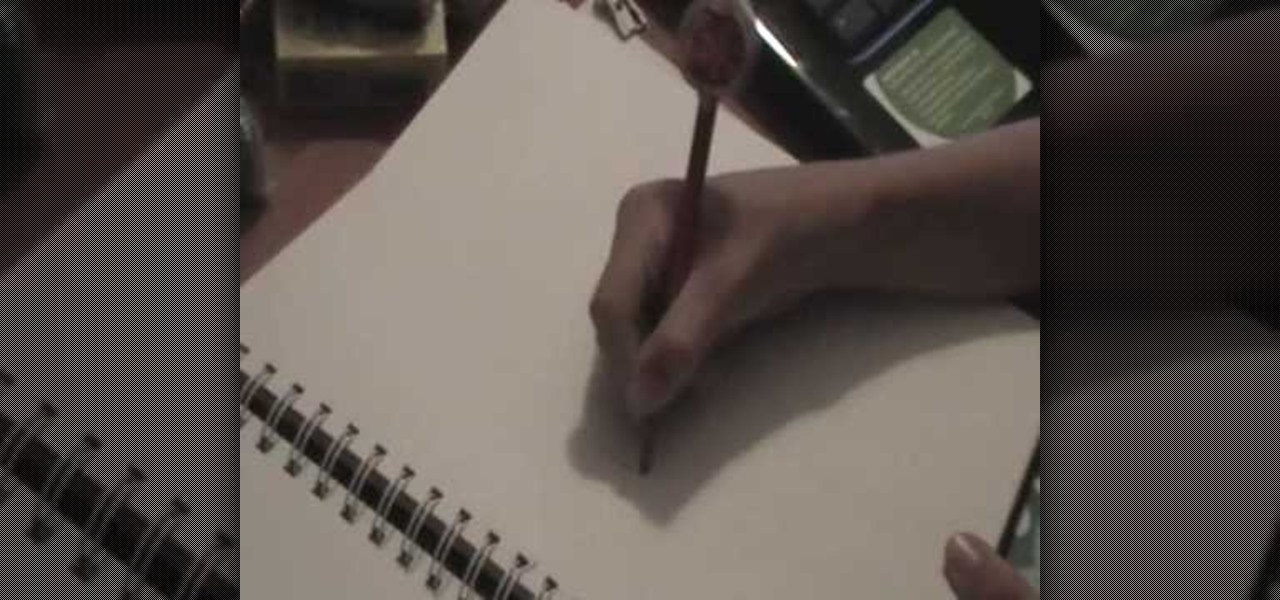Make the perfect cake for any little boy or girl with Sesame Street character cake toppers! In this two-part video tutorial, learn how to make a baby-version of the Cookie Monster out of fondant icing and gumpaste. To make Elmo, carry out the same technique & instructions but with red icing. Give that little special someone in your life a cake they will cherish!

Nothing says 'I Love You' more than a gift that was made from scratch. Especially if that gift is shaped like a heart and is made from wood.

In this video, we learn how to photograph a pregnant mom. Try taking a shot of the woman outside, this will feature her stomach and show off the glow of her skin as well. Process it after you have taken the photo to edit it further. Drape a sheet around the woman as well, which is a really popular photo technique as well. Take fun shots with your partner, animals, other children, and around the house! The camera can focus on different things to show multiple subjects in the scene. Be creative...

A great gift to offer someone for Valentine's Day is something you make yourself. In this tutorial, learn how to make a celebrity style keepsake box using decoupage techniques. This box can hold anything from gifts to precious items to little trinkets.
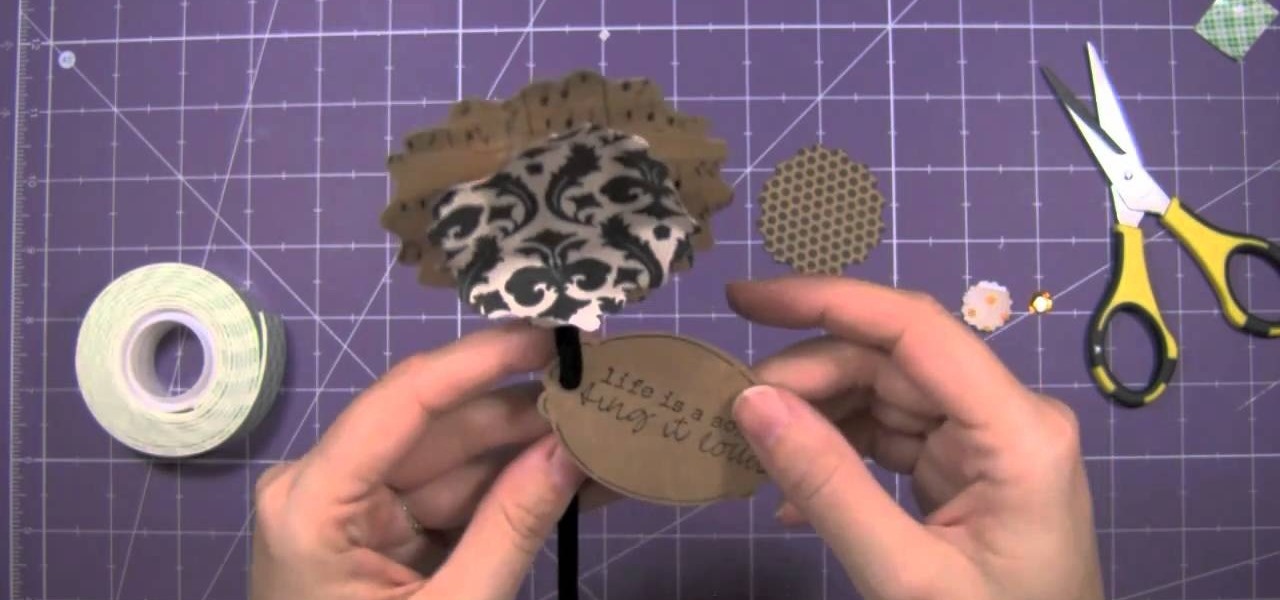
The biggest pro paper flowers have over real flowers is that they last a hell of a lot longer. So whoever receives your paper flower will be able to cherish the present for longer than a few days.
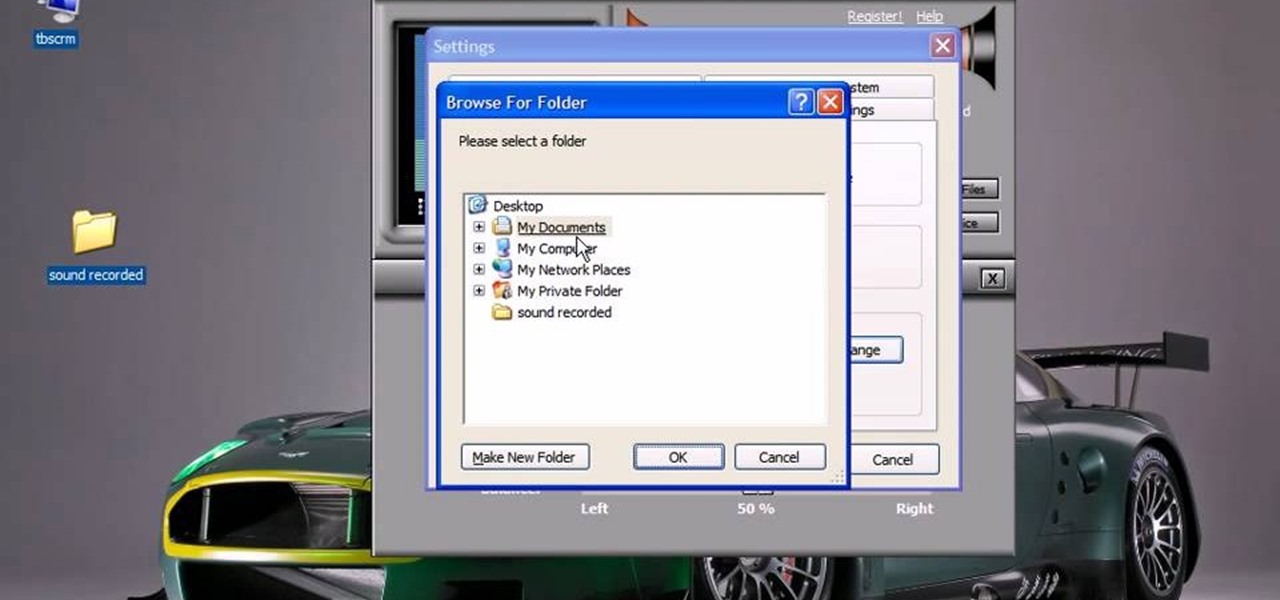
This video will show you how to record audio from the internet. Once you install this program, the video goes on to give you step by step instructions on all of the bells & whistles within the Free Sound Recorder. It will teach you how to work it according to your computer settings, and show you how to personalize and change the settings within the program. It gives you recommendations on the best options for the best audio. It also gives suggestions like choosing which folder to default all ...

With Michael Jackson's recent death, people from around the world have come to cherish what he was best know for - being the "King of Pop", even with all of the allegations of child molestation for which he was never convicted of. This video series is a dedication to Michael Jackson, to forever immortalize him on paper.

With Instagram's archive feature, we have the pleasure of hiding all our stupid photos of #gettingcrunk from back in the day. This wonderful new IG feature will still allow us all to cherish those embarrassing moments in our life, yet hide them from those people we hope would never scroll so far down.

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

You may be tempted to install the iOS 16 developer beta on your iPhone to try all the exciting new features it has to offer, but it may be a good idea to wait if you only have your personal iPhone that you use every day.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

If you're a diehard Apple fan, chances are the new iPad 2 caught your eye, stole your heart and emptied your wallet. Who couldn't resist the sophisticated slim-body design or its fascinating new Smart Cover? Well—it seems nobody could. And if you were late to jump on the bandwagon, you're still probably cleaning that dust out of your mouth because it took off without you—leaving the latest and greatest Apple gadget out of your reach.
For this very reason I would like to share some affiliate marketing tips for beginners here so as to make the journey to affiliate success a less painful one. Did I say painful there?

Tis’ the season…for weddings! At the beginning of October, three of my college pals got married on the same day. This meant a ton of planning, parties, and presents for these three lucky ladies. This also meant that there were many a brides maid needing to make sure their bride was feeling special on such a wonderful occasion. One of the most exciting aspects of being the Maid of Honor is helping to plan the Bridal Shower, but it can also be a lot of work if you aren’t prepared. Here are 10 t...

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)

Choose the Right Path Making a choice