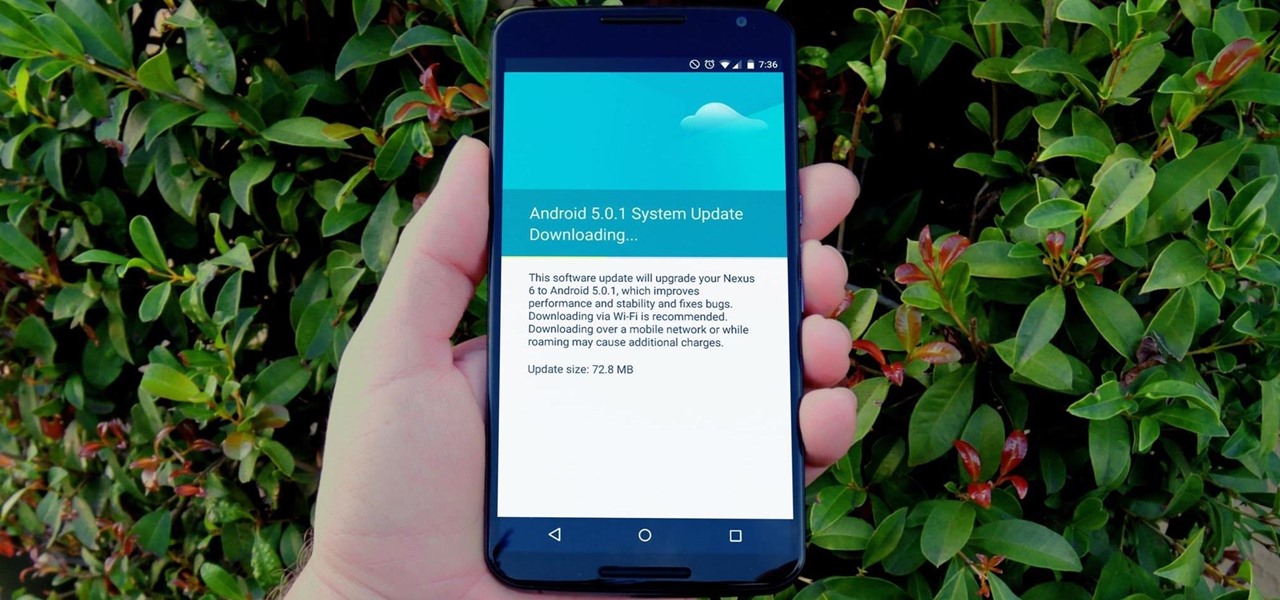
One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

This tutorial series shows you how to put up an Adobe Air Flex 3 Encryption System. One of the weak points of Adobe AIR and Flex is there is no encryption system built in, making your data and applications vulnerable. But that's ok, because this tutorial will show you how to remedy the problem by adding an AES encryption system.

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

Do you worry that if your PC is stolen someone can copy all of your data? Then you should encrypt your hard drive and removable USB drives too. In this video tutorial, you'll see how Windows 7 has beefed up Bitlocker, its built-in encryption program, and learn how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just under two minutes of your time. For more information, including complete, step-by-step ...

BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands.

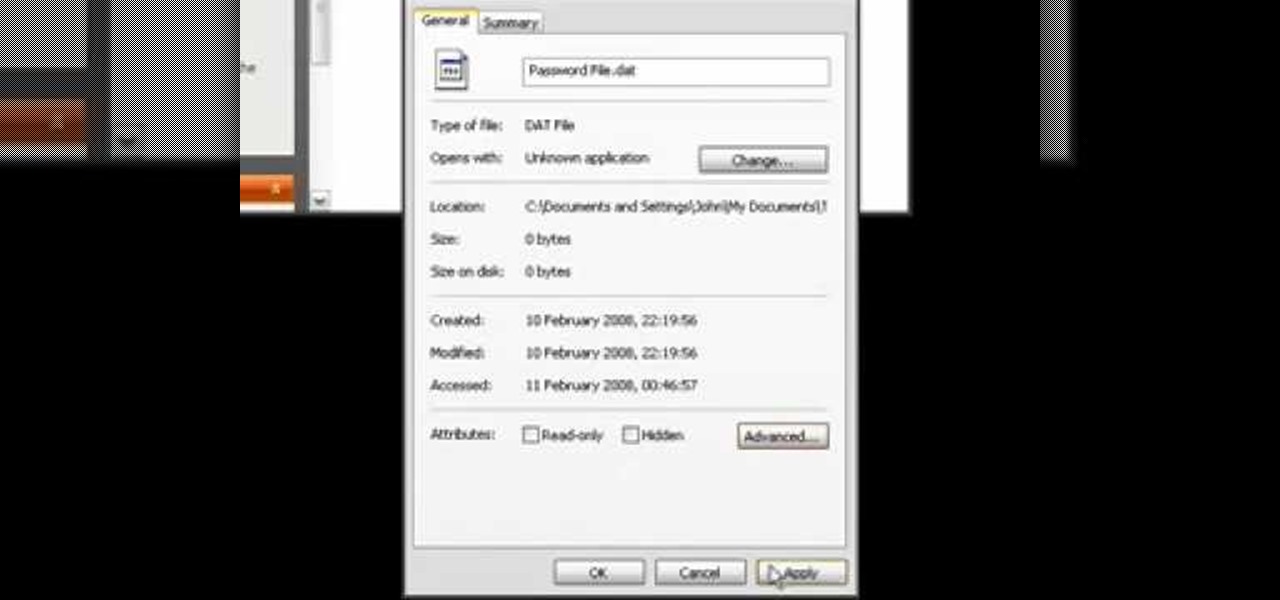
If you have files on your PC that you don't want other window's accounts to be able to access, you can encrypt them. Right click the file that you want to encrypt and select properties from the drop down menu. Once the properties page comes up, choose advanced. Now choose Encrypt contents to secure data and click ok. Now you click on apply. Select encrypt the file only and click ok. Hackers and administrators will not get an access denied message when they try to open the file. To make things...

Hello, welcome to my first post! Today, I would like to talk about setting up a Page File Encryption in Windows 7 and Vista. But first - what is a Page File Encryption? Why should you enable this option?

For this particular example, I will be working on Wndows (sorry X users). I might write a similar guide once I am more comfortable with programming in Linux.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

You've managed to get your Motorola Droid X rooted, so now what? What's one of the first things you could install on your Droid X? What's the most valuable items you need on your cell phone? Everybody knows the answer… wireless tether, a way to suck the internet from your Droid X to your laptop or home computer. Well, this video tutorial will show you how to get the free Wi-Fi tether mobile hotspot app, called Wireless Tether, on your Droid X from Verizon Wireless. You don't have to pay tons ...

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.