Eric Scott demonstrates on how to use a pendulum to connect to the spirit. You can get any pendulum you have or use the custom made light plastic pendulum about five and a half inches long which may help to get your response very quickly.

Daydreaming about drifting? Drifting refers to a motorsport where the driver intentionally oversteers, causing loss of traction in the rear wheels through turns, while maintaining vehicle control and a high exit speed. Learn how to drift in your car with help from this video.

Freud once said that jealousy is both inevitable and universal. So why not work it to your advantage? While the end results of intentionally game playing are dubious, at least as far as building a healthy relationship, if you're hell bent on fostering a bit of jealousy in someone, this how-to video will do the trick. Follow along with the steps in this video and find out if flirting and acting unavailable help you out in the dating game.

One way to avoid plagiarism is to paraphrase. Plagiarism is taking credit for words and ideas that are not your own. Plagiarism can be done intentionally or unintentionally. Paraphrasing is one way to do this, as long as you give credit to the source of the ideas.

This speed-drawing tutorial demonstrates how to draw a futuristic soldier character with a flamethrower and a gas mask on your computer. It moves very quickly, but if you can't keep up you can reference the artist's step-by-step sketches where he breaks down the steps he takes in copious detail. The background is intentionally vague so that you can fill in whatever you like, most likely a post-apocalyptic setting of some kind. A good view for any comic book, fantasy, or science fiction artist.

This video shows you how to get a fabulous faux bob glamorous updo. 1. Gather needed tools a curling iron and preferred hair spray of your choice.

Google's new cross-platform video chat app, Duo, is finally making its debut today, following a long waiting period that began in late May. The app was heavily teased during the keynote speech at Google I/O, but was not made available for download until now, so any early hype Google managed to whip up has died down quite a bit.

Love mehndi but don't know how to apply it on your own? Well, here's a design that shall enlighten you on how easy it is to create beautiful mehndi designs in no time. Generally, the most famous pattern is the floral henna design which uses flowers such as lotus, sunflower and buds in combination with leaves and creepers. It is unlike the traditional design which completely covers the hand leaving no space. In this design, spaces are left intentionally to let the design stand out. It takes on...

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

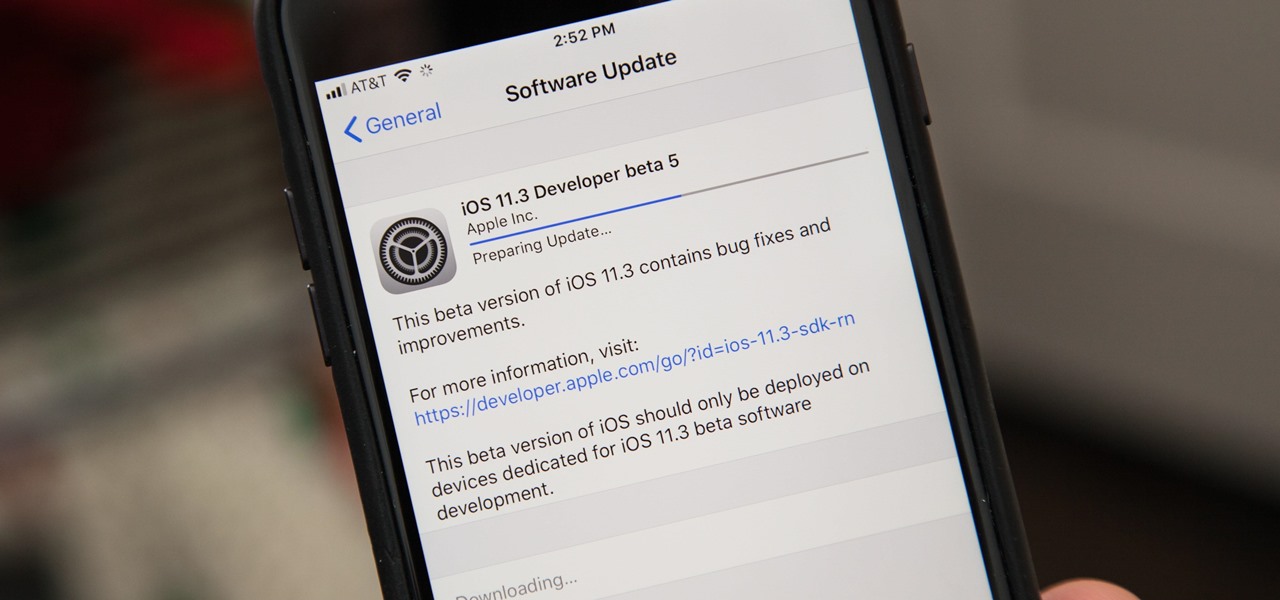
Apple released the fifth build of the iOS 11.3 developer and public beta on Monday, March 12. The update comes exactly one week after the March 5 release of beta 4, which mostly introduced bug and stability patches. At this time, this new beta appears to do much of the same.

Snapchat accidentally—and then intentionally—announced their digital eyeglasses, known as Spectacles, over the weekend. While we'd hoped their augmented reality-heavy platform would result in related hardware, Spectacles unfortunately seek to "reinvent" little more than a video camera.

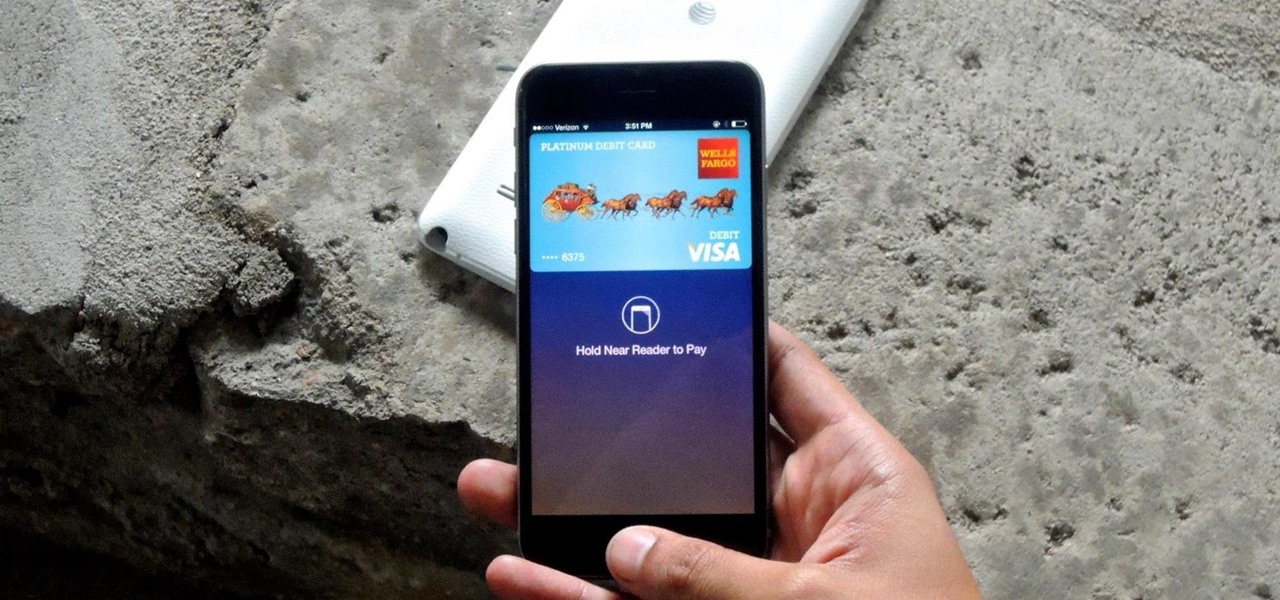
Apple Pay is ready for use at over 220,000 outlets across the United States. By using your iPhone 6 or 6 Plus, all you have to do is point your device at any NFC-enabled point-of-sale system compatible with Apple Pay, press your fingerprint on the home button, and voilà—you've just paid for something with your card. As a matter of fact, the store doesn't even need to have Apple Pay compatibility to work with your phone. If their machines have NFC-technology, they'll recognize your device (unl...

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your phone.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

The stereotypical geek is not good at sports. Think about it, we’re known for spending time in dark basements doing weird stuff that has nothing to do with running around and being active. So we’re known for our inability to play sports, but I wouldn't call it an inability so much as a creative way of passing these challenges by the skin of our teeth. Examples:

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

With the Galaxy S9 finally making its debut, flagship season is officially underway. But even though Samsung's latest offerings are the newest phones out there, they already face some stiff competition — namely, the LG V30.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

If you want to root your phone, it's a huge plus. If you want to install a custom ROM like LineageOS, it's an absolute must-have. Custom kernels like ElementalX, custom recoveries like TWRP — none of this happens unless you buy a phone with an unlockable bootloader.

Google has done it again—they've pushed another broken OTA update for the Nexus 6. Except this time, it almost completely softbricks your Nexus 6 instead of just screwing up Android Pay and SafetyNet. Apps are force-stopping left and right, making the phone practically unusable.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

There's no shortage of reasons to love the One, yet a feature curiously omitted from the device, much to the chagrin of power users, is a multitasking button.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

The dream of Google Glass lives on via North's stylish and normal-looking smartglasses that bring text messages and navigation prompts into the user's field of view and Amazon Alexa integration for voice-activated assistance.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

Zenge came to my attention as a free game on the Google Play store — it will remain free until midnight, so anyone catching this review on the 25th, download it ASAP — but I imagine it would be worth the typical $0.99.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.