In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.
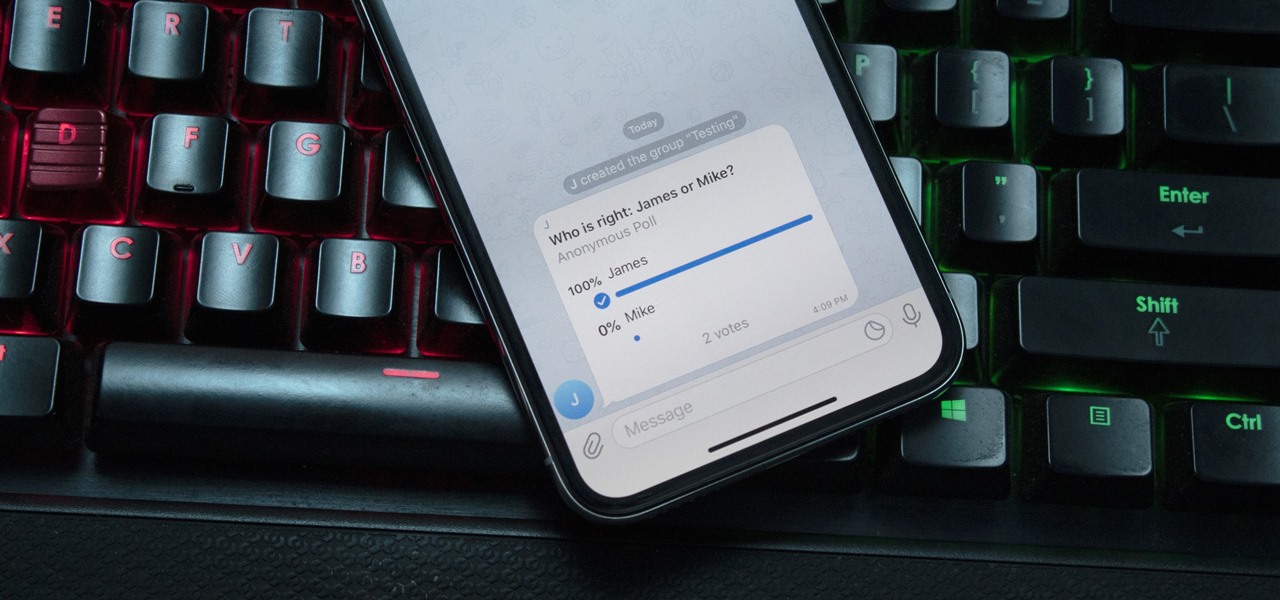
With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

With divorce rates set to hit a record high this year, 'betterdatethannever' explains how to avoid arguing with your partner. Most people experiencing marital difficulties blame financial reasons for their fights. The easiest way to avoid conflict with your partner is to make sure you communicate and share your problems. Holding things deep inside makes them get worse and worse till they explode into one huge argument. Allow your partner to speak their mind and express things they do not like...

Conflict is a part of life but how you deal with that conflict is up to you. You may find yourself in an argument and instead of making it a shouting match, employ some techniques that will be sure to keep this conversation civil.

In this how-to video Tracey Cox explains a method for quelling arguments in a relationship. If you find that you and your partner are always arguing about the same things, then Tracy has a way to help you move past it. Watch and learn how to settle your arguments and make your relationship much more peaceful. Avoid recurring arguments in a relationship.
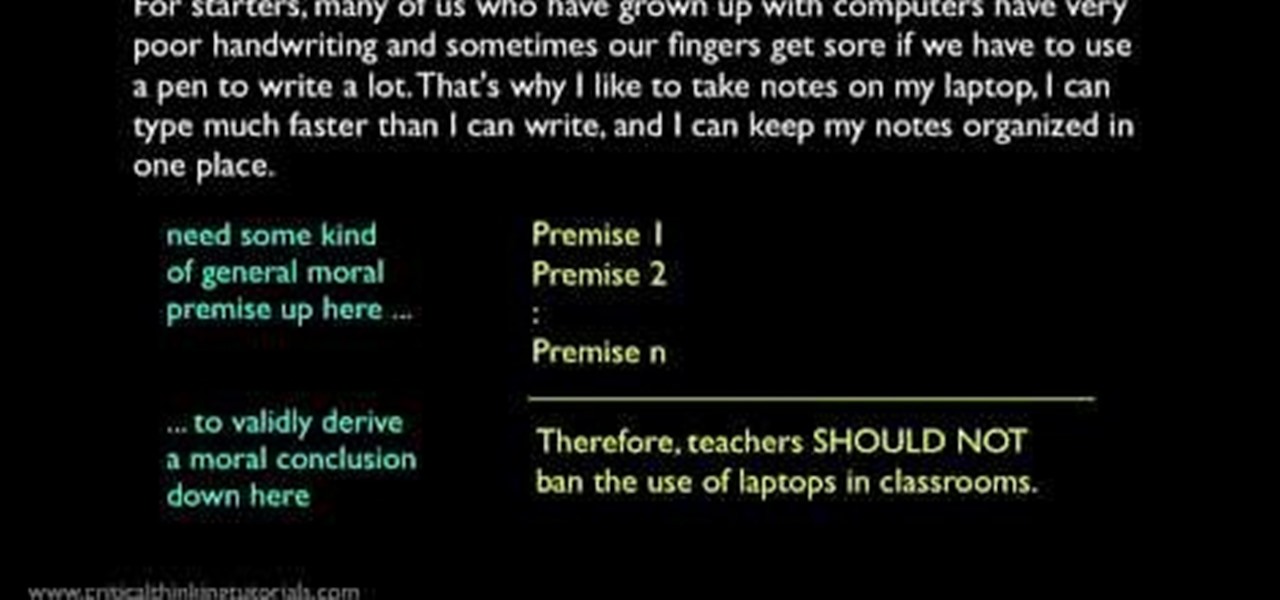
This video describes the art of writing argumentative essays. In other words it narrates how to improve arguments of an essay. It starts with an analysis of classic examples. The speaker begins by criticizing the style of paragraph and how to improve the suggestions. He explains how to omit errors and form your arguments in commanding manner. Finally, he says how to come a conclusion by adding solid evidence. At the end of course he will show you how to transfer a old matter into a classic ex...

This video takes the viewer through a simple, step-by-step process for writing a compelling introduction to an argumentative essay. According to the author, an ideal introduction should begin with detailing the subject matter of the essay, and should provide the background information on the issue being discussed in the essay. The introduction should be very clear about the conclusion that the author of the essay is alluding at. One of the major problems with student essays is that their intr...

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Excel 2008 for Mac makes it easy to create formulas for cells. You could always do it before, but now with the new Formula Builder feature, building formulas just got one step closer to simple. The Microsoft Office for Mac team shows you just how to build formulas by using the new Formula Builder in this how-to video.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

So you need to find the p-value for your hypothesis test. To do so, employ the spreadsheet program Microsoft Excel. Using a simple formula, you can easily determine the p-value for your tests and thereby conclude strong or weak support of the null hypothesis.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

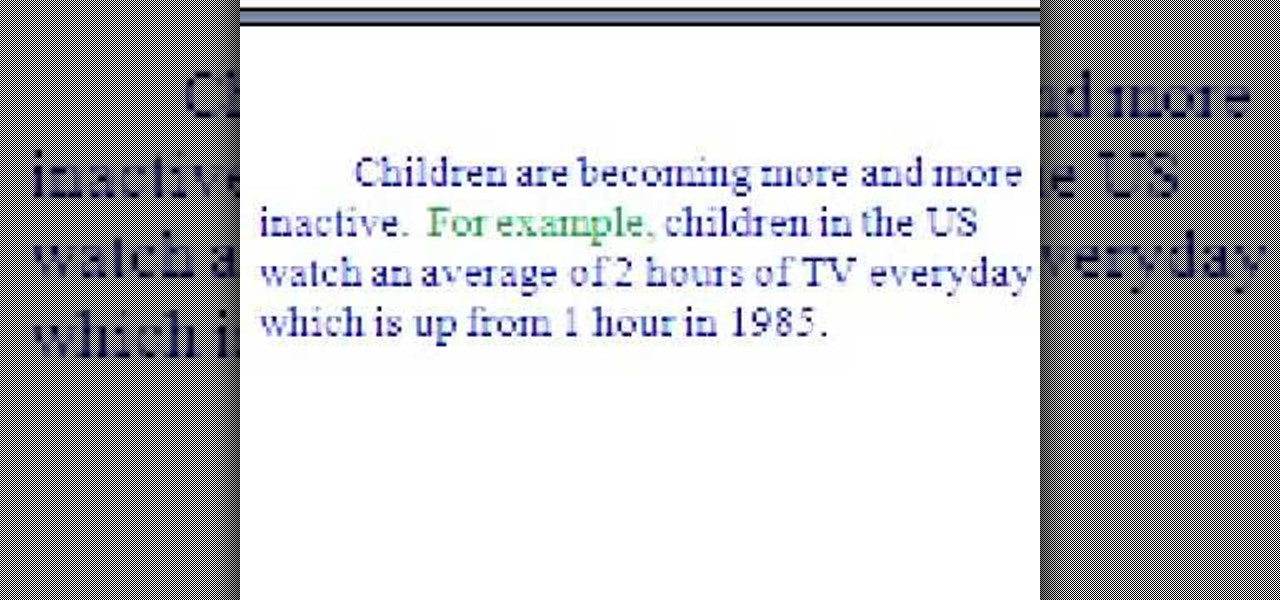
This is a video on writing essays. The video is a part of a series on essay writing. The current video involves inserting examples into an essay that you are writing. The speaker describes how to complement arguments contained within essays that provide support to the argument. The purpose is to improve the strength of arguments and, by extension, the quality of the essay. The speaker goes on to describe different phrases that are helpful in introducing examples into an essay.

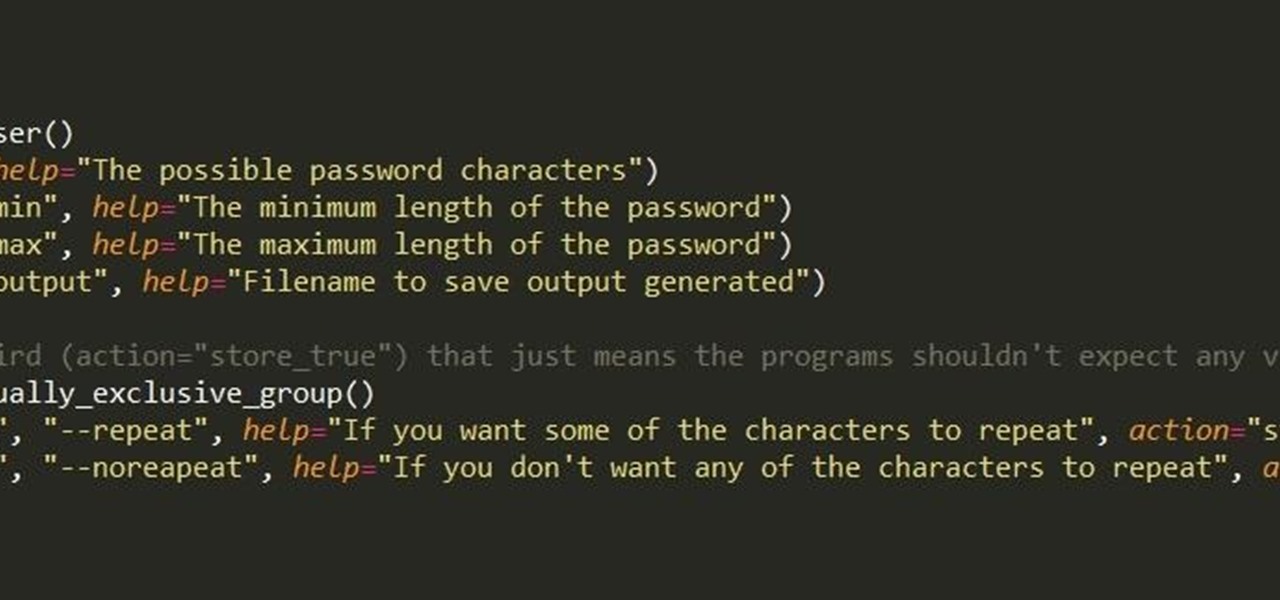
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

This video is about showing you how to use feng shui in repairing your dysfunctional family and getting rid of the bad vibes that may be in your home, re-energizing the foundation of love. The family center is located on the left center of your home. The element for the family is wood and you wouldn't want to have dead or plants with sharp leaves because they start arguments. Too much red is considered the fire element and can also lead to your family having arguments. If you have metal in yo...

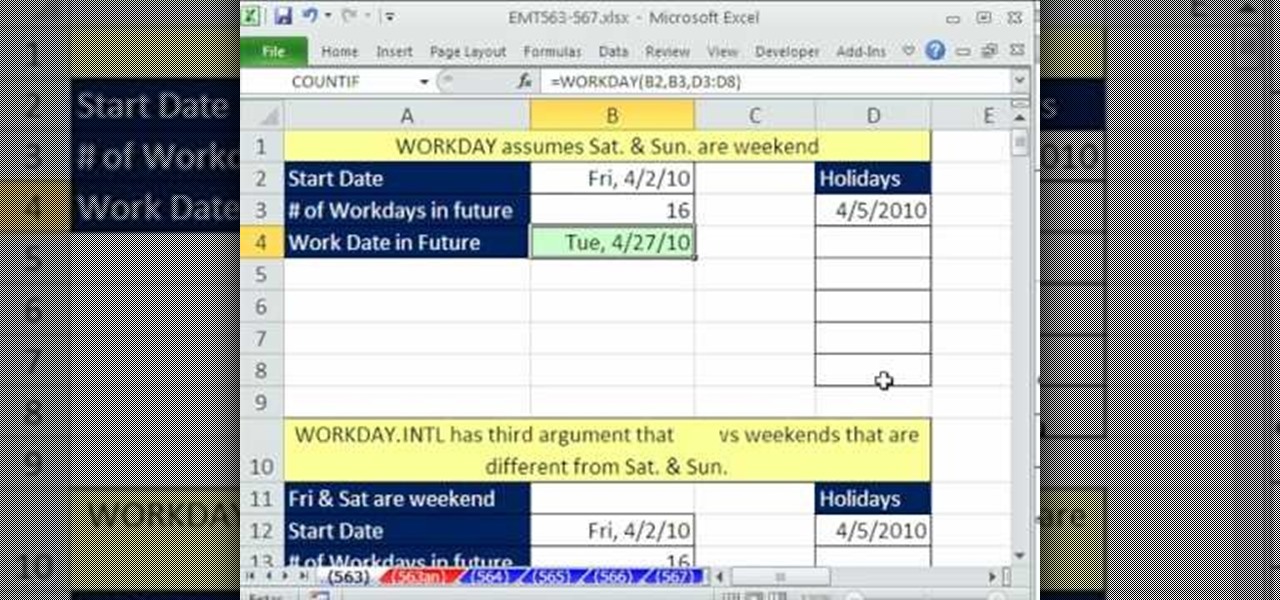
This video tells us the method to use the WORKDAY & WORKDAY.INTL functions in Excel. These functions are used to find a workday after a finite number of workdays in the future. WORKDAY uses Saturday and Sunday as off days. Its syntax is WORKDAY(start date, days, [holidays]). 'days' refers to the number of days in the future and holidays is the list of holidays written below each other in the same column. If Saturday and Sundays are not your off days, use WORKDAY.INTL. Its syntax is WORKDAY.IN...

It is argued that sun exposure and warm weather helps people cope with and fight multiple sclerosis. Sun is important to produce vitamin D. There are arguments that vitamin D deficiency is connected with cases of multiple sclerosis. Get a blood test to make sure your vitamin levels are optimum and you are suffering from no mineral or vitamin toxicity.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

He's not exactly demanding sexual favors, but his flirting is getting really gross. What's a girl who likes her job to do? You will need diplomacy and documentation. Assess his behavior. Now, don’t be offended, but we have to ask: Is he really coming on to you, or is he just a sociable, flirtatious kind of guy? If it’s the latter, just ignore it. Do your part to keep the relationship professional. Don't chat about how your last two boyfriends cheated on you and then expect him to know that di...

How you work out your abs determines how they'll appear in the long run. Not only are the type of ab exercises you do important, but also the frequency with which you do them.

In this tutorial, we learn how to teach children to be gentle. If children are in a setting with other kids, arguments will arise. If a child happens to try to harm another, you will need to tell that child that it hurts the other one if you harm them. Tell them that it's not nice and that they need to say they are sorry for not being gentle. Tell them that it is a nice thing to be gentle with other people and they will make friends by doing this. This will help your child be gentle and make ...

Elizabeth Chamberlain, with Space Lift, demonstrates how to make room for love with feng shui at home. First, find your focus room with your energy map by laying the energy map on top of your floor plan. The love area is the far right corner from the front door, facing in. If the love area turns to be an outside area like a patio, clean it up. Remove the cacti and pointy plants to reduce arguments in the relationship. Clear out any unfinished materials and projects. Next, complete the area by...

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.