Tinder, marketed as a free 'dating' app, is no stranger to paid features. The company has long allowed users to step up their game by spending money on their 'Tinder Plus' service. Tinder would like more of your money, it seems, as it rolls out a new paid service with a highly-desirable premium feature — the ability to see who has swiped right on your profile, without having to match.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.
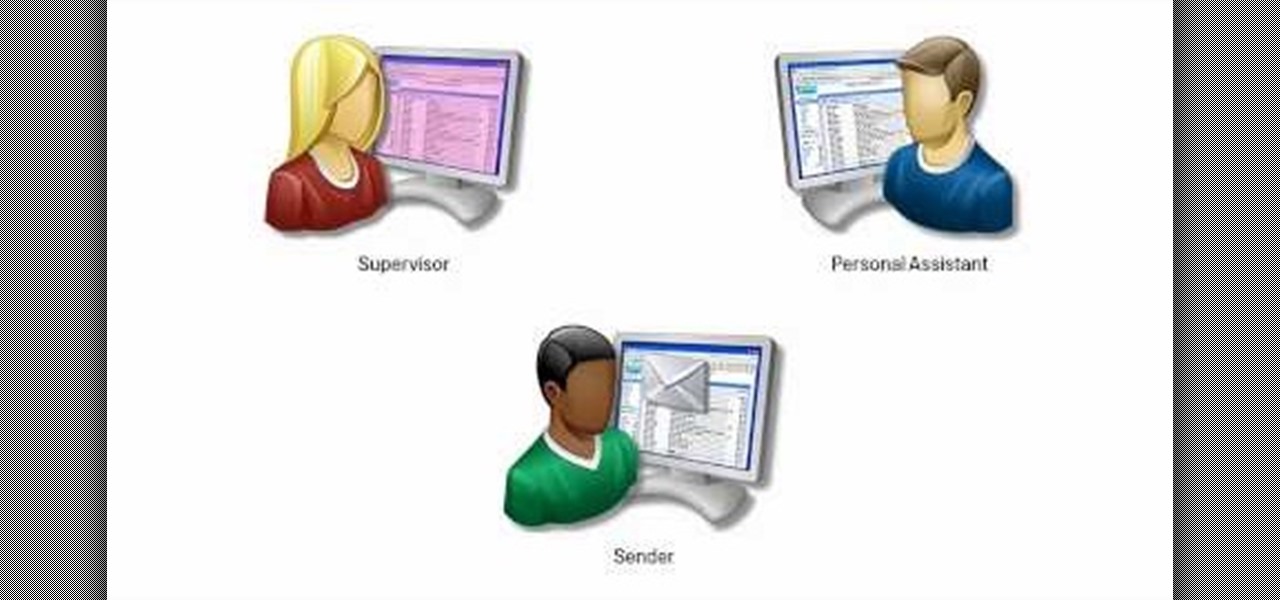
When you're personal assistant needs to handle your e-mails for you, it can be quite daunting having to give out your personal account information just so they can have access to your e-mail. And more importantly, having to battle for log in time might also be quite the hassle. With Gmail you can actually delegate your personal assistant so they have access to your inbox and can reply and send messages on your behalf, but they cannot change settings, passwords, or chat on your behalf. In this...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 593rd installment in their series of digital spreadsheet magic tricks, you'll learn how to add data validation to allow only Monday dates in a cell using the custom option and the WEEKDAY function.

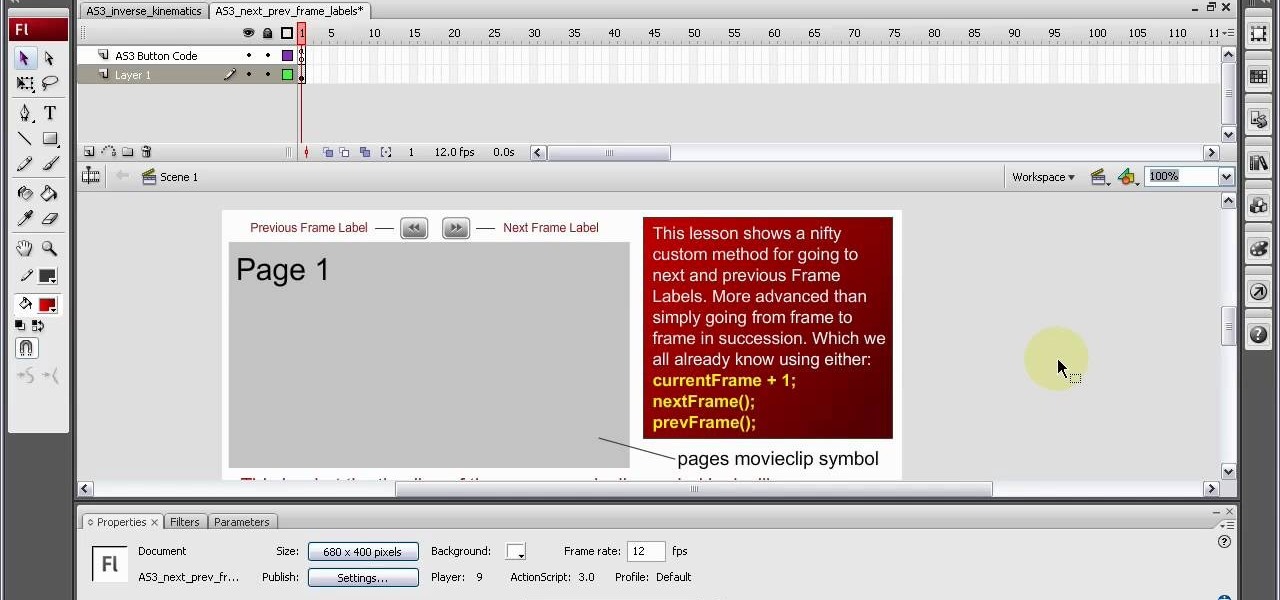
Frame labels are titles associated with certain segments of content (such as playing a tutorial in sequence and assigning each clip a separate frame label). This tutorial shows you how to set up a custom navigation system for your frame labels, so users can switch back and forth between segments.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to add a exit full screen mode feature to your applets when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

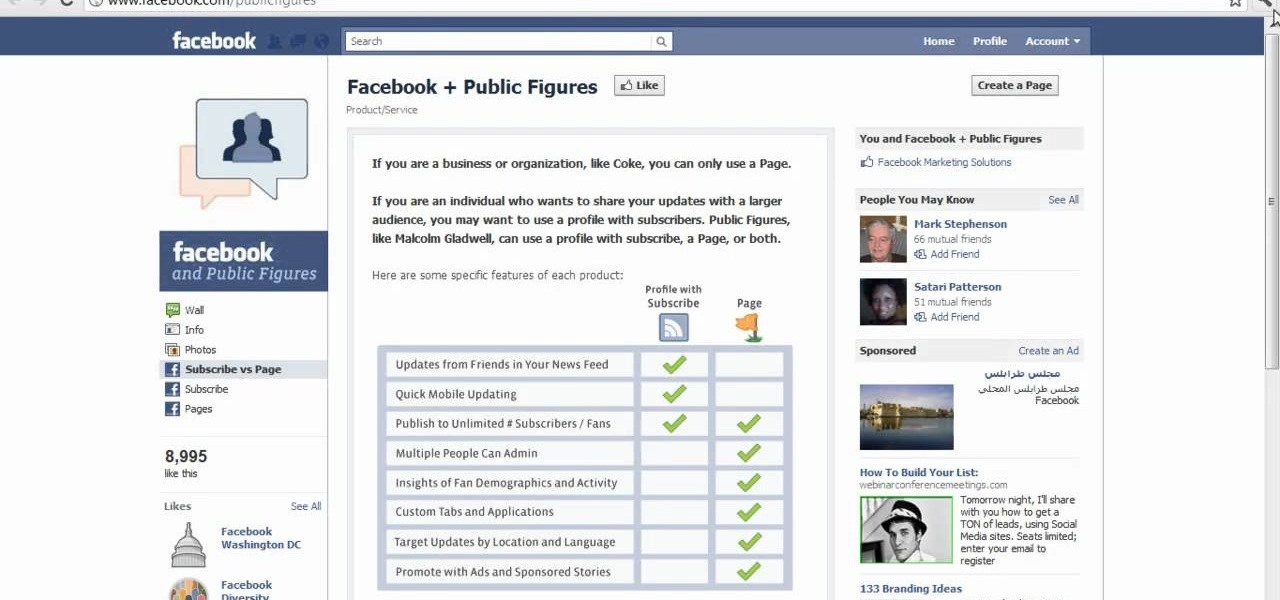
If you're interested in adding a Facebook button to your profile to allow your friends and others to subscribe to you so they can see your updates and posts without being your friend, take a look at this tutorial. With it, you'll be able to turn on a Facebook button for your profile.

Let visitors to your website vote on a poll! Then, display the results to viewers, and also set it up so certain IPs can only vote once. You can easily code this poll using Flash, and this tutorial shows you how to create your own poll.

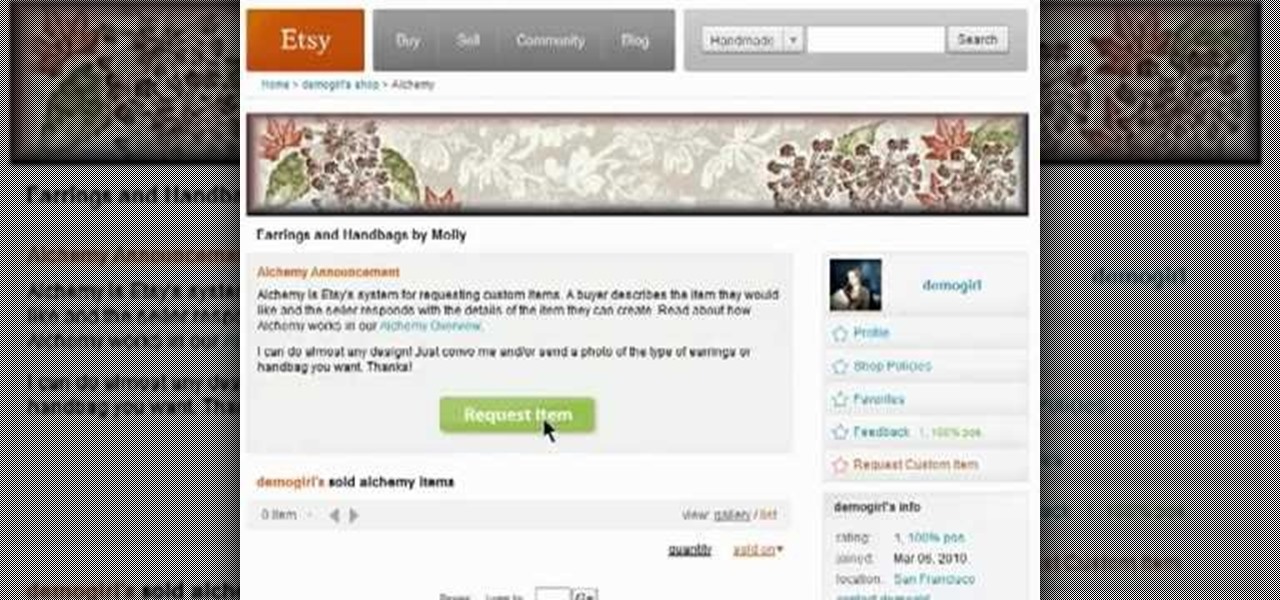
Need some help figuring out how to utilize the Alchemy feature when selling things on Etsy? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using Alchemy yourself, take a look.

This video will show you how to enable/disable the pop up blocker for a specific web page: 1. To allow pop ups on a specific website click on the pop up blocker button on your tool bar, the Icon will change to show that pop ups are now allowed.

In this clip, you'll learn how to use Content Presenters with templates when working in Silverlight. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

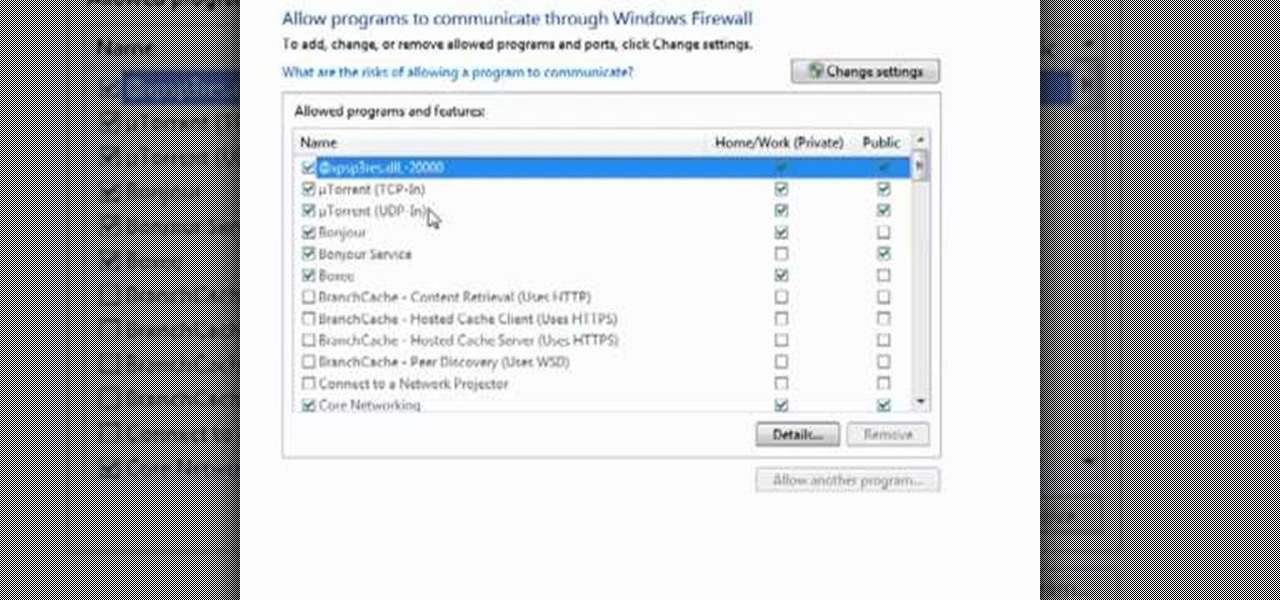
Want to adjust the Windows Firewall to permit µTorrent? This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

Lawrence Moroney shows you how to build an instant messaging application in Silverlight using ASP.Net controls to support international text entry. If you want to add an instant messenger to a web site or web tool and have it support international text entry, then you should watch this Silverlight ASP.net programming tutorial.

Want to know how to add contributors to your WordPress blog so other people can post to it? This clip will show you precisely how it's done. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about its features through videos like this one. Take a look.

There is a seemingly endless supply of games on mobile. While many of these games are fantastic, many are also, well ... garbage. And unfortunately, the platform as a whole has been dismissed because of those garbage games. This situation leaves gamers like myself wondering what can be done to develop a deeper public respect for gaming on smartphones.

Here is a tutorial on getting a perfect 1/4" seam allowance for quilt piecing. The sewing machine foot will sometimes have a groove to allow you to make a perfect quarter inch seam automatically. If you don't have one of these, there are a few ways to make your own quarter inch seam guide.

This is the GetNetWise video guide on how to set up Internet Explorer 6.0 for Windows to allow cookies from some sites. This is useful if you wish to block cookies by default, but allow for certain sites. The procedure is simple; firstly, select "Internet Options" from the "Tools" menu. Then select the Privacy Tab of the Internet Options menu, and under the Web Sites section click the Edit button. In the text box labeled "Address of Web site", type in the address of the site from which you wa...

In this video the instructor shows how to allow email from people you know and block emails from all other users in AOL 9.0 for Windows. To do this, first open your AOL mail box. Go to the Mail Options menu and select the option "Block Unwanted Mail". This pops up an "AOL Unlimited Use Area" screen. You have to select "Yes" to proceed. This opens the Mail and Spam controls window. Now scroll down in the window till you find an "Additional Spam Filters" heading. Now there is a Select Filter ov...

In this tutorial, we learn how to allow only your computer to access your Wi-Fi while using Apple Airport. First, select the Apple Airport Express item on the base station chooser. Double click this and press Configure, then enter your password in the new window that pops up. Now, a new window will open, and you will need to click to "Access Control" tab on the top of the window. Next, click "add" and then select "Mac address" and enter in your MAC address and description. Once finished, clic...

It's great to see proof that Google+ is listening to feedback from their users. As a result of the discussion surrounding gender and privacy, Google+ Profiles Product Manager +Frances Haugen announced that Google+ will allow users to hide their genders on their profile.

Original picture appears on the ONION.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

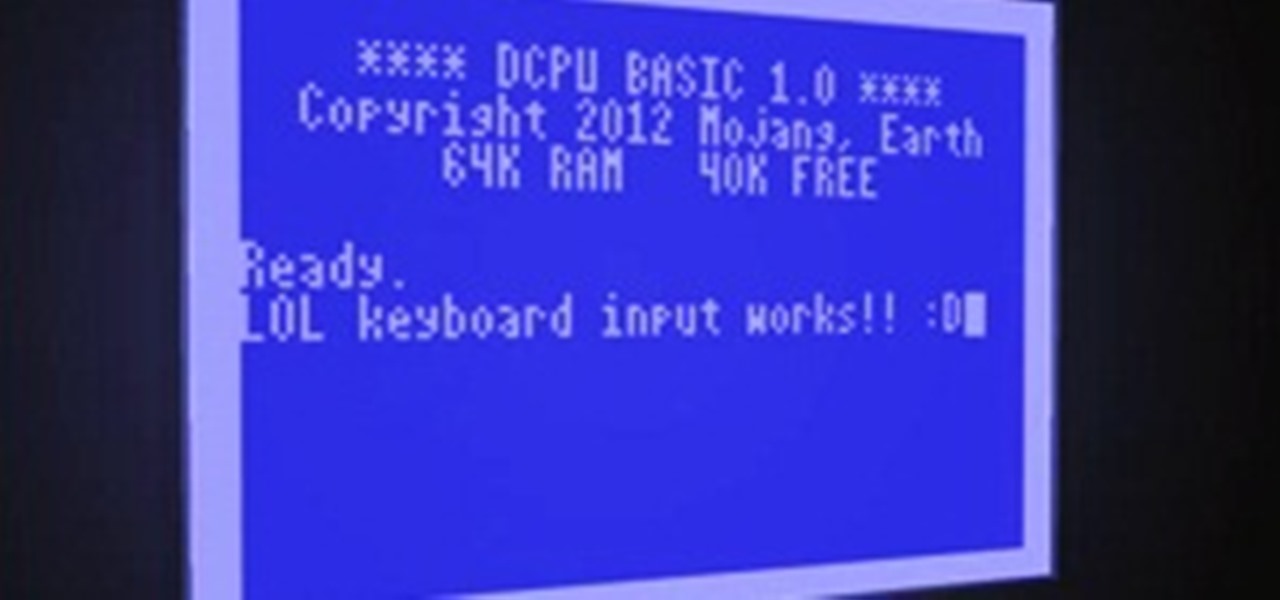
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Pumpkin carving is one of the most fun and creative of the many fun and creative elements that make Halloween such a great holiday. If you need some tips for improving your pumpkin carving, you've come to the right place. This video will show you tips, tricks, and tools that will allow you to carve more elaborate, cooler pumpkins more easily.

The video is an episode of Indy Mogul. It opens with a man who tells us the topic of this show is to help people make fake prosthetics for a fish-man costume for Halloween. After an intro showing us that the show is about making homemade special effects and props on a cheap budget and a disclaimer the show tells us the ingredients we'll need to make the prosthetics. They are: clay, sunglasses, latex sheet, quarter-inch foam, styrofoam head and bald cap, and liquid latex. The show then demonst...

In this video, we learn how to create Halloween inspired skull nails. First, apply a base coat to the nails before applying anything else. After this, apply a black nail polish to the entire nail and allow it to dry. Now, take a silver nail polish, and draw a skull shape onto the nail. Use your black nail polish to create the eyes in the skull, then use a nail brush to create the shape of the head and bones underneath the skull. Let the nail dry, then repeat this on all your nails for a spook...

If you're looking to pull off a great prank for Halloween, this next tutorial will show you a classic prank. It involves using a candy dish and your hand.

Are you having a Halloween party? Looking for a spooky dessert to serve to all of your friends? In this tutorial, learn how to make a cake shaped and decorated like a mummy. This mummy design is very realistic looking and will make a perfectly spooky addition to any Halloween festivities. Allow Ronda to take you step by step through the process of creating this deliciously scary dessert and be the hit of the holiday!

You will need some vodka and orange juice. Take your shaker and fill with ice. Add the orange juice to the ice. Set aside to chill. Next pour off the right amount of vodka you will need. Mix a teaspoon each of green and red food coloring. Add it to the vodka and stir. This should make your vodka appear black. Pour some sugar on a plate and take your martini glass, place it upside down in the sugar, and spin it so the rim of the glass is covered. Put some ice in the glass and fill half the gla...

In this video, we learn how to apply a glitter makeup masquerade mask for Halloween. Start off by applying primer to the eyes, then a dark pink eyeshadow up to the crease. Next, apply purple to the lower lids, blue to the crease, and white underneath the eyebrow. After this, take a darker blue to the outside of the eye and blend together with the pink in the middle. Next, apply the blue shadow to the lower lash line, then apply eyeliner on the top and bottom of the eye in black. Now, you will...

This video is a step by step guide for creating exposed teeth makeup . This is loosely based on the Harvey Dent character from Batman: the Dark Knight.

Check out this Halloween set video that explains how this entry archway display was created. This show & tell video was taken immediately following the Halloween Yard Haunt prior to dismantling. The unscripted prop descriptions are as complete as time would allow.

Check out this instructional video that shows how to set up a prop static ghost for Halloween.

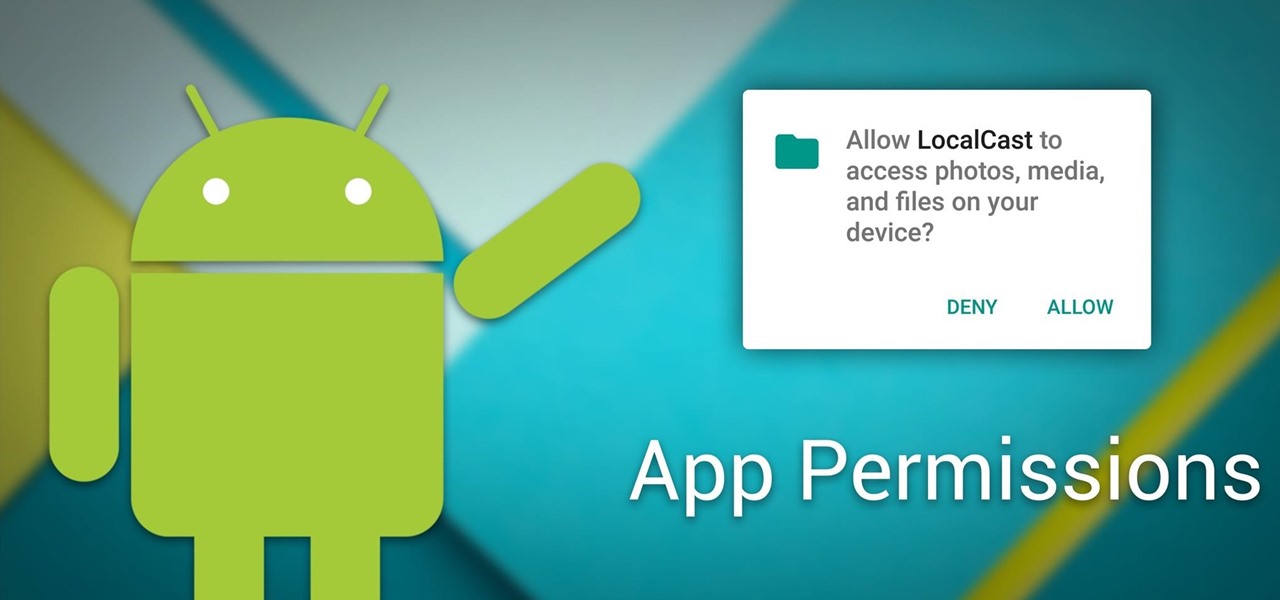
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.